The United States Department of Justice and the FBI announced that they remotely removed Chinese-linked malware from approximately 4,258 US-based computers and networks.
The announcement comes at the conclusion of a multi-year international investigation and operation. The malware the FBI — working with French authorities — removed from American victims is the infamous and archaic PlugX malware. This malware was first seen in 2008. It has since been modified and updated exhaustively by Chinese espionage threat actors.
In this report, we look at how the FBI removed the backdoor to secure American computers. We also examine whether this type of operation is legal and why US law enforcement could take similar actions in the near future.
China paid Mustang Panda and Twill Typhoon to launch the global PlugX campaign, FBI says
The DOJ explained in its official communication on January 14 that this specific version of the PlugX malware was developed by a group of hackers supported by the People’s Republic of China (PRC), specifically the groups Mustang Panda and Twill Typhoon.
Twill Typhoon is part of the wider Typhoon family linked to China. The group has been relentlessly pounding the US for the past months, breaching telcos and the American critical infrastructure sector.
The version of PlugX these groups developed was coded to infect, control, and steal information from breached devices. In simple terms, it’s classic cyberespionage malware that aligns with Chinese tactics.
According to court documents, China paid Mustang Panda and others back in 2014. Since then, thousands of computers have been breached in the US, Europe, and Asian countries, especially where Chinese dissidents reside.
Most of the owners of the thousands of globally impacted computers were completely unaware that their system was running the PlugX backdoor.
US Attorney Jacqueline Romero for the Eastern District of Pennsylvania said, “This wide-ranging hack and long-term infection of thousands of Windows-based computers, including many home computers in the United States, demonstrates the recklessness and aggressiveness of PRC state-sponsored hackers.”
A technical rundown on remote backdoor removal
A major question needs to be answered. How did the FBI manage to remotely delete the Chinese backdoor from thousands of American computers? The answer to this one is actually very interesting.
An affidavit released by the DOJ reveals that FBI agents had been investigating global PlugX operations for some time. The evidence they gathered revealed that the campaign allegedly violated the Computer Fraud and Abuse Act, 18 U.S.C. § 1030(a)(5)(A) (damage to protected computers).
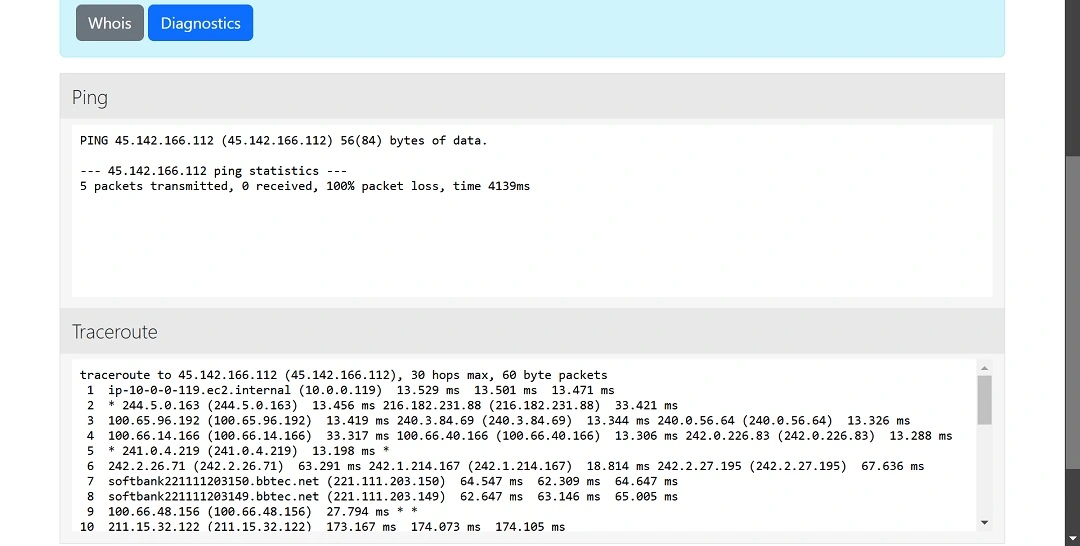
The FBI identified the IP address 45.142.166.112 as the C2 attacker-controlled server that devices infected with this PlugX version were communicating with and exfiltrating data to.
“Since September 2023, at least 45,000 IP addresses in the United States have contacted the C2 server assigned IP address 45.142.166.112,” the FBI agent says in the affidavit.
This is the part of the story where the FBI “got lucky.”
French company deploys sinkhole and takes control of PlugX’s IP and C2 commands
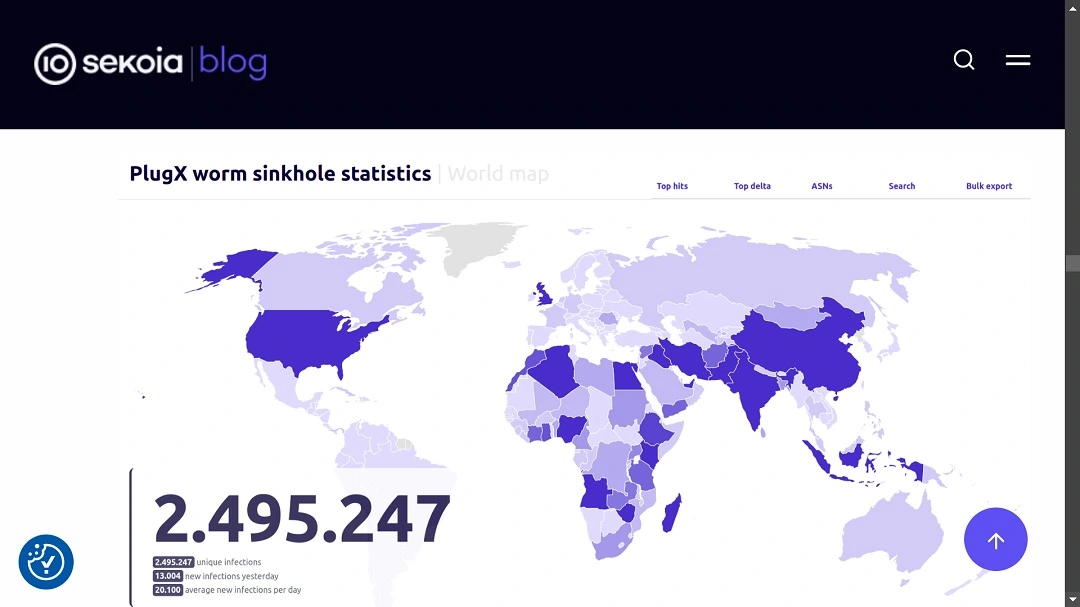
In 2023, the French cybersecurity company Sekoia announced that it had successfully “sinkholed” the PlugX-linked command and control server. A sinkhole is a server or system used to intercept and redirect malicious traffic.
Sekioa said that for just $7, they acquired the unique IP address tied to a variant of PlugX. They then began redirecting traffic from PlugX-breached computers to the sinkhole IP they deployed.
The French company not only found that hundreds of thousands of IPs across the world were affected, but while investigating the cryptography of PlugX’s communications, they hit gold. Sekoia researchers found a way to send PlugX commands to the infected computers and run self-delete commands.
However, because Sekoia saw too many legal problems with remotely deleting this state-sponsored backdoor from infected devices, they notified each affected country.
Sekoia contacted top national computer emergency response teams (CERTs), law enforcement agencies (LEAs), and cybersecurity authorities in the affected regions. This is how the FBI got word that PlugX could be wiped.
An FBI international operation led by French law enforcement and Sekoia was set in motion.
“Working with these partners, the FBI tested the commands, confirmed their effectiveness, and determined that they did not otherwise impact the legitimate functions of, or collect content information from, infected computers,” the DOJ said.
French law enforcement, gaining access to the C2 server, sent commands to devices connected with the assigned IP address, 45.142.166.112.
“The FBI has tested this self-delete command and has confirmed that it does not affect any legitimate functions or files on the TARGET DEVICES, nor transmit any content information from the TARGET DEVICES,” the FBI said in the affidavit.
A new PlugX malware version
The PlugX malware is not your typical backdoor. The variant in this threat campaign has worm components, allowing breached devices to infect other devices via USB.
Once the backdoor is installed, it establishes stealth and persistence. The backdoor connects to the C2, where it receives commands. While establishing contact with a C2 is common for many types of malware, including those used by criminals motivated by money, this version is designed for espionage, not financial heists.
It is unknown what exactly the Chinese threat groups were attempting to achieve or what their target was with this widespread digital espionage campaign. The DOJ and the FBI have not released any information regarding the victims targeted, nor whether they belong to or are related to a specific sector like the government.
PlugX is a modular malware that calls back to a C2 server, gathers machine information, performs screen captures, and manages services and processes. Additionally, it seeks to obfuscate its activities by performing actions like modifying the characteristics of folders to hide them.
Experts explain that the PlugX source code has been around for so long that modified versions of the source code are easily accessible to anyone online.
Was the FBI’s PlugX operation by the book? The legality of remotely wiping malware
How legal is it for law enforcement to wipe malware from your computer, even when it does not impact any part of the system or data? The legality of this issue depends on the jurisdiction and specific circumstances. In this particular case, the FBI seems to have checked all the right boxes, moving forward with court-approved warrants.
“In August 2024, the Justice Department and FBI obtained the first of 9 warrants in the Eastern District of Pennsylvania authorizing the deletion of PlugX from US-based computers,” the FBI said.
The FBI and DOJ’s operation to delete the PlugX malware was legal because it was conducted under court-authorized warrants, ensuring compliance with US laws, including the Fourth Amendment.
These warrants specifically targeted infected systems, allowing only the removal of the malware without accessing personal files or collecting additional user data.
Authorities say the operation was necessary to protect US victims from the ongoing threat posed by state-sponsored hackers, particularly Mustang Panda, who used PlugX to control computers and steal sensitive information.
The FBI also provided notice to US owners of computers affected by the court-authorized operation.
Why we might see similar FBI and DOJ operations against Chinese-supported hackers
The Trump administration has signaled its clear intention to impose harder restrictions and sanctions against China and Chinese-linked threat actors who seek to disrupt critical infrastructure and national security systems.
As the dust of the Salt Typhoon attack against American telcos settles, the DOJ-FBI operation sends a zero-tolerance message to Chinese-backed hackers.
“The FBI worked to identify thousands of infected US computers and delete the PRC malware on them,” Special Agent in Charge Wayne Jacobs of the FBI Philadelphia Field Office said.
“The scope of this technical operation demonstrates the FBI’s resolve to pursue PRC adversaries no matter where they victimize Americans,” Special Agent Jacobs said.
Final thoughts
In an unusual move, the FBI, working with international partners, took a bold, proactive step in offensive security. Instead of chasing down the responsible actors to impose sanctions, shut them down, or confiscate malicious infrastructure, they simply went ahead and remotely deleted the espionage malware at a large scale.
This operation is one of a kind, sets a strong precedent, and is a demonstration of the reach of international law enforcement powers in their fight to disrupt Chinese global cyber espionage campaigns.






