A remote access trojan (RAT) targeting Windows devices since at least 2020 has been updated and modified to go after Mac users.
Remote access trojans present themselves to victims as legitimate downloads. Once the malware hidden in the fake download unpacks and auto-executes, it establishes a connection with a command-and-control (C2) server controlled by attackers. From there, the bad actors take full control of your computer as if they were sitting in front of it.
HZ RAT pivots from targeting Windows devices to Mac users
On September 5, Intego reported that a new version of HZ RAT, built to breach macOS environments, is being distributed in the wild. While Intego does not provide attribution details, historical reports on HZ RAT point to China as the origin host for this malware.
HZ RAT may not be a stealer, but it is sneaky and persistent, and it can steal data and spy on users. As a remote access trojan, the malware gives the attacker full remote administrator privileges.
The malware can take screenshots, record what a user types, steal data from Google Password Manager, and go after user data to breach their WeChat and DingTalk — both of which are popular Mac apps in China.
Other than information gathering, the real motive behind this campaign is unclear. More concerningly, the malware also has a low detection level by security vendors.
How is this malware distributed?
How this malware is being distributed by bad actors is still unknown. However, some sites and domains have already been identified as hosting this malware.
Additionally, Intego found a sample of malware impersonating the VPN app OpenVPN Connect. An investigation by Secure List also confirms that this malware is impersonating OpenVPN Connect.
A 2022 investigation of the Windows version of this malware also identified several Chinese IPs and domains linked to this malware campaign, including:
- oa.pumch.cn
- finance.yto.net.cn
- Sgwpdm.ah.sgcc.com.cn
- finance.yto.net.cn
- ww.hbzyjxkh.cn, hbszyy.gcptrial.com, zhyy.hbszyy.cn
- dsm.hn.sgcc.com.cn
- sgwpdm.ah.sgcc.com.cn
Intego believes the new Mac malware may be distributed via fake malicious Google Ads, website impersonation, or watering hole style attacks. Because no specific attack vector has been identified, Mac users are cautioned to only download software through the official Apple App Store.
Domains and IP analysis of HZ RAT
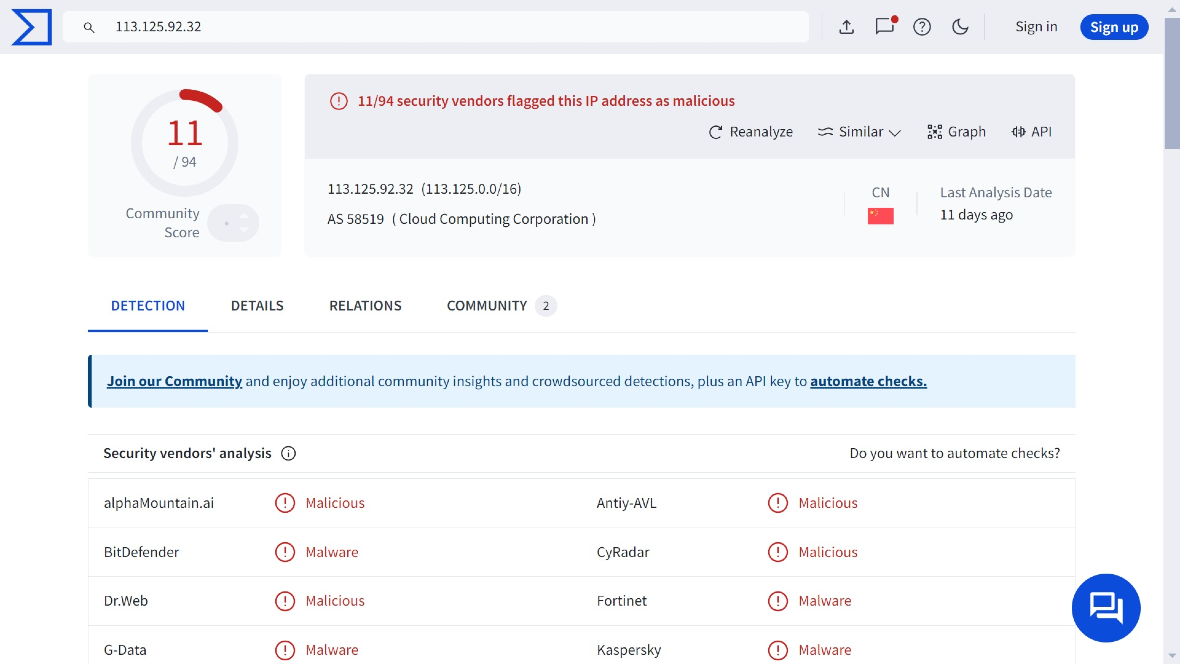
For some time, this RAT has flown below the radar. Even now, according to VirusTotal, the IPs and domains linked to the campaign are flagged as malicious by only a handful of security vendors.
Of the C2 IP addresses linked to this malware, most seem to be located in China:
- 20.60.250[.]230
- 29.40.48[.]21
- 47.100.65[.]182
- 58.49.21[.]113
- 111.21.246[.]147
- 113.125.92[.]32
- 120.53.133[.]226
- 123.232.31[.]206
- 218.65.110[.]180
- 218.193.83[.]70
Moonlock pinged and ran traceroutes for the IPs in the list and found that about 80% of the IPs were active but unreachable. These findings imply that someone pulled the plug on a component and looped the connection for it to time out. The other 20% of IPs were inactive.
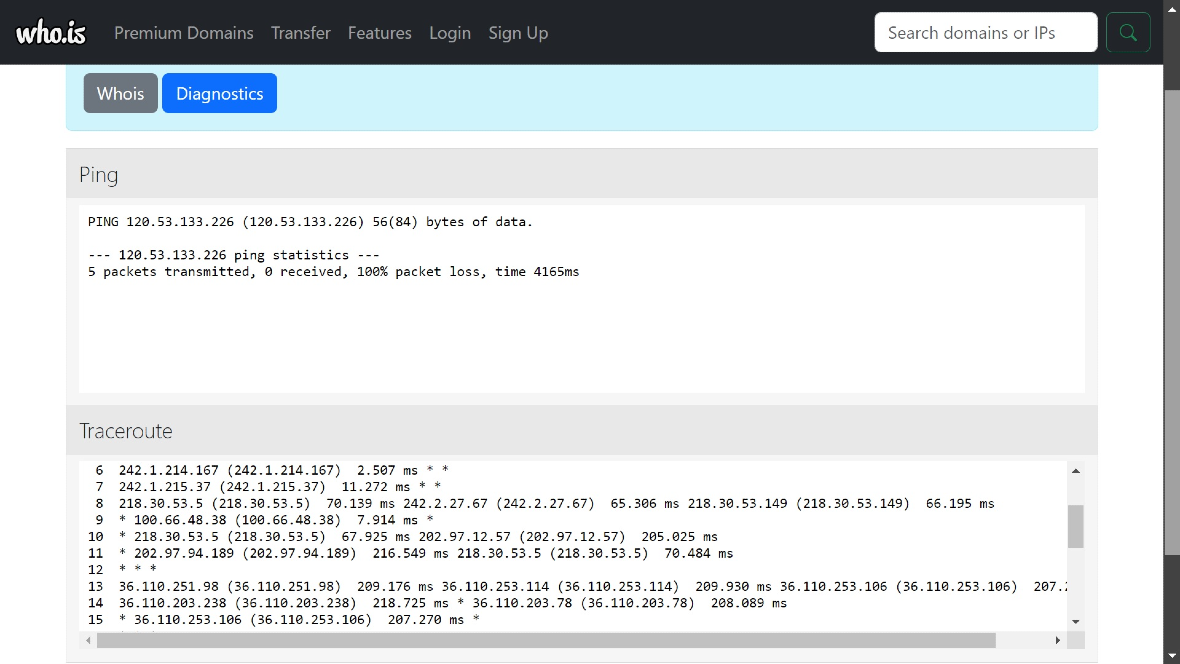
Additionally, the registry and update dates for some of the IPs in this campaign are very dated, at times up to 10 years old or more.
Traceroute information shows asterisks (*) indicating unanswered requests at some points. The IP traceroute data also reveals repetitive hops, appearing multiple times, indicating potential routing loops or load balancing.
If the attackers were exposed or faced increased scrutiny due to media coverage, it’s possible that they abandoned the infrastructure associated with the HZ RAT campaign to avoid further detection.
Simple Mac malware that can cause a lot of damage
The HZ RAT malware itself is quite simplistic. Once it installs, it connects to a command-and-control server to receive further instructions. This means the attacker can remotely run PowerShell commands and scripts, write arbitrary files to the system, and upload and extract files to the attacker’s server.
Analysis by Intego shows that the backdoor supports only 4 commands:
- execute_cmdline: Execute shell command
- write_file: Write file to disk
- Download_file: Send file to server
- ping: Check victim’s availability
The malware can gather the following data from a breached Mac:
- Local IP address
- Bluetooth devices data
- Wi-Fi networks and wireless network adapters data
- Information about the network the device is connected to
- Hardware specs
- Data storage info
- List of apps in the breached device
- Information from WeChat
- User and organization data from DingTalk
- Username and websites from Google Password Manager
While the malware does not extract passwords from Google Password Manager, it is believed that actors may be using stolen password leaks, bought on the dark web, to pair with the username and other data they extract using the malware.
Final thoughts
A piece of malware that used to target Windows devices and has shifted to target Mac users — specifically in China by bad actors in China — is not a common occurrence.
While some believe the malware is a generic bulk data extractor, due to its capabilities, it may also conduct illegal surveillance of civilians, foreigners, journalists, or activists.
To protect your Mac from this and other threats, always download software from reputable sources like the Apple App Store. Be cautious of suspicious emails, links, or attachments, and keep your operating system and security software up to date.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and the Apple App Store are trademarks of Apple Inc.






