Banshee, a stealer that emerged in mid-2024 to target macOS users, has received an alarming update. The developers behind Banshee have “stolen” Apple’s XProtect encryption, giving the malware increased stealth and attack rate efficiency.
Half-price and now running Apple encryption, Banshee’s new version is dangerous
Banshee — linked to the Russian cybercriminal industry — is offered on the dark web under malware-as-a-service models. Since August 2024, the malware has been identified in various campaigns, often combined with the use of the Lumma Stealer, which targets Windows devices.
Criminals distributing Banshee use fake phishing pages on GitHub that impersonate legitimate downloads.
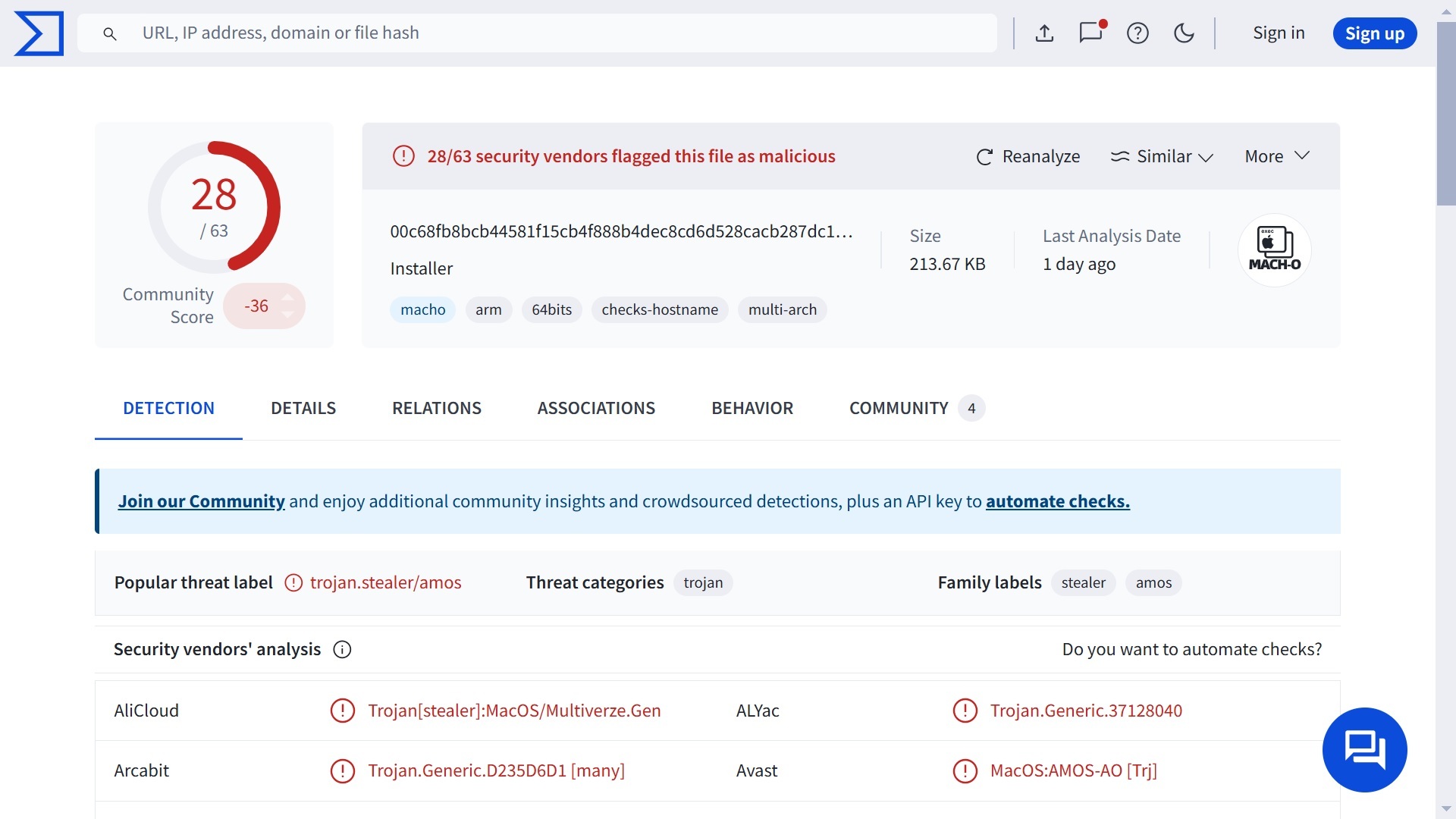
While Banshee has capabilities similar to those of the infamous AMOS macOS stealer, its previous versions were easily flagged by cybersecurity researchers. However, with this new update, Banshee has been flying under the radar for the past 2 months, infecting macOS users.
Check Point research experts discovered how Banshee acquired these new powers. Shockingly, they found the malware now encrypts its strings and operations using the same encryption that Apple uses on its built-in cybersecurity software for Macs — XProtect.
By using the same encryption, not only does Banshee avoid detection on Mac environments, but it also decreases its likelihood of being detected by other anti-malware software you might have running on your Mac, as the software might confuse Banshee processes for XProtect.
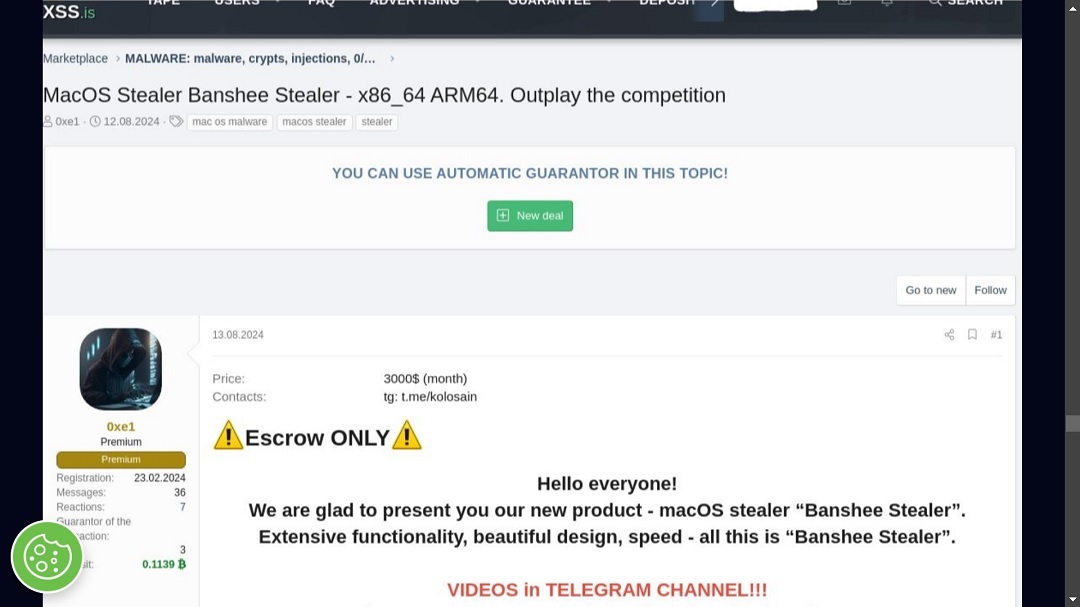
To make matters worse, Banshee distributors are on a mission to scale operations fast and wide. Last year, the price for the Banshee Stealer was $3,000. Today, the new Banshee is on a fire sale for just half that — $1,500.
Banshee is the product of a resourceful and skilled operation
Banshee’s new capability to use XProtect encryption is impressive. It speaks to the sophistication, technical skills, and resources that the criminal gang behind this stealer possesses.
Cybercriminals are increasingly abusing legitimate software and features to breach systems and studying anti-malware solutions and security patches to gain an edge.
“While Apple’s XProtect rules are effective at detecting known malware, they are closely monitored by malware authors, allowing them to adapt and evade detection in future iterations using creative methods,” Jaron Bradley, Director of Threat Labs at Jamf, told Moonlock.
Check Point’s report warns that Banshee is now a stealthy malware that can infiltrate, operate undetected, and blend into macOS environments using normal system processes.
Malware targeted Apple ecosystems: A growing concern
“This new Banshee Stealer variant exposes a critical gap in Mac security,” said Ngoc Bui, Cybersecurity Expert at Menlo Security.
Bui explained that companies have increasingly adopted Apple ecosystems, but the company’s security tools have not been able to keep up the pace.
According to Bui, even the top security solutions have limitations and blind points on Macs. Bui added that the Apple security industry is facing a deficit of trained cybersecurity Mac experts.
Today, Banshee can breach a wide range of browsers such as Chrome, Brave, Edge, Vivaldi, and more. It is noteworthy that the Safari browser is still not on the list of the Banshee browser victims.
Banshee can exfiltrate a lot of information from a Mac, including passwords, system info, IPs, and more. Its operations are focused on targeting multi-factor authentication (MFA) extensions and crypto wallets such as Exodus, Electrum, Coinomi, Guarda, Wasabi, Atomic, and Ledger.
Banshee’s criminal gang ignores malware rules, allowing operators to target Russian-language systems
The new Banshee version is coded to allow operators to target Russian-speaking systems. This violates an unwritten rule in the Russian cybercriminal industry, meaning that the criminal group developing and distributing Banshee is unlikely to be acting as a nation-state group. More likely, they are motivated by money.
Previous versions of Banshee adhered to this unwritten rule. They would not run if they detected the Russian language in the system they were trying to breach. The new Banshee no longer possesses the Russian language checks that the stealer used to have.
Check Point says that this means an expansion of potential targets. However, it could also signal a change of hands in the malware, as its source code was leaked on GitHub 2 months before the new version came out.
Banshee’s success, like other macOS stealers, is built upon social engineering
According to Check Point, even seasoned IT professionals struggle to identify the presence of Banshee in a system. This stealth is what Check Point says is the most alarming trait of Banshee.
Bradley, from Jamf, told Moonlock that the success of macOS stealers — which have been on the rise for the past years — is primarily driven by social engineering.
Bradley explained, “Attackers have to convince users to execute the malware themselves.”
“This highlights an important lesson: No matter how robust the operating system’s security measures are, attackers can often bypass them by presenting users with a convincing reason to act.”
Where you might come across Banshee on the web
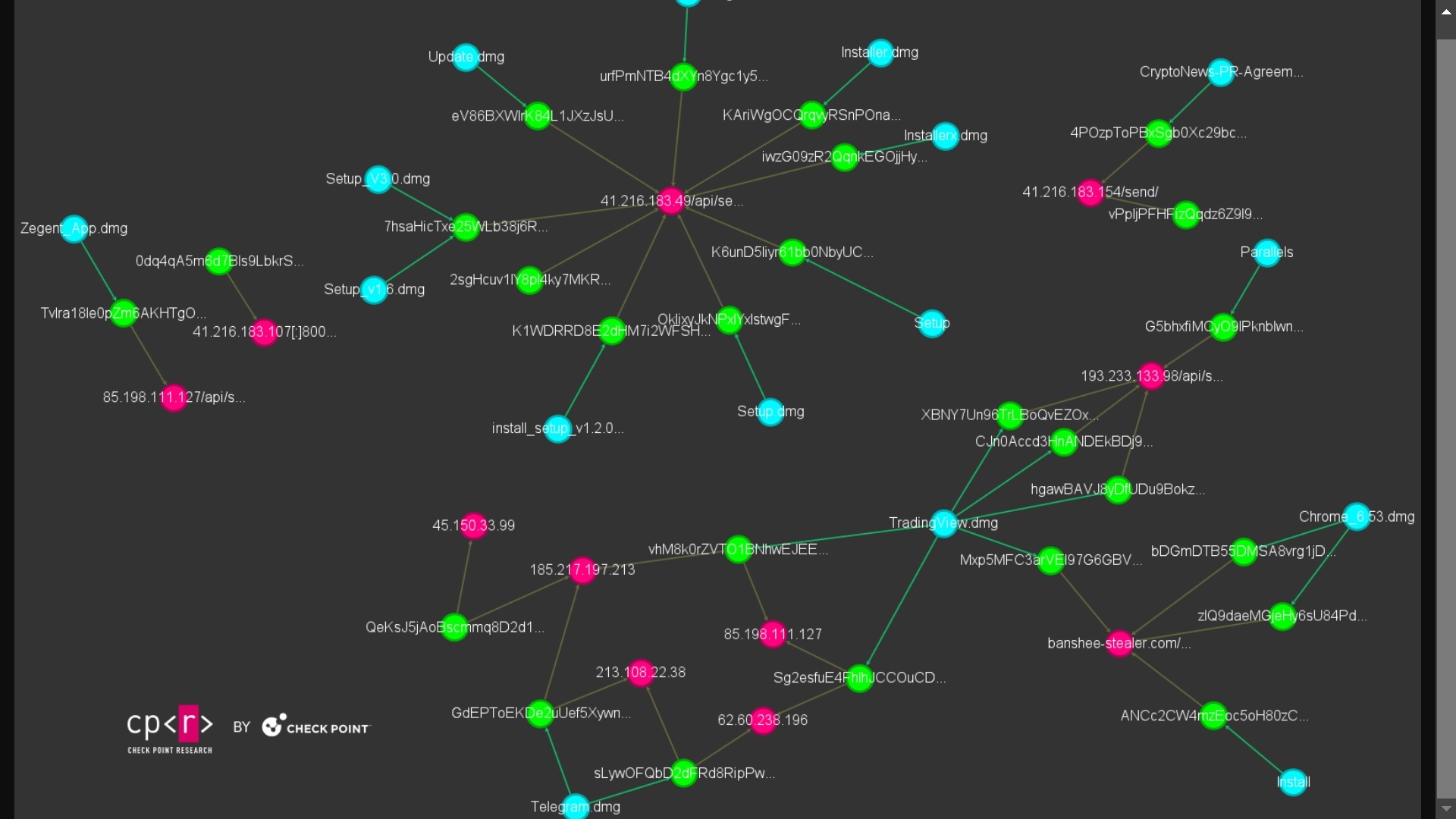
Check Point researchers said that the new Banshee is being distributed via GitHub repositories. These repositories are not strictly technical GitHub pages. Rather, they are sites where threat actors impersonate brands like Adobe and other popular software, as well as solutions used by security researchers, developers, ethical hackers, and others.
The GitHub repositories that Check Point flagged show a design that looks very much like a commercial website template.
As mentioned, these malicious sites are cross-platform ready. Threat actors offer malicious “Download for Mac” (Banshee) and “Download for Windows” (Lumma Stealer) buttons. Clicking on these buttons and installing the software will lead to a breach.
“Over 3 waves, malicious repositories were created to impersonate popular software and lure users into downloading the malware,” Check Point said. “These repositories often appeared legitimate, with stars and reviews to build trust before launching their malicious campaigns.”
Developers, ethical hackers, and security researchers are the primary targets of this initial wave of the new Banshee. Accordingly, they should read the full technical report of Check Point and check out the IoCs.
Banshee could also be distributed via links sent through email, SMS, social media, and other platforms.
Final thoughts
Malware that uses the same encryption that Apple uses on all Macs is something we do not see every day.
By using this technique, Banshee can scramble its strings and only decrypt them during execution. Banshee also presents itself as less suspicious to antivirus or anti-malware software running on Macs, thanks to this encryption trick.
This, combined with the surge in macOS stealers, is a worrying concern. While stealers still require social engineering, the advancements that cybercriminals are making in Apple-focused malware should not be underestimated.
It is likely that Banshee will continue to evolve and may even find a way to breach users without social engineering. As the criminal trends of 2024 continue to play out, 2025 will be a tough cybersecurity year for Apple and its users — now in the crosshairs of criminal gangs.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, macOS, and XProtect are trademarks of Apple Inc.






