The researchers at Avanan, a Checkpoint software company, have discovered a new malicious campaign targeting college students and aiming to steal their personal information.
Attack methodology
Hackers use phishing, a type of social engineering malware attack, to steal confidential information from students. The information collected is primarily online account credentials.
The attack works as follows:
- Hackers send a phishing email from a legitimate compromised email address.
- The sender’s email address is already compromised using an account takeover attack, meaning this campaign uses a chained attack.
- The email contains a malicious link. When the victim clicks it, it will redirect to the hacker’s website, soliciting the victim for personal information.
- After stealing the victim’s account credentials, hackers can perform various malicious actions with this information. These actions include extorting money from victims, using stolen information to execute other attacks, and selling the information on the darknet marketplace.
Best practices to avoid phishing attacks
Follow these steps to avoid falling victim to this recent attack:
- Hover your mouse over any link received in an email before clicking it.
- When receiving short URLs via email, try to unshorten them using a service such as unshorten.it to reveal the actual link destination.
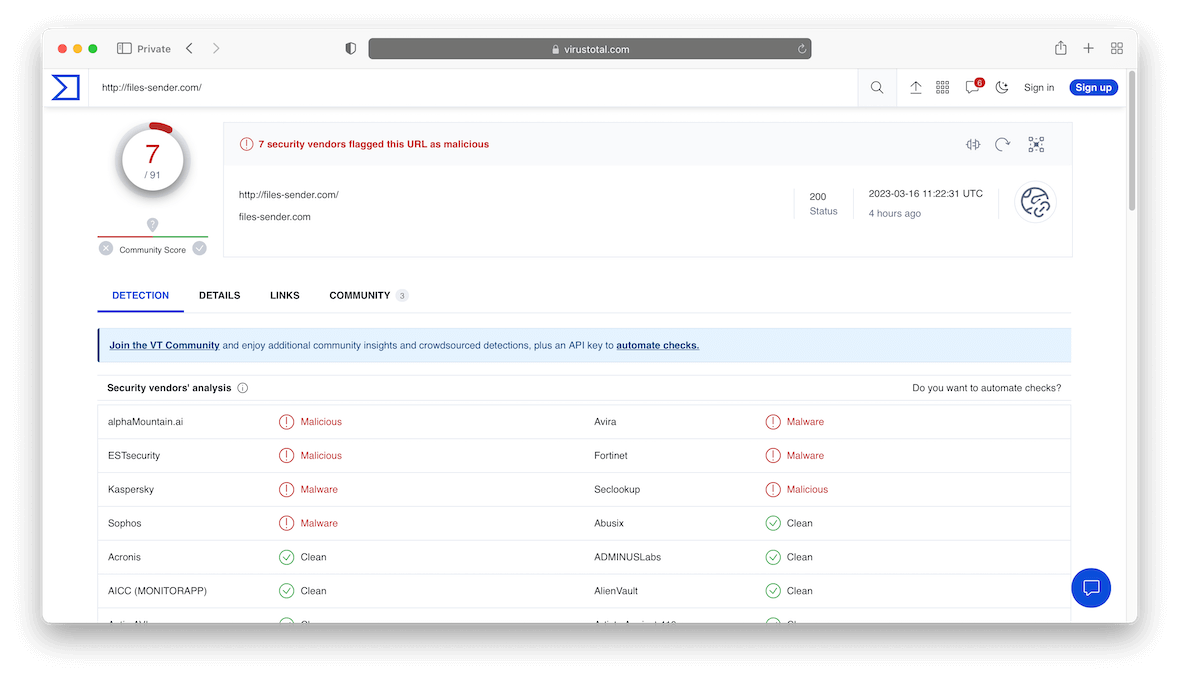
- After revealing the actual URL of any suspicious links, use VirusTotal to see if they are marked as malicious. VirusTotal is one popular service that scans URLs and files against the databases of multiple antivirus engines.
- Do not access unsecured websites. A secure website URL will begin with HTTPS and should display a closed padlock next to its URL.
- Do not click on pop-ups that appear suddenly while browsing because they are frequently linked to phishing websites.
- Only apply for jobs on reputable job portals (such as Indeed or Monster) or the company website announcing the job.
- If you’re currently a college student, consult your university’s IT department if you receive a job offer that appears suspicious.
- Educate yourself on how phishing and other social engineering attacks work.
Technical measures for personal cybersecurity
In addition to the steps mentioned above, observe the following cybersecurity practices:
- Use a reputable antimalware program.
- Keep your operating system and all installed applications up to date.
- Install a personal firewall on your device.
Phishing is the primary social engineering attack hackers use to steal targets’ account credentials. Thankfully, taking a few precautionary measures can keep you safe from similar attacks.