LightSpy, a piece of spyware malware that gained its reputation in 2020 for breaking into iPhones, is back. Researchers who have been following the C2 servers of LightSpy’s alleged developers have found that the new version has been significantly enhanced and has greater capabilities.
LightSpy leverages jailbreaking and has 16 new plugins
On October 29, ThreatFabric researchers said that the new LightSpy version for iOS, which had 12 plugins, now has 28. Each plugin in the malware gives LightSpy a hacking feature, some of which are destructive.
Back in 2020, LightSpy — which targets both macOS and iOS using similar methods — already had many impressive capabilities. It could extract data, contacts, and SMS messages. It could also access geolocation data, record VoIP phone calls, access Telegram, WeChat, iCloud Keychain data, and web browser history from Safari and Google Chrome.
As spyware, it could also access the device’s microphone and camera to record audio and take pictures or video.
Now, LightSpy can go well beyond that.
How LightSpy breaches your iPhone and what it can do today
ThreatFabric researchers said the new version can breach iOS versions up to 13.3. LightSpy now jailbreaks its way into a device using jailbreak kits. It establishes communication with a C2 server controlled by the attackers, connects its malicious environment to the victim’s device, and starts unbundling payloads.
The attackers then load the core spyware, along with the new, enhanced 28 plugins.
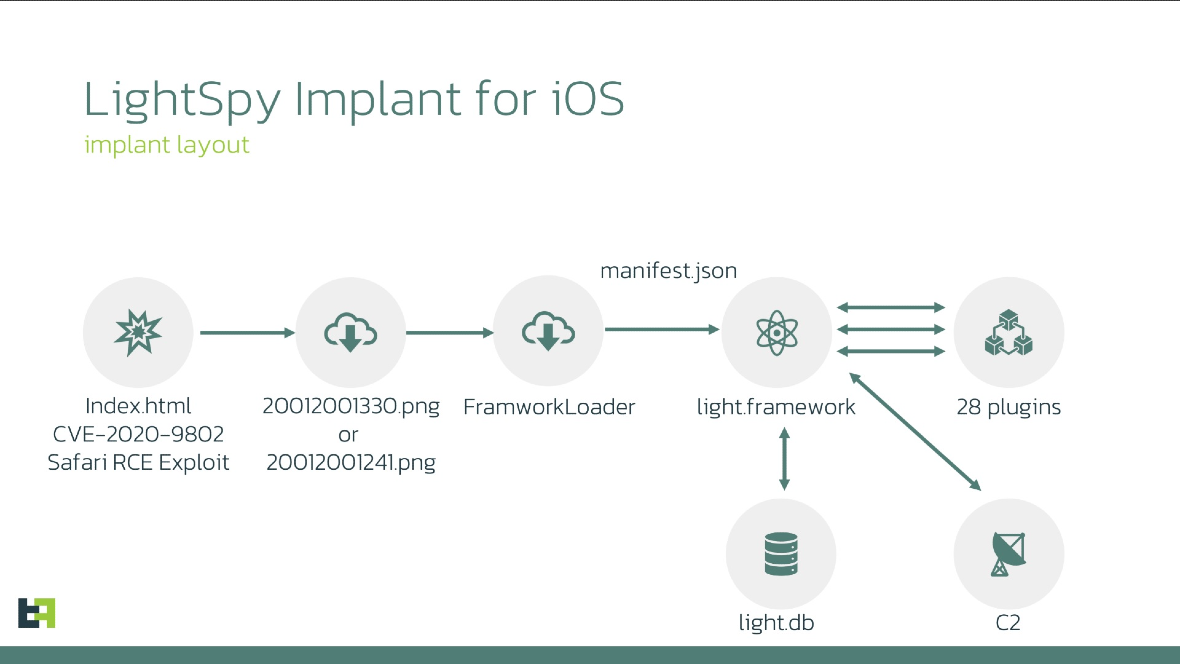
The new version of LightSpy includes the following plugins:
- AppDelete: Deletes messenger-related victim files
- BaseInfo: Exfiltrates contact list, call history, and SMS messages, and can also send SMS messages by command
- Bootdestroy: Prevents the device from booting up
- Browser: Exfiltrates browser history
- BrowserDelete: Wipes browser history
- Cameramodule: Takes camera shots (single or multiple)
- ContactDelete: Deletes specific contacts from the address book
- DeleteKernelFile: Freezes the device
- DeleteSpring: Freezes the device
- EnvironmentalRecording: Records ambient sound and calls
- FileManage: Exfiltrates files
- ios_line: Exfiltrates Line messenger data
- ios_mail: Exfiltrates Apple Mail application data
- ios_qq: Exfiltrates Tencent QQ messenger database
- ios_telegram: Exfiltrates Telegram messenger data
- ios_wechat: Exfiltrates WeChat messenger data
- ios_whatsapp: Exfiltrates WhatsApp messenger data
- KeyChain: Exfiltrates Keychain data
- Landevices: Scans Wi-Fi networks
- Location: Exfiltrates location data
- MediaDelete: Deletes media files from the device
- PushMessage: Simulates incoming push messages with specified URLs
- Screen_cap: Captures screenshots
- ShellCommand: Executes shell commands
- SMSDelete: Deletes specified SMS messages
- SoftInfo: Exfiltrates information about installed apps and running processes
- WifiDelete: Deletes Wi-Fi network configuration profiles
- WifiList: Exfiltrates Wi-Fi network data
Your iPhone is an extremely secure device, but, as you can see from the list above, if a hacker gets inside of it and compromises the OS, your security goes out the window.
With LightSpy, attackers gain full control of your phone and your data, and they can escalate an attack from there.
LightSpy is not being sold nor operating online, but threat actors are showing off its capabilities
Fortunately, ThreatFabric did not discover any incident or evidence that would indicate that this spyware is being used in the wild. They have uncovered several small-scale operations that they conclude are most likely tests to show off the malware to potential buyers.

If this malware were to hit the dark web at an accessible price, the damage it could cause under the malware-as-a-service industrial cybercriminal umbrella is alarming.
However, evidence signals that the developers of this spyware will probably keep this malware close to the chest. Pieces of spyware like this are often reserved for powerful threat actors usually tied to nation-state groups.
A Boot Block plugin that could prevent users from enabling Apple’s Lockdown Mode
As ThreatFabric mentions in its investigation, LightSpy has been equipped with destructive plugins. One of these plugins is Boot Block.
When deployed and enabled by the attackers, Boot Block will prevent a breached victim from rebooting their device. This is particularly problematic for iPhone users.
Apple’s best security feature, designed especially for cyber espionage malware, is Lockdown mode. With Lockdown mode, iPhone users dramatically reduce their digital attack surface.
Lockdown mode also shuts down communications, analyzing which are secure and which are not. This means it often disconnects the infected device from the malicious infrastructure to which it is linked, leaving attackers out in the cold.
However, for Lockdown Mode to be active, users need to manually enable it through Privacy & Security settings and then reboot their device. If a reboot is not done, Lockdown Mode will not be enabled.
It is not known why LightSpy developers would develop a plugin that prevents users from booting their devices. What is known is that this particular plugin seems to prevent iPhone users from enabling Lockdown Mode.
How LightSpy is distributed is still unknown
Understanding the distribution method of LifeSypy has always eluded cybersecurity researchers. In 2020, the distribution was said to possibly be done through watering hole attacks, most likely through Asian news outlets online. This means threat actors compromised known media sites, breached them, and used them to distribute the malware.
Today, the distribution method continues to be obscured, although ThreatFabric says the same methodology could be in play today.
“In 2020, security researchers noted that a watering hole attack vector was used,” ThreatFabric said. “It seems that for the LightSpy versions that were described in this report, the same attack vector could be used. However, we do not have any evidence for that.”
LightSpy’s threat model: A focus on targeted attacks and evasion
While distribution methods remain unknown, we know some things about LightSpy for certain. Notably, this spyware will not only exploit zero-day vulnerabilities or other known iOS vulnerabilities but also use jailbreaking kits to gain access to the device.
Jailbreaking kits are used to remove software restrictions on devices to allow unauthorized applications and features. Jailbreaking kits are also used to wipe stolen phones clean before they are resold on the underground market. Some developers also use jailbreaking kits for specific technical reasons.
ThreatFabric identified at least 3 developers working on LightSpy and some small-scale tests, but there is no evidence of the spyware being sold under malware-as-a-service. Therefore, while we don’t expect LightSpy to become popular among cybercriminals, it might be deployed for very specific high-value operations, which could be motivated by political agendas.
As ThreatFabric pointed out, the use of destructive plugins that allow the spyware to wipe contact lists, disable devices, and delete files, history, and system components, are likely developed for evasion, stealth, and persistence.
Regarding the actors behind all this, ThreatFabric found that the location plugin contains a function that recalculates location coordinates according to a system used exclusively in China, which indicates that LightSpy operators are likely based in China.
Final thoughts
LightSpy is a powerful piece of spyware that seems to have been developed for specific purposes. Investigations show that the spyware is already being tested in what are likely demonstrations to potential buyers or leaders of a wider operation.
Given the evidence and history, it is likely that the targets of the next LightSpy campaign are located in Asia. However, an international expansion of the software, as well as more plugins and enhancements, should not be ruled out.
If you think your iPhone or your Mac is infected with spyware, enable Lockdown Mode immediately and follow Apple’s official guidelines. Keep your software up to date, as LightSpy uses vulnerabilities that Apple often patches up quickly through security updates. Additionally, stay alert for any suspicious behavior on your devices and accounts, and take proper actions to secure them if needed, e.g., changing passwords and enabling MFA (with biometrics if possible).
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and iPhone are trademarks of Apple Inc.






