A new investigation has uncovered a complex digital infrastructure used to run “pig butchering” scams across Asia and Europe, as well as possibly America.
Due to the one-to-one nature of pig butchering scams, where attackers build intimate relationships with their victims to steal their money, little is known about the fake apps used in these crimes. Now, thanks to a new report, we get a clear glimpse into this digital criminal world.
Group-IB uncovers large-scale pig butchering infrastructure
On October 2, Group-IB specialists pulled back the curtains on a large-scale operation that used fake trading apps to target both Android and Apple iOS users.
Using UniApp — a framework that allows apps to run on web browsers and, therefore, different OSs — threat actors managed to bypass strict Apple App Store security guardrails.
The malicious fake trading apps were downloaded at least thousands of times, a number that becomes serious considering that the attacks begin with spear phishing.
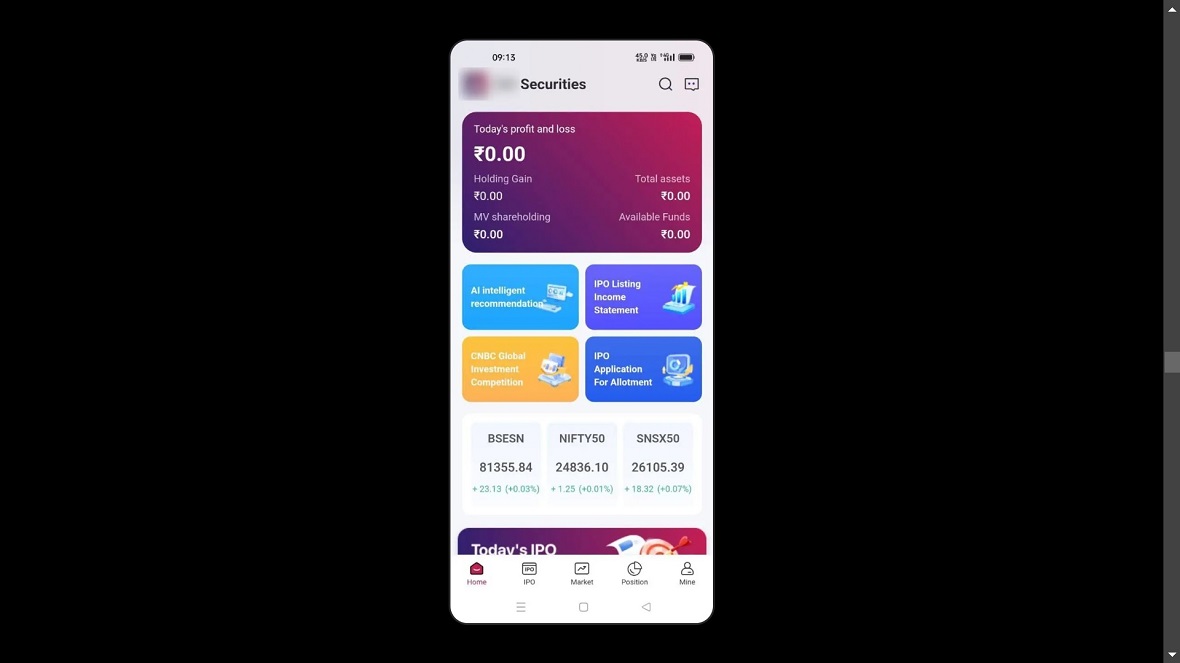
Not only were these apps distributed through the Google Play Store and the Apple App Store, but the threat group also created fake malicious websites where they offered download links.
It is unknown at the present time who is behind this criminal enterprise. The group is prolific and operates in several languages, including English, Portuguese, Chinese, and Hindi. Code examined by Moonlock on malicious domains linked to the campaign also included other languages, such as Spanish.
The motivation for these attacks is strictly financial. Due to the regions of operations and those targeted, the group may be connected to the South Asian criminal syndicates, or it could be a new player in town. Registration information shows that this group has been active since at least 2022.
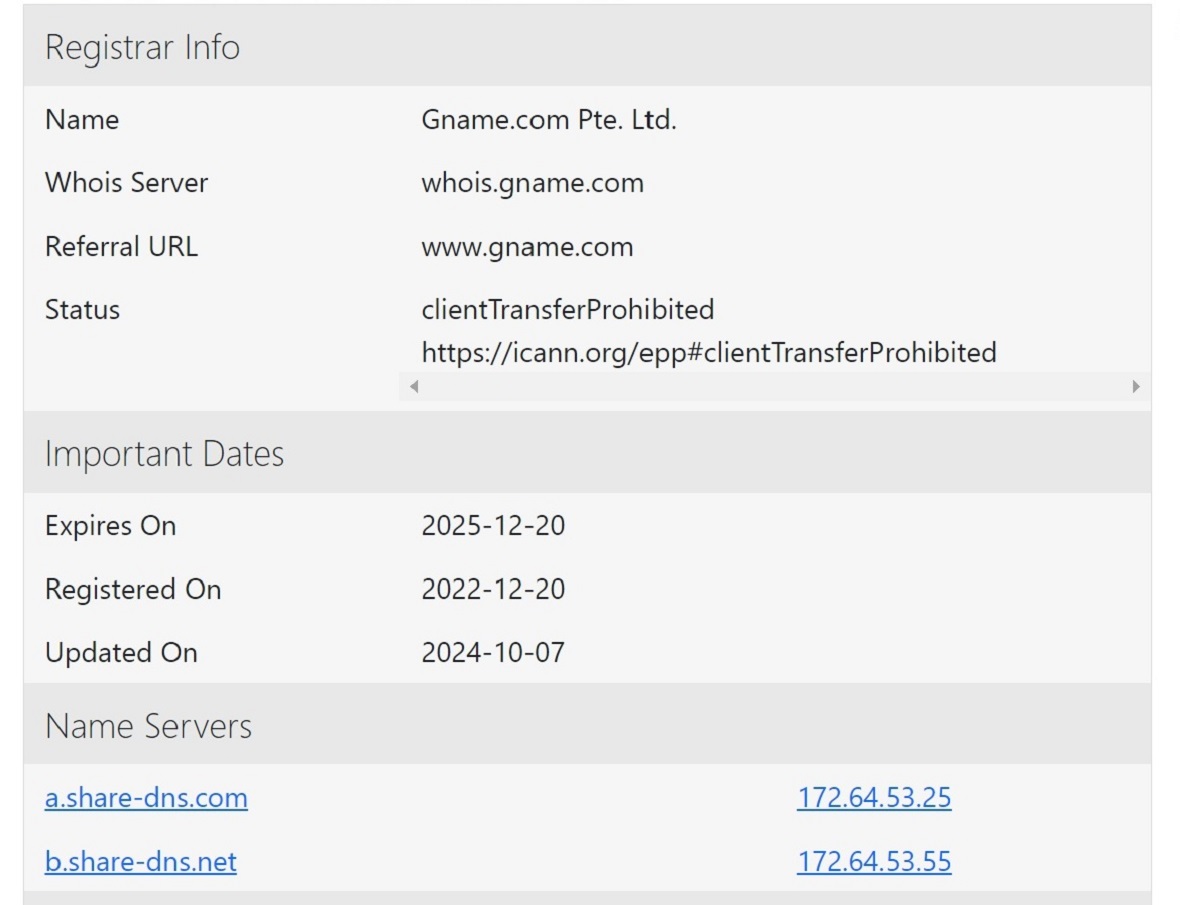
How the threat actors fooled Apple’s App Store
To trick Apple’s App Store security policies, the bad actors behind this campaign created a lightweight app that is simply designed to redirect users to the web version of the app. The app uploaded to the App Store contained no malware and flew under the radar, undetected for weeks before Apple removed it from the store.
While the app in the App Store was “merely retrieving and displaying a web-app URL” and did not present any malicious or Trojan characteristics, when this one was taken down by Apple, the group pivoted to distributing the app via malicious domains.
Additionally, the group developed apps with UniApp frameworks, meaning they can run on any Android or iOS device, as the single codebase is not in a downloaded software but runs on any web browser.
The basics of pig butchering scams
The scam in this illegal operation runs like any pig butchering scam. First, the group does research on potential targets — in this case, individuals in crypto and finance, investors, and brokers. The victim is then contacted via social media or other channels (see below). The attacker then attempts to establish a relationship with the victim.
Once a victim takes the bait, attackers introduce them to a “successful investment project.” They then redirect users to download the app via official stores or malicious domains. If the victim downloads the app and follows the attackers’ step-by-step guides, which include how to install the app by circumventing iOS built-in security features, they will be one step closer to financial ruin.
These fake trading apps are designed to put up a convincing front. The user interface shows an account balance, transfers, market movements, and blockchain assets in real-time. However, none of them are real. Victims deposit money into these apps to begin trading based on the attackers’ guidelines and quickly see big wins on their fake account balances. This incentivizes them to invest more.
This situation goes on and on until the victim wants to make a withdrawal. The victim will soon find out that making withdrawals is impossible, at which point they realize they fell for a scam.
The personal data at risk and malware capabilities
Throughout the entire process, the attackers will ask for users’ personal ID, passports, details about their work history, bank information, and bank card data. Unknowingly, users will also give away their type of mobile phone, camera permissions, and other data.
Because the apps are developed using the UniApp framework, there are few differences between what these apps do when they run on different operating systems like Android or iOS. Analysis of code done by Moonlock also showed that the app might require users to enter their screen lock password if the application finds that the screen is locked.
Compromised domains identified include:
- www.upstoxcalculator[.]com
- www.yupstocks[.]com/h5/#/login
- a.gold-blockchain[.]cc/app/home/getH5
- fxbrokers.cc
- b.gold-blockchain.cc
Most domains in this campaign are inactive or suspended, but some remain operational.
Group-IB said attackers had reached the regions of Asia-Pacific, Europe, the Middle East, and Africa.
For some reason, the threat actors used different .cc domains, which are domains for the Cocos (Keeling) Islands, a remote territory of Australia. Additionally, Moonlock found that the group leverages Chinese web hosting as well.
Another app by the same developer could be used for scams
Moonlock looked into the developer who created the fake trading app hosted on the Apple App Store: Colin Touhey.
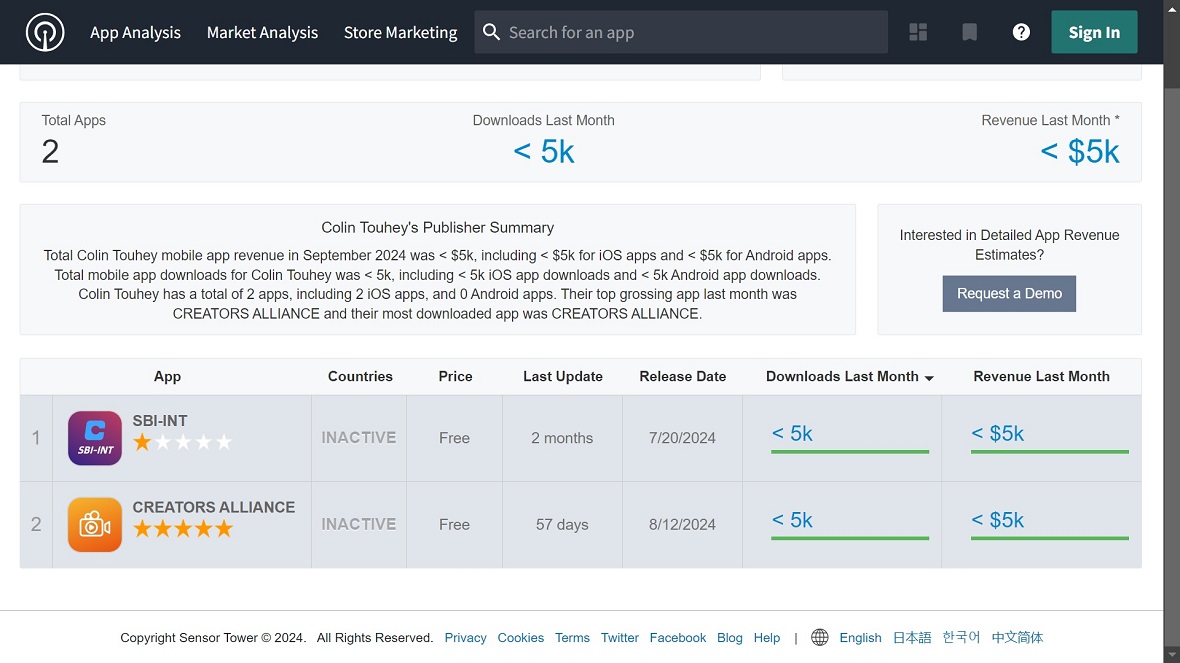
We found that besides the SBI-INT app (fake trading app), Colin Touhey also developed another app currently inactive on the App Store called Creators Alliance. Both apps have over 5,000 downloads in the past month and over $5,000 in revenue, according to analysis.
Interestingly, the app Creators Alliance was released 1 month after SBI-INT in August 2024 on the App Store. However, Creators Alliance’s presence online predates that launch.
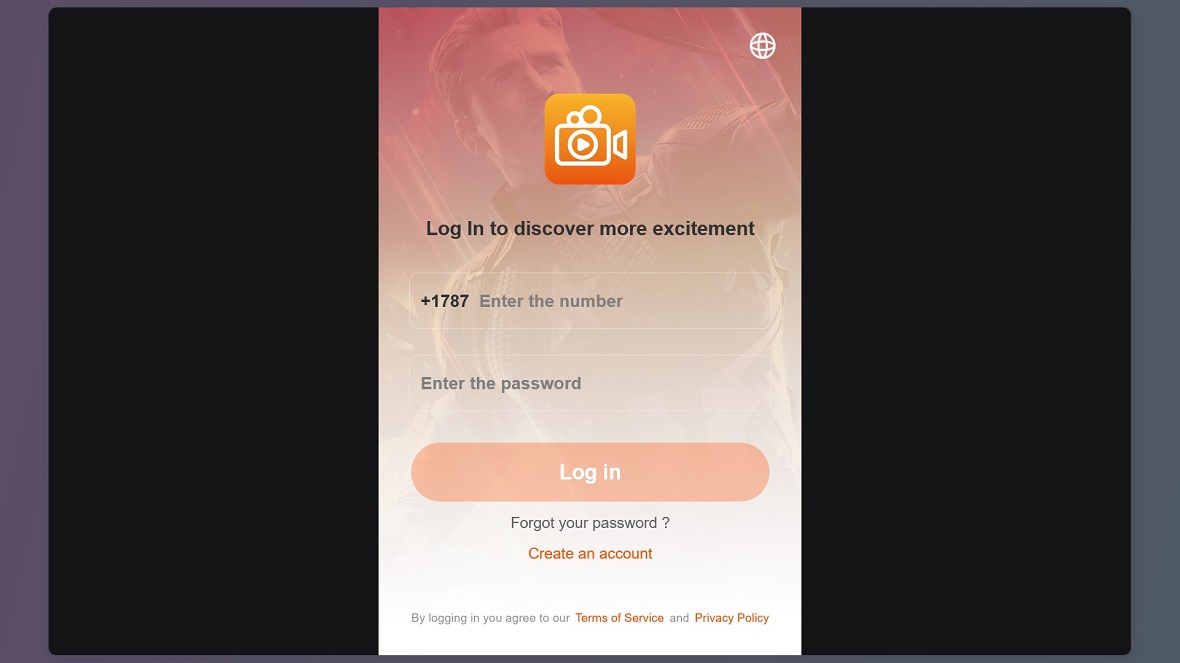
The Creators Alliance app is a type of social media app that offers several features, all ideal for criminal abuse. It also runs on a web browser, where “creators” share short videos.
Users of the app can donate USDT or Bitcoin to programs that claim to be legitimate, such as fighting poverty in Africa. Moonlock has not verified these groups or donations, but due to the lack of transparency and the connection with the existing fake trade app campaigns, they are, to say the least, doubtful.
Creators Alliance also runs a “pay to work” scheme where users pay certain fees upfront to get jobs as content creators, an issue that has led to people raising red flags on forums and social media channels like Reddit.
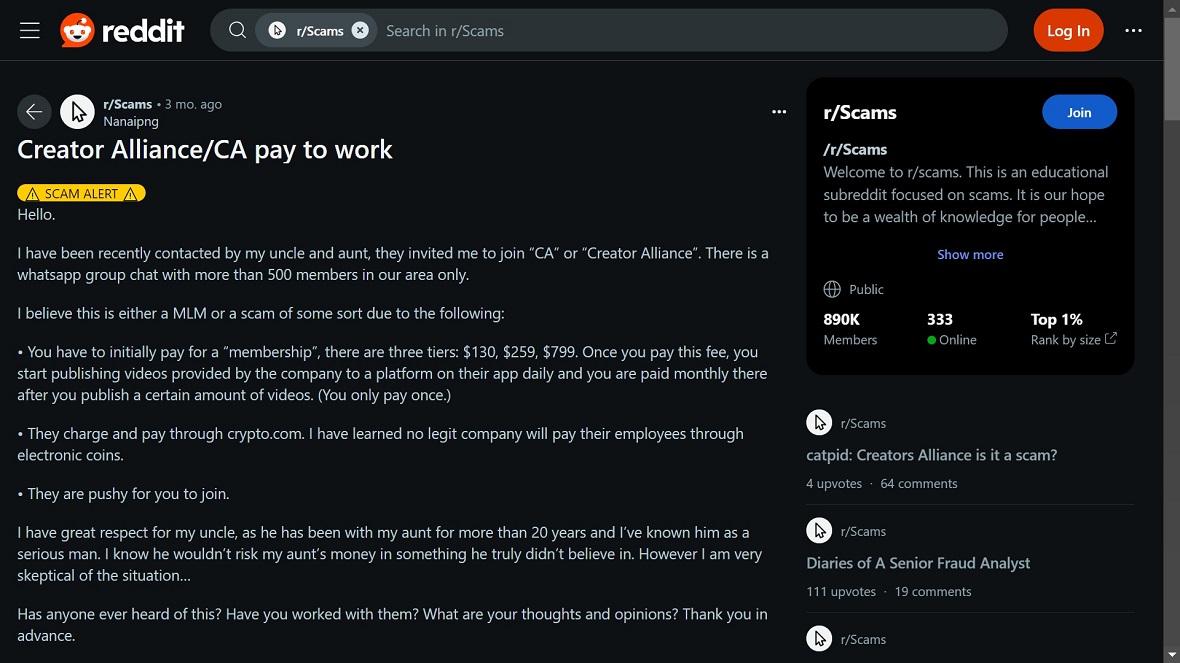
Pig butchering scams via social media
Group-IB reveals in its report that they were unable to identify exactly how the fake trading pig butchering group was contacting potential victims and assumed it was done via social media. An app like Creators Alliance — a social media app in itself — offers a perfect way to connect to specific victims and targets. By owning their own social media channels, cybercriminal groups gain an incredible advantage.
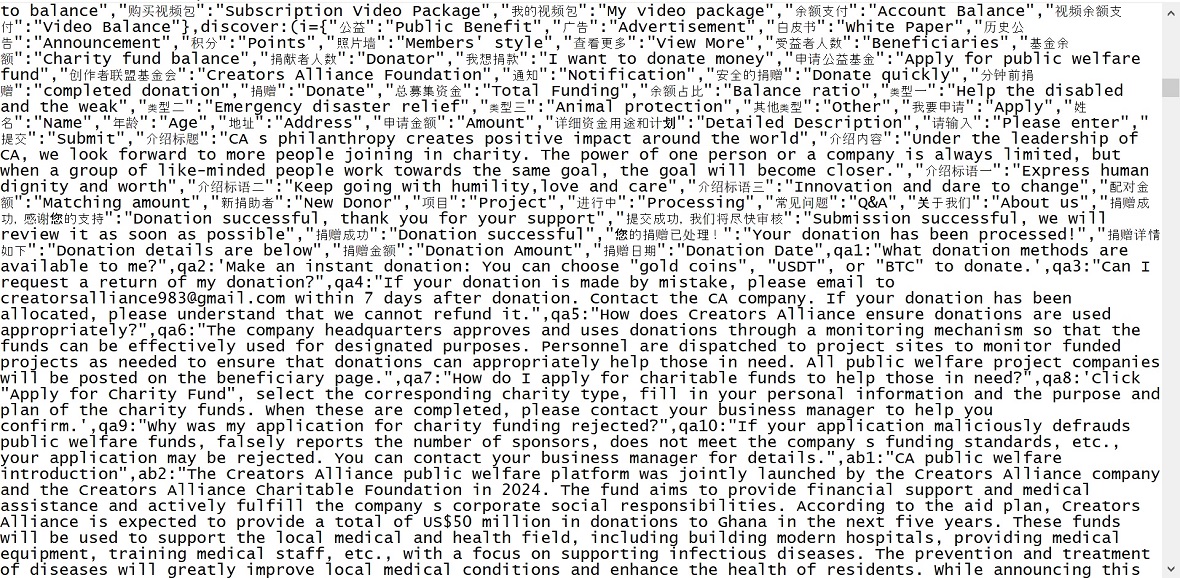
Additionally, our analysis of the code of Creators Alliance found that the app also creates a sort of pyramid-style hierarchy in which managers can recruit creators, and creators then recruit more creators. This modality may be the reason why Moonlock identified, via Facebook, a meeting of Creators Alliance in Puerto Rico — a United States territory.
Moonlock also found several generic press releases claiming that Creators Alliance had invested billions to go global. These releases were probably distributed via paid business wire press release services.
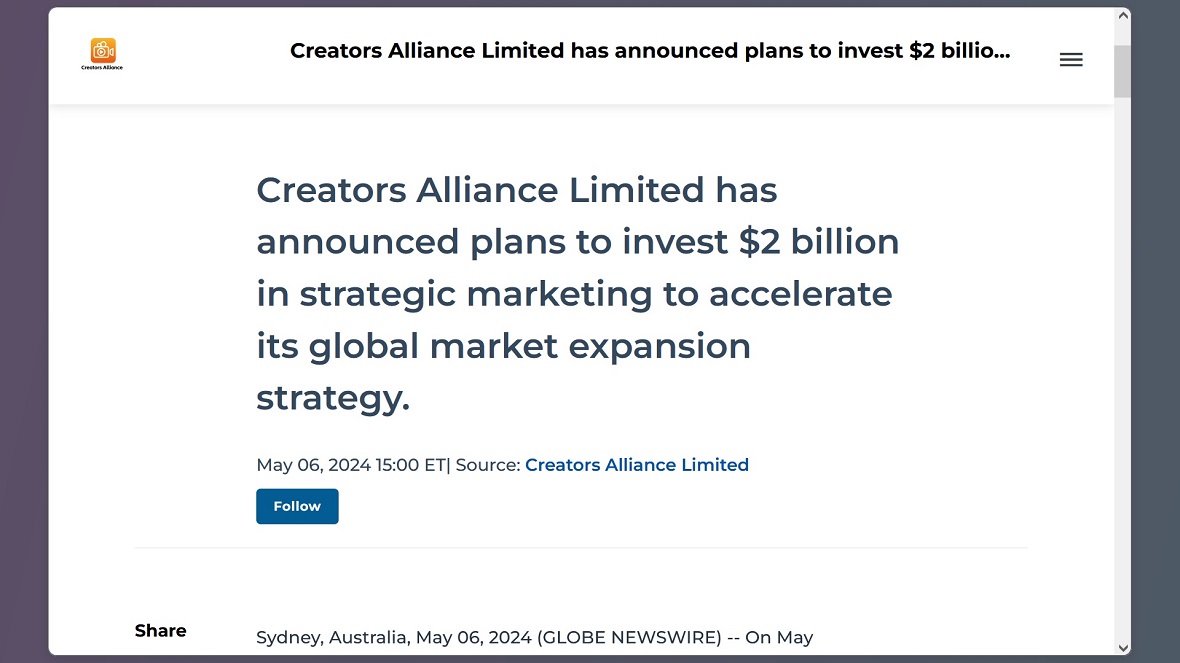
The meeting and Facebook page of Creators Alliance in Puerto Rico features documents and certifications issued by the Australian Security and Investment Commission. Moonlock was unable to verify the legitimacy of these documents, which appear to include public officials’ signatures.
To date, the Creators Alliance site is still live and operating online.
Final thoughts
Pig butchering scams are evolving and becoming more sophisticated, and this fake trading app operation is particularly unique. It not only managed to fool the Apple App Store security but also targeted iPhone and Android users alike through UniApp web-browsing apps.
Additionally, the network of this organization expands beyond Moonlock’s investigation, signifying the scale of the enterprise. It’s crucial for users to remain vigilant, be wary of unsolicited investment opportunities, and only download apps from trusted sources.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iOS and the Apple App Store are trademarks of Apple Inc. Android and the Google Play Store are trademarks of Google LLC.






