The release of new operating systems and updates is never an entirely smooth ride. After all, rolling out OS globally, every year — as Apple does — is no easy task.
However, even taking into account the usual glitches that are to be expected, the new macOS Sequoia update seems to have bitten off more than it can chew. In fact, reports are emerging that suggest it is “breaking” major cybersecurity solutions, popular VPNs, and web browsers.
What services did macOS 15 “break”?
On September 16, Apple announced the release of what it called “the world’s most advanced desktop operating system.”
The highly anticipated macOS 15 Sequoia was well received and shined for its artificial intelligence integration. But just 2 days later, users, companies, and media reported major problems with security, browsers, and VPNs.
Specifically, the complaints say that the Apple software update “broke” CrowdStrike Falcon, Mullvad VPN, SentinelOne, and Microsoft services. It also caused problems for Chrome and Firefox browsers, as well as third-party VPNs, ESET software, Spotify, Microsoft Defender for Endpoint, and social media.
Patrick Wardle, Mac security expert and founder of the Objective-See Foundation, expressed his frustration with the update and said in a LinkedIn post that the incident is a “deja vu” event, hearkening back to the 2022 macOS 13 — also known as Ventura — release bug.
“Déjà vu?! Did Apple again release a new OS that again breaks 3rd-party security tools?” Wardle’s post reads.
Like other Mac experts, Wardle pointed at the macOS firewall as the culprit.
“Root cause appears to either be macOS firewall itself, or the lower-level networking extension subsystem that is ‘corrupting packets’ or other ‘unintentional changes’ to network structures,” Wardle said.
From Google to CrowdStrike: The solutions of experts and affected companies
While users took to social media and Reddit to express their shock and frustration, at times blaming Apple developers for not properly testing the OS during the beta developers stage, others began looking for solutions.
Wardle said that there are no good solutions at the moment. Users can either turn off the macOS built-in firewall or turn off the third-party security tools that are not working.
Meanwhile, vendors of the security software that is not working after the Sequoia update made their own internal and public-facing communications.
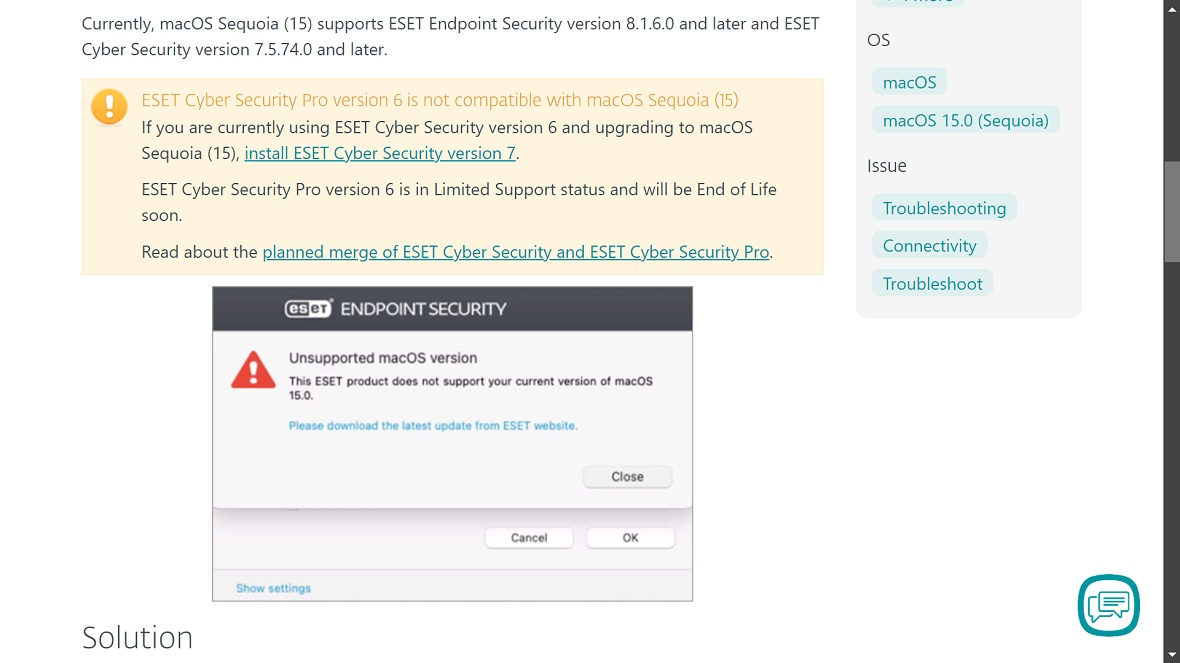
Bleeping Computer, who had access to a non-public bulletin from CrowdStrike, reported that the company advised its customers not to upgrade to macOS.
“Due to changes to internal networking structures on macOS 15 Sequoia, customers should not upgrade until a Mac sensor is released that fully supports macOS 15 Sequoia,” CrowdStrike told its customers.
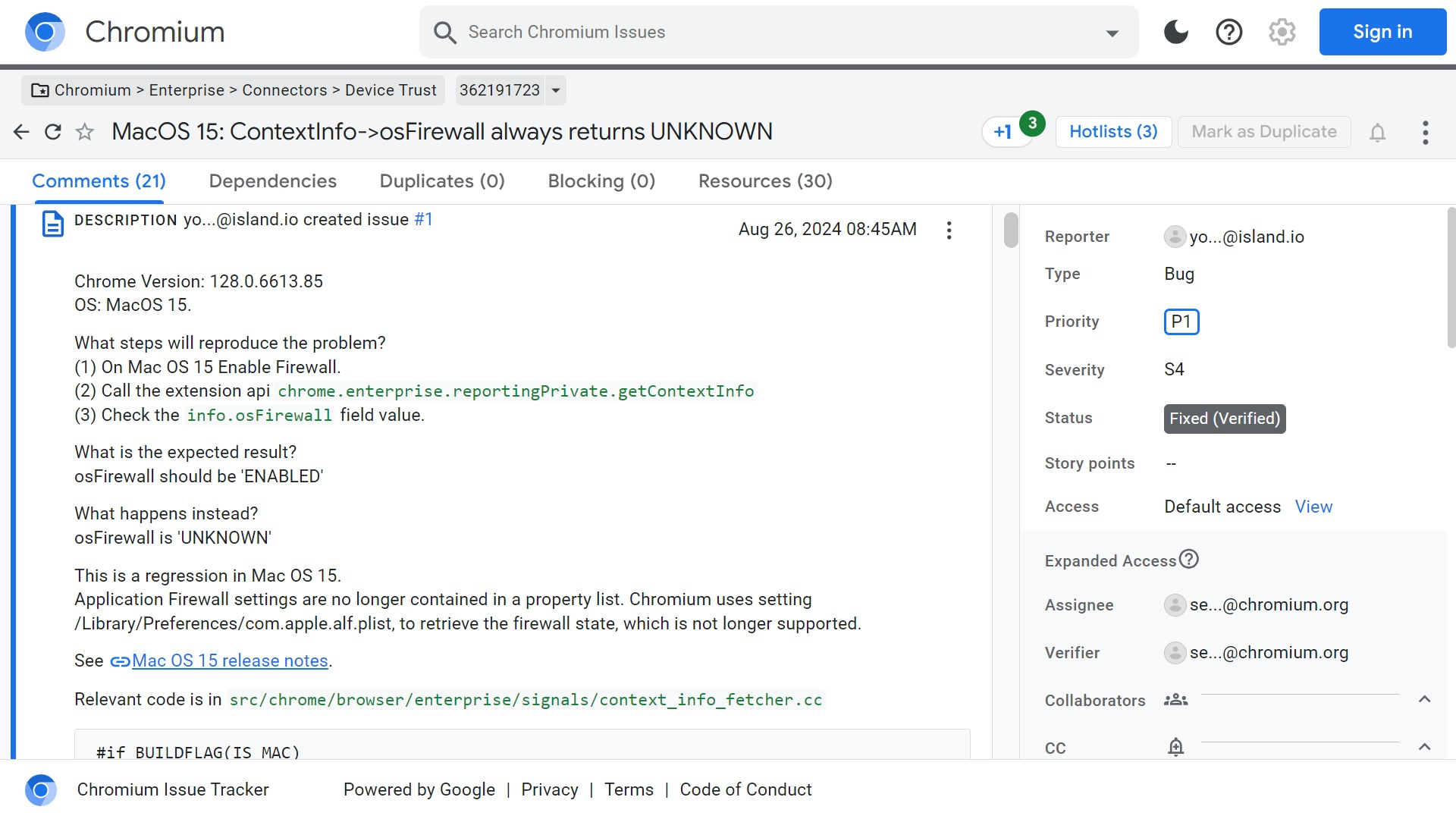
Google also addressed the macOS 15 bug affecting its browser. The report reveals how Google Chrome detects glitches with the Mac firewall settings set by the new OS.
Google said that this bug occurs when macOS 15 has the firewall enabled. Chrome then interacts with the Mac firewall and checks the field value for the firewall. While Chrome should get a verification that the firewall is ENABLED, it instead receives a status of osFirewall UNKNOWN.
Only Apple can fix the problem
This macOS 15 bug has many users and specialists turning to complex configurations to try to apply a quick fix. But, like most bugs, this one acts irrationally. Therefore, it is unlikely that anyone other than Apple, through an update, can fix the problem.
“I get it, that writing bug-free software is challenging, but maybe if Apple spent less time and money on marketing, and more time on actually testing their software, we’d all be better off!” Wardle told TechCrunch.
What can be done about Apple’s software bugs and vulnerabilities?
Evidently, the global market competition for operating systems, especially in the era of artificial intelligence, is putting pressure on Apple developers to release OSs and updates that are not fully ready for global rollout. So, what can be done?
This is not a new issue. In fact, it is getting much worse. 2024 has seen a record-high number of emergency security updates and software releases, with Apple releasing over 70 updates, emergency security updates, and OS versions in 2024.
With the release of any OS, apps, patches, updates, or new versions, the digital attack surface changes and expands. This expansion presents endless opportunities for bugs to arise.
Furthermore, the expansion of the digital attack surface also creates vulnerabilities that bad actors exploit with zero-day attacks. The fact that zero-day attacks are becoming more common is also a wake-up call for the software industry.
Google’s Threat Analysis Group (TAG) and Mandiant data found that 97 zero-day vulnerabilities were exploited in 2023, marking a significant increase compared to previous years. But 2024 has already surpassed that number.
In the first half of 2024 alone, the number of newly disclosed common vulnerabilities and exposures (CVEs) soared 30% year-on-year, from 17,114 to 22,254, according to Qualys researchers.
While companies like Apple will never be able to guarantee flawless software or OSs, as vulnerabilities are always expected with a new product, the increased rate of both CVEs and zero-day attacks signals rushed development, lack of exhaustive testing, and gaps in the Apple DevSecOps lifecycle.
Final thoughts
At this time, there is little that users and companies can do to remediate the firewall issue that is affecting third-party providers in the macOS 15 environment. Options are limited to either turning off the firewall or not engaging with the products that are failing.
While it is expected that Apple will release a patch for this bug, users are once again left to wait as they test-run a new Apple AI-driven OS, which, despite its impressive achievements, cannot get the firewall right.
If you do decide to turn off the built-in firewall in macOS 15, note that you expose your Mac to the dangers of fake and malicious sites, downloads, and other online threats.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






