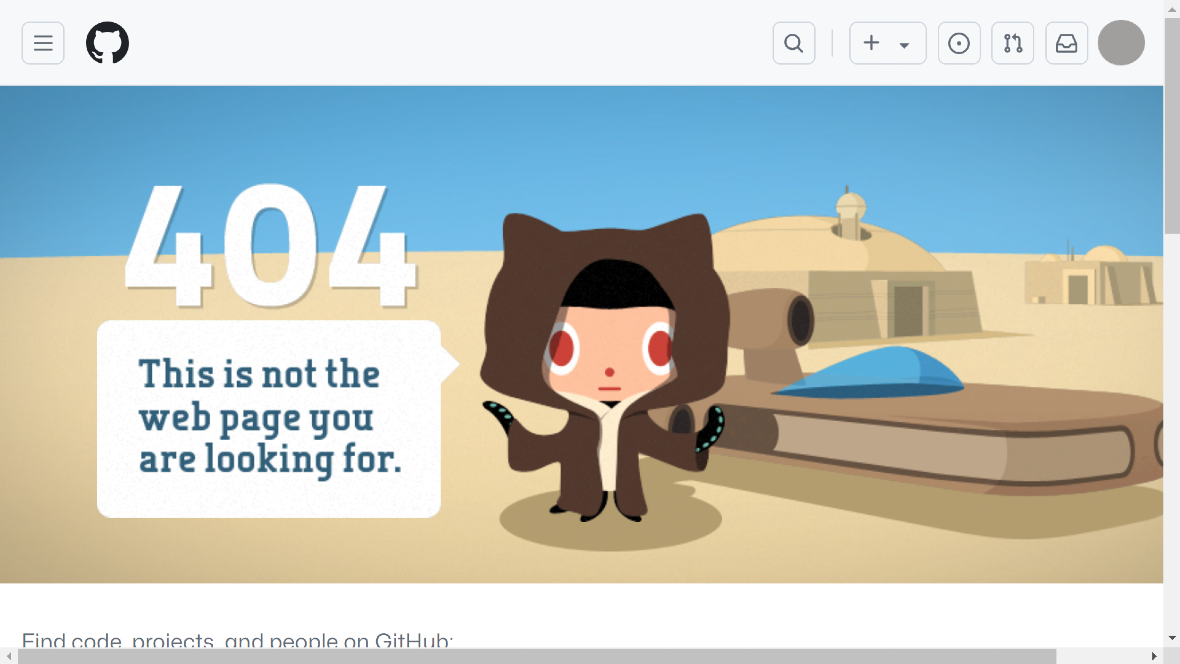
GitHub, the popular software platform used by over 100 million developers, is the latest target of a Russian-speaking coordinated cybercriminal campaign of malware distribution.
GitHub allows a global community of software developers to store, track changes, and collaborate on code. From a criminal perspective, the platform can be very attractive due to its storage capabilities and the fact that it offers the sort of reliable features that aren’t found on untrustworthy sites on the dark web.
Developers have always known the risks of code hosted in GitHub, but now, a new report from the Insikt Group has exposed the inner workings of a highly sophisticated criminal enterprise.
How the cybercriminal enterprise is exploiting GitHub
On May 14, Recorded Future’s Insikt Group released an exhaustive investigation uncovering a new cybercriminal campaign led by Russian-speaking threat actors from the Commonwealth of Independent States (CIS).
The threat actors created a fake GitHub profile and code repository under the username papinyurii33 (currently no longer active). Using this GitHub account, they impersonated legitimate software to hide different types of malware, including the Mac-targeting Atomic macOS Stealer (AMOS) and Vidar.
Criminals offered malicious versions of 1Password, Bartender 5, Pixelmator Pro, and other software through this GitHub profile. The GitHub account used by the criminal group has been active since January 16, 2024.
The counterfeit versions of these widely used pieces of software contained malware that was coded to breach victims’ systems and exfiltrate sensitive data.
Overall, the campaign leveraged both the good name of trusted software brands and the community culture of GitHub to trick victims into believing their operation was legitimate.
Web phishing and distribution
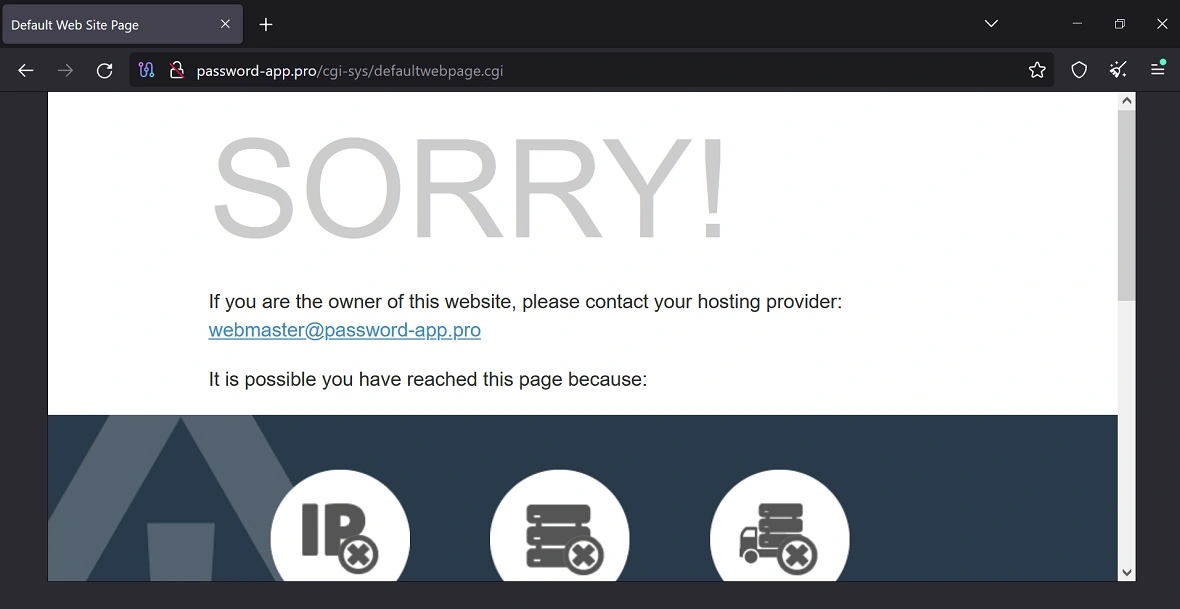
To drive potential victims toward the GitHub profile, the group created dozens of phishing sites, which included a direct link to the papinyurii33 GitHub profile hidden in the download buttons of the fake HTML sites.
Moonlock confirmed that most of the sites listed by the investigation had already been taken down by the criminal group, as it surely rushed to cover its tracks.
While the research done by Insikt Group does not mention how the bad actors attracted visitors to their fake websites, previous AMOS distribution campaigns used similar techniques, creating fake sites that impersonated brands like Slack, as Moonlock reported in early 2024.
Additionally, AMOS distributors have used search engine optimization techniques and exploited ad platforms like Google Ads to direct users to these fake sites. It can, therefore, be inferred that similar techniques were used in this new campaign.
Bold or desperate? Criminals in search of sites to host malware are getting creative
The interesting twist in this campaign is that criminals are now using GitHub as a way to host and distribute their malware. Hosting malware in the cloud is a big problem for cybercriminals. Most cloud and hosting providers have installed security guardrails to prevent malware from being part of the environment. Furthermore, most hosting services have direct connections with law enforcement and security researchers.
These challenges have forced criminal groups to get creative about where to store their damaging malware. An example of this was seen in November of last year when Discord had to switch to temporary links to curb the spread of malware, as Moonlock reported.
In the Discord incident, cybercriminals exploited Discord’s own content delivery network (CDN) — smaller edge data centers working close to the user to speed up the service — to host and distribute malware.
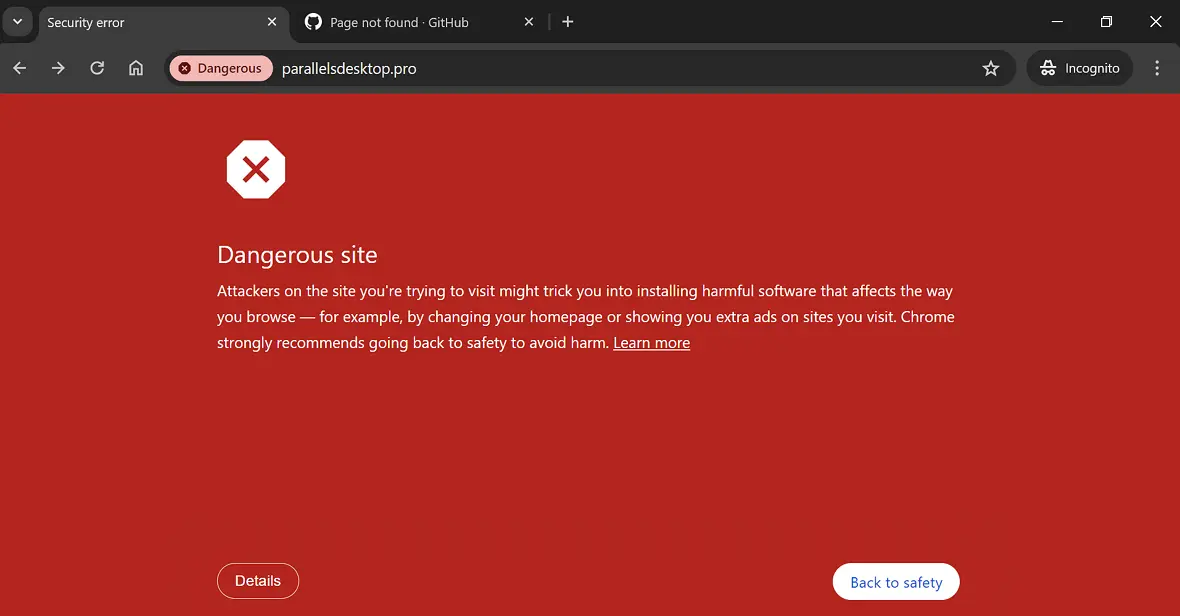
This new criminal group is nothing if not audacious. Using GitHub, a platform ripe with security professionals and advanced developers, represents a high risk for them. It’s a platform where the community can easily pick up on malicious schemes due to their technical knowledge and experience.
Insikt Group found that despite having access to a wide range of premium cybercriminal tools and techniques, the threat actors identified in this campaign use free and web-based infrastructure, like FileZilla servers, as a mechanism for malware delivery, abusing these legitimate channels to disseminate various malicious payloads to victims’ devices.
There are a few reasons why cybercriminals might prefer legitimate sites over illegal hosting servers or dark web hosting. These include but are not limited to trust and familiarity, wider reach, and specific social engineering needs that cannot take place on illegal hosting sites or on the dark web.
Connecting multiple malware to the same C2 server
Researchers from Insikt Group also found that the malware variants being distributed by the group, including Atomic macOS Stealer (AMOS), Vidar, Lumma, and Octo, were not standalone operations.
All malware variants shared a common hacker-controlled command-and-control (C2) infrastructure, suggesting a coordinated effort to maximize the impact of the attacks. C2 infrastructure allows bad actors to remotely communicate with breached devices and enables the transfer of information and commands to and from the breached device to the C2.
Warning: Rapid rebranding and redundant malware campaigns are on the rise
It is worth mentioning that Insikt Group has historical evidence of this campaign’s evolution and warns that the group is capable of rapid rebranding. Rebranding is becoming a common practice among the most advanced and resource-rich cybercriminal operations.
The essence of rebranding is redundancy. As bad actors create campaigns, they know that being exposed is just a matter of time. To avoid downtimes, criminals will create entirely new campaigns that duplicate the ones that were exposed. These may be created even before the existing infrastructure has been compromised to accelerate deployment.
This redundancy concept allows cybercriminals to continue operating under new brands once law enforcement or security experts expose the visible campaign to the public. In just days, a criminal enterprise can shut down fake profiles on platforms like GitHub, delete websites, and erase most of its digital footprint while simultaneously releasing a new set of malicious phishing domains and switching to other platforms.
A call for exhaustive code review
Organizations and developers using GitHub are urged to adopt security protocols when integrating external free code into apps or environments. Checking code performance and legitimacy is common practice in the DevSecOp sector, with manual and automated code checks being essential. In simple terms, organizations should make sure nothing unusual is included in the free code they are using.
Today, organization-wide code review processes are more critical than ever, especially with the rise of zero-day vulnerabilities. Automated scanning tools like GitGuardian, Checkmarx, and GitHub Advanced Security can help organizations strengthen their security posture and “do more with less” by automating security scans to high speeds.
What can be done to address a threat like this?
While developers using free, licensed, open-source, or closed-source software do not tend to apply Zero Trust principles — assuming that no code can be trusted — the concept could serve the industry.
Additionally, users should do the same. When searching online for popular software to download, they should assume that all software and apps are malicious. Taking this extreme mindset toward software and app downloads would oblige users to double-check sites and verify their authenticity.
Staying vigilant is key because you never know where an attack may come from. As mentioned, this group is capable of rapid and effective rebranding and has a redundant, malicious system in place to continue operating in the shadows even after a major security investigation uncovered their game. Monitoring and blocking unauthorized applications and third-party scripts, which could serve as gateways for malware, is also important.
Companies should also educate employees, developers, and users about the risks associated with downloading code from untrusted sources, including GitHub repositories.
Training that helps users identify suspicious repositories — for example, those that have low activity levels, are unverified authors, and have unusual file names — is fundamental to preventing an attack from happening in the first place.
Firewalls, intrusion detection systems (IDS), intrusion prevention systems, endpoint security solutions, and incident response plans are also necessary for small, medium, and large businesses.
On an individual level, the same principles and tools apply. Always double-check profiles on social community platforms, check for suspicious red flags, only download software through official channels and app stores, and run trusted antimalware software on your devices.