North Korean hackers are at it again. In the past few years, cybercriminal operations linked to the Democratic People’s Republic of Korea (DPRK, aka, North Korea) have been doubling down on crypto cyberattacks in an effort to increase illegal financial gains, most likely to fund military programs in the country affected by international sanctions.
However, now the NSA, the FBI, and the US Department of State are warning that the North Korean threat actor Kimsuky (also known as Emerald Sleet, APT43, Velvet Chollima, and Black Banshee) is spear-phishing its way into a widescale espionage campaign.
North Korea’s Kimsuky catches the eye of the NSA
On May 2, the NSA released a Joint Cybersecurity Advisory warning users that North Korea’s illegal intelligence-gathering operations were ramping up. Using spear-phishing, Kimsuky hackers contact individuals via email to collect intelligence on geopolitical events, adversary foreign policy strategies, and any information affecting North Korea’s agenda and interests.
Posing as real journalists, academics, and experts in East Asian affairs, North Korean hackers are working in the shadows to steal data by gaining illicit access to victims’ private documents, research, and communications.
“Spear-phishing continues to be a mainstay of the DPRK cyber program, and this CSA provides new insights and mitigations to counter their tradecraft,” NSA Cybersecurity Director Dave Luber said in the press release.
The main targets? People in the United States, South Korea, and any other country perceived by North Korea as a threat or challenge to its military, political, security, and economic goals.
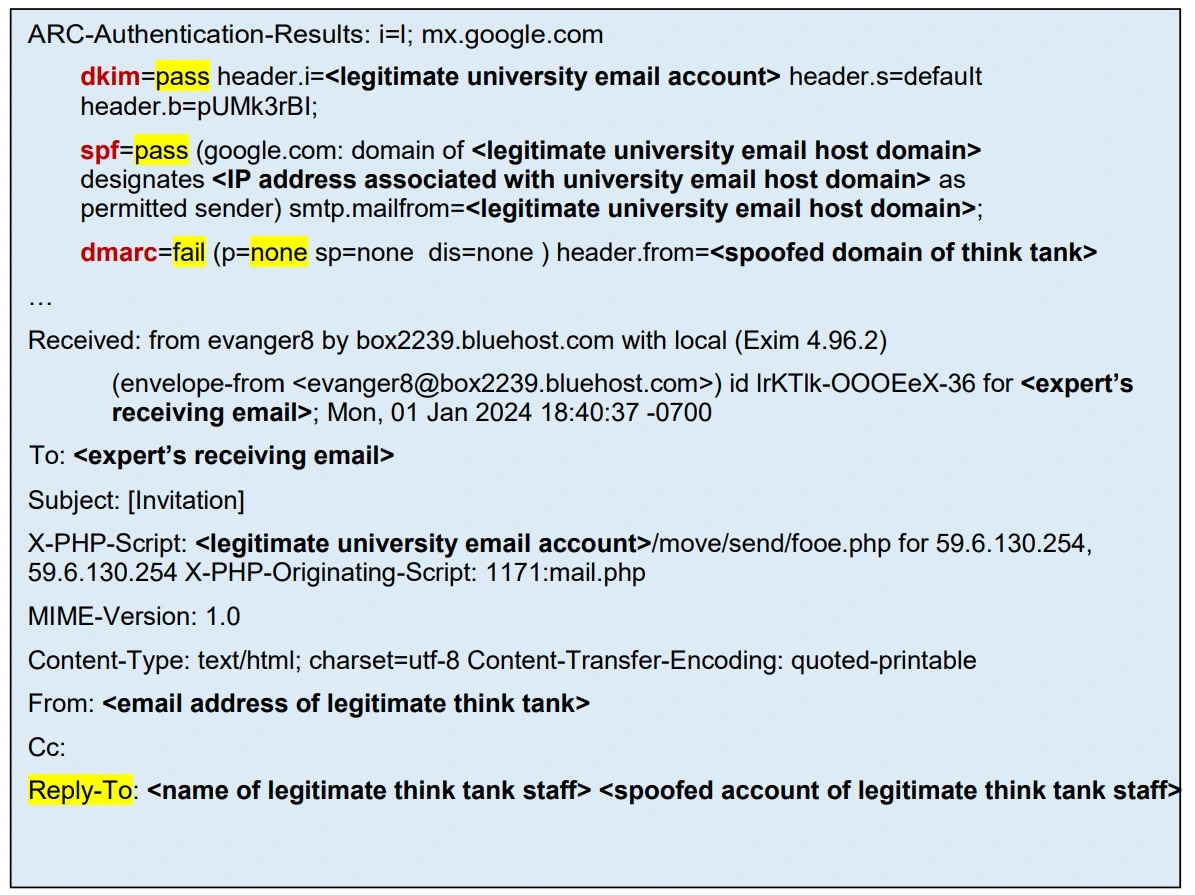
The NSA explains that Kimsuky hackers not only sent out well-crafted spear-phishing emails but created fake personas and fake usernames. They also use legitimate domain names to impersonate individuals from trusted organizations — including think tanks and institutions of higher education.
The fraudulent emails in this espionage cyberattack campaign do not come from the trusted organization’s actual domain email, but rather from the actor-controlled email address and domain.
“The ‘reply-to’ section of the email header would reveal the North Korean actor-controlled email address and domain, but it would still appear to be legitimate,” the NSA explains.
Exploiting weak email security configurations and policies
North Korean threat actors are well-experienced and rich in resources. The NSA attributes this campaign to North Korea’s premier military intelligence organization: the Reconnaissance General Bureau (RGB). The RGB has been sanctioned by the United Nations Security Council and has been on an illegal espionage rampage since 2012.

However, as scary as these attacks may sound, one simple fix can shut the group out of your email inbox.
The fix? DMARC policies.
What are DMARC policies?
The reason why North Korean hackers are bypassing email security features in this spear-phishing comes down to just one thing: DMARC policies.
DMARC — short for Domain-based Message Authentication, Reporting and Conformance (DMARC) — is an email authentication protocol specifically designed to safeguard email domain owners from unauthorized use. A well-implemented DMARC policy can protect users against phishing and spoofing.
Using DMARC, companies and individuals can implement policies that dictate how receiving mail servers should handle emails that fail authentication checks.
Setting up DMARC policies is a relatively straightforward process. However, it is commonly disabled due to a lack of awareness, technical gaps, and fear of disruption. The NSA breaks down the work that DMARC policies do.
“DMARC policy tells a receiving email server what to do with the email after checking a domain’s Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) records. Depending on if an email passes or fails SPF and DKIM, the email can be marked as spam, blocked, or delivered to an intended recipient’s inbox.”
The NSA recommends changing missing DMARC policies, or DMARC policies with a “p=none” value, with the following configurations:
- “v=DMARC1; p=quarantine;”: The email servers will quarantine emails that fail DMARC, considering them to be probable spam.
- “v=DMARC1; p=reject;”: This configuration will instruct email servers to block emails that fail DMARC, considering them to be almost certainly spam.
Authorities also recommend setting other DMARC policy fields, such as “rua” to receive aggregate reports about the DMARC results for email messages purportedly from the organization’s domain.
DMARC tools streamline implementation and strengthen security
Users can also check out popular DMARC tools that help streamline the configuration and provide protection. There are numerous organizations and companies that offer free and paid DMARC tools, including Google Postmaster Tools, Mimecast, Validmail, and DMARC Advisor, just to name a few.
What else can Apple users do to stay safe?
While setting up DMARC is generally considered simple for individuals and organizations alike, it still requires some technical knowledge. So, what else can Apple users doo?
Besides DMARC settings, Apple users can also leverage several built-in email security tools. For example, Mail Privacy Protection.
Mail Privacy Protection on iPhone
This tool makes it harder for senders to gain insight into your Mail activity. The feature will hide your IP address, so senders can’t link it to your other online activity or use it to determine your exact location. Mail Privacy Protection also prevents senders from seeing whether you’ve opened the email they sent you.
To activate Mail Protection on your iPhone:
- Go to Settings > Mail > Privacy Protection.
- Turn on Protect Mail Activity.
Those subscribed to iCloud+ can also use Hide My Email. This feature will generate unique, random email addresses that are configured to forward incoming emails to your personal email account. This allows users, for example, to avoid sharing their real email when filling out forms, using the web, or sharing email accounts with unknown sources.
Lockdown Mode on macOS, iOS, and watchOS
Additionally, if you believe you are being targeted by North Korean threat actors, you should immediately activate Lockdown Mode. Lockdown Mode works in macOS, iOS, and watchOS.
To enable Lockdown Mode on your iPhone or iPad:
- Update your devices to the latest software before turning on Lockdown Mode.
- Open the Settings app.
- Tap Privacy & Security.
- Scroll down and tap Lockdown Mode, then tap Turn On Lockdown Mode and enable the feature.
- Now tap Turn On & Restart and enter your device passcode.
Note: Turning on Lockdown Mode on your iPhone will automatically enable the feature on your Apple Watch if it is paired with your phone.
While Lockdown Mode needs to be turned on separately for your iPhone, iPad, and Mac, when you turn on Lockdown Mode for one of your devices, you will get prompts to turn it on for your other supported Apple devices.
Lockdown Mode will take extreme measures to protect your data. This means it will dramatically reduce your digital attack surface, and numerous features on your devices will not work as they should.
The NSA urges all those affected to file a report with www.ic3.gov, reference #KimsukyCSA in the incident description, and keep the original email and attachments as they might serve authorities in their investigation. You can also report suspicious activities, including any suspected North Korean cyber activities, to local FBI field offices.
Red flags helping you spot the phishing, according to the NSA
Users can take other precautions to strengthen their security postures, even if they do not have DMARC settings enabled. In the Joint Advisory, the NSA shared several red flags.
These include:
- Phishing in stages: The scam starts with seemingly harmless emails containing no links or attachments. Later emails introduce malicious links or documents.
- Persistent contact: If you don’t respond to the initial email, expect follow-up attempts within a few days.
- Personalized content: Deceptive emails might use snippets of genuine conversations that the attacker obtained by compromising other victims’ accounts.
- Grammatical errors: Look out for awkward sentence structure and grammatical mistakes, as these can indicate that the email isn’t from a professional source.
- Targeted audience: Spear-phishing emails often target specific groups, such as government officials, military personnel, or those dealing with sensitive topics like North Korea or Asia.
- Spoofed identities: Attackers might use email addresses that closely resemble legitimate ones, with subtle misspellings of names or domains found in public directories or official websites.
- Macro malware: Beware of attachments that require enabling macros to function. This is a common tactic to install malware on your device.
- Impersonation with a twist: The email might appear to be from a legitimate organization, but the sender’s email address might have a slight variation from the official domain (check the email header information for details).
By recognizing these red flags, being aware of the threat, and taking simple actions, you can significantly reduce the risk of falling victim to a spear-phishing attack.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iPhone, Mac, iOS, macOS, and watchOS are trademarks of Apple Inc.






