At Moonlock Lab, we’ve recently uncovered a sophisticated and alarming threat spreading through Google-sponsored URLs. The threat, a stealer malware targeting macOS, poses as the popular application Loom, a widely used screen recording tool.
A deceptive Google Sponsored Link
Our investigation kicked off when we noticed a Google ad that appeared to promote the official Loom application. At first glance, it looked legitimate, enticing users to click on what seemed to be a trusted source. However, upon clicking the link, things took a nasty turn.
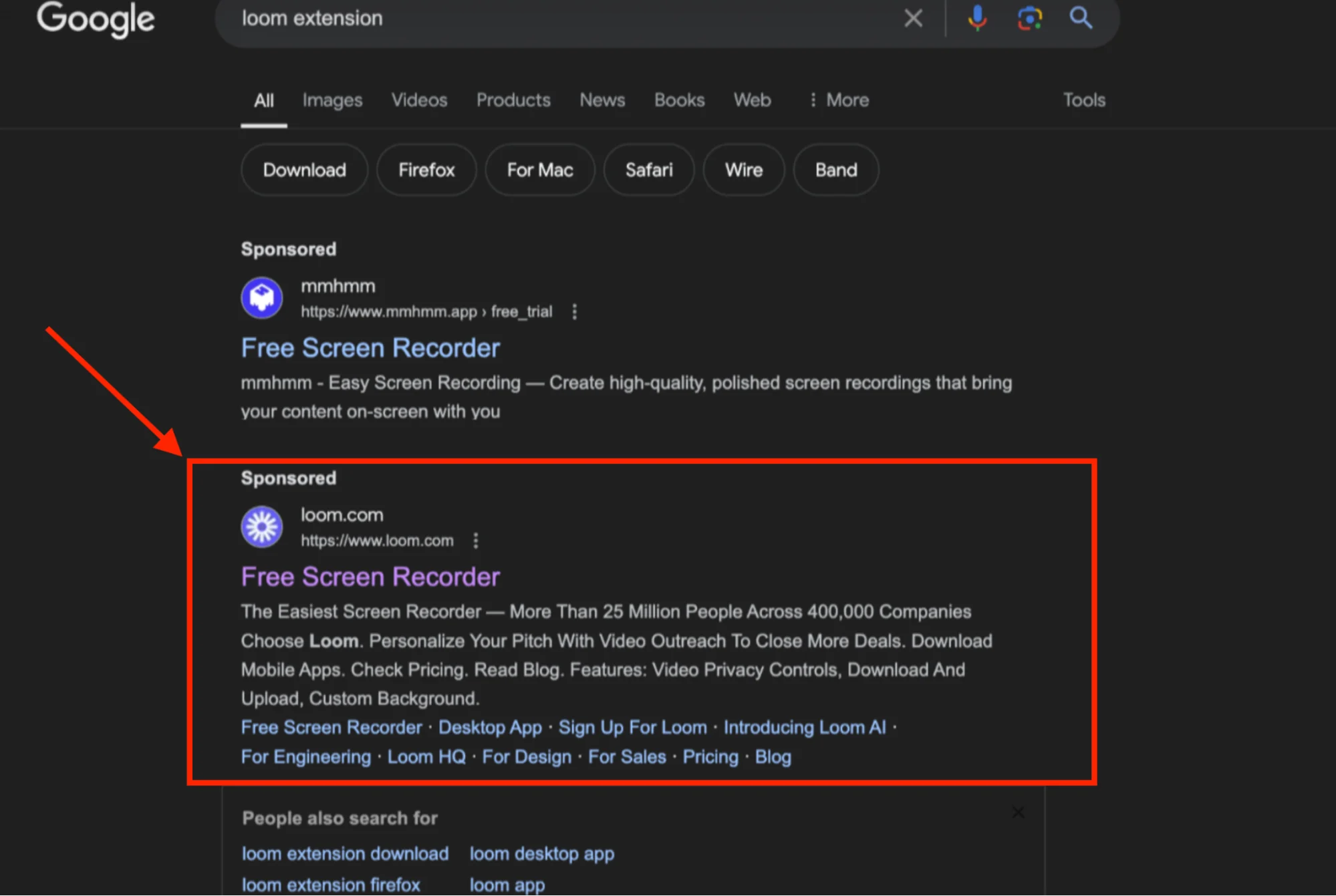
When we clicked on the link, the domain changed, redirecting us to a site that was a near-perfect replica of the official Loom website. This fraudulent site was hosted at smokecoffeeshop[.]com.
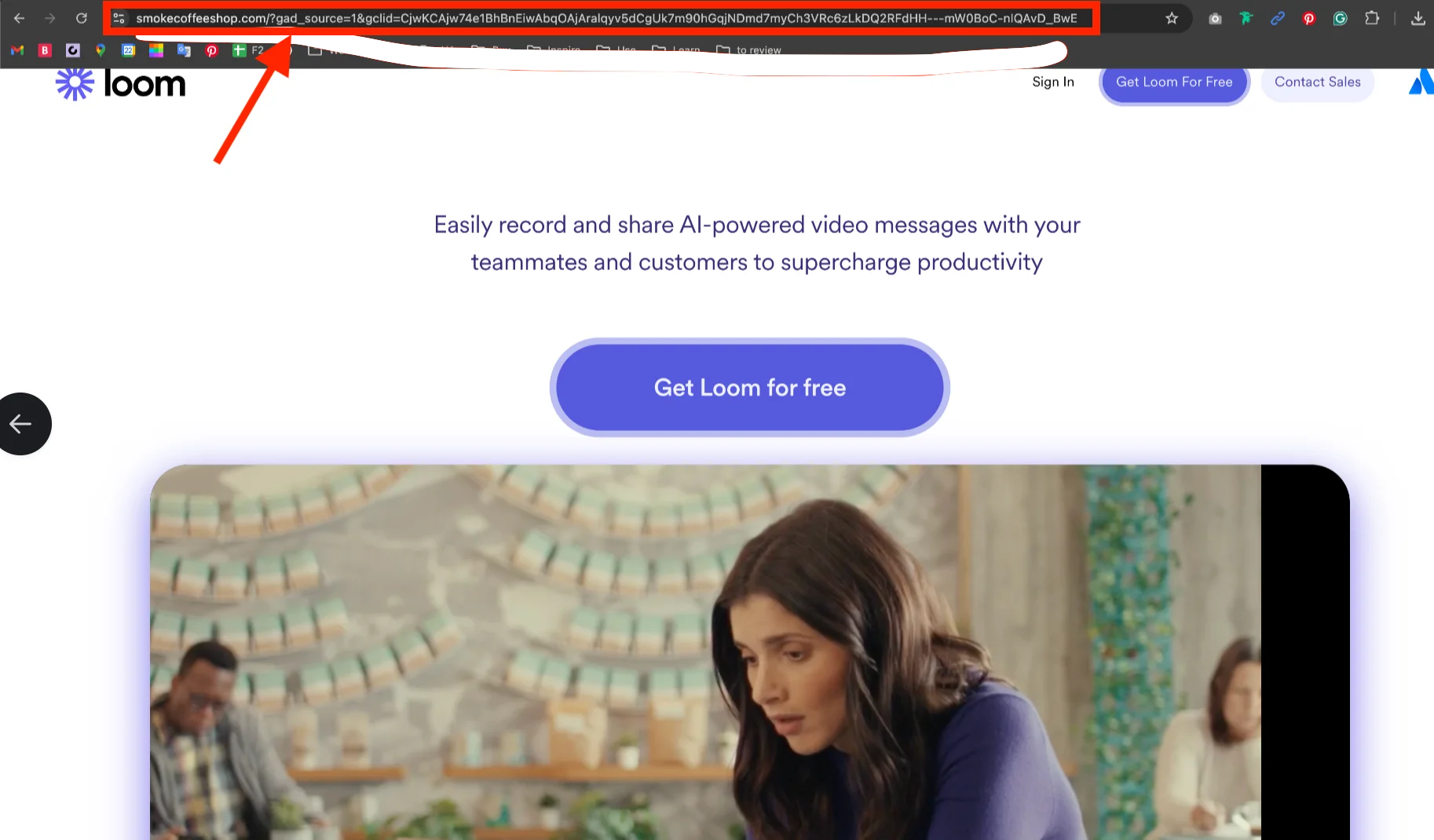
Once redirected to this fake website, users are prompted to click the “Get Loom for free” button to download the application. Users who aren’t vigilant could easily make the mistake of clicking on this link, which, not surprisingly, does not download the Loom application. Instead, it downloads a malicious file that contains stealer malware.
Attackers are counting on users’ hurry and lack of attention, redirecting them multiple times to avoid detection. This tactic helps bypass security measures, as the multiple redirects make it harder for automated systems to flag the malicious sites.
The file itself was downloaded from hxxps://wouldyougunna[.]com/yvfiubhferwewf/process_l00m.php, showcasing the attackers’ efforts to create a convincing phishing scheme.
The extent of the campaign
As we dug deeper, it became clear that this campaign was not limited to Loom. We discovered similar malicious functionality in other files. In fact, we discovered that the attackers also created fake versions of other popular applications, including Figma, TunnelBlick (VPN), Callzy, and an intriguing case named BlackDesertPersonalContractforYouTubepartners[.]dmg.
The following chart illustrates the various applications we’ve detected being impersonated while investigating this campaign.
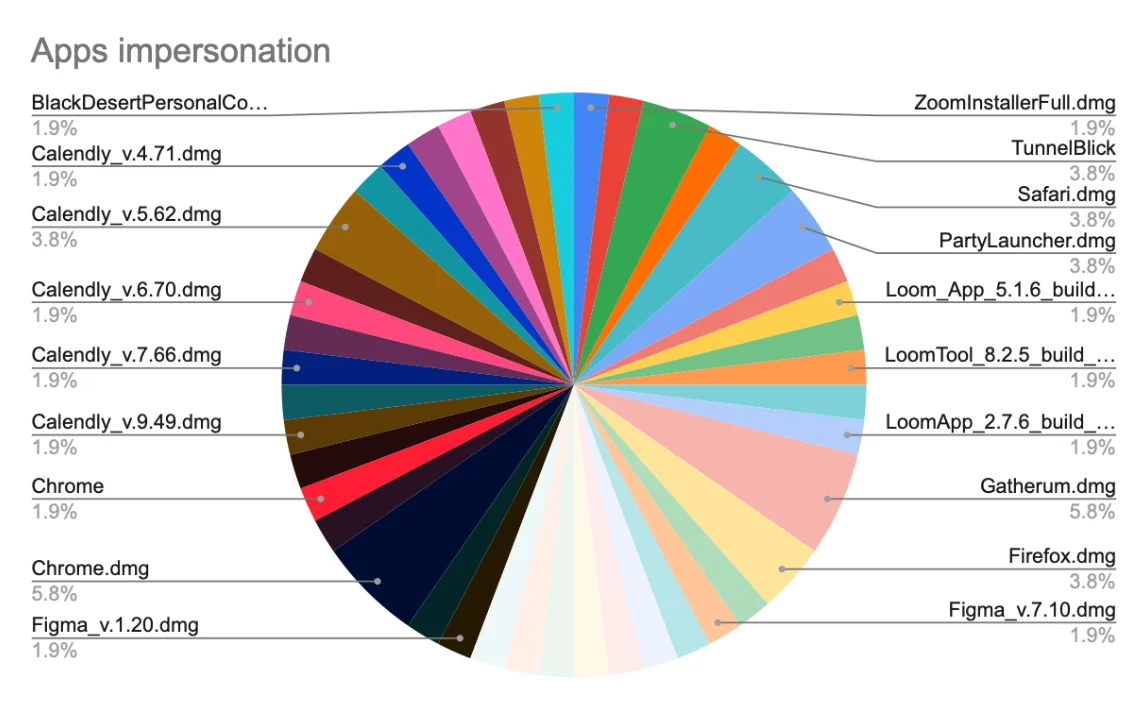
The name of the final example listed above, “BlackDesertPersonalContractforYouTubepartners,” implies a reference to Black Desert Online, a popular massively multiplayer online role-playing game (MMORPG), strongly suggesting a phishing campaign targeting YouTube content creators. This is an old tactic used by threat actors.
Two years ago, attackers sent similar phishing emails to Windows users. Now, they are using the same lure to target macOS users. An example of one such email was shared on Reddit by user @Away-Ad-2460 here.
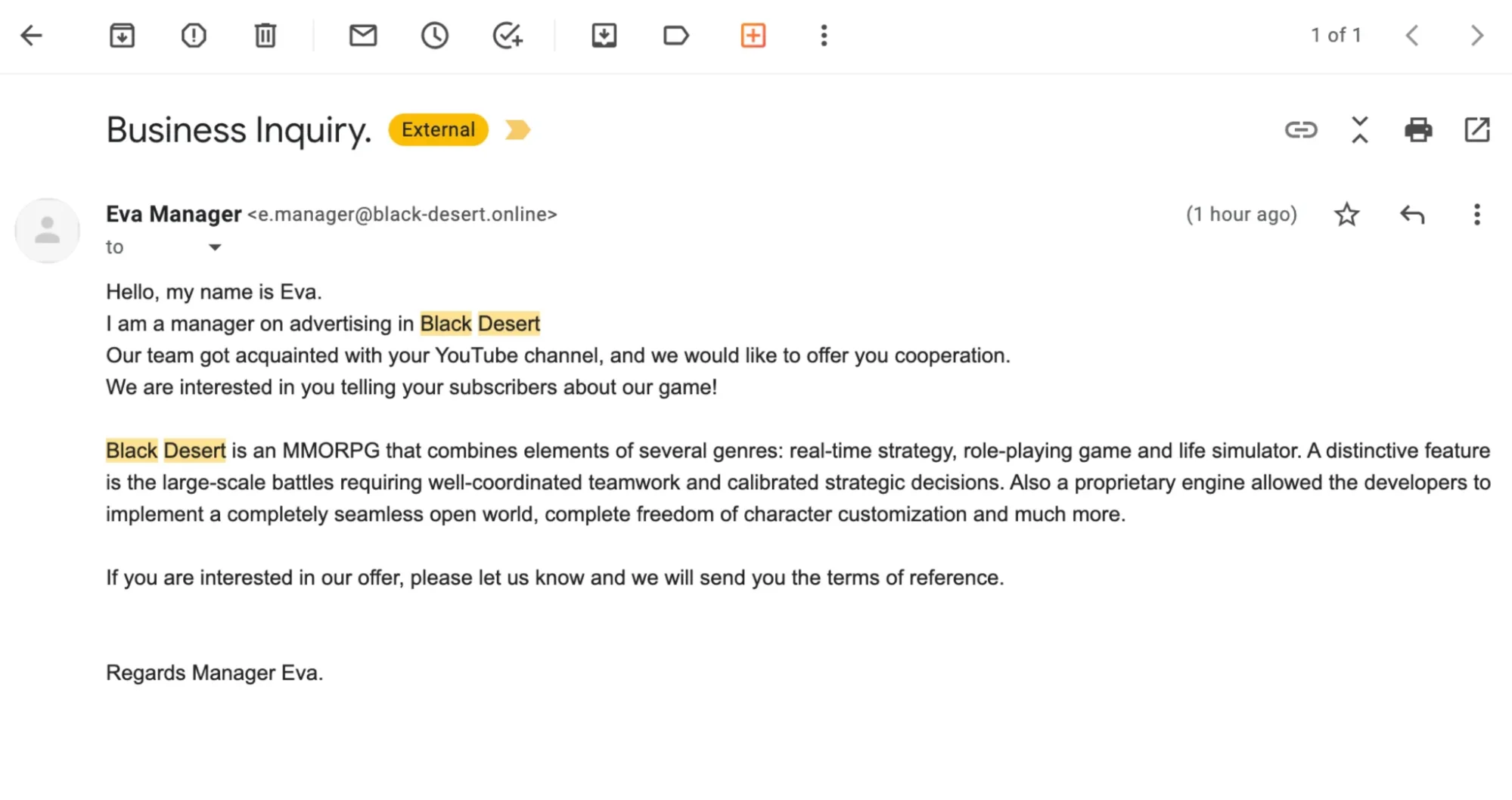
This campaign exploits the relationship between gaming companies and content creators, luring bloggers and content creators in the gaming space with the promise of a personal contract to promote Black Desert Online on their channels.
The malicious LedgerLive clone
One of the concerning aspects of this campaign is the use of a stealer that replaces the legitimate LedgerLive app with a malicious clone. We previously highlighted this feature in our X (Twitter) post.
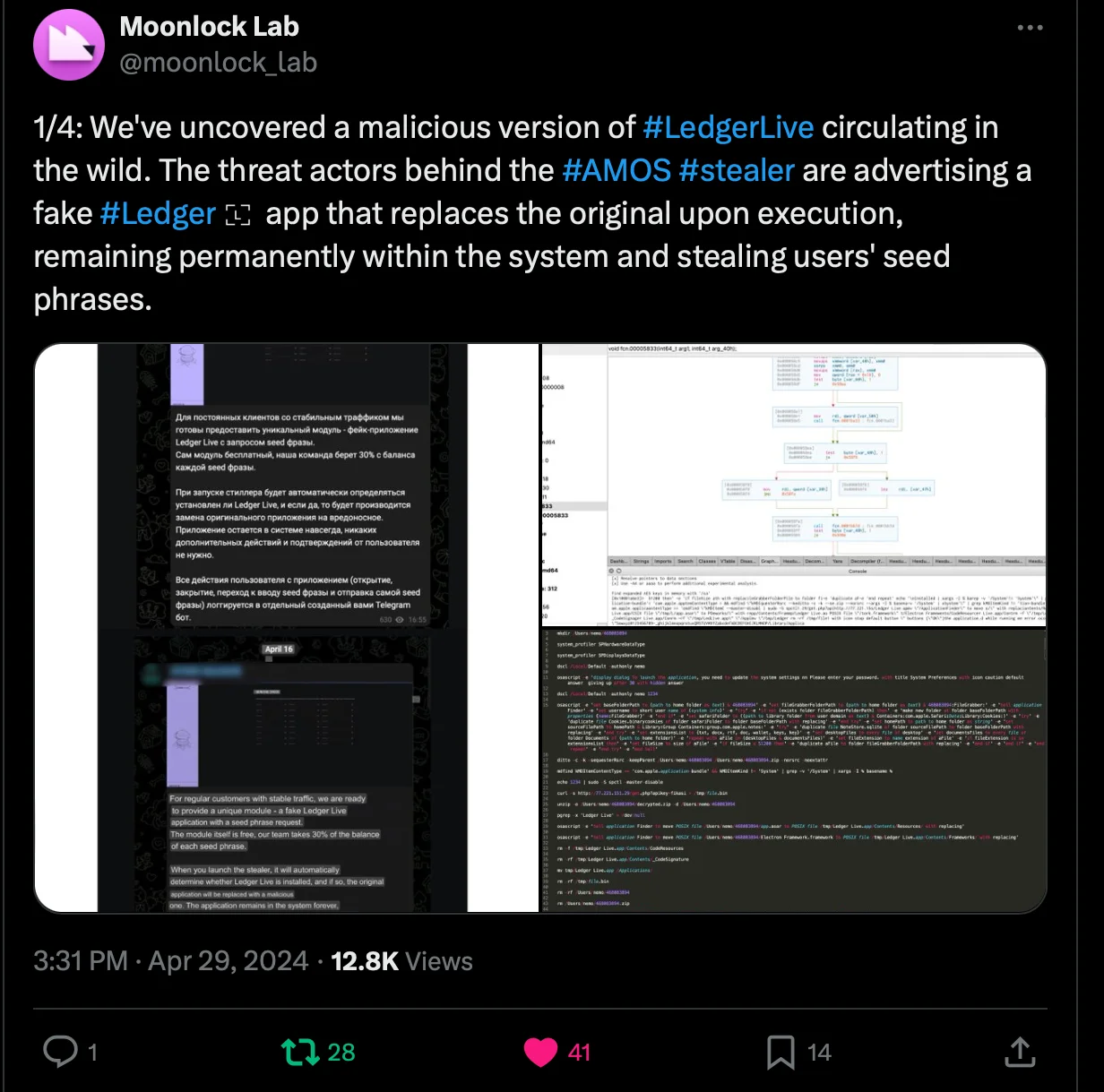
LedgerLive, widely used by cryptocurrency holders to manage their assets, presents an attractive target for cybercriminals.
By replacing the genuine app with a harmful version, attackers can potentially access and drain victims’ cryptocurrency wallets. This can lead to financial losses, as the malicious clone is designed to closely mimic the legitimate app’s appearance and functionality, making it difficult for users to detect the compromise.
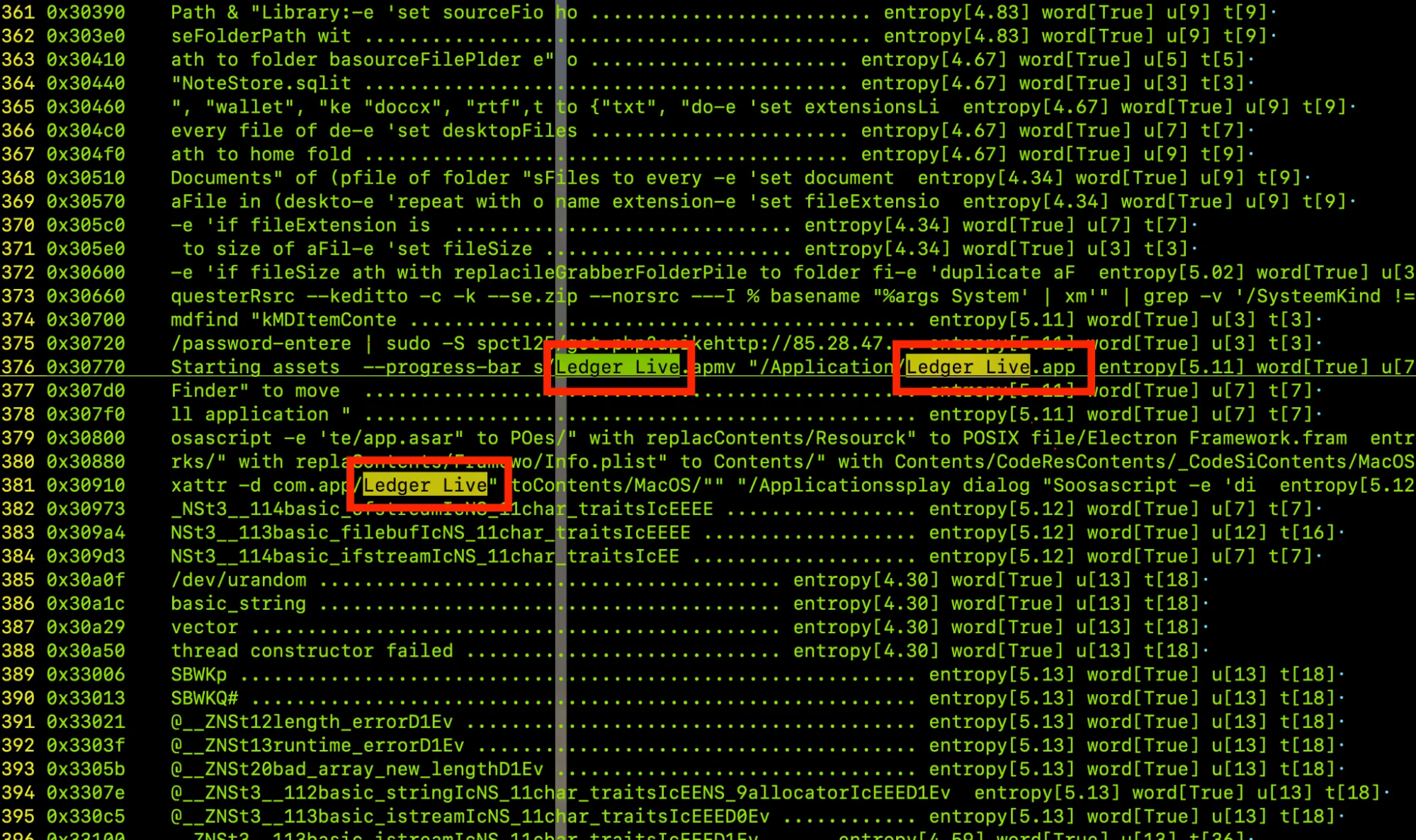
In our investigation, we found strings containing “Ledger” in the infected files we hunted, further confirming the malicious intent towards users’ cryptocurrency assets. This particular version is identified as a variant of AMOS and retains all the key features, such as grabbing files, hardware information, passwords, data from browsers, keychain dump credentials, and more.
Darknet recruitment and attribution
The day before, we saw recruitment ads on the darknet seeking individuals to join a team using this variant of macOS stealer. The recruitment announcement, posted by Crazy Evil and titled “RECRUITMENT IS OPEN,” details the benefits of working with them, including a macOS/Windows stealer with reliable protection, exploiting various formats for different victims, and replacing Ledger on macOS.
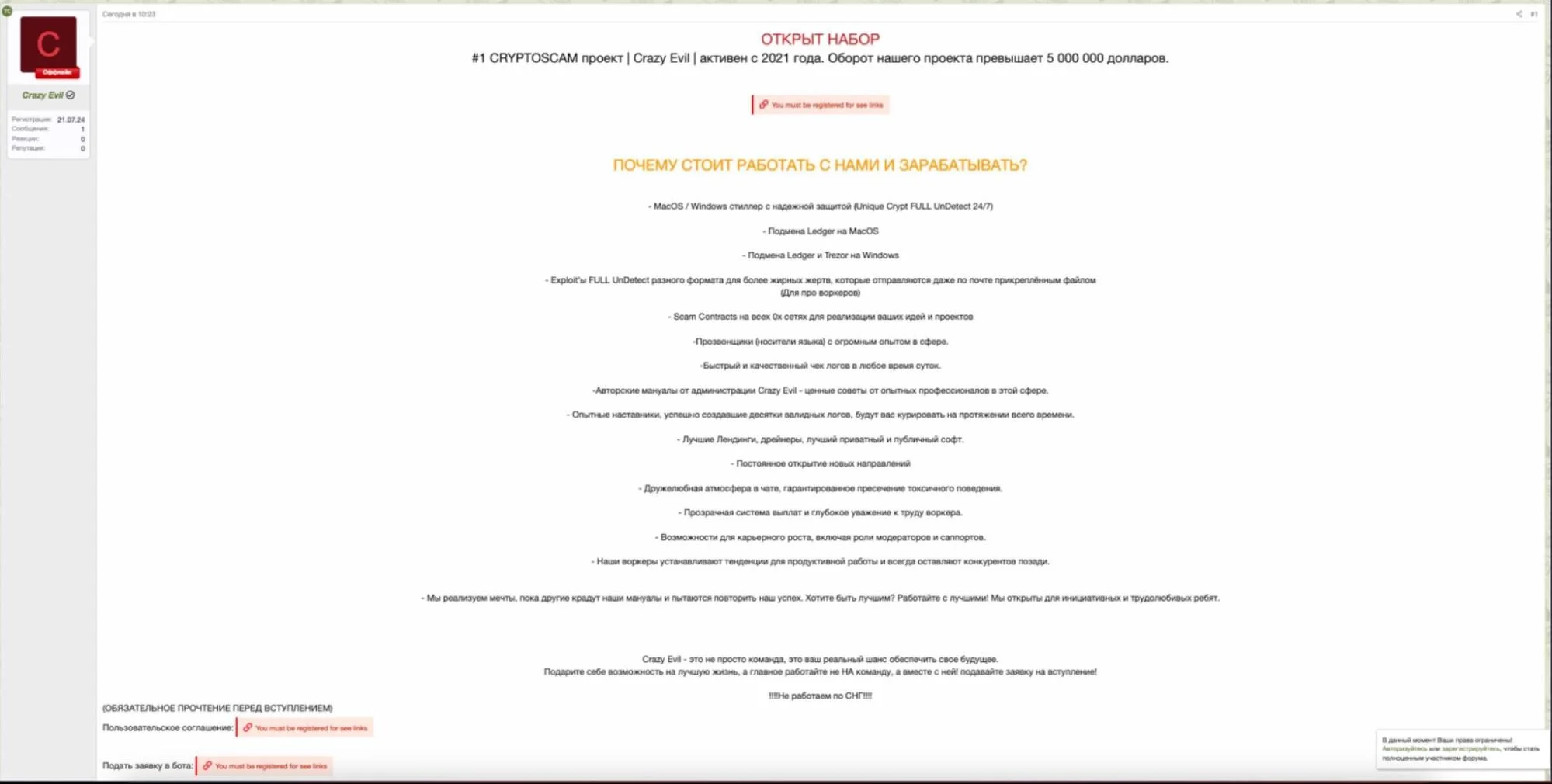
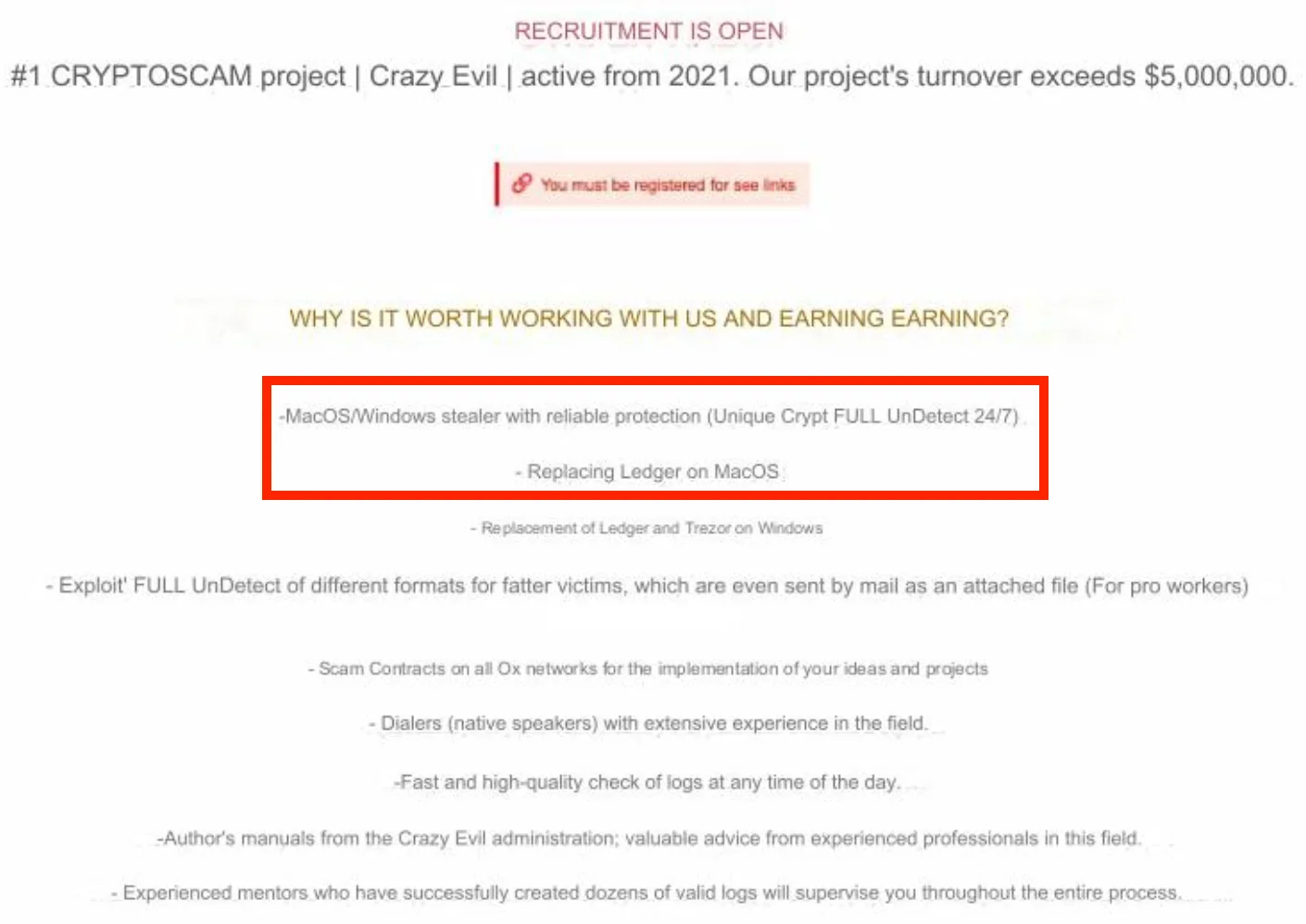
All this suggests that the Crazy Evil group is allegedly behind the campaign we spotted over the course of the next few days. As a side note, Crazy Evil seems to be a well-organized group that communicates with its partners and recruits via a Telegram bot.

Interestingly, during our investigation of samples with functionality similar to the fake Loom threat, we were able to identify an IP address with a high malware association linked to a governmental entity. The IP address, 85[.]28[.]0[.]47, has zero detections on VirusTotal but has 93 files marked as malware in the Memory Pattern Parents field. We observed that macOS-related files from the campaign started appearing there on July 23, 2024.
![A screenshot of the results for the IP address 85[.]28[.]0[.]47 on VirusTotal.](https://moonlock.com/2024/07/11_virustotal.webp)
Conclusion
Our investigation into the recent macOS stealer campaign has brought to light several critical findings.
The attackers have employed deceptive Google-sponsored URLs to distribute malware, targeting popular applications to trick users into downloading malicious files. And the infection chain is sophisticated, involving the replacement of legitimate apps like LedgerLive with malicious clones.
Additionally, we discovered the recruitment of cybercriminals via darknet advertisements and identified an IP address linked to a governmental entity, likely leveraged for malicious purposes.
For individuals and organizations, it is crucial to stay informed about such threats and adopt proactive security practices. This includes regularly updating software and being cautious of communications, especially those promising lucrative deals or contracts.
Always pay close attention to URLs when downloading files, even if they come from Google Ads or top search results. Additionally, it’s a good practice to scan your devices with anti-malware tools like CleanMyMac X with the Moonlock Engine to ensure that no malicious software is present.
Indicators of compromise
| f2ce2113938b923add1c9c338e438966a1c5783aba3e42d46b2c52b97d3d1753 | SHA256 | LoomDMG |
| ed3245c6a3e2bcb11dd22f65e9c397f8bf6cffcf4280e3f16a30b7c8b362bd09 | SHA256 | Firefox Mach-O |
| e2e36eb97bbfe6696ca1ed472b573af676d1a50dc8ecf456ae582fa0feee436a | SHA256 | TunnelBlick Mach-O |
| 856043eae6c9c9cfdca108076eda47e1abd3c3f17d44434eff299693dbf323ab | SHA256 | BlackDesertPersonalContractforYouTubepartnersDMG |
| 5a31c8ee2f76fadc9d9900f02573d809ff8fc01c066331928533d74afa3be02c | SHA256 | LoomDMG |
| ad32880c7f0e814d175b8170e3cef8459752b6c5818819d6d55512d948e24626 | SHA256 | FigmaDMG |
| 0a0ff972ea5c16f0ad3e090613d32b873768367b47f2f4e26737fec2c5168556 | SHA256 | CallzyDMG |
| smokecoffeeshop[.]com | Domain | Phishing site |
| hxxps://wouldyougunna[.]com/yvfiubhferwewf/process_l00m.php | URL | Malware download URL |
| 85[.]28[.]0[.]47 | IP | IP address with a high malware association |
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.