It is widely accepted that the next couple of months will be critical for geopolitics. With landmark EU, UK, and US elections all happening this year, the days to come will not only shape the future of the Russia-Ukraine war, but Eastern Europe and European policies for the next decade. Consequently, these elections have caught the attention of Russia and its cyber intelligence agencies. These agencies wage cyber warfare in the region, seeking to influence agendas. But politics and elections aren’t the only things Russia is keeping a close eye on.
As Putin takes a more aggressive military approach to Ukraine, renewing attack efforts on new battlefronts, a fresh wave of weapons for Ukraine from NATO and the US has Russia scrambling for intel — especially with President Joe Biden’s approval of the use of American arms for strikes inside Russia.
Russia’s GRU on the hunt for weapons import intel
On May 30, Recorded Future Insikt Group, a team of veteran threat researchers, revealed that GRU’s BlueDelta deployed a new operational infrastructure. GRU, also known as the Chief Intelligence Office, is Russia’s foreign military intelligence agency. While the goal of this operation was defined as “military espionage,” it remains unclear what the specific objectives of this new campaign are.

BlueDelta is going after European, Eastern European, and Ukrainian targets using a sophisticated combination of techniques, from geofencing to information-stealing Headlace malware, credential-harvesting fake web pages, phishing, and more.
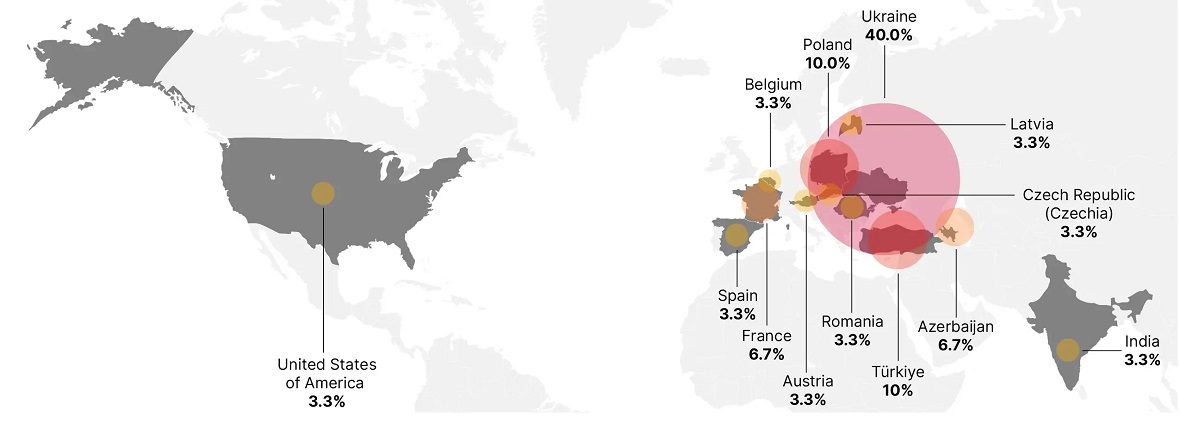
So far, 13 countries have already been targeted under this warfare campaign. Ukraine, at the top of the BlueDelta attack lists, accounted for 40% of all the activity identified. Other countries include Spain, France, Poland, Romania, the US, the Czech Republic, Romania, Austria, Turkey, and Azerbaijan.
Looking at a regional map, it’s impossible not to notice that most of the targeted countries surround Ukraine or are directly or indirectly involved in the arms and aid package routes.
Who is BlueDelta?
BlueDelta is a GRU-affiliated hacker group, part of Russia’s ever-evolving cyber warfare infrastructure.
BlueDelta is also known as or linked to APT28, Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422. All are considered advanced persistent threat (APT) groups affiliated with Russia’s strategic military intelligence unit, the GRU.
Irina Tsukerman, a national security and human rights lawyer and President of Scarab Rising, Inc., spoke to Moonlock about BlueDelta.
“BlueDelta is the cyber espionage unit of the GRU,” Tsukerman said. “Its modus operandi is multi-phase campaigns, usually targeting Europe.”
The sabotage of EU railways to shape global logistics
The power and capabilities of DeltaBlue should not be underestimated. As Tsukerman explained, the group is “particularly infamous for its hacks of the European railways.”
“It’s important to note that such operations are closely coordinated with the rest of Russia’s foreign policy and geopolitical strategy,” Tsukerman said.
“The timing of the European railway hacks was not random or coincidental,” Tsukerman explained. “It was closely linked to the Houthi attacks on the maritime routes in the Strait of Hormuz and the Indian Ocean, which in turn undercut the European collaboration with India and the Middle East (the IMEC corridor, aka the Spice Route), backed by the US, which would have provided economic alternatives to China-backed initiatives.”
The result was that India moved most of its shipments via railways in Russia instead, joining the North-South Corridor. These developments disrupted Europe’s economic projects while benefiting Russia.
Simultaneously, the hacks were used to also disable European railways, disrupting the supply chains for key products even more.
Blockades and corridors for import and export
“Right now, the ‘only’ alternative to the Black Sea blockade is a new corridor opened in the fall of 2023, which runs along the Western coast of the Black Sea,” Tsukerman said. “The US has helped Ukraine develop temporary alternatives via the Danube River. US shipments are generally delivered overland, but the existing corridor runs next to Bulgaria and Romania and is considered NATO-controlled territory, which protects Ukrainian ships from direct attacks.”
Corridors are fundamental for Ukraine to find ways around ongoing blockades (of grains and other imports/exports). They allow the country to export and import products to and from Africa and the Middle East, including Israel and Egypt.
Tsukerman said that Russia’s goals are twofold. First, to gather intelligence on any potential arms deliveries or other technologies that could be reaching Ukraine. Second, to disrupt the additional avenues of grains and other product deliveries to prevent Ukraine from getting aid.
“These cyberattacks are part and parcel of Russia’s economic warfare against Ukraine and anyone doing business or helping it,” Tsukerman said.
These cyberattacks are part and parcel of Russia’s economic warfare against Ukraine and anyone doing business or helping it
Irina Tsukerman, President of Scarab Rising, Inc.
BlueDelta is harvesting credentials from Ukrainian military import-export firms
The Ministry of Defense of Ukraine, as well as European transportation infrastructures, were also part of the BlueDelta action.
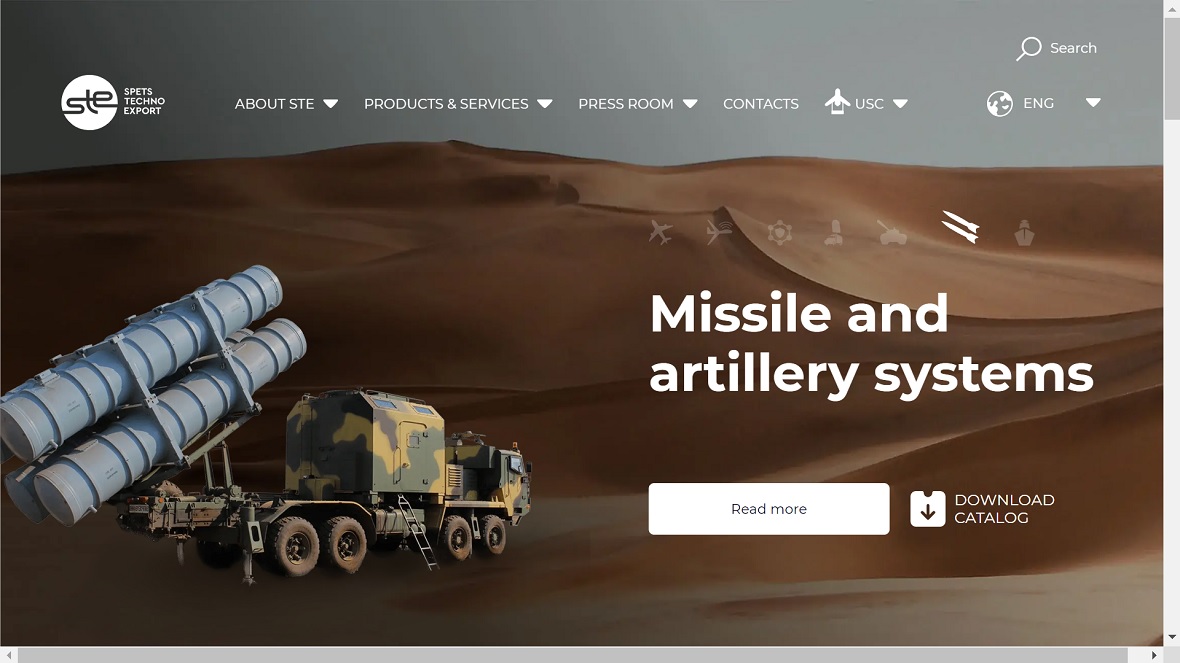
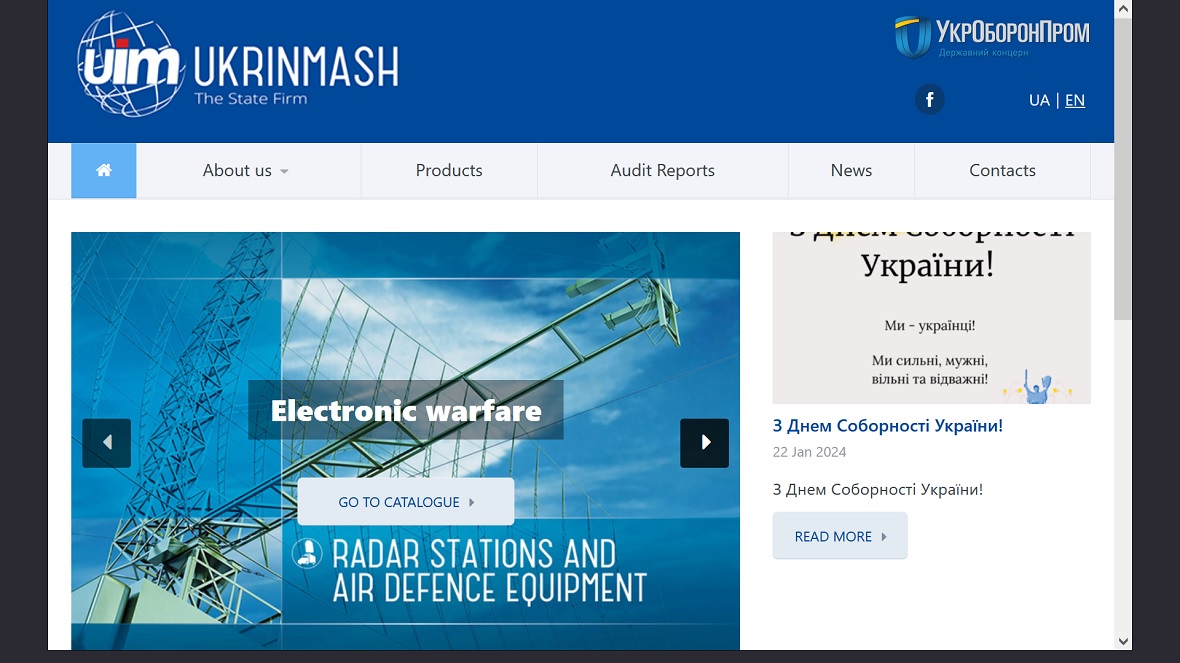
Additionally, and more concerningly, GRU BlueDelta hackers targeted and created credential-harvesting pages linked to importers and exporters of military goods and services based in Ukraine.
These include the State Enterprise Company Specialized Foreign Trade Firm PROGRESS, the State Foreign Trade Enterprise SpetsTechnoExport, and Ukrinmash, an official Ukrainian importer and exporter of military goods and services.
“BlueDelta’s objective is to acquire intelligence that bolsters Russia’s military endeavors in Ukraine and gather insights into geopolitical dynamics in neighboring nations and NATO member states,” researchers from Insikt Group said in the press release.
“The adaptability, skill, and ferocity demonstrated in this report will continue at pace as Russia tries to capture intelligence, which gives it an edge on the battlefield and regarding geopolitical interests,” Insikt Group warned.
The infiltration of networks linked to Ukraine’s defense ministry and European railways could give BlueDelta access to intelligence that might shape battlefield tactics and overall military strategies.
What military classified information is the group after?
The targeting of military import-export firms in Ukraine could signal an effort by Russia to obtain details on military aid packages.
It is common knowledge that countries like the US send weapons, ammunition, and other military resources to Ukraine. However, the specific route of the cargo deliveries is considered part of a sensitive military logistics operation. For security reasons, specific routes, schedules, and quantities of military equipment are frequently classified information. This helps prevent adversaries from intercepting supplies or planning attacks.
Even public announcements like those made by the US Department of Defense do not reveal the full details, logistics, or technical specifics regarding shipment. Transportation routes are likely omitted for security reasons. And open-source public information cannot be used to pinpoint exact routes or types of armaments.
Despite public lists of weapons shipped, advanced weaponry and modern military equipment frequently incorporate sensitive technology or capabilities that other countries would like to learn about. These are also usually kept a secret.
Weapons with classified components also require restricted information, even if the general type of weapon is known (e.g., missiles, drones), specific models or variants might have classified features. Disclosing this information could compromise operational security.
Is this the information that BlueDelta and Russia seek to get their hands on? And is it why military import and export organizations in Ukraine are being targeted?
What is the Headlace malware?
From April to December 2023, GRU’s BlueDelta deployed the Headlace malware infrastructure. Headlace is a multi-component malware that includes a dropper, a VBS launcher, and a backdoor.
This backdoor malware usually breaches devices, networks, or systems, luring victims through phishing attacks that tend to impersonate legitimate organizations. Headlace is also an information-stealing malware, meaning it aims to steal sensitive data from compromised systems.
This isn’t the first time Russian-linked hacker groups have used Headlace. Recently, on May 8, 2024, ATP28 was used in a cyberattack campaign that targeted Polish government institutions.
On November 8, 2023, IBM X-Force found that the Russian group ITG05 also used Headlace malware against targets based in at least 13 nations worldwide. Their goal was to acquire intelligence on United National Human Rights Council members. In that campaign, attackers sent out phishing content about human rights related to the Israel-Hamas war as the main bait.
The BlueDelta infrastructure
The BlueDelta infrastructure is evolving and adaptable. BlueDelta’s ongoing development of its infrastructure indicates a sophisticated and agile threat actor rich in resources.
Key components:
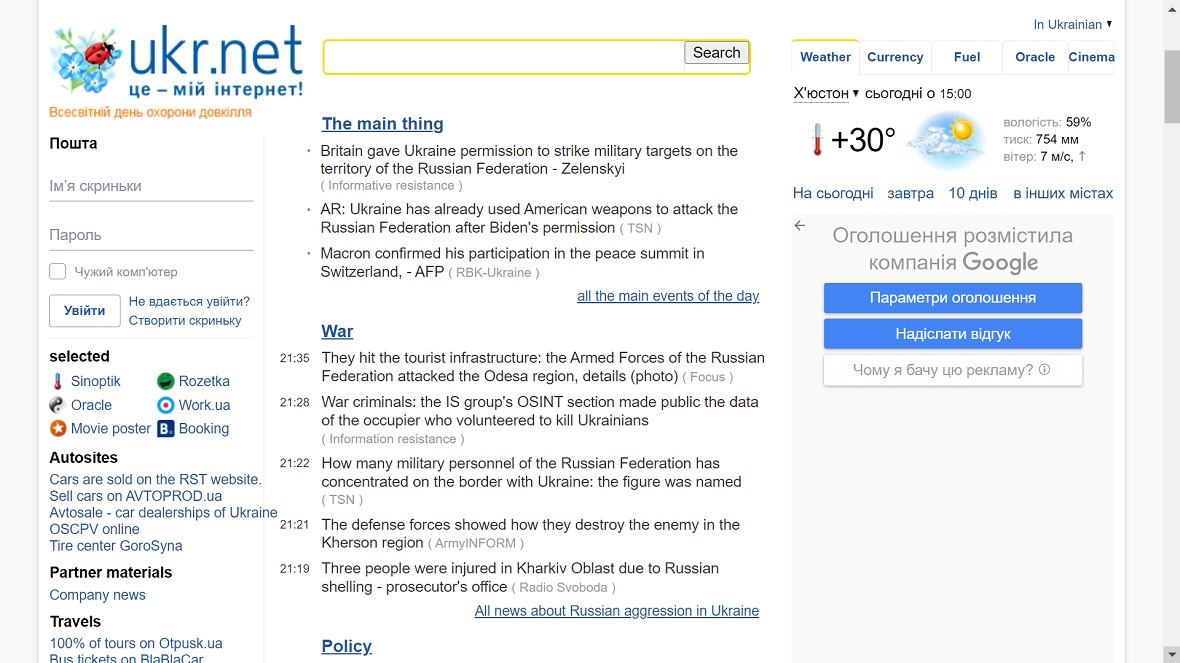
- Credential-harvesting pages: In their attacks, BlueDelta created credential-harvesting pages targeting Yahoo and UKR.net users. The pages can bypass 2-factor authentication and CAPTCHA challenges. They achieve this by relaying requests between legitimate services and compromised routers.
- Phishing emails: BlueDelta uses phishing emails as the initial point of entry, aiming to steal user credentials.
- Living off the land binaries (LOLBins): BlueDelta leverages preexisting, legitimate tools on compromised systems to download malware, steal data, and move laterally within the network.
- Legitimate internet services (LIS): BlueDelta abuses legitimate services like cloud storage, communication platforms, and content delivery networks (CDNs). This is done to disguise their malicious activities and host malware.
By using legitimate services and tools, BlueDelta can bypass security controls. Consequently, security solutions aimed at detecting malicious software or suspicious network traffic can be avoided.
Their activities also appear to mimic system administration tasks or file sharing. This makes it difficult for automated cybersecurity technologies to detect or track these attacks.
The bottom line
The BlueDelta infrastructure is up and running. Governments and organizations working in military, defense, and related sectors with links to the Ukraine-Russia war must take special precautions.
As Insikt Group group said, “The rise of BlueDelta’s activities is a call to bolster cybersecurity measures: prioritizing the detection of sophisticated phishing attempts, restricting access to non-essential internet services, and enhancing surveillance of critical network infrastructure.”
In these critical times, long-term policies that will influence geopolitics for years to come are being shaped. Remaining vigilant and up-to-date with the threat landscape is essential.






