Remember when the FBI warned us not to charge our phones in airports, shopping malls, and public spaces? We haven’t heard much about this type of cyberattack for some time now, but “juice jacking” is back on the threat landscape.
The term “juice jacking” was coined in 2011 when security researchers figured out that cybercriminals were modifying phone charging stations in public spaces to install spyware or steal data from victims. Since then, Apple and Google have released security patches to prevent this from happening on iOS and Android devices.
Now, a new scientific study has demonstrated that juice jacking cybersecurity patches can be bypassed.
Researchers built a malicious smartphone charger that can breach your iPhone
Researchers from the Graz University of Technology in Austria recently released a proof-of-concept paper on what they called “Choice Jacking.” Choice jacking is a new variation of juice jacking, in which smartphones are breached through the use of fake public smartphone chargers, but with a twist.
The security updates that Apple released years ago to prevent this type of attack are based on one premise. The premise is that a malicious smartphone charger connected via USB cannot take over control of a smartphone. This is because a charger, Apple thought, cannot type in confirmation prompts.
What are confirmation prompts, you might ask? Pop-up notifications appear when you connect your phone to a USB. The phone asks you to select “charge” or “transfer files.” That is the confirmation prompt that supposedly only the user can accept or deny by interacting with their screen.
However, this paper demonstrates that by using this new method, malicious smartphone chargers can bypass this security guardrail, inject confirmation prompts, and switch from host to peripheral. Combined, these capabilities give the attacker a new way into your device.
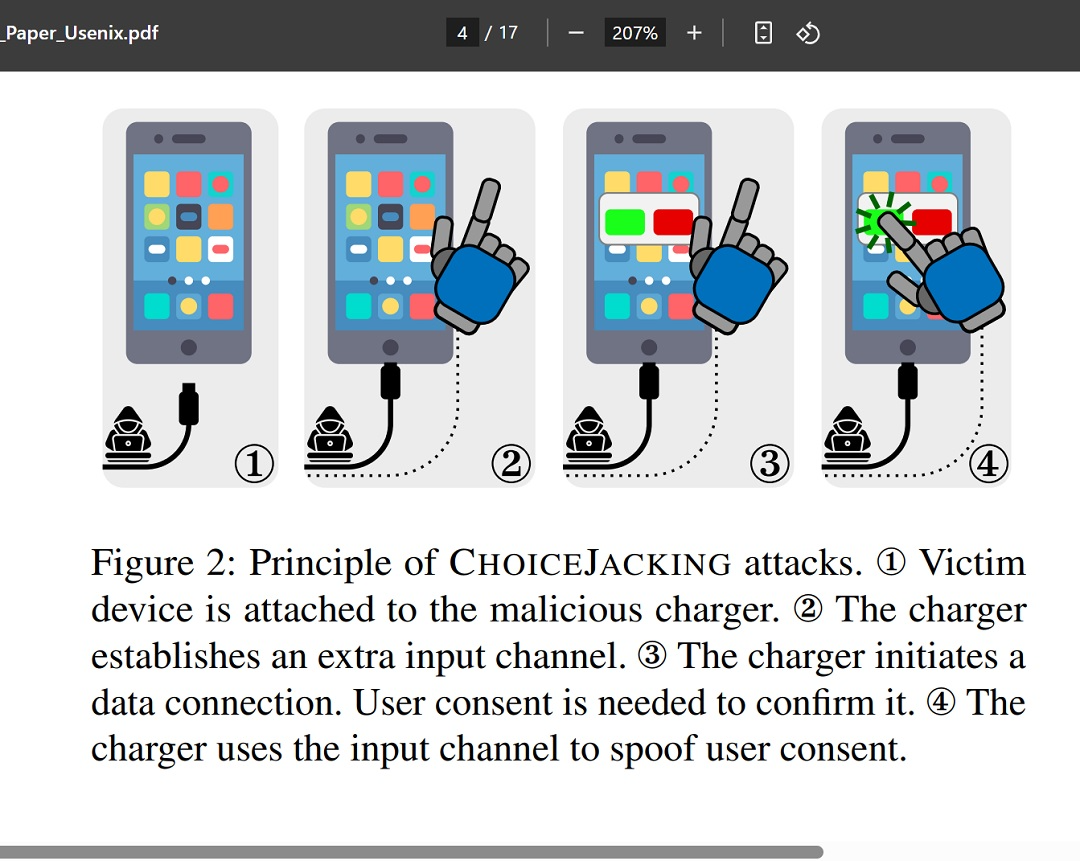
This is how choice jacking works
The devices believed to still be vulnerable to this threat include iPhones that are not updated, older models, and Android models that are not manufactured by top brands like Samsung.
The attack works as follows:
- You connect your device to a malicious charger with its screen unlocked.
- Soon after, the charger performs a USB PD Data Role (DR) Swap. This means it is now acting as a USB input device.
- Next, the charger generates an input to ensure that your Bluetooth is enabled.
- The charger then navigates to the Bluetooth pairing screen in your phone’s system settings to make the mobile device discoverable.
- Now, the charger begins advertising itself as a Bluetooth input device (keyboard, mouse).
- By constantly scanning for newly discoverable Bluetooth devices, the charger identifies the Bluetooth device address of the mobile device and initiates pairing.
- Using the USB input device, the charger takes control. It then selects Yes when the pairing dialog notification pops up on your iPhone.
- The charger sends another USB PD DR Swap. It now acts as a USB host, and the mobile device is the USB device.
- As the USB host, the charger initiates a data connection.
- Through the Bluetooth input device, the charger confirms its own data connection on the mobile device.
- The malicious charger breaches your iPhone successfully.
Mitigation: Is my iPhone safe in public charging stations?
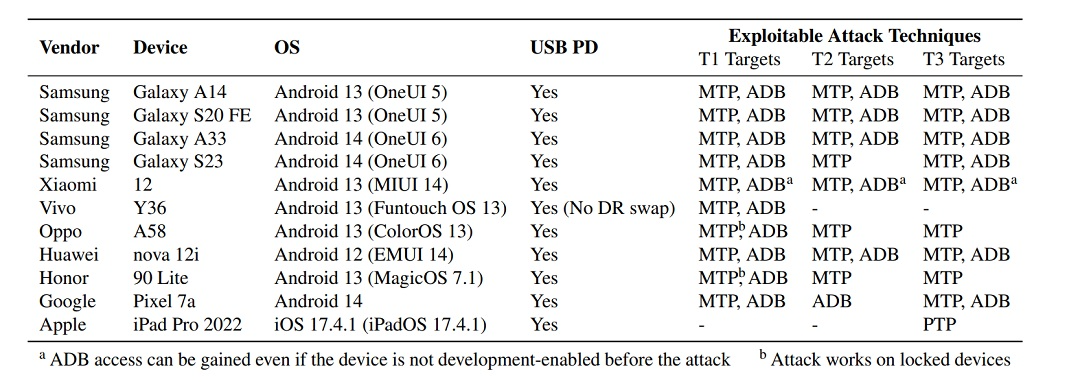
To be able to run this cyberattack, researchers identified and exploited 16 vendor-specific security issues. Of these vulnerabilities, 6 are unique to Android, 4 are related to upstream Android and Google vulnerabilities, and 1 is found in Apple iPhones.
Researchers also found that iPhones and iPads are the least vulnerable to this type of breach technique. Of the 3 demonstrated cyberattack techniques that were able to breach Samsung, Xiaomi, Vivo, Oppo, Huawei, and Google devices, only 1 was capable of breaching Apple devices.
ArsTechnica reported that after the researchers disclosed this vulnerability to Apple, the company released iOS/iPadOS 18.4. The update addresses the vulnerability by requiring user authentication in the form of a PIN or password. So, in theory, all updated iPhones should be clear of the threat.
Despite the increased resilience, Apple devices were not fully immune to the threat before the new patch was recently issued.
“On the iPad Pro 2022, choice jacking attacks can extract photos and videos within 23 seconds,” the research paper found.
When an iPhone or iPad is attached to a USB host, iOS exposes a PTP interface, which allows exchanging photos and videos. While the PTP interface requires user consent, the malicious smartphone charger researchers developed and built comes with an internal keyboard and mouse to move around a screen. This is activated when the charger runs code to switch from host to peripheral, taking over control of a device.
How likely are you to encounter a malicious charger in the wild?
According to the researchers, the malicious charger they built is capable of 1) operating as both a USB device and a USB host, (2) providing power to the attached mobile device in both modes, and (3) switching the USB data role of both the charger and the mobile device.
“Overall, the cost of our prototype is less than $100. This means choice jacking attacks can be mounted even by unsophisticated attackers,” the paper says.
Developing this type of malicious hardware requires advanced technical skills in the fields of hardware and software, as this malicious smartphone charger is built using a Raspberry Pi, electronics for a printed circuit board (PCB) — which can be miniaturized to fit into the USBC connector — and lots of coding.
It’s worth noting that cybercriminals would have to bypass physical security guards in public spaces before they could install these malicious chargers, hiding components behind a wall or in other spaces to properly mount the chargers without raising suspicion.
Final thoughts
While Apple has already patched this up, it’s important for users to always be cautious when charging their phones and other electronic devices in public spaces. It’s best to avoid public charging stations in shopping, airports, train stations, or other locations whenever possible.
New cyberattack methods that use public smartphone chargers, public Wi-Fi, and Bluetooth manipulation will continue to emerge as threat actors get creative. Once again, the best defense is to charge your phone at home or carry your own charger.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iPhone, iPad, and iOS are trademarks of Apple Inc.