Malware in the form of fake Google Chrome updates is nothing new. In fact, they have existed for years. Despite Google’s efforts to block these cybercriminal campaigns and the work the cybersecurity community does to track and expose these types of attacks, they continue to persist.
On October 25, Sucuri researchers revealed a prolific new malware variant in the form of a fake Chrome update. The variant, dubbed “FakeUpdateRU” by Jerome Segura from MalwareBytes, is infecting a wide range of websites posing as legitimate Google Chrome update sites.
Fake browser update copycats and new attacks
Fake web browser updates represent one of the most common types of malware for a reason. Who wouldn’t click “Update” if a Chrome notification popped up with a new version?
As with any trojan, fake web browser malware poses as an official organization to convince users that it is in their best interest to download or update an app. Behind this apparently beneficial and harmless update, cyber criminals hide malware. This allows them to gain access to devices and deploy spyware, ransomware, and other malicious software.
Some variants of Chrome update malware, such as SocGholish, are so efficient that other cybercriminal organizations copy them to create their own versions.
Sucuri assures that FakeUpdateRU (RU for Russia) seems to be a “competing/parallel group of threat actors.” This is just one of several SocGholish copycat groups that have emerged in the past months. The trend implies that these types of malware variants will continue to increase and persist in the wild.
What do FakeUpdateRU attackers want?
Researchers say that FakeUpdateRU is a remote access trojan (RAT) that belongs to the Zgrat and Redline Stealer malware families. These malware families are linked to a wide range of ransomware attacks.
The bad actors behind this new Chrome fake update malware are motivated by money, plain and simple. And, of course, this money is illegally obtained.
The way this attack unfolds is simple:
- Users are directed to a fake Chrome browser update landing page.
- Victims click on Update, triggering a ZIP file download.
- The download is unzipped. When executed, it infects the device.

Look out for this fake Chrome landing page
The criminals behind the FakeUpdateRU attacks have designed a fake Chrome malware update page that appears to be exactly the same as the one Google hosts for users who want to download the browser.
The reason it looks so convincing is that attackers have simply saved the official Google page and slightly modified it. Attacks investigated so far show that bad actors originally saved the HTML code from the UK English version of Google’s website.
Once attackers save the HTML page (which is easy for anyone to do), they simply replace the word “Download” in the button section with the word “Update.” Then they change the wording below for the page to read, “To continue you need to update your browser,” and, “The site uses the new chromium engine, to continue it needs to be updated.”
The Update button on the fake Chrome page hides JavaScript code that will kickstart the malicious download if a victim clicks on it.
Both the fake Chrome update page and the download files that the Update button triggers are hosted on different hacked websites without the knowledge of the website owners.
If you access these fake malware pages using Firefox, Safari, or any other browser, you still get a fake Google page. The page shows that FakeUpdateRU attackers are just getting started. Fake web browser update variants tend to evolve and be customized to show different content depending on what browser is being used to access them.
Signs and warnings you should not ignore
The first thing that users need to understand is that Chrome updates are automatic. Google explains that Chrome updates will apply automatically when you close and reopen the browser. This means that Google will never send you an email, notification, or push request for you to perform an update. And Google will certainly not offer users Chrome updates while they are browsing online.
Second, users need to pay close attention to the URL and the content of any website that is asking them to update their web browser or any other plugin, app, or software. In this specific attack, criminals are redirecting users to hacked sites. There, they host a fake Chrome update page with links to several domains to download the bogus update file.
These domains include:
- chromiumengine[.]space
- chromiumtxt[.]space
- basechromium[.]space
- placengine[.]site
- browserengine[.]online
Taking a close look at the URL can help you prevent an attack before it happens. Always ask yourself, would Google offer me a Chrome update using this URL? Does this URL look suspicious? Does the URL have spelling errors? Or does the page have a strange address?
You can always turn to a trusted and free online URL checker — there are many excellent choices out there — to get instant insight on whether a site is dangerous or not.
Security warnings from Google Chrome
Another way to stay safe from this type of attack is to keep an eye out for Chrome warnings.
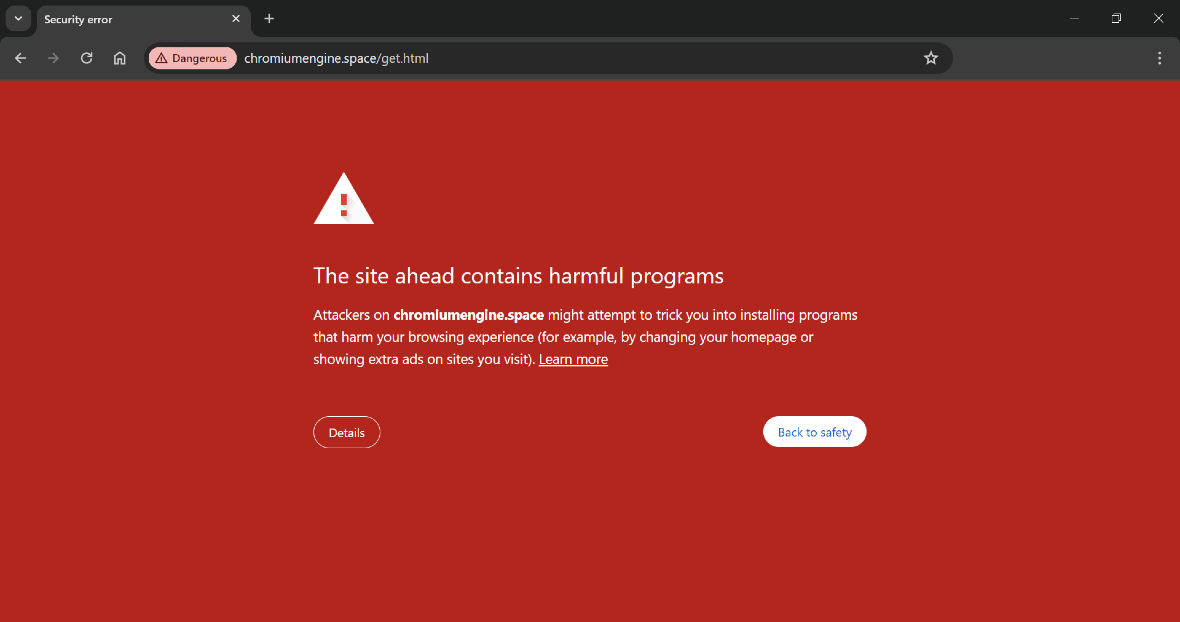
If a site is used for phishing or is designed to spread malware, there’s a good chance that Google is already on top of it. In fact, Google has already responded to some of the FakeUpdateRU attacks by rapidly blocking malicious domains. Users who visit some of these domains will see a large red Google warning sign on the website.
To better understand all the Google warnings you might get when visiting dangerous and deceptive content, let’s look at how the company phrases them.
Google Chrome warnings phrases include:
- The site ahead contains malware: This one is pretty self-explanatory. Don’t push ahead, and don’t try to access this site.
- Deceptive site ahead: This site is used for phishing, so stay away.
- Suspicious site: In other words, visit at your own risk. Google’s advice is to stay away.
- The site ahead contains harmful programs: This Google warning means that the site may host malware and is designed to trick you into installing them.
- This page is trying to load scripts from unauthenticated sources: This warning indicates another type of unsecured site.
If you get any of these warnings, the best course of action is to close your web browser.
To protect yourself against fake web browser update malware, keep the tips in this report in mind. Never download suspicious files from the web or any other media. Running a good antimalware program can also help you prevent these attacks from happening.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Google LLC. Google Chrome is a trademark of Google LLC.