Information stealers targeting Mac users are nothing new. In fact, they have become a steadily growing trend in the past 2 years. What is new is a combination of stealer and spyware, which is exactly what the actors behind a recently discovered criminal campaign are doing.
Given the nature of the distribution tactic that this new malware has — fake websites offering converters for popular music services like Amazon Music, Spotify, and Apple Music — it can be assumed that this attack is going after regular Apple users and not spear-phishing for high-value targets. However, this doesn’t make the malware any less dangerous.
Let’s dive into this new malware to learn what it can do and how you can stay safe.
The new threat targeting Apple users
On April 30, Kandji researchers published their investigation on the new malware dubbed “Cuckoo.” While the name itself may sound harmless, researchers explain that the name comes from a bird that lays its eggs in nests that do not belong to it, confusing the real owner of the nest into feeding and raising foreign hatchlings.

Cuckoo: A display of power and resources
It’s clear that the Cuckoo operation isn’t an amateur campaign. Kandji researchers first discovered the malware in April 2024 after a sample was uploaded to VirusTotal. A rapid Google search led them to the host website, dumpmedia.com. The website (active at the time this report was being written) offered several apps that were not available through official app stores like the Apple App Store.
Kandji researchers, who originally believed that the malware was only found in one of the apps called DumpMedia Spotify Music, soon realized the issue was much more serious.
“On further investigation, we found it to be more widespread. Not only were other applications hosted on the DumpMedia site found to be malicious, but also those on additional websites hosting similar tools.”
Moonlock found that all sites linked to malware are up and running, including tunesolo[.]com, fonedog[.]com, tunesfun[.]com, and tunefab[.]com. Through these rather well-designed websites, the attackers offer iOS and Android data recovery tools, WhatsApp recovery tools, popular music service converters, and more.

As usual, these sites present themselves as legitimate websites to trick potential victims into downloading the apps.
The malware-linked apps on DumpMedia
The main site, DumpMedia, home to the malware sample analyzed by Kandji researchers, offers the following apps:
- Spotify Music Converter
- Apple Music Converter
- Amazon Music Converter
- DeezPlus
- Pandora Music Converter
- Video Converter
- Video Downloader
- Audible Converter
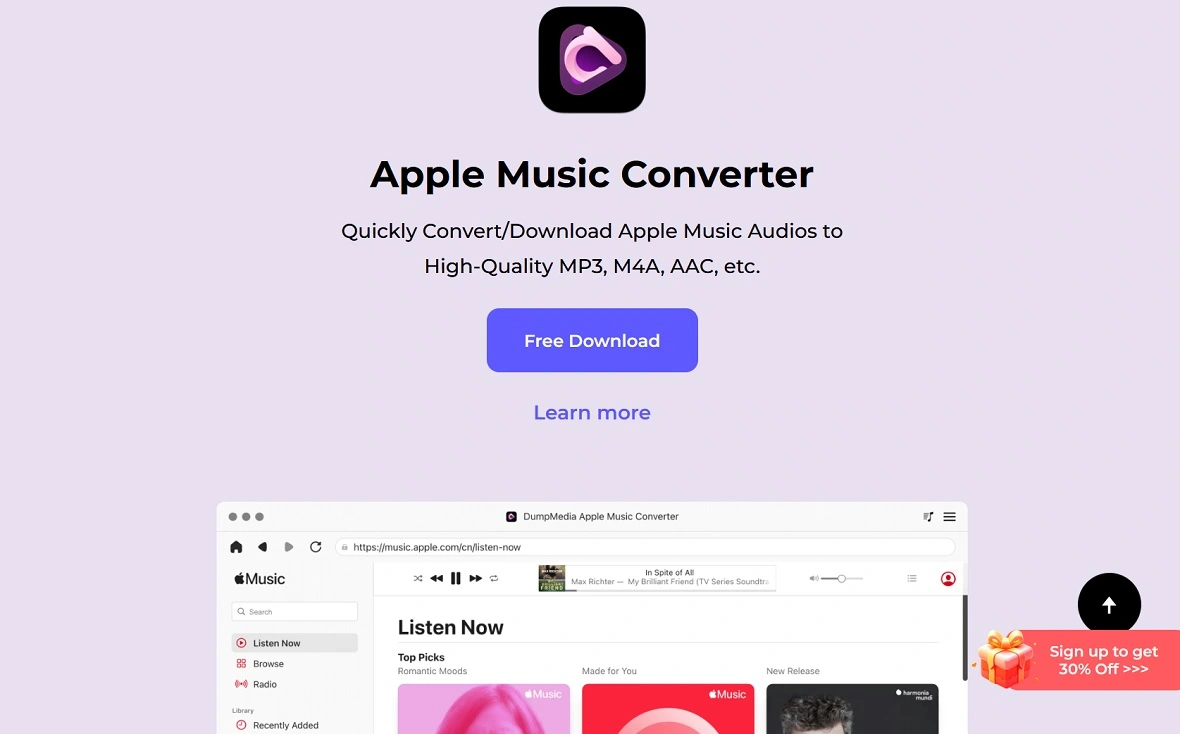
The website DumpMedia also offers features like 24/7 support, free trials, SSL-secure payments, and refund policies. It also has Twitter, YouTube, and Facebook channels specifically designed to keep up appearances and pose a legitimate business. Dangerously, these apps are available to download for Mac and Windows.
Kandji researchers believe that the malware may have spread beyond these websites. Moonlock confirmed this suspicion to be true.
Who is behind the new malware?
A group of criminals and black hat hackers who manage to pull off this type of operation should be considered well-experienced and abundant in certain resources. Here’s why:
- Creating multiple malicious app sites: This indicates knowledge of app development and distribution methods, as well as the ability to manage multiple online presences.
- Social media savvy: Having YouTube, Twitter, and social media channels suggests a well-rounded understanding of online manipulation and audience engagement. These platforms can be used to spread awareness of malicious apps and build a false sense of legitimacy. Avoiding the shutdown of social media channels also requires knowledge.
- Staying hidden: The ability to evade detection and keep their sites operational demonstrates advanced techniques for covering their tracks. This could involve anonymization tools, exploiting vulnerabilities in hosting platforms, or constantly shifting tactics.

While Kandji researchers have not attributed this campaign to any specific group, they have identified the valid Developer ID of Yian Technology Shenzhen Co., Ltd (VRBJ4VRP) linked to almost every site listed in the compromised sites list.
Environmental variables taken into account by malware raise questions
Part of Kandji’s investigation revealed a surprising twist. Cuckoo malware is coded to check for system environmental variables, which is used to determine whether the malware will load. Kandji broke it down, explaining how the variable check works.
“The point is that the creators of this malware did not want to infect devices in 5 countries:
- Armenia
- Belarus
- Kazakhstan
- Russia
- Ukraine”
The Chinese-language Valid Developer ID, combined with this variable check that prevents the malware from operating and installing on devices located in specific countries, poses several questions. It also provides hints about who could be behind this new attack and what agenda these criminals have.
What can Cuckoo do? How dangerous is it?
As a stealer and spyware, Cuckoo has several damaging tricks under its sleeve. For example, stealers are not known for executing persistent attacks — remaining for long periods of time in an infected device without the victims’ knowledge. But because the malware is also spyware, it has features that allow it to do exactly that.
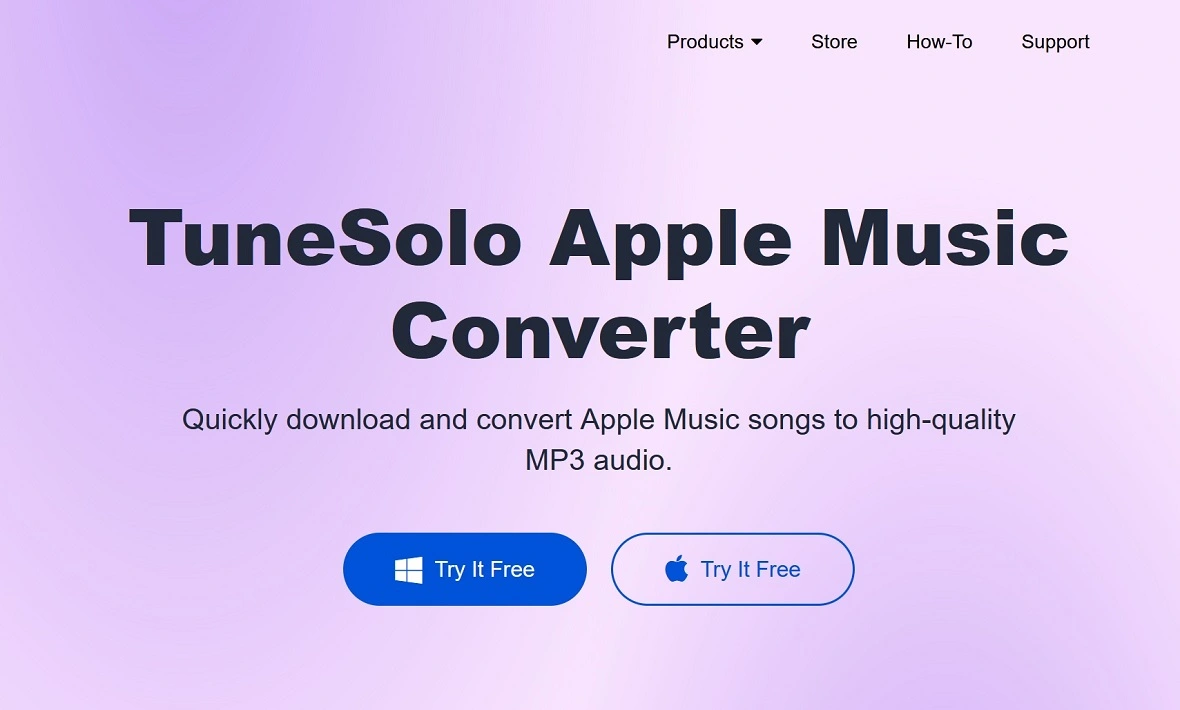
Once a victim downloads malware from these fake websites and follows the on-screen steps to install the file, the malware begins its operation.
Cuckoo can:
- Trick users into giving away passwords using the prompt “macOS needs to access System Settings”
- Steal Apple passwords, test them, and run privilege escalations
- Make changes in systems, apps, and files
- Access Finder, microphone, downloads, and other apps and features
- Gather detailed information on the OS, hardware, software, and system breached
- Gain insight on currently active running processes
- Search for specific applications and specific files
- Communicate with the hackers’ Command and Control server (C2)
- Copy files related to Safari, Notes, and Keychain
- Collect app data
- Search for bookmarks, cookies, and history in web browsers
- Mute the computer to take screenshots without arousing suspicion
- Target browsers including Opera, Microsoft Edge, Google Chrome, Mozilla Firefox, and Mozilla Thunderbird
The malware also targets popular wallets, including:
- Ethereum
- Electrum-LTC
- ElectronCash
- Monero
- Jaxx
- Guarda
- Atomic
- BitPay
- MyMonero
- Coinomi
- Daedalus
- Wasabi
- Blockstream
- Exodus
- Ledger Live
- Trezor
How to stay safe from this malware
Naturally, the best defense against this type of malware is to avoid downloading the malicious file in the first place. Apple users should stay away from the following sites:
- http://tunesolo[.]com
- http://fonedog[.]com
- http://tunesfun[.]com
- http://dumpmedia[.]com
- http://tunefab[.]com
If you have downloaded an app from one of these sites, you should activate Apple’s Lockdown Mode, available on iOS and macOS devices. Lockdown Mode is an extreme security measure designed for sophisticated spyware attacks. Once activated, the Apple security feature will take drastic measures to keep you and your data safe, focusing on minimizing your digital attack surface (exposure).
After taking this precaution, Moonlock recommends that you download a trusted and professional antimalware program. At the time, only 28 out of 66 security vendors recognize the malware file in their scans, according to VirusTotal.
However, while most security engines cannot detect this new malware, it’s only a matter of time until they do. Furthermore, a professional antimalware program should certainly detect any suspicious commands running on your device and shut it down.
Users should also keep their guard up and be suspicious about similar apps that are “dedicated to ripping music from streaming services and to iOS data recovery,” especially if these are not hosted in official app stores.
Final thoughts
Not only does Moonlock agree with Kandji researchers when they say that “they assume that other websites and applications out there are hosting this malware but are not yet discovered,” but our investigation found evidence of this being true.
Moonlock found DumpMedia Spotify Music Converter download app links and information listed in sites like Softonic, DownloadIt, Softpedia, FileHippo, UpdateStar, and other online sites that host links to downloads. This proves that the operation is widespread and has been online for some time now.
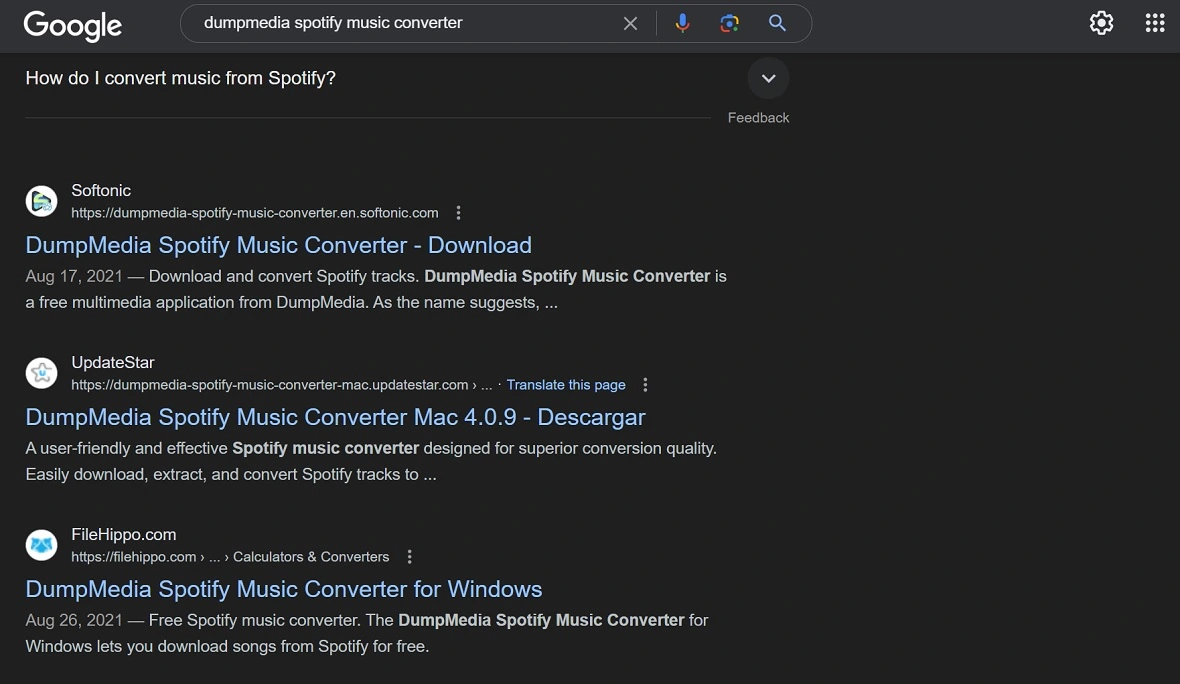
To stay safe, never download files from untrusted sources, never give the app permissions it should not require, and never give away your Apple password when prompted during an app installation. Always keep your system up to date, and have an antimalware security solution running in the background. If your browser flags a download or a website, pay attention to the warning.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, macOS, and iOS are trademarks of Apple Inc.






