The Microsoft Threat Intelligence team discovered a vulnerability and exploitation in macOS, Safari, and Apple’s TCC framework. While Apple has already patched the vulnerability, understanding how the exploitation works is useful for users to learn about the importance of permissions security and how these work on your Mac.
Microsoft researchers discover the vulnerability
On October 17, Microsoft Threat Intelligence presented a report on the new macOS vulnerability dubbed “HM Surf.” The exploitation of this vulnerability leads to unauthorized data access.
Microsoft Threat Intelligence demonstrated how threat actors could bypass the macOS Transparency, Consent, and Control (TCC) framework and technologies. By doing this, attackers can gain unauthorized access to a Mac user’s protected data.
The exploitation involves removing the TCC protection for the Safari browser directory and modifying a configuration file in said directory to gain access to the user’s data. The types of data that could be accessed by attackers include history, camera access, microphone access, location, and others without user consent.
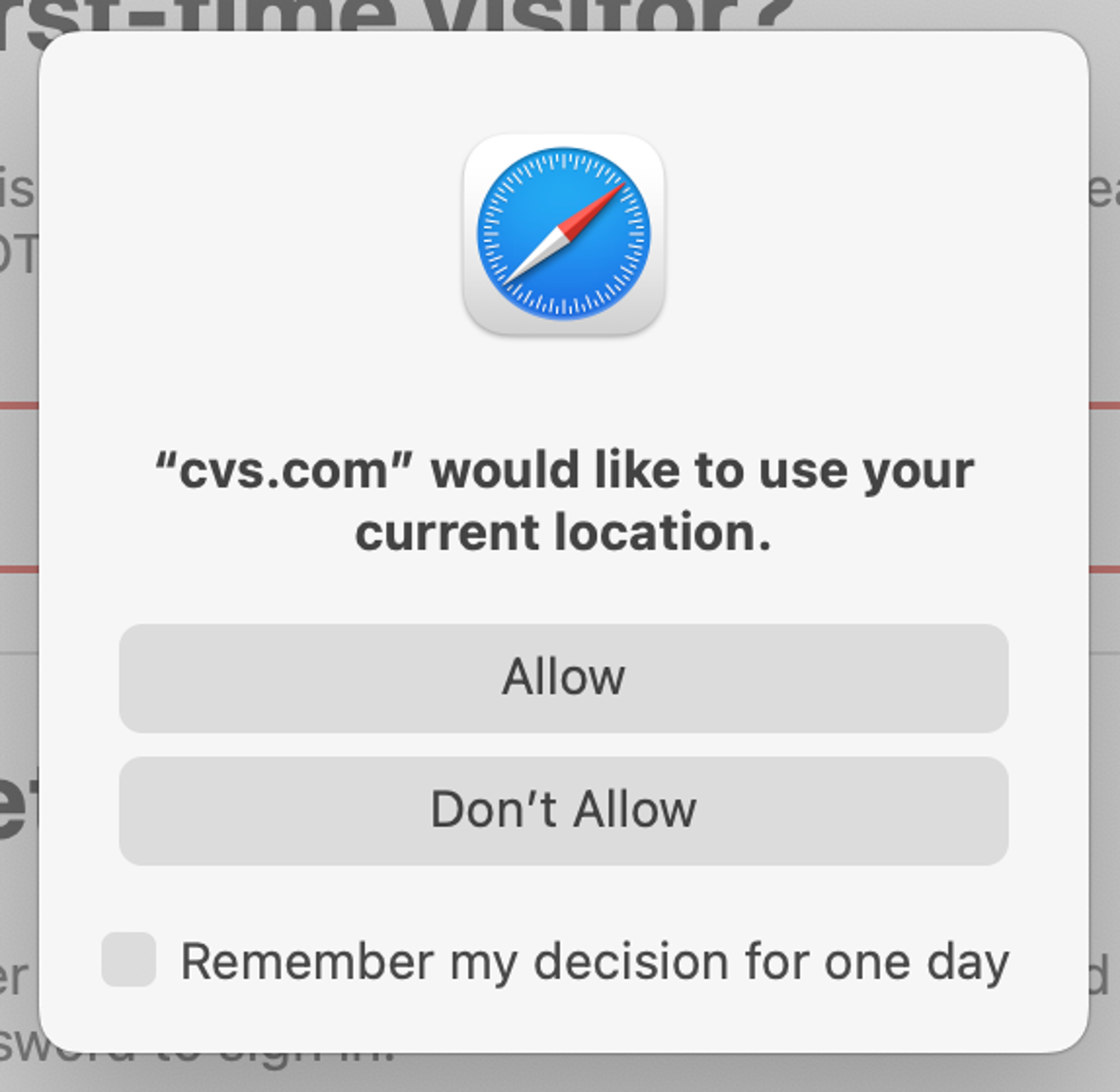
Microsoft shared their findings with Apple, and Apple released a fix for the vulnerability known as CVE-2024-44133. The fix was released with security updates for macOS Sequoia, which was rolled out on September 16.
Why TCC breaches and browser permissions matter
To understand why this vulnerability matters, even when Apple has already issued a fix, it’s important to understand that TCC bypasses and abuses related to permissions given by Apple under the TCC framework are constantly targeted by attackers looking to gain a foothold into a Mac and its user data.
Apple’s Transparency, Consent, and Control (TCC) framework is designed to protect user privacy, but criminals have found ways to circumvent it several times.
Threat actors may discover and exploit previously unknown vulnerabilities in macOS or Safari to bypass TCC protections and escalate their privileges to gain system-wide control and override TCC restrictions.
What cybercriminals can do when they bypass Apple’s TCC
Cybercriminals who bypass TCC and gain permissions may use the data they obtain to create more efficient deceptive emails or messages that trick users into clicking on malicious links or downloading malware.
They may also impersonate legitimate entities, such as Apple support, to gain trust and manipulate users into revealing sensitive information or granting unnecessary permissions.
Cyberespionage hackers also abuse permissions to access cameras, image folders, and microphones. In contrast, macOS infostealers often go after browser data to access users’ accounts.
An example of a breach and malware distribution campaign that employs these tactics is the Adload macOS threat family.
To mitigate the risks of these vulnerabilities, Apple users must ensure that their Macs are up-to-date with the latest security patches, keep an eye on the news to understand upcoming threats, emerging malware, and techniques, and understand how Apple’s TCC and web browsers’ permissions work.
How Microsoft Threat Intelligence exploited Apple’s vulnerability
Bypassing Apple’s TCC (the Microsoft way) requires some basic understanding of the framework and advanced technical skills. The bottom line is, don’t expect a wave of TCC Safari attacks, as these are highly sophisticated.
Threat actors today mostly turn to phishing, malvertising, and new social engineering techniques like ClickFix to breach your Mac, load malware, and access your data.
However, this does not mean that technical hacks don’t happen. So, let’s dive into how HM Surf works.
First, the victim’s home directory must be changed using the dscl utility, which does not require TCC access in Sonoma. This makes the ~/Library/Safari directory no longer TCC-protected. Next, attackers modify the sensitive files under the user’s real home directory (such as Users/$USER/Library/Safari/PerSitePreferences.db).
After this modification, the home directory is changed again so that Safari can use the modified files instead of the default. The browser is then opened to a webpage that takes a camera snapshot and traces the device’s location.
The problem with Safari’s private entitlement and permissions
Apple’s TCC framework prevents apps from accessing users’ personal information, including services such as location services. The problem is that Apple apps, such as Safari, are given broader permissions.
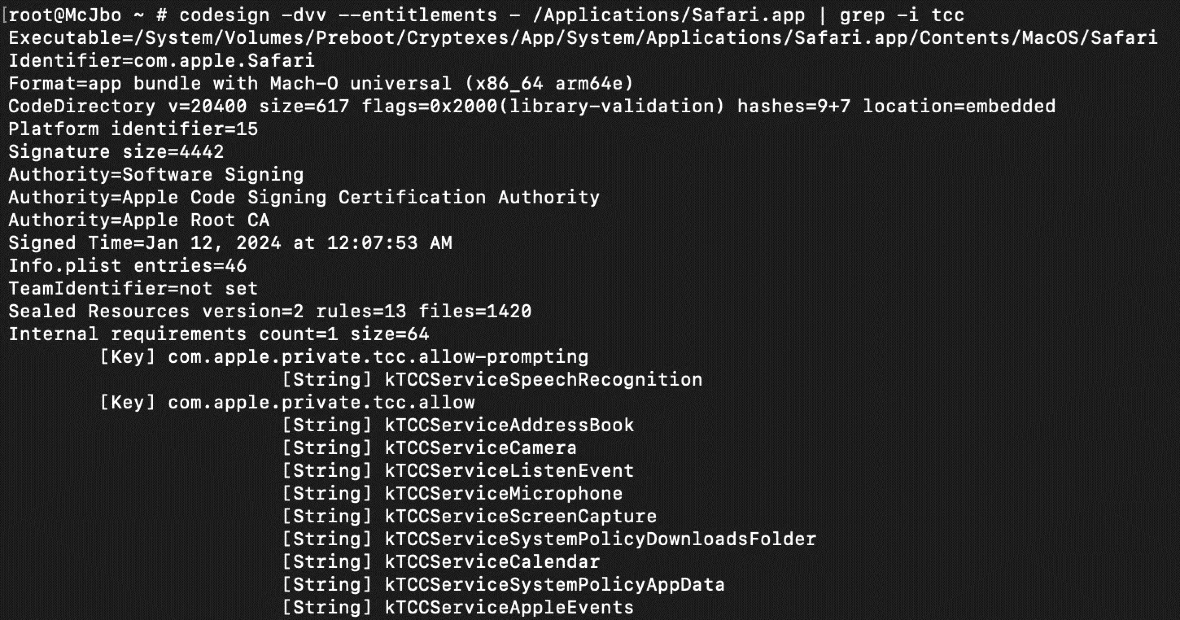
Safari’s private entitlements allow the browser to completely bypass TCC checks for services. While these private entitlements do not give Safari automatic permission to access your camera, microphone, downloads directory, and other locations without your prior consent and knowledge, they do grant Safari extraordinary permissions.
By using the dscl utility to temporarily remove TCC protection and com.apple.private.tcc.allow to suggest bypassing, TCC attackers could:
- Host the snapshot somewhere to be downloaded later privately
- Save an entire camera stream
- Record the microphone and stream it to another server or upload it
- Get access to the device’s location
- Start Safari in a very small window to not draw attention
Microsoft said that it is not known if the Adload malware campaign is running the HM Surf vulnerability or a similar tactic. They warned that bad actors could, in fact, be using this technique.
Microsoft listed the CVE-2020-9771, Time Machine mounts, CVE-2020-9934, and CVE-2021-30713 as historic vulnerabilities that run similar tactics.
So, what should Apple users do?
Apple is constantly working to improve the security of macOS and Safari. Users can expect future updates to address potential vulnerabilities and tighten security around TCC and app permissions.
However, it’s crucial to remember that security is an ongoing battle. By staying informed about threats, practicing good security hygiene, and keeping software updated, users can significantly reduce their risk of being compromised by vulnerabilities like HM Surf.
It goes without saying that if Safari or any other browser, software, or apps you download requests access to your files, camera, microphone, and/or other resources, make sure it is 100% legit.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






