FIN7, a Russian-linked cybercriminal organization active since 2013, has reemerged with new global capabilities. The group, like other cyber gangs, is leveraging the popularity of generative AI to lure victims.
FIN7 threat group modernizes to leverage AI and honeypots
On October 2, Silent Push cybersecurity researchers warned that the threat group FIN7 had created new domains to host honeypots with malicious AI DeepNude generators. The experienced group, historically linked to thousands of malicious domains used in spear-phishing emails, phishing kits, and malware campaigns, is taking a sophisticated approach.
FIN7 is using a new artificial intelligence (AI) “DeepNude Generator” in its attacks, with 7 domains already linked to them.
Silent Push researchers found that the group is using at least 2 versions of AI deepfake nude malware honeypot techniques. One requires a simple download, while the other has a more complex social engineering “free trial” deception technique.
![Screenshot of Nude[.]ai, one of FIN7 many malicious sites hosting honeypots.](https://moonlock.com/2024/10/honeypot.jpg)
FIN7 is also continuously serving remote access trojan malware distributed under fake ads (malvertising) and using the classic “Browser extension required” trick to load honeypots and malware, including infostealers and ransomware.
Why are cybercriminals using honeypots?
“Honeypot” is a term exclusive to cybersecurity teams. As the name implies, honeypots are digital resources that are intentionally left vulnerable and are designed to look valuable on purpose to attract attackers. Once a hacker gets into a honeypot, they can be tracked and monitored by security teams, and their devices may even be remotely controlled.
Most respected cybersecurity professionals tend to stay away from using honeypots as defense tools due to ethical concerns. Due to their aggressive nature, honeypots blur the lines between criminal behavior and legal, professional tools.
Silent Push explained that they used the term “honeypots” to refer to the “technical minefields that have carefully crafted lures used by bad actors to bait their unsuspecting victims, as opposed to traditional decoys and detection mechanisms.”
As the new FIN7 report reveals, honeypot techniques can be incredibly useful for cybercriminals who do not have a moral compass.
How FIN7 runs its attacks
As mentioned, FIN7 uses a wide range of techniques, fake domains, and malware to execute large-scale attacks, casting a wide net.
Impersonating browser extensions
The criminal group FIN7 delivers NetSupport RAT malware to victims who land on their fake sites after being lured by fake ads (malvertising).
NetSupport Remote Administrator (RAT) is a remote access software that allows users to control and manage other computers remotely. While it can be used for IT support, troubleshooting, and remote administration, malicious actors love it because it can control devices from any distance.
The way FIN7 loads malware and RATs varies. In one known technique, when a potential victim lands on a fake FIN7 domain, a popup emerges informing them that a “Browser Extension (is) Required.” These types of automatic push notifications can be easily mistaken by victims as legitimate requirements for their systems.
Not surprisingly, those who do agree to install the browser extension are loading malware, specifically malware in the .MSIX format — a type of software package created by Microsoft.
When executed, malicious code packed in MSIX format can install other malware, take control of a system, and damage files or systems.
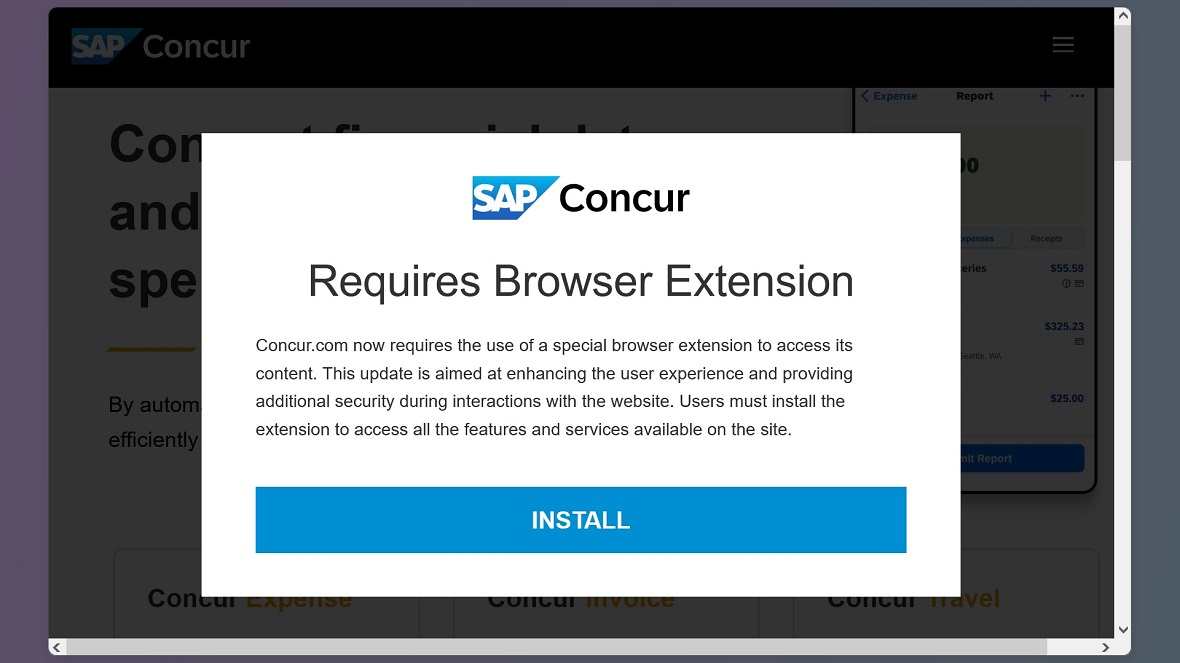
Silent Push researchers found that FIN7 is targeting a variety of brands, including SAP Concur, Microsoft, Thomson Reuters, and FINVIZ stock screening.
“FIN7 still has active IPs — and likely new websites — that are pushing the required browser extension ploy,” Silent Push researchers warned.
The .MSIX browser extension used by FIN7 searches for “workgroup computers” when it loads. This means it is targeting company environments. If the breached machine is in a workgroup, the script extracts 2 encrypted 7-Zip archives and runs an executable NetSupport RAT for remote control. FNI7 has also been observed deploying ransomware in these instances.
FIN7 AI deepfake nude honeypots
Like many cybercriminal gangs, FIN7 is also trying to leverage the popularity of generative AI. However, unlike other cybercriminal groups that impersonate ChatGPT or MidJoureny, this group is delving into the adult content AI industry.
FNI7 has created several domains to trick users who are looking for adult-themed AI generators online. The targeting of this specific population group is not coincidental, as a level of psychological extortion can play out in their favor.
Under these sites, FIN7 uses 2 techniques, “Free Download” and “Free Trial,” the second being more sophisticated than the first.
In the Free Download tactic, when a potential victim visits an AI nude generator website that FIN7 controls, they will be offered a free download. Clicking and downloading this file installs malware on the device.
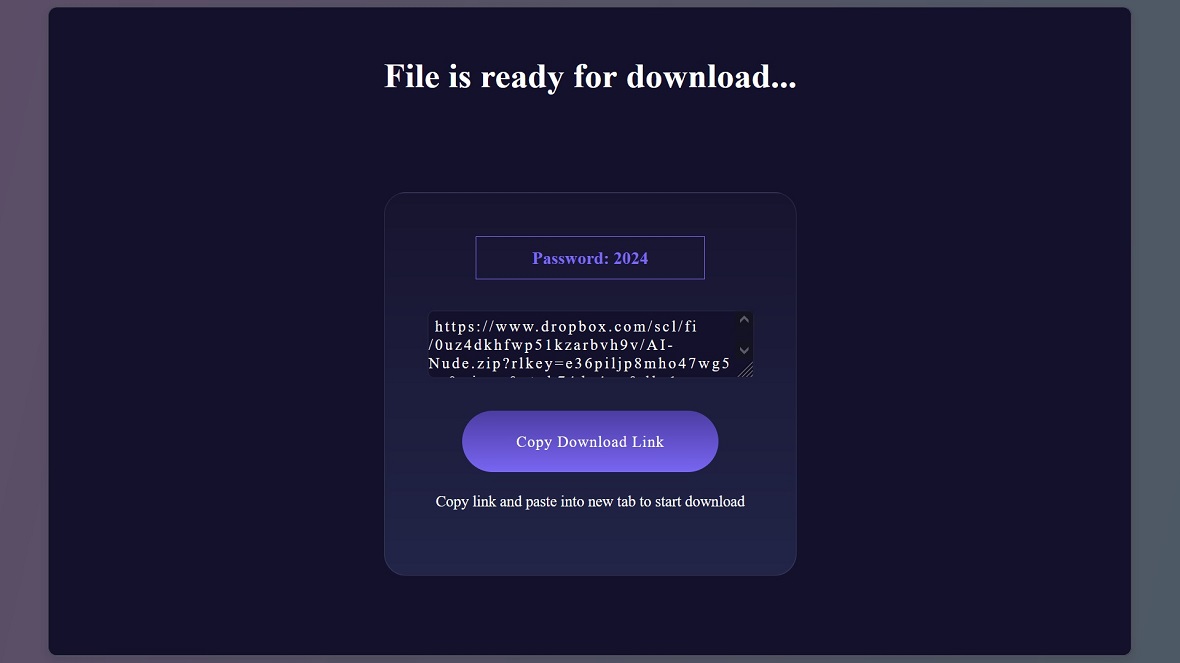
The malware used in this campaign includes different infostealers that can steal cookies, passwords, and other data.
The details on how FIN7 operates
Domains identified as operating under FIN7’s control include aiNude[.]ai, easynude[.]website, ai-nude[.]cloud, ai-nude[.]click, ai-nude[.]pro, nude-ai[.]pro, ai-nude[.]adult, and ainude[.]site.
While all these sites have been taken down, other websites are believed to still be operational, as they have not been identified.
Interestingly, FIN7 builds these malicious AI nude deepfake generator sites on top of existing aging sites, known as “shell websites.”
The second version of FIN7 is the “Free Trial” technique. Some of the deepfake AI nude domains have a Free Trial button on the homepage. When users click on this button, FNI7 runs a simulation of the AI deepfake generator. After being asked to upload an image to the AI deepfake nude generator as a prompt, they are offered a link and a download. Inside the download, the infamous Lumma Stealer is concealed.
Besides malvertising, the criminal gang is also using SEO tactics. They are creating content designed to rank high in web search engines such as “Best Porn Sites” web pages. These SEO pages redirect users to the malicious AI deepfake nude generator online sites.
FIN7 honeypots are dangerously rich in resources and scale. They include the use of legitimate software and resources, and they leverage social engineering, malvertising, phishing, remote controllers, and infostealers that include REdline, D3D3F@ck Loader, and the Lumma Stealer. By grouping these tools, FIN7 can connect to remote servers, detect corporate and virtual environments, and take over execution controls.
Additionally, the group is impersonating PuTTY, Razer Gaming, Fortinet VPN, Fortnite Video Game Cheat, Zoom, Cannon, and other brands and resources.
Mitigation: How to protect yourself against FIN7
Companies or individuals that operate advanced security tools can integrate known domains, IPs, hashes, and other indicators of compromise linked to FIN7 — compiled by Silent Push or other cybersecurity organizations into their frameworks — to block access to sites and elements already identified as malicious. Incorporating this type of data into technology stacks is critical to ensure security.
As an individual, you can also take several steps to mitigate the risk of FIN7 attacks. The online adult content industry is ripe with malicious actors. Understanding this simple truth can go a long way.
Additionally, never download software, free trials, or free downloads from untrusted and suspicious sites. When looking for known software or apps like Zoom or open-source resources like PuTTY, make sure you download them from legitimate app stores or websites.
Always keep your device up to date with the latest security updates, which technology providers develop to patch up the latest threats. Enabling MFA on your most important accounts is also important. As FIN7’s ultimate goal is to steal your money, an MFA on your accounts will alert you if anyone has, for example, stolen your password and is trying to access your accounts. Biometrics MFA is believed to be the most secure method of authentication despite not being 100% uncrackable.
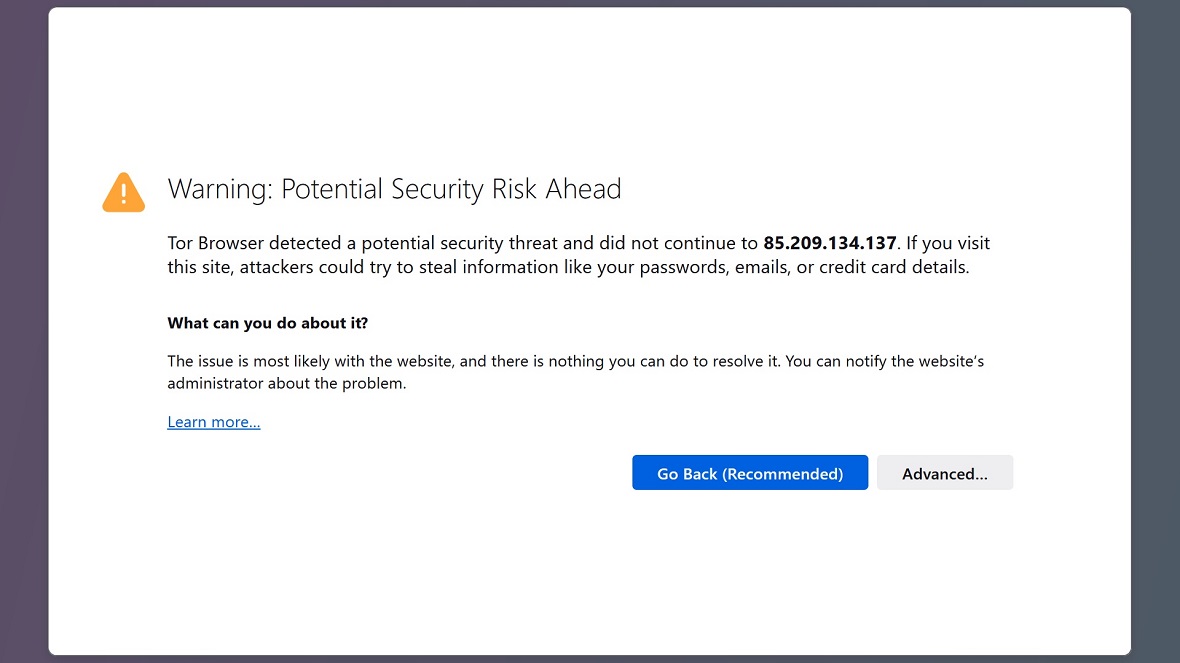
Finally, pay attention to web browser warnings and red flags, and never underestimate the capabilities of threat actors like FIN7.