For the past few years, macOS malware has been on the rise, with information stealers, malvertising, phishing, and AI-driven attacks impacting Apple users. But not all attacks start with malware.
As the software and technology industry pushes innovation and global market competition drives the creation and release of new operating systems (OS), apps, software, and APIs, a major risk lurks in the background: vulnerabilities.
Cybercriminals welcome new software and OS releases, as they are the perfect opportunity to find new weaknesses to exploit them in attacks. Not surprisingly, a new report found that Apple users are being affected by this trend.
Apple operating systems rank high in terms of risk
The recently released Action1 Corporation report “Software Vulnerability Ratings 2024” identified 5 top vulnerability threat trends. Apple’s OS risks came in second on the list.
Action1’s report concluded that macOS and iOS exploitation rates increased by 7% and 8%, respectively, in the past year.
While the number of macOS vulnerabilities dropped by 29% in 2023, the exploitation of these vulnerabilities rose by more than 30%. On the other hand, iOS reported 268 vulnerabilities, of which attackers exploited 20. This contrasts widely with Android, which had 1,421 vulnerabilities in the same year, of which only 3 were exploited.
Action1 said that iOS has been the leader in Remote Code Execution (RCE) counts over the past 3 years.
“These findings underscore the targeted nature of attacks on iOS devices, possibly due to the perception of the valuable data they store,” the report reads.
These findings underscore the targeted nature of attacks on iOS devices, possibly due to the perception of the valuable data they store.
Action1 Corporation report, “Software Vulnerability Ratings 2024”
OS vulnerabilities accounted for around 75% of all vulnerabilities analyzed by Action1.
Apple vulnerabilities drop, and exploitation rises — but why?
The Action1 report reveals that while Apple vulnerabilities are significantly lower than those linked to other operating systems like Windows or Linux, the exploit rates for Apple operating systems are higher.
For example, Windows desktop OS still has the highest number of vulnerabilities, but the exploitation rates for the OS remain stable at 4%.
In the mobile operating systems segment, there is an even greater disparity, as mentioned above. iOS exploitation rates of 8% proved to be higher than those of Android, set at 0.2%. But what does this all mean?
Action1 suggests that the rates of exploitation are linked to cybercriminals” perception that Apple users’ data is more valuable than those using other operating systems. However, the report also warns that “for some reason,” Apple is not managing to fix vulnerabilities before attackers exploit them.
Innovation and pushing the envelope to sustain global leadership in tech markets may be Apple’s strength, but it is also its Achilles heel.
Apple’s security updates and Rapid Security Responses list more than 45 security updates in 2024 released to secure different operating systems on Apple devices, including iOS, macOS, watchOS, Vision Pro, and others.
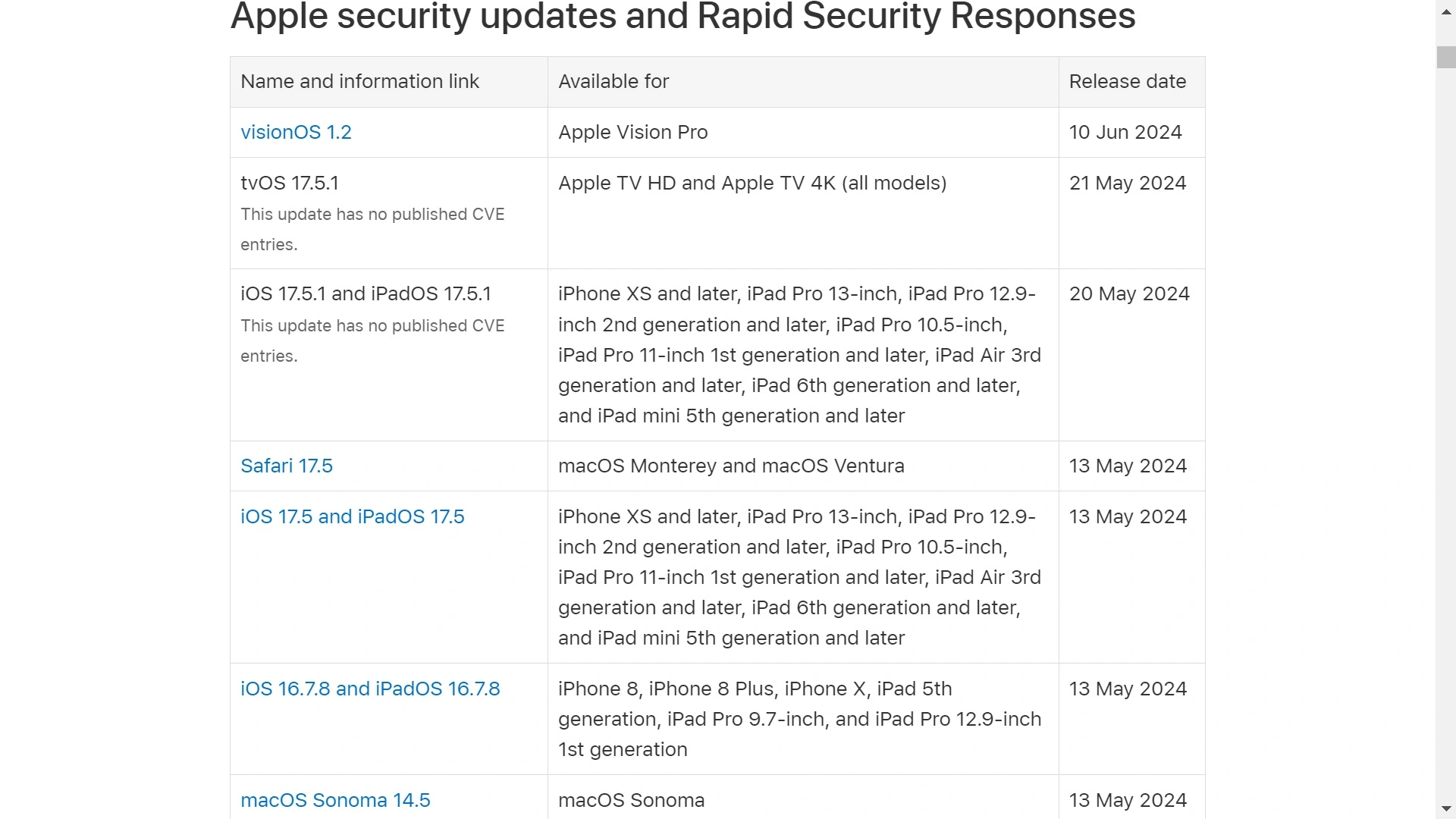
Evidently, the accelerated rate of upgraded software and OS versions that Apple puts out in the world has hidden security and privacy costs. Like other companies, Apple periodically seems to be working to put out fire after fire, at times releasing up to 9 urgent security patches on the same day.
However, there is another wider issue that is affecting the cybersecurity vulnerability sector, and its responsibility is nowhere near that of the company from Cupertino.
The NVD crisis results in vulnerabilities database being paused since February
The US National Vulnerability Database (NVD), run by the National Institute of Standards and Technology (NIST), is responsible for listing information on software and hardware flaws that potentially could lead to security incidents. The NVD is not just critical to US national cybersecurity but a vital tool for all international software and hardware vendors.
NIST compiles the NVD information from sources like security researchers and vendors who discover vulnerabilities. This information is then organized and analyzed according to technical details and cataloged according to standards that identify the severity of a vulnerability and its impact.
The standardized NVD format provides clarity for security vendors everywhere. NVD does not create security patches but might suggest solutions at times. The most important role of the NVD is to make everyone aware of the top security weaknesses and exploitations in the wild.
However, over the past months, NIST has almost completely stopped adding analysis to Common Vulnerabilities and Exposures (CVEs) listed in the National Vulnerability Database.
What does the NVD crisis mean for the future of cybersecurity?
The NVD crisis represents a challenge for vendors like Apple. Paused since February, initiatives to restart the NVD have been slow and painful.
On May 29, NIST announced it had awarded a contract for additional processing support for incoming Common Vulnerabilities and Exposures (CVEs) for inclusion in NVD.
“We are confident that this additional support will allow us to return to the processing rates we maintained prior to February 2024 within the next few months,” NIST said in the press communication.
Responding to the backlog of unprocessed CVEs that has been building up since February, the NIST said it is working with the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) to facilitate the addition of these unprocessed CVEs to the NVD.
“We anticipate that this backlog will be cleared by the end of the fiscal year,” NIST said.
The report from Action1 recognized the challenges that the NVD crisis represents to the industry, especially at times when the volume of vulnerabilities being identified in the wild is staggeringly high.
Vendors and cybersecurity experts describe the NVD repository as critical to providing much-needed insights into the ever-evolving vulnerability landscape for software.
Mike Walters, President and Co-founder of Action1, called for security leaders and organizations to navigate the NVD crisis together in a press release.
“In light of the NVD crisis, the cybersecurity community needs to share information and build stronger relationships amongst private cybersecurity firms, academic institutions, and other threat intelligence platforms to facilitate holistic and timely data sharing so that all organizations can enhance their security posture.”
How does this affect Apple users?
Apple users are affected in many ways due to the state of vulnerabilities. For example, Apple relies on the NVD for vulnerability analysis data. Delays in this data could result in Apple taking longer to identify and patch vulnerabilities in their software, leaving iPhones, iPads, and Macs exposed for longer periods of time.
Apple, like other vendors working with NVD repos, may also have difficulty prioritizing which vulnerabilities to address first, as the complete analysis from the NVD presents risk standards used to identify weaknesses that demand urgent patching.
Additionally, Apple might be impacted by slower patching processes due to NVD delays — creating a situation where the company is constantly playing catch-up on security fixes.
However, it’s important to remember that Apple has a strong internal security team and may have alternative methods for identifying vulnerabilities rather than solely relying on the NVD. Additionally, security researchers often disclose vulnerabilities directly to Apple, allowing them to issue patches before the NVD is released or updated.
Despite all this, one thing is clear: With the NVD repos out of the game, bad actors have an advantage.
Apple did reduce the number of critical vulnerabilities in macOS by an impressive 62% from 2021 to 2023. However, it still reported a significant number of exploited vulnerabilities in 2023, resulting in a significant exploitation rate of 7%.
Additionally, while iOS shows a decrease in total vulnerabilities from 2021 to 2023, it is the leader in total RCE count over the 3 years analyzed. The OS also has a 100% increase in the number of exploited vulnerabilities in 2023.
Unfortunately, this trend shows no signs of slowing down in 2024 and could, in fact, be accelerating.
Other findings that impact Apple users’ security and privacy
The Action1 report also found vulnerability-critical issues related to office apps, document viewers, password managers, web browsers, antivirus software, image editors, and web browsers. All these vulnerabilities affect Apple users.
In total, 2023 saw 4,359 vulnerabilities, of which 107 were exploited. Office apps, including Microsoft Office, LibreOffice, and OpenOffice list, 226 vulnerabilities, and document viewers like Adobe — the most targeted PDF viewer analyzed, accounting for 74% of all vulnerabilities in the category — are listed at 270. Web browsers represented one of the most affected categories after operating systems, with a total of 1,024 vulnerabilities identified.
“Unsurprisingly, Chrome has the highest total number of vulnerabilities reported over the 3 years, with 1,006 vulnerabilities,” the Action1 report reads. “It leads significantly over Firefox (471 vulnerabilities) and Edge (178 vulnerabilities).”
While only 4 vulnerabilities were discovered for password managers, including KeePass, 1Password, Bitwarden, and LastPass, the number may not represent a strong security posture but rather potentially underreported or undiscovered vulnerabilities.
The LastPass 2022 security breach and other password managers’ security incidents clearly show that the sector is not immune to attacks.
Regarding Antiviruses, Action1 identified vulnerabilities in Avast, Bitdefender, Malwarebytes, Eset, Kaspersky (recently banned by the US due to national security concerns), and McAfee.
How to protect your Mac or iPhone data
While Apple continues to improve the security of its devices, vulnerabilities still exist and are actively exploited by attackers. Here are some steps you can take to protect your Mac or iPhone data:
- Install software updates promptly: Apple frequently releases security patches to address vulnerabilities. Installing these updates as soon as they become available is essential for keeping your device safe.
- Use strong passwords and enable 2-factor authentication: A strong password is at least 12 characters long and includes a mix of uppercase and lowercase letters, numbers, and symbols. 2-factor authentication adds an extra layer of security by requiring a second code in addition to your password to log in.
- Be mindful of what apps you install: Only install apps from trusted sources, such as the App Store. Before installing an app, read reviews and check the developer’s reputation.
- Use a reputable antivirus or internet security suite: While Apple devices are generally considered secure, an antivirus program can provide additional protection against malware and other threats.
- Back up your data regularly: Regularly backing up your data to an external drive or cloud storage service ensures that you can recover your files if your device is lost, stolen, or damaged.
By following these tips, you can help keep your Mac or iPhone data safe from even the most sophisticated attacks.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iPhone, iOS, Mac, and macOS are trademarks of Apple Inc.