As GenAI becomes multi-modal, the hype of image and video AI generators has captivated the world. Millions of users worldwide flock to OpenAI’s website to check out Sora, while others turn to Midjourney. But these two GenAI models, as well as DALL-E 3, Evoto, ChatGPT 5, and many others, aren’t just popular among users. Cybercriminals love them, too.
Using the global trend of AI as bait, cybercriminals have been running malicious ads on Facebook. As Bitdefender reported, a Facebook page using the name Mid-Journey AI had 1.2 million followers and ran a fake ad that reached more than half a million users in Europe. Some fake GenAI ads on Facebook even managed to stay active and undetected for over a year. This speaks very poorly of Meta’s ad security guardrails and policies.
Once victims click on these malicious ads, they are directed to fake pages that impersonate major brands in the GenAI business sector in order to distribute malware. These pages are extremely well designed to trick users into self-installing stealers on their devices.
Fake GenAI ads leading to stealers: The new doorway into your device
Bitdefender — investigating and observing “a motley crew of AI-powered illicit operations” over the past year on social media — reported that criminals are now impersonating advanced AI companies and their services and apps to distribute malware.
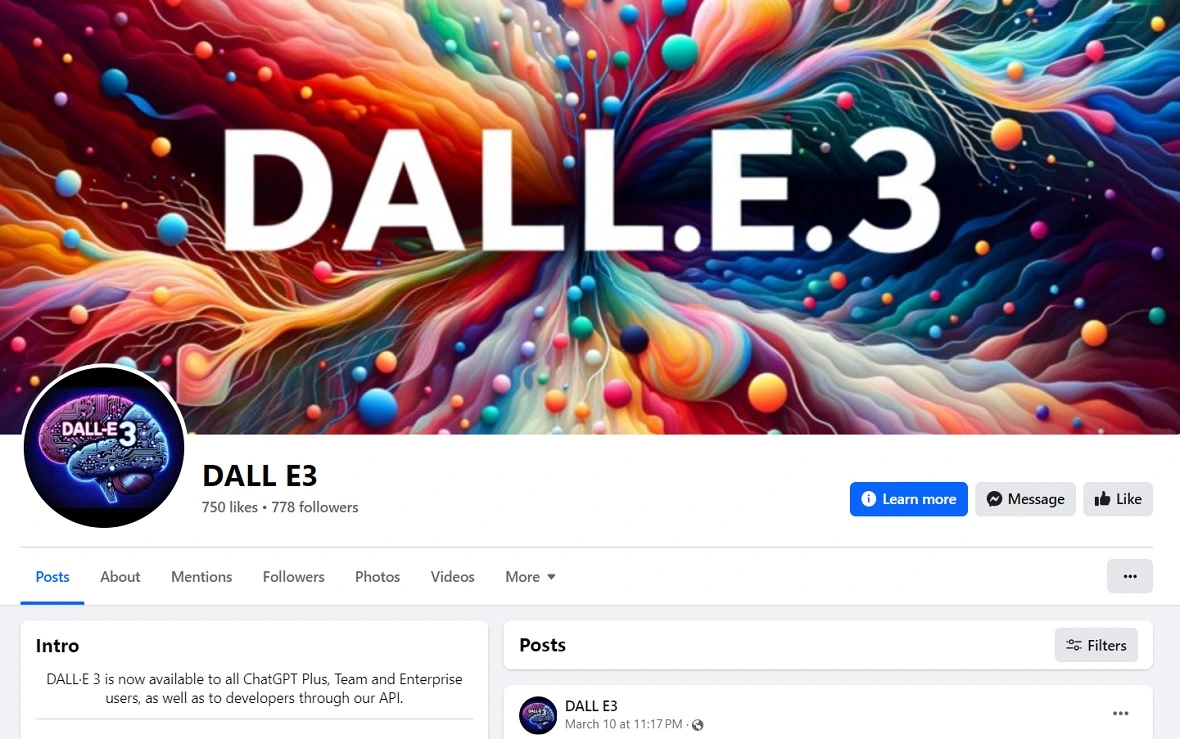
Browser data at risk
Bitdefender found that the fake GenAI ads on Facebook had been “meticulously designed” to look like the official desktop versions of popular AI software. The investigation also revealed that attackers are actively updating the malicious payloads they are distributing to avoid detection. All this puts users’ browser data at risk.
Browser data goes well beyond browser history. It includes cached data, cookies, browsing preferences, credentials and passwords, downloaded files, and browsing patterns and behaviors. Bitdefender explained why bad actors go after browser data.
“The links direct users to malicious web pages that download a variety of intrusive stealers to harvest sensitive information from compromised systems, including credentials, autocomplete data, credit card information, and even crypto wallet information,” read the report from Bitdefender.
Analysis of the distribution and reach of fake GenAI ads
The most concerning findings discovered by Bitdefender are unquestionably the reach that this new wave of fake Facebook ads has had and the potential number of victims it can reach.
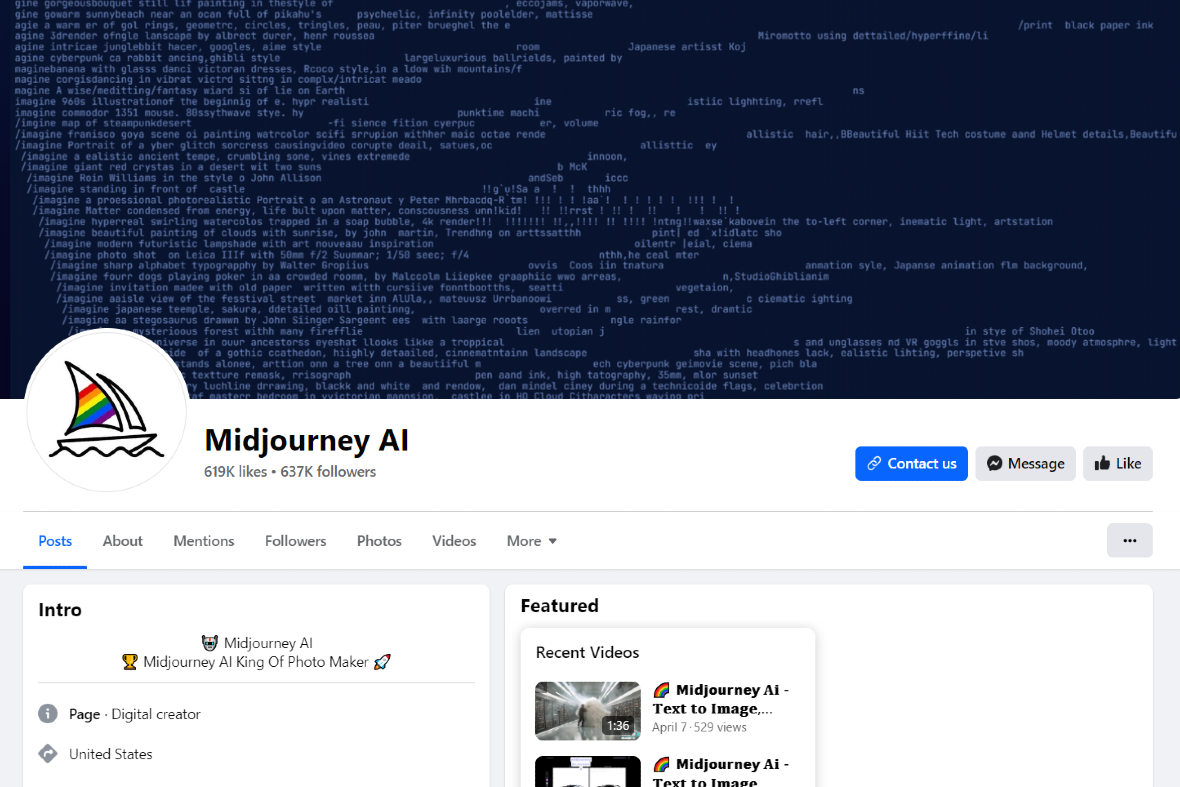
The wave of malvertising campaigns has spread significantly by leveraging Meta’s sponsored ad platform. Some of the countries most affected include Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, Sweden, and others.
Threat actors have observed how easy it is to bypass Meta’s security — and how effectively they can scale their attacks. Consequently, new fake pages are constantly being created to distribute even more malicious ads to users via Facebook.
AMOS Stealer continues to pose a threat to macOS users
The fake ad social engineering tactic, combined with malware stealers that usually target browser data, is not new. Over the past year, the infamous Atomic Stealer (AMOS) has been shapeshifting using the same technique. It manipulates Google Ads platforms and search engine optimization (SEO) algorithms, impersonating system updates and popular platforms like Slack.
Recently, AMOS was once again discovered hiding in the background of another fake ad campaign. On April 5, Jamf Threat Labs discovered that the hackers behind AMOS had once again tricked Google Search and managed to list their fake site among top search engine results.
As Jamf Threat Labs explains, AMOS is now impersonating the new “Arc Browser.”
Rampant criminal activity on social media linked to tech layoffs
The level of fake and malicious content on Meta is reaching concerning levels. In March 2024, 40 US states and Washington, DC called on Meta to combat the dramatic rate of account takeovers in the platform. In a letter to Meta’s chief lawyer, the US states said that criminals are “winning the war and running rampant on Meta.”
The rise of malicious fake ads on Meta’s social media platforms has been linked to the company’s 2022 layoff of thousands of security and privacy-focused workers.
In 2023, tech layoffs continued. CNBC reported that in May 2023, Meta, Amazon, Alphabet, and Twitter strategically executed a mass downsizing, affecting the companies’ security and privacy capabilities.
Meta cut 21,000 jobs. This reduced the size of security and privacy teams working in the company, including a new fact-checking project.
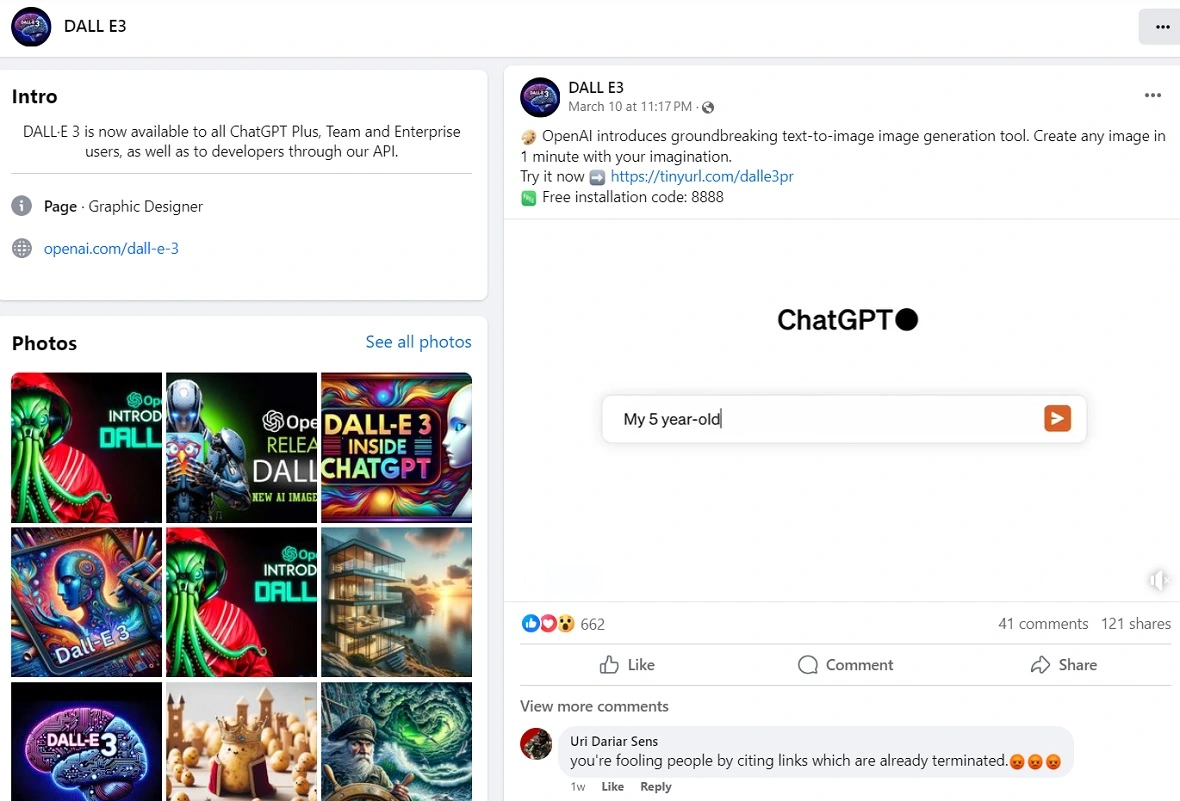
Stealers-as-a-service: The malware dealers behind the scenes
Bitdefender’s investigation showed that these fake GenAI ad campaigns are directing users to download stealers such as Rilide Stealer, Vidar Stealer, IceRAT (written in JPHP), and Nova Stealer.
All of the malware being used in this campaign is available for sale on the black market and in the underground world of the dark web, indicating that the key enablers of these attacks are criminal groups. Such groups sell or lease out stealers to other attackers. As stealers-as-a-service evolves, lowering the technical bar required to launch attacks, this trend is only expected to accelerate.
Some of the malware mentioned in the Bitdefender report (Rilide Stealer, Vidar Stealer) might specifically target Windows. However, it is unknown whether criminals using malware-as-a-service models are also distributing versions that target macOS and iOS.
The investigation revealed that criminals are impersonating a wide range of GenAI brands and products, including Sora, CapCut and CapCut Pro, Gemini, and Photo Effects Pro.
As stealers that are capable of breaching Google Chrome, Opera, Brave, and Microsoft Edge to target browser data, these malware kits can monitor online behavior, capture browser history, steal login credentials, and even withdraw crypto funds by bypassing 2FA through script injections.
The bottom line and how to stay safe
At the time of this writing, most of the fake social media accounts used for the massive distribution of malware on Facebook were still active.
Moonlock also found that fake websites that impersonate top AI brands are also still up and running and have not been shut down, nor are they flagged as “dangerous sites” by browsers.
Social media companies, including Meta, are failing in their responsibilities to protect users from malicious ads run by cybercriminals. As new stealers continue to emerge, the best protection users have is prevention.
Users should only download GenAI and other technologies through official channels and official stores. Following a link from a Facebook ad, a Google ad, or even search engine results can have serious consequences, placing victims just one click away from losing control of their data, security, and privacy.
Moonlock recommends that users not follow links in ads. Always verify URLs before visiting sites, and never download popular software through unofficial channels.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Meta Platforms, Inc. Facebook is a trademark of Meta Platforms, Inc. DALL-E is a trademark of OpenAI. Midjourney is a trademark of Midjourney, Inc.






