In what seems to be a wide-net style phishing campaign, hackers likely linked to China are impersonating the Security Service of Ukraine.
Reports say this malicious email campaign is designed to target Ukrainian government agencies. However, Moonlock employees — who are not connected to the government of Ukraine in any way — have received similar emails.
CERT-UA sounds the alarm
On August 12, the Computer Emergency Response Team of Ukraine (CERT-UA) reported that they had identified a mass distribution of emails sent with a link redirecting possible victims to a malware download. The emails were drafted to impersonate the Security Service of Ukraine.
CERT-UA said that to date, they have identified over 100 affected computers. Many of them belong to central and local government bodies.
A breakdown of the attackers’ techniques and technologies reveals deficits
While the malware sent in these emails can be used to remotely control a device, the emails themselves reveal several gaps and deficits. For example, the emails Moonlock’s team received came in with a clear spam flag. These were automatically redirected to the spam folder by the email provider (as seen in the image below).
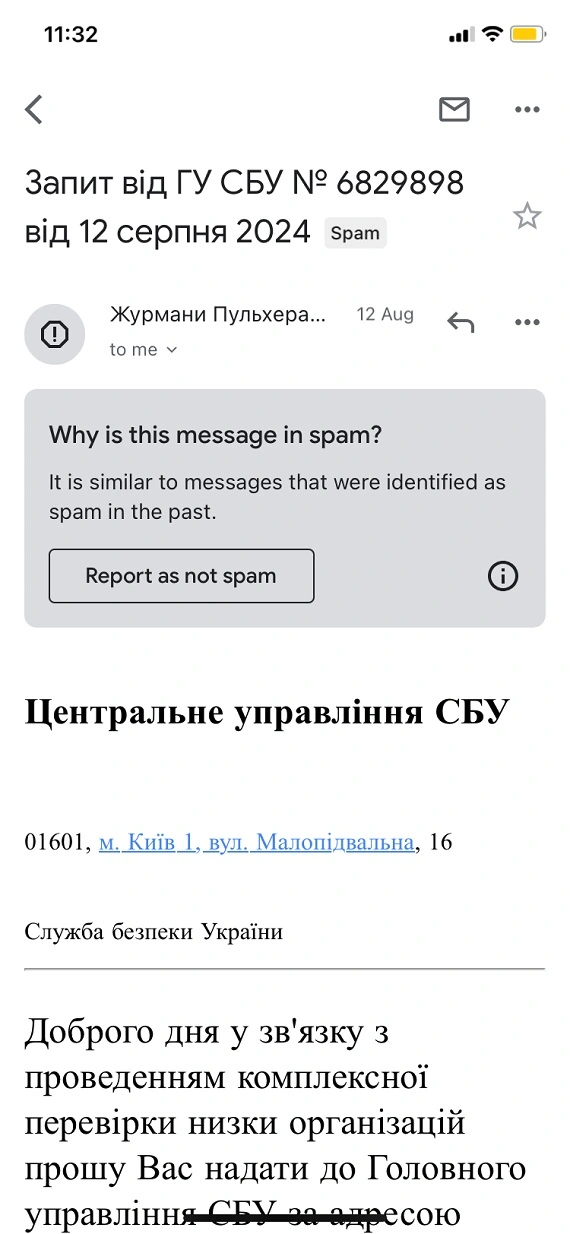

Cybercriminals use several techniques to avoid landing in spam folders or being flagged by email providers. Among these strategies is the inclusion of “invisible-to-the-reader” text in the body of the email. This is done to confuse spam-detecting machine learning algorithms.
Because those behind this campaign are not using any of these methods, it can be assumed that the operation is not as stealthy or sophisticated as high-risk cyber espionage or cyber sabotage actions tend to be.
Borrowed code and outdated Ukrainian sender names
Additionally, CERT-UA identified a configuration file within the attached malware that is identical to the MeshAgent program available for free on GitHub. MeshAgent is used to run remote devices and works in Windows, several Linux distributions, macOS, and other OS.
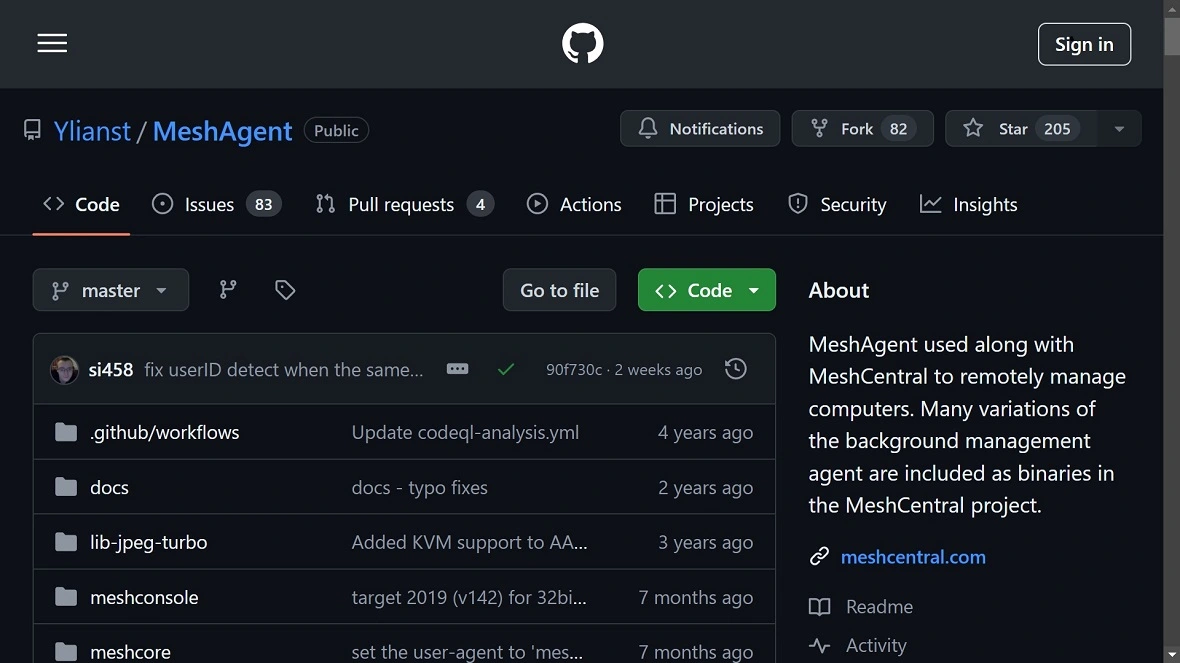
CERT-UA said that the presence of identical MeshAgent code suggests “source code borrowing.”
While source code borrowing is not an indication of the capabilities of the hackers behind this attack, the fact that the code is almost “identical” could be. This is because highly capable hackers tend to modify and customize borrowed code.
By modifying code, bad actors can create new, unique signatures, making it harder for antivirus software to detect their attacks. Customization also allows them to tailor the malware to specific targets or objectives, increasing its effectiveness.
Diverse techniques can be used to hide the malicious intent within the modified code, making it more difficult to analyze. But the bad actors behind this email campaign targeting Ukrainian government agencies and workers did no such thing.
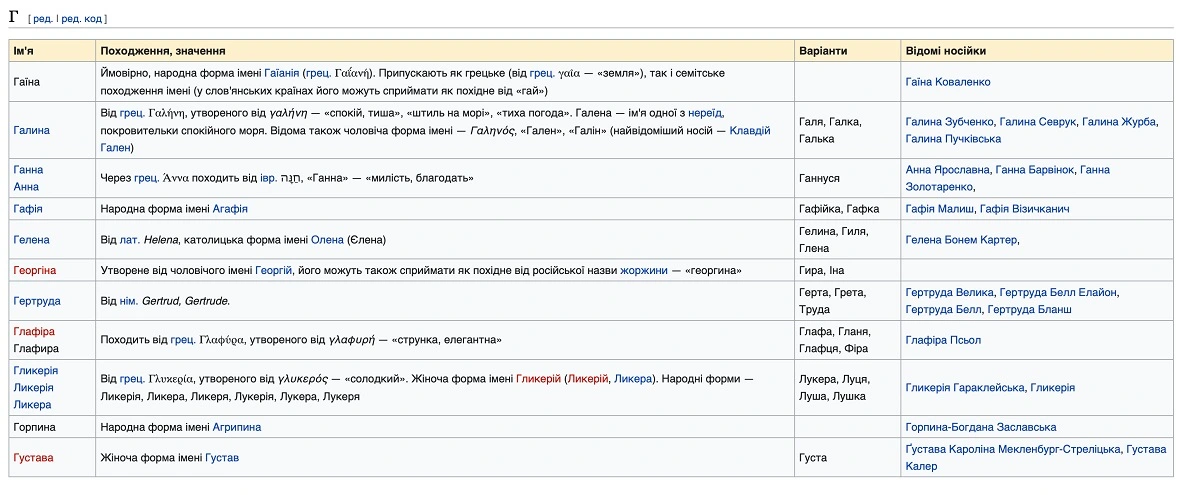
Additionally, Moonlock employees — who, as mentioned, received an email linked to the campaign — said the bad actors are using odd and uncommon sender names. These names included “Glikeria” and “Pulkhera.” These are apparently female names, but the Moonlock team explained that they are remarkably rare or outdated names, “so it instantly looks like a red flag.”
Kseniia Yamburh from Moonlock Lab added that one possible explanation for the use of these strange names is that the emails are automated. In this case, the algorithm used by the hackers may just take random names from a list on Wikipedia.
A dry run for something bigger? Or a non-advanced attacker?
One could argue that this campaign is a dry run test and is simply a preview of something bigger. However, the email spam flag, the identical borrowed code from MeshAgent, and inconsistencies with the local language — spelling mistakes and the use of uncommon sender names — all point to an unsophisticated campaign.
Despite this, the malware download link in the emails and the targeting of government agencies should still be considered high risk, which demands further investigation.
The malware itself, dubbed ANONVNC by the developer, is contained within a link found in the email. The link redirects users to download a file named “Documents.zip.”
CERT-UA explained that, according to their investigations, this campaign is ongoing and dates back to at least July 2024. CERT-UA added that the campaign may include a wider geography, which means targets could be far from Ukraine.
Additionally, CERT-UA also found over a thousand EXE and MSI files linked to the mass email distribution attack. The presence of so many files could imply different campaigns run by attackers run to find the most effective vector and malware of attack.
CERT-UA warned users not to underestimate these emails, stressing that the malware is dangerous.
“Clicking on the link triggers the download of the MSI-file, which launches ANONVNC malware on opening, allowing attackers to gain stealthy unauthorized access to the victim’s PC,” said CERT-UA.
Fake Ukrainian Security Service emails contain possible links to China
Reporting on the news, BleepingComputer said some samples were signed using the code signing certificate of what appears to be a Chinese company — Shenzhen Variable Engine E-commerce Co., Ltd.
The body of one of the emails analyzed by BleepingComputer read, “Good afternoon, in connection with the comprehensive inspection of a number of organizations, I am asking you to submit to the Main Directorate of the SBU at the address 01601, Kyiv 1, str. Malopodvalna, 16, list of requested documents until August 15, 2024. Download the official request: Dokumenty.zip.”
Some of the features of the attack align with previous Chinese state-sponsored threat actors. This includes the goal of breaching a device with stealth and persistence and the targeting of government-linked individuals. The vector of attack (email phishing) is also consistent.
Unlike other nation-supported groups, Chinese gangs have a strong focus on cyber espionage and tend to avoid more aggressive one-time attacks on systems and infrastructure. Given the recent strengthening of ties between Russia and China, the government of Ukraine fits into the category of nations that impact the “Chinese government agenda.”
It is worth mentioning that so far, no one has been officially attributed to these phishing malicious emails.
Capabilities of the malware and indicators of compromise
BleepingComputer added that while CERT-UA doesn’t provide an exact description of the malware’s capabilities, they have warned that it has the potential to enable the threat group — tracked as UAC-0198 — to access compromised computers covertly.
CERT-UA said they have taken urgent measures to reduce the probability of the realization of a cyber threat and listed the following indicators of cyber threats:
- [email protected]
- [email protected]
- [email protected]
- (wss)://syn.hiddenvnc[.]com:443/agent.ashx
- hXXps://filedn[.]eu/lodwtgn8sswha6pn8hxwe1j/………../
- hXXps://filedn[.]eu/lodwtgn8sswha6pn8hxwe1j/1…/
- hXXps://filedn[.]eu/lodwtgn8sswha6pn8hxwe1j/tox/
- hXXps://filedn[.]eu/lodwtgn8sswha6pn8hxwe1j/tox2/
- hXXps://filedn[.]eu/lodwtgn8sswha6pn8hxwe1j/tox2/scan_docs#40562153.msi
- hXXps://gbshost[.]net/
- filedn[.]eu (legitimate pCloud service)
- gbshost[.]net 2024-08-11 @webnic.cc (Cloudflare)
- gbshost[.]org 2024-08-11 @webnic.cc (Cloudflare)
- syn.hiddenvnc[.]com
- sync.hiddenvnc[.]com
- sync.anonvnc[.]com
- sync.invoice-traffic[.]com
- sync.smart-vnc[.]com
- sync.smartcloudflare[.]com
- hiddenvnc.com 2024-06-14 @cloudflare.com
- anonvnc.com 2024-06-11 @cloudflare.com
- invoice-traffic.com 2024-06-23 @cloudflare.com
- smart-vnc.com 2024-06-23 @cloudflare.com
- smartcloudflare.com 2024-08-02 @cloudflare.com
- 186.2.171.76 AE @iqweb.io
- 66.94.109.162 US @contaboserver.net
- 66.94.104.42 US @contaboserver.net
The bottom line
While this phishing campaign appears less sophisticated than some, it still poses a significant risk, having led to a noteworthy number of infected machines.
Overall, the use of readily available malware and easily identifiable red flags suggests that the attackers may be less skilled. However, the potential for gaining remote access to compromised computers warrants caution.
CERT-UA advises vigilance and offers indicators of compromise to help identify malicious emails. If you receive a suspicious email, do not click on any links or attachments. Report the email to your IT security team and delete it.
Whether you are located in Ukraine or work in the government sector, if you received an email similar to those associated with this campaign, CERT-UA urges you to stay vigilant. Contact them immediately at [email protected] or by phone at +38 (044) 281-88-25.






