BitDefender has uncovered a threat group using malvertising to distribute an information stealer known as SYS01. This development follows a trend that is becoming more popular every day among cybercriminals.
BitDefender uncovers a new large-scale malvertising campaign
On October 30, BitDefender published a report detailing the findings of their investigation into a new malvertising campaign. The attackers behind this campaign have created hundreds of malicious Facebook ads. They are estimated to have reached at least a million people in Europe, the United States, Asia, and the rest of the world.
The BitDefender analysis found that the ads — some of which are still running — impersonate video editing software like CapCut, productivity tools like Office 365 and Adobe, and video streaming services such as Netflix. They also impersonate a wide range of video games, including Grand Theft Auto and Minecraft.
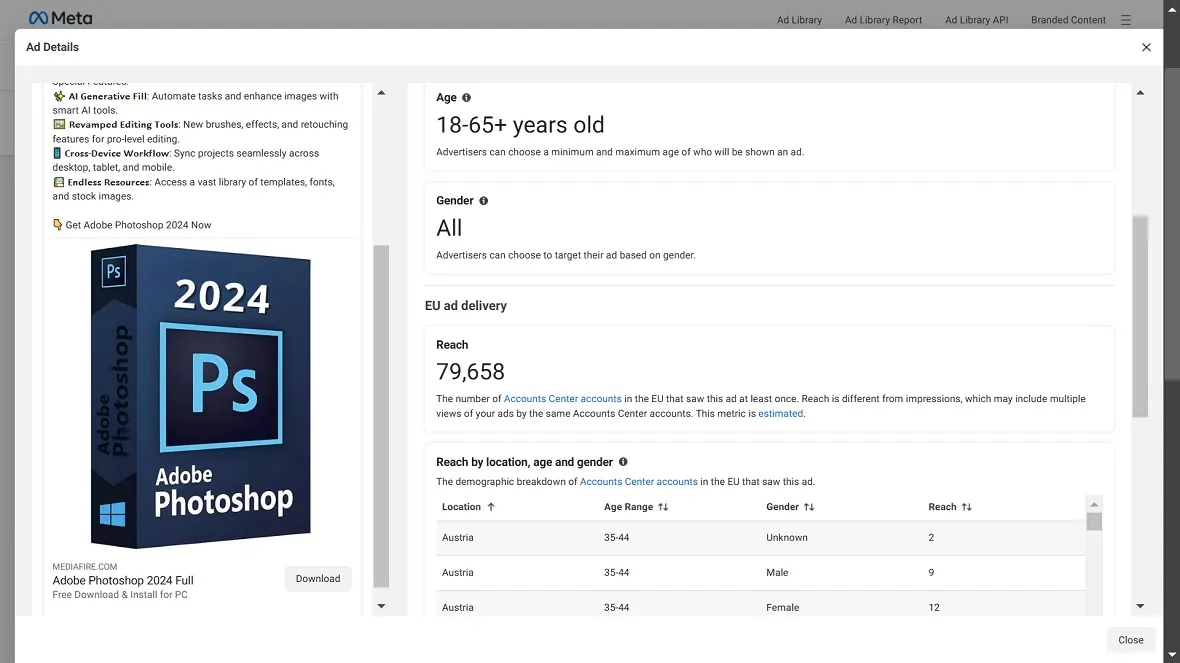
The value of Facebook Business Accounts on the dark web
The attack method is simple. Threat actors target victims globally who are aged 18 to 65 (or 23 to 65). The lack of customization of demographic targeting in these ads reveals that the group is casting a wide net and not selecting any specific type of population group.
After analyzing the SYS01 infostealer malware that the group is distributing, BitDefender warned that it is clear that they are after Facebook Business Accounts.
Facebook Business Accounts are highly priced in the underground dark web market. Having the credentials to breach Facebook Business Accounts allows bad actors to rapidly delete all existing account data. They can then change configurations and passwords to block out users, upload impersonating content, and, most importantly, use the accounts to promote their malicious sites by abusing the Facebook Ads platform.
“The scope of this attack is global, with potential victims in the millions, spanning regions such as the EU, North America, Australia, and Asia — particularly males aged 45 and above,” BitDefender said in the report.
The group can also use the stolen information for illegal financial gains and continue to scale their attacks.
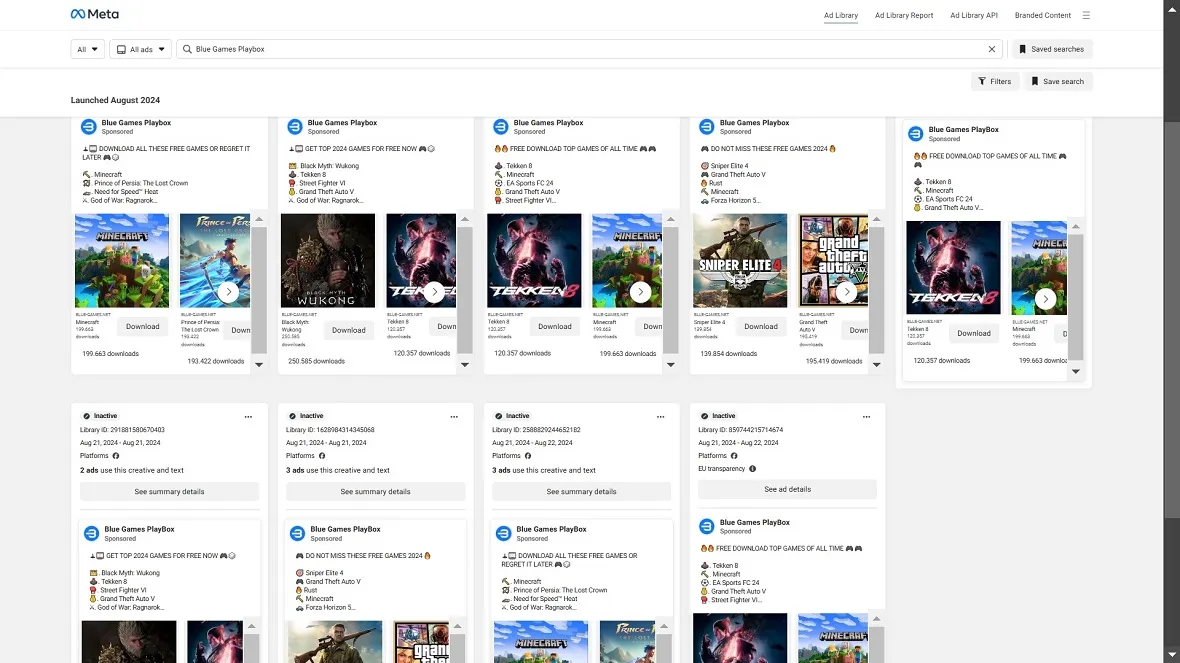
Criminals develop a large-scale malicious infrastructure
The ability to develop hundreds of malicious sites, impersonating brands like Netflix or Telegram, plus the knowledge required to take over Facebook accounts and abuse the Facebook ad platform, implies a group rich in resources and knowledge.
Moonlock investigations show that most ads, and even websites, identified by BitDefender as associated with SYS01 were completely vacated before the embargo for this BitDefender investigation was cleared. Additionally, Facebook has already identified several ads from this group and flagged and banned them.
The data indicates a large-scale infrastructure. Cybercriminals build hundreds of sites and promote them through email phishing, social media, or ad platform abuse (malvertising). However, this is nothing new. It’s a trend that has been growing rapidly in the past months.
Once groups are exposed by security researchers, they will close down the websites. But they don’t close down shop — they simply pivot to a new infrastructure that’s likely just as large-scale as the one exposed by researchers.
BitDefender warned that this group is capable of evading detection by changing or adapting the malicious payloads (malware). They can do this practically in real-time via their C2 servers.
“Once antivirus companies detect and block a version of the malware dropper, hackers enhance obfuscation methods and re-launch new ads with updated versions,” BitDefender said.
This real-time C2 malware obfuscation technique speaks of the agility and skills of this group. It can easily pull off an infrastructure-disappearing act, just to continue operating in a new, undetected architecture.
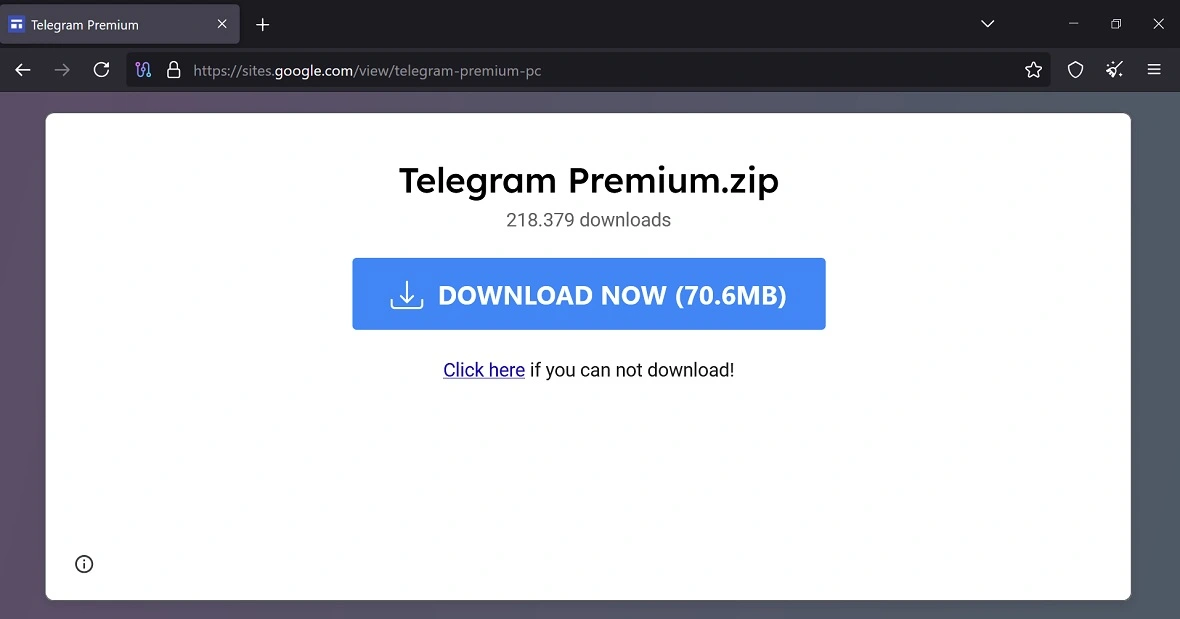
When victims click on these fake Facebook ads, they are usually directed to a MediaFire link or to a site that allows direct download of malicious software.
“In many cases, the malware runs in the background while a decoy app — often mimicking the ad-promoted software — appears to function normally, making it difficult for the victim to realize they’ve been compromised,” BitDefender said.
In many cases, the malware runs in the background while a decoy app — often mimicking the ad-promoted software — appears to function normally, making it difficult for the victim to realize they’ve been compromised.
BitDefender
Why are Middle Eastern small businesses listed as “Payers and Beneficiaries”?
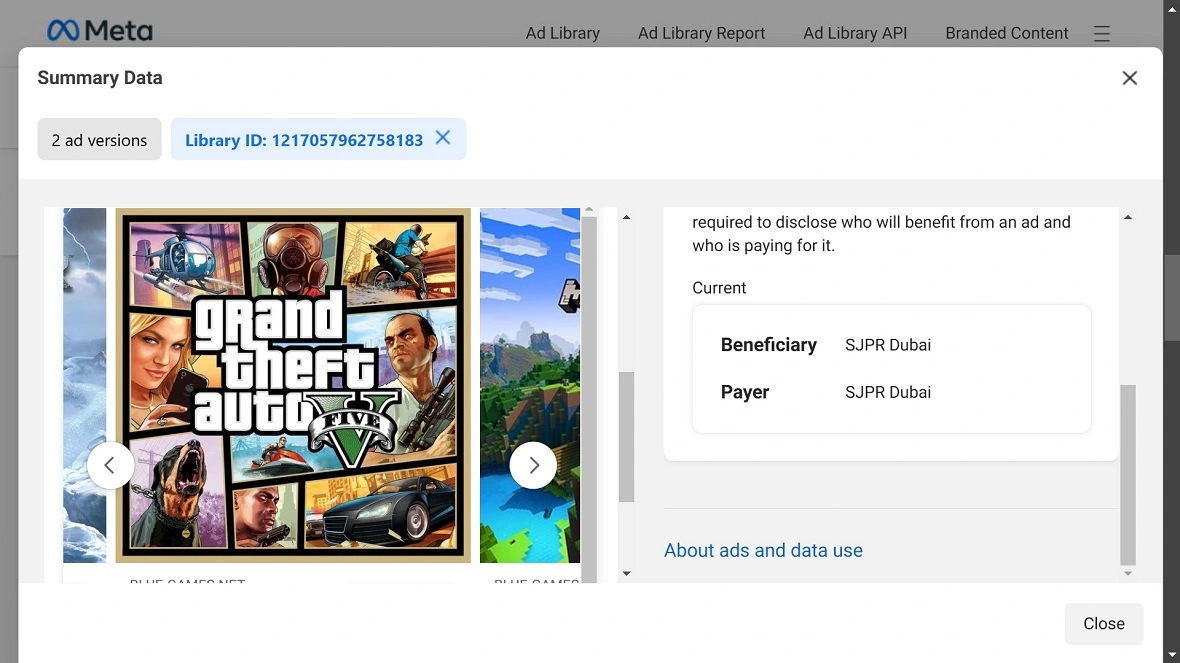
Moonlock investigated the malvertising campaign using the Facebook Ad Library. The platform allows anyone to gain insight into what ads are active and inactive. Moonlock found several peculiarities.
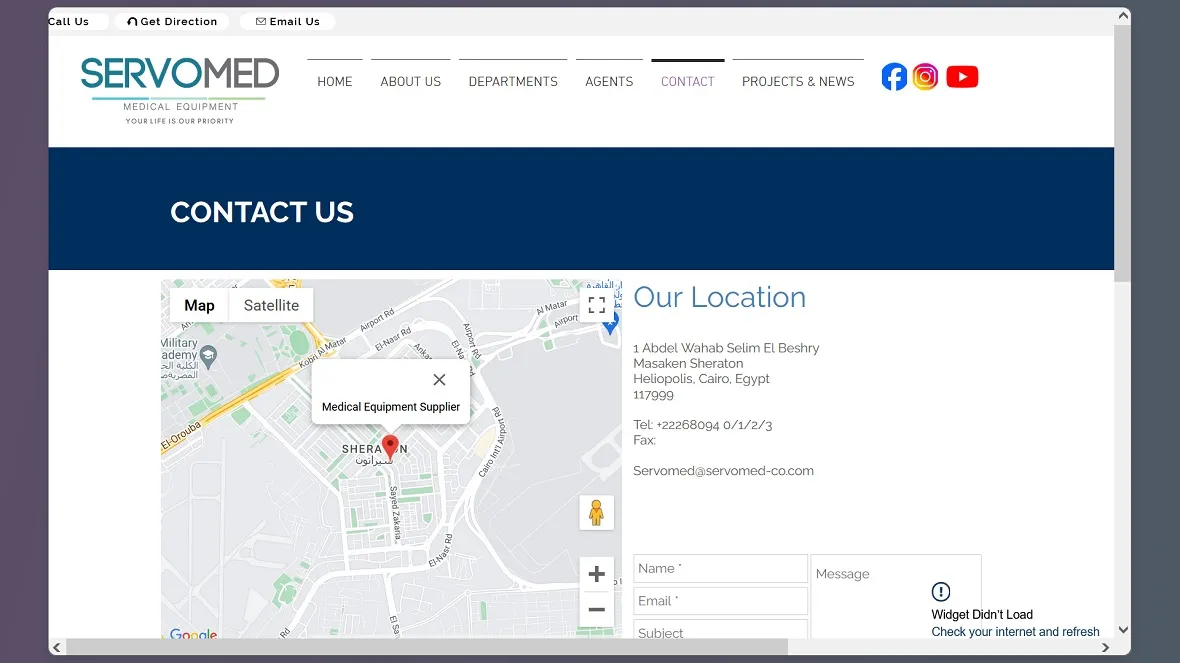
Moonlock investigated the ads identified by BitDefender as part of the malicious campaign distributing infostealers. A look at the Facebook Ad Library revealed that all but one of said ads had Payers and Beneficiaries located in the Middle East. This includes a brick company in Iraq, a small business in Oman, a cloth shop in Kabul, Afghanistan, and a medical equipment company in Cairo, Egypt.
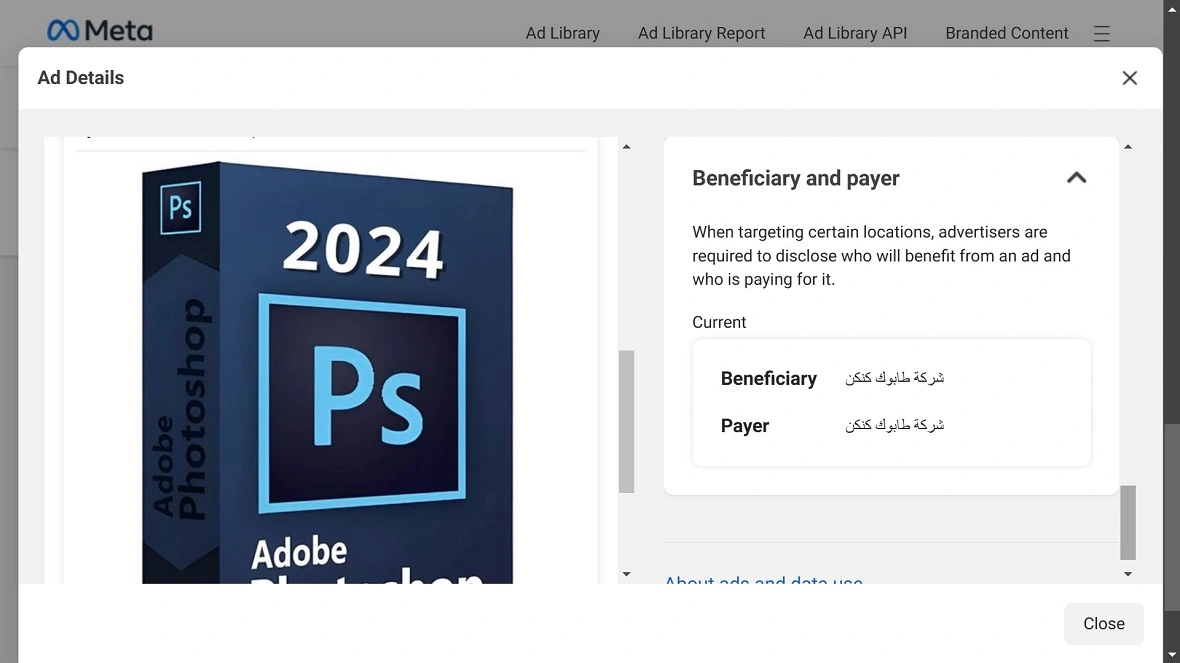
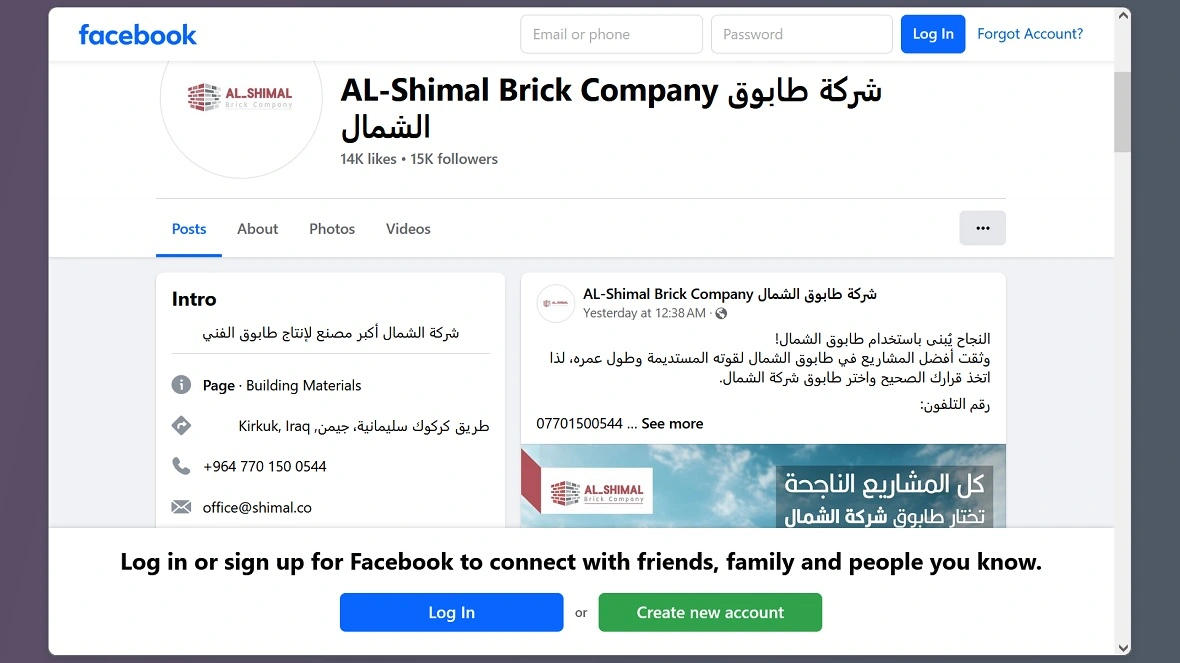
Moonlock also found that one of the Beneficiaries and Payers of these ads listed an organization with a US address. That address was associated with Muslim mentors for children and teens. Another address directed Moonlock researchers to a financial consulting firm in Dubai.
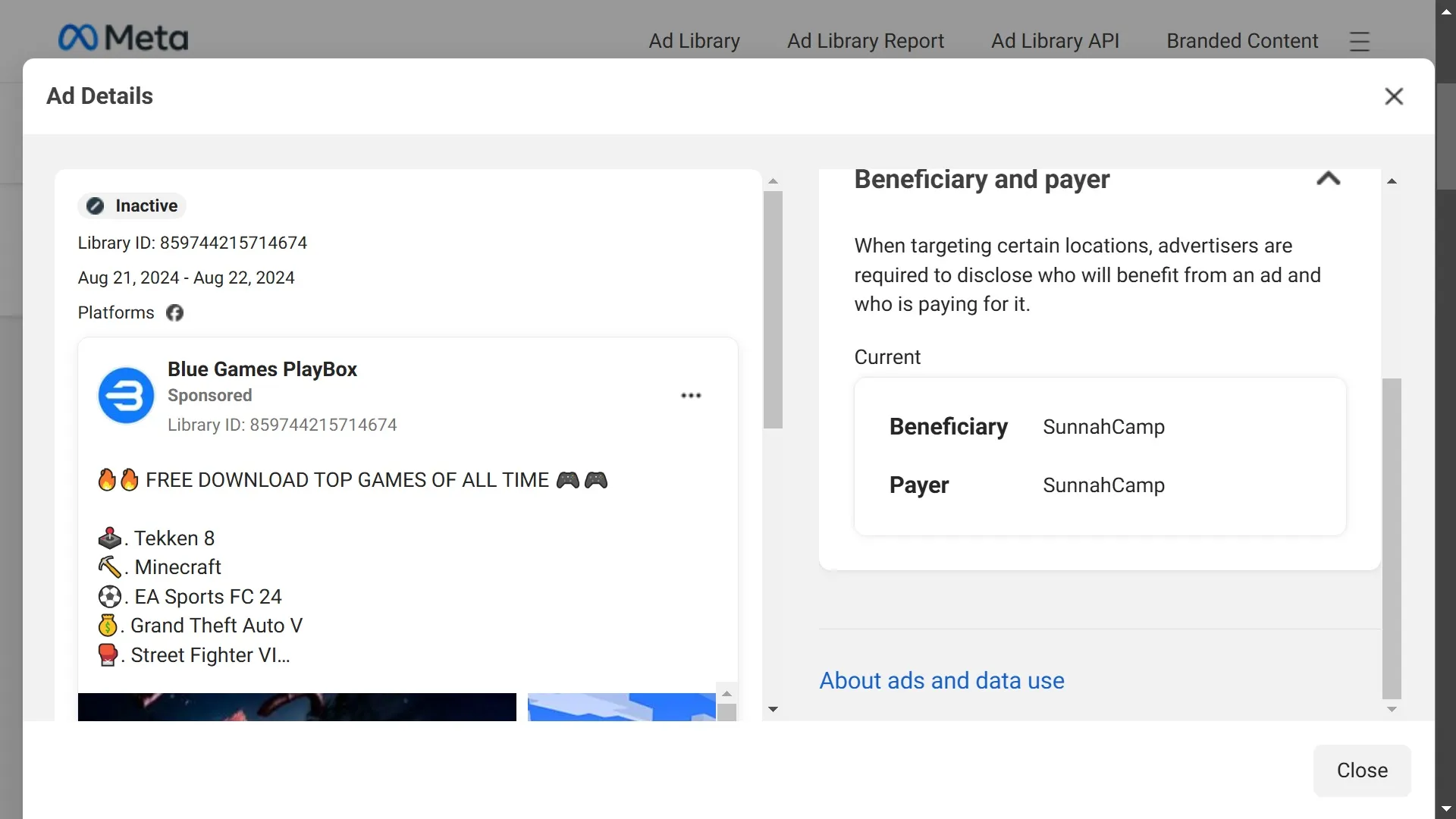
It is important to note that these findings in no way determine that these companies are behind this campaign.
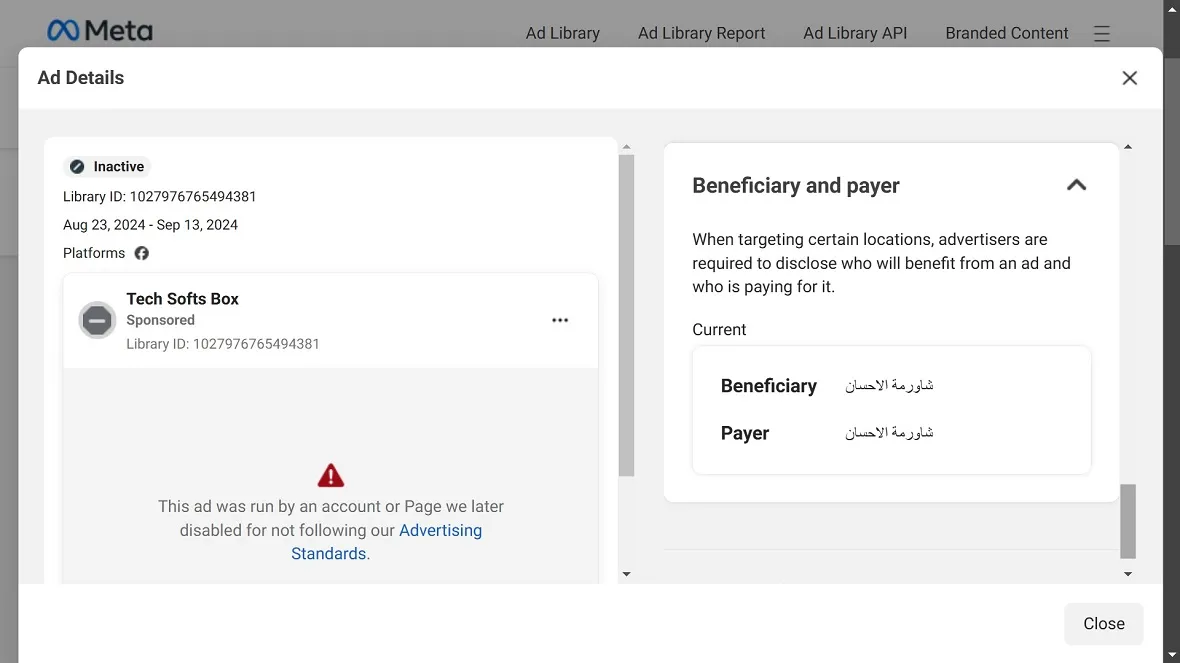
Given that this malware distribution attack on Facebook is targeting people all over the world and appears to be financially motivated, the fact that all Payers and Beneficiaries are in the Middle East is strange indeed.
The first step toward understanding the Middle Eastern connection
There are many possible explanations for this Middle Eastern connection. The most likely explanation is that these are compromised accounts that the hackers have taken over to run fake ads on Facebook.
However, the use of “money mules” to transfer funds or receive payments associated with ad campaigns, as well as the use of local small businesses to launder illicit funds, are common tactics in the Middle East.
Another possibility is that the threat group intentionally used accounts from the Middle East to divert attention from their true origins and make attribution more difficult.
Finally, running malicious operations on Facebook from accounts in the Middle East may also be a tactic to leverage a regional digital environment that is less scrutinized or regulated, making it easier to set up and operate fraudulent schemes.
Little is known about who’s behind the SYS01 infostealer despite it being active for years. However, Trust Wave believes that the malware is connected to another piece of malware known as Rilide. Who developed that one is also a mystery.
Final thoughts
As we have said before, these types of large-scale campaigns with auto-renewing infrastructures are becoming quite common, and they are extremely hard to shut down. The only way to put an end to these cybercriminal operations is through hard research and investigation that delivers accurate and precise attribution.
In simple terms, until authorities know who is pulling the strings on these digital monsters, it’s impossible to stop them.
The perpetuation of these digital criminal trends does not mean users are unsafe. By enabling MFA (and biometrics if possible), not clicking on ads, double-checking URLs, and never downloading software from unsolicited or untrusted sources, users can strengthen their security posture and protect their data and privacy.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Meta Platforms, Inc. Facebook and Facebook Ads are trademarks of Meta Platforms, Inc.






