On October 31, Bitdefender Labs reported that cybercriminals are using an updated and enhanced version of the infostealer malware NodeStealer to run malvertising campaigns on Facebook. Let’s look into this dangerous new attack and how to protect yourself from it.
Catfishing Facebook ads are spreading malware
Targeting and impacting largely males ages 45 and older, the coding of this new malware is relentless. To lure potential victims into clicking on NodeStealer ad campaigns, criminals use revealing photos of young women.
One click on the NodeStealer is all it takes for a malicious executable file called “Photo Album” and a second hidden malware file to be downloaded and self-installed. It can then start stealing your passwords, data, and browser cookies.
“Given that each ad click instantly downloads the malicious archive, we’ve estimated 100,000 potential downloads from the ad reach analysis, with a single ad having as many as 15,000 downloads within just a 24-hour rollout,” Bitdefender Lab says about the massive impact of this new criminal endeavor.
NodeStealer criminals are also well aware that fake ads are reported by users to help Facebook block them out. To get around this problem, they only use a maximum of 5 active ads at a time and switch between them every 24 hours.
This dramatically reduces the chances of potential victims reporting the malware ad, as well as Facebook’s capacity to block the attacks or sites. In fact, 7 days after this attack was reported by Bitdefender Labs, all of the fake profiles identified as being created by attackers were still active on Facebook.
And these aren’t just any profiles. They clearly stand out as fakes.
NodeStealer hackers have created multiple fake Facebook profiles, all of which contain provocative images of young women. They also hijack business and personal Facebook accounts and use them to promote their ads. Bitdefender Lab says that by using these tactics, criminals are “creating havoc on Facebook.”
The new NodeStealer 2.1 is supercharged
The new version of NodeStealer, dubbed 2.1 by Bitdefender Labs, allows criminals to not only steal Facebook credentials but to take over other accounts such as Gmail and Outlook, steal data, spread malware, and steal crypto wallet balances.
Those who fall victim to this new attack are at risk of suffering devastating reputational and financial damages.
In terms of malware, NodeStealer is the new guy in town. It was initially discovered by Meta’s security team in January 2023. Back then, the malware was used to take over Facebook accounts in bulk, mostly business accounts. While it did have some impressive features, such as its capacity to bypass two-factor authentication technologies and steal web browser cookie sessions from Chrome, Edge, Brave, and Opera, its abilities effectively ended there.
But now, threat actors linked to the cybercriminal world of Vietnam have supercharged NodeStealer to do much more. Equipped with these new powers, threat actors are on a malvertising-as-a-vector spree on Facebook.
NodeStealer 2.1 can:
- Obtain entry to other platforms beyond Facebook, including Gmail and Outlook
- Steal personal data
- Be used to download more malware
- Drive reputation extortion scams
- Create financial losses
- Empty out crypto wallet balances
Take these actions to be in the clear
Undoubtedly, social media is the preferred medium for cybercriminals to run malvertising. By using social media, bad actors do not have to figure out how to appear on the first pages of search engine results. They can easily create a fake channel, company, or person and even pay to have their fake ads delivered directly to sites. They can also skip this entire process and simply breach a legitimate social media account and then use it to run their malware ad campaigns.
So, how can you stay safe from these types of attacks? First of all, it’s vital to know how NodeStealer criminals work.
NodeStealer criminals will:
- Target ads mostly to male users on Facebook ages 18 to 65
- Prefer users from countries that are in Europe, Africa, and the Caribbean
- Create provocative images of young women and short descriptions to bait users into downloading albums
- Use lines such as “New stuff is online today” and “Watch now before it’s deleted” to draw you in
Known malicious Facebook profiles are still live
There are several Facebook profiles that have already been linked to NodeStealer. At the time that this report was filed for publication, all of them remained active.
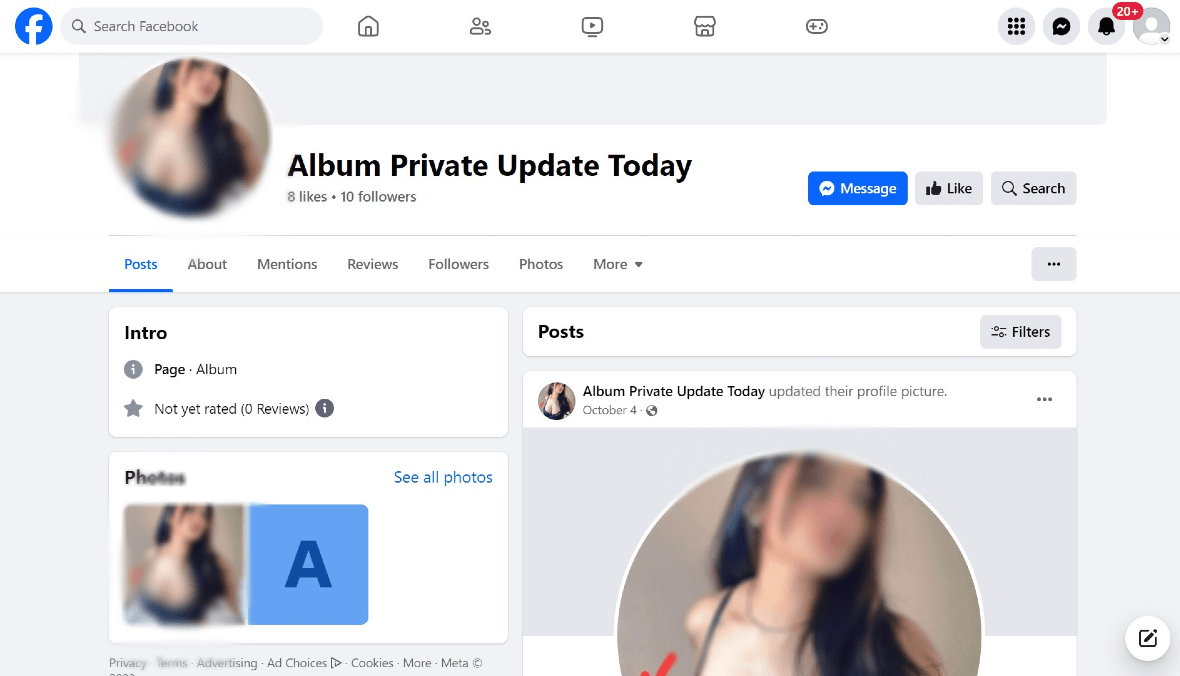
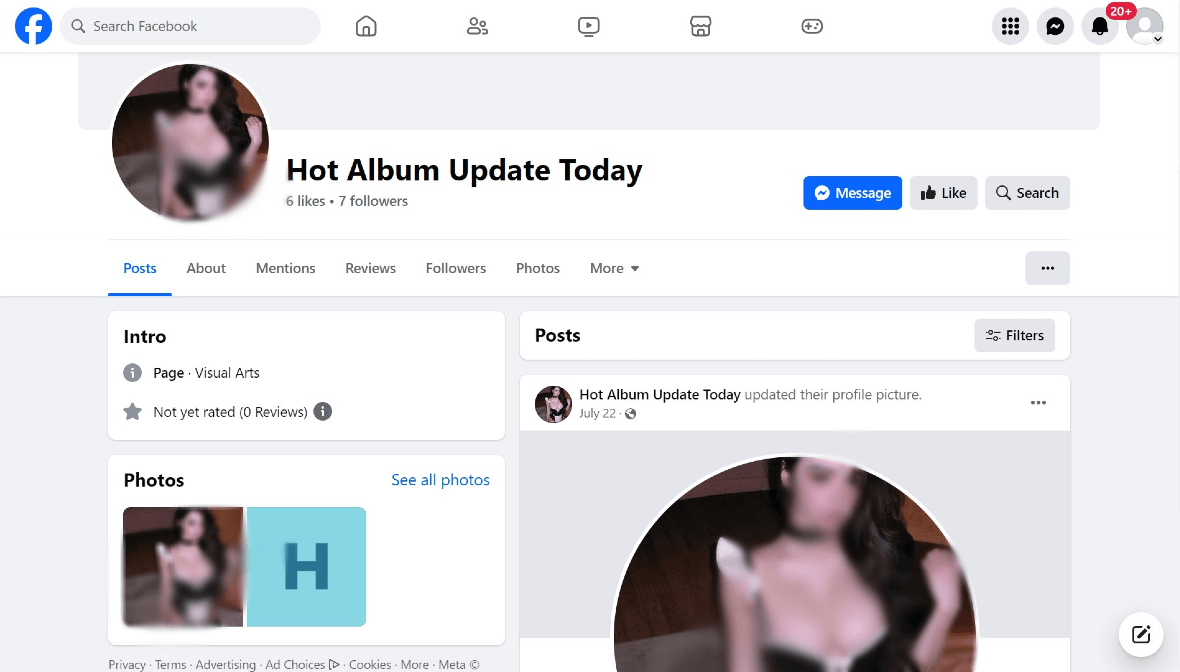
It’s important for you to stay away from the following Facebook profiles and their ads:
- Album Update
- Album Girl News Update
- Private Album Update
- Hot Album Update Today
- Album New Update Today
- Album Private Update Today
Besides good online practices, such as avoiding clicking on suspicious malware, being cautious when strangers message you, and not downloading unknown files from untrusted sources, you should set a strong password and enable two-factor authentication on Facebook.
You should also keep your devices updated to make sure you have the latest official security patches set up. It’s a good idea to deploy and run professional and trusted antimalware software that will detect any problem before it is too late. Finally, remember that no matter how tempting or intriguing an ad may be, always think twice before clicking on it.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Meta Platforms Inc. Facebook is a trademark of Meta Platforms Inc.






