It turns out that when you click on that little button on your iPhone allowing an app to access your Contacts list or other data, what happens next is incredibly complex. Those who misuse and abuse these processes are becoming more dangerous and sophisticated every day. For example, some apps, when given access to Contacts, leverage something called “private entitlements.”
Private entitlements, coded into an app by its developer and never seen by users, can allow an app to do more than just access your contacts. In fact, it might take your entire call log history. It might even go after your calendar data or the location of your family members while it’s at it.
Responding to this extremely technical cybersecurity environment, Apple developed a small feature for iOS 18 that is being praised by cybersecurity media. The feature is part of a wider set of tools you can find on your iPhone if you are running iOS 18.
In this report, we go over the fundamentals of this feature. Plus, we outline what black hat hackers can do with permissions and how you can make your iPhone more secure.
Thousands of iPhone apps ask users for permissions reserved for rare cases
A recent Zimperium report found that over 40,000 apps use private entitlements and more than 800 use private APIs. They also found hundreds of apps that exploit iOS vulnerabilities to alter system-level settings.
To understand what really happens when you grant permissions to an app, we need to understand a few key terms: permission misuse, private APIs, and private entitlements. These concepts involve complex software engineering and mechanics. To be honest, given the app threat landscape, even the brightest cybersecurity minds at Apple struggle with it.
What really happens when you give an app permission to “Allow Access”?
It happens all the time with technology. As users, we see clear, rounded buttons and elements on our screen (the user interface) and assume everything is as simple and straightforward as it appears. But behind the scenes, there is a lot of code running. Consequently, a simple “Allow Access” button can be a nightmare.
To simplify the “Allow Access” problem, Apple developed a small feature for iOS 18. With it, users grant an app access only to specific contacts.
Before this feature existed, clicking on “Allow” would give away access to the entire Contacts list (and perhaps more). Now, with this feature, by default, users choose what specific contacts the app can access, if any.
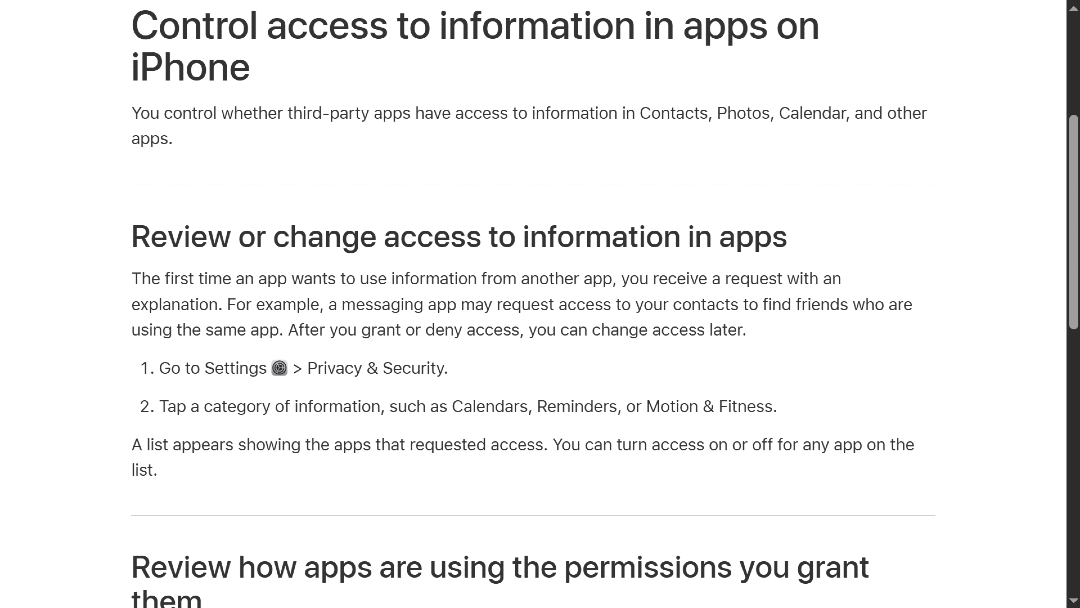
While The New York Times reported that developers had concerns that this tool would hold back growth for new social media apps (that leverage access to users’ Contacts to send invites and grow), Erich Kron, security awareness advocate at KnowBe4, told us that at its core, the feature is about user trust.
“Our phones are incredibly useful, especially with the use of so many great applications available,” Kron said. “Unfortunately, people place a lot of trust in these application developers and will even go out of their way to sidestep built-in security features to install potentially dangerous applications without considering the ramifications.”
Side-load at your own risk
While Zimperium’s report does not mention specifically where these risky apps were found, they do highlight the dangers of side-loading. Side-loading involves intentionally bypassing iPhone security settings and downloading apps from platforms other than the official Apple App Store.
“The official app stores for most devices do a pretty good job vetting applications and removing or denying publication of those that are malicious or could be problematic. However, even that is not foolproof,” Kron explained.
“In some cases, the device owner is willing to bypass the safety features to install applications that seem especially useful or entertaining.”
In some cases, the device owner is willing to bypass the safety features to install applications that seem especially useful or entertaining.
Erich Kron, Security Awareness Advocate at KnowBe4
So, let’s look at permission misuse, privilege entitlements, and private APIs.
What is permission misuse?
Permission misuse is when an app asks for permission, for example, to access your Contacts because it wants to “connect them in the app.” Once you grant it permission, however, it actually uses this access to extract your entire Contacts list. The list can later be used for targeted marketing, analytics, or other activities that you did not explicitly consent to.
Privilege entitlements: Permissions so wide that users never interact with them
Next, we have privilege entitlements, which are more sophisticated. These are not managed by users but are coded into apps. For example, a legitimate use of privilege entitlements could be an iOS Apple update. An update leverages privilege entitlements mechanisms to temporarily gain privileges to modify deep system settings or install new software without asking for explicit user interaction every time.
Now, imagine what a malicious app with privilege entitlements can do. Naturally, the abuse of this feature not only undermines user trust and privacy but also violates Apple App Store policies.
Private APIs: Deep core permissions
Ask an expert or search online for what “Private APIs” are, and you’ll get lengthy jargon in response. So, in an attempt to break down what a Private API can do, we can say they are intrinsically connected to your iPhone’s operating system and are intended to be used only by your iOS (in most cases).
Private APIs are mechanisms hidden from the average user. Unlike public APIs, they allow apps to perform actions or retrieve information that typically remains hidden from third-party apps. They can go deeper into the core functions of your iOS, too.
Setting the record straight on the risks involved
It is easy to dismiss an app’s permission requests as minor inconveniences. However, experts tell us that the risks for users and businesses alike are serious and significant.
Those risks include privilege escalation attacks, data breaches, and exposure to data brokers and the dark web.
“Cybercriminals and bad actors take advantage of this desire and will work hard to market dangerous applications as useful, then use them to access bank accounts, steal passwords, and perform other dirty deeds,” Kron told us. “This can be especially problematic if the devices contain information from their employer or have access to the employer’s network.”
Privacy Report: Apple’s privacy monitoring tool
The iOS feature that allows users to give access only to specific contacts is part of a wider set of app privacy monitoring features that Apple continues to strengthen.
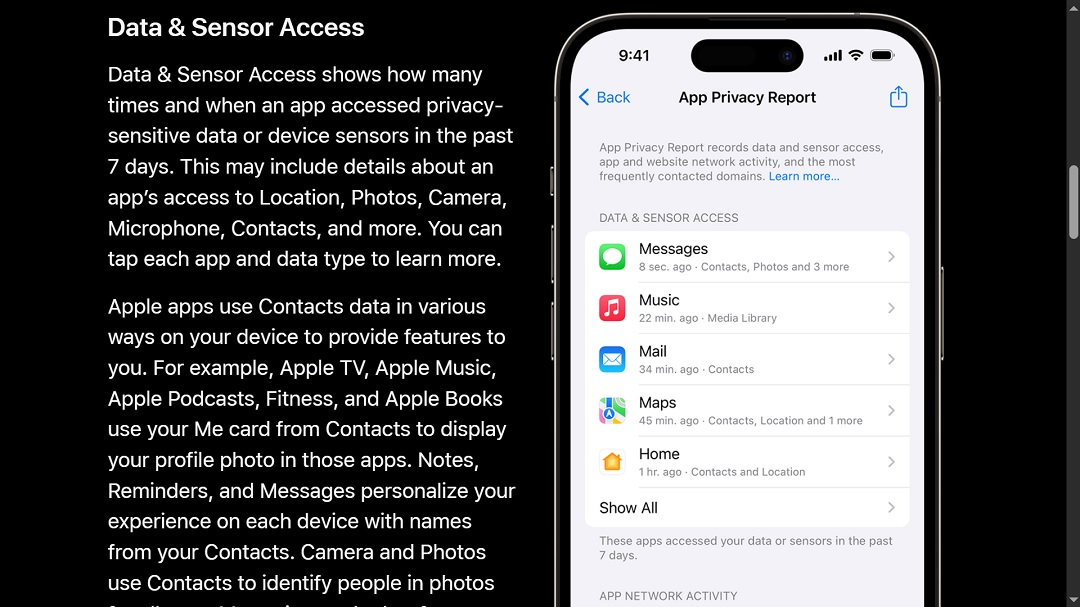
Using the App Privacy Report, which you can access by going to Settings > Privacy & Security, then tapping on App Privacy Report, you can monitor which apps access your data, sensors, and network activity. You can also view the most frequently contacted domains.
When monitoring what apps have accessed your data and your sensors (camera, mic, etc.), the feature will list not only how many times they accessed them, but when they were accessed. The feature monitors access to your privacy-sensitive data or device sensors in the past seven days.
Privacy Report keeps a close eye on how apps access your Location, Photos, Camera, Microphone, Contacts, and more. The tool also shows websites that have been contacted. This applies to connections made directly or from content within an app, domains that have been contacted by websites you’ve visited within apps, and the web domains most frequently contacted by all your apps, either directly or from in-app web content.
Privacy Report is the place on your iPhone where you’re most likely to find clues about whether you have any fishy or malicious apps running on your phone. The problem is that malicious and stealthy apps leverage deeper-level code and tools like privilege entitlements and private APIs. These are technologies that operate behind user interfaces. So, it is a possibility that some apps may bypass this monitoring tool.
Final thoughts
When it comes to cybersecurity, users already have a lot to watch out for. Threats include malicious and/or fake apps, side-loading dangers, app companies that sell user data to data brokers, and straightforward malware.
In short, most of us have enough to worry about, even without private entitlements.
From data brokers to invasive apps, adware, scareware, and spyware, it’s not just cybercriminals who abuse permissions, trick users, and develop privilege entitlements and private API exploits. Next time you see that little pop-up on your iPhone, you might want to think twice before clicking “Allow Access.”
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iPhone and iOS are trademarks of Apple Inc.






