An email sent from Google to a lead blockchain developer turned out to be such a sophisticated attack that it has attracted the collective attention of cybersecurity media.
Phishing emails are the most popular attack vector used by cybercriminals. And impersonating brands like Google is the go-to tactic used to abuse user trust in a brand and convince them to do things they should not. However, this phishing campaign stands out for several reasons. Let’s dive straight in.
Lead developer of Ethereum Name Service gets an unusual email from Google
On April 16, Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a decentralized naming system on the Ethereum blockchain for users to register human-readable names and link them to the blockchain, revealed that he had been targeted by threat actors who abused Google infrastructure.
Johnson said that the vulnerability on Google’s side needed to be fixed, which the company first denied but later recognized. Johnson added that if this bug isn’t fixed, the phishing cyberattack technique could be leveraged by more threat actors.
How does this phishing cyberattack work?
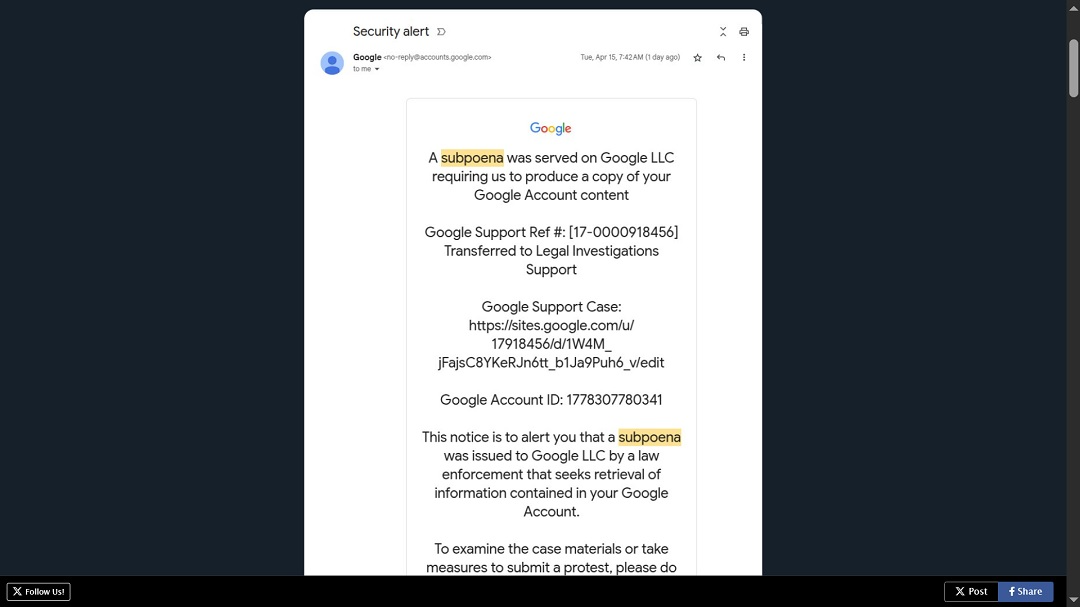
The email Johnson received not only impersonated Google but also came from a legitimate, valid, signed email of the company — specifically, [email protected]. The email went through DomainKeys Identified Mail (DKIM) signature checks and Gmail security guardrails like a hot knife through butter. In fact, it triggered absolutely no warning or alarm whatsoever.
The email’s content was cleverly designed to look just like an authentic email from Google. Strangely enough, the text claimed, “A subpoena was served on Google LLC requiring us to produce a copy of your Google Account content.”
To create the illusion that the victim is, in fact, talking to Google, the attackers abused sites.google.com, a free service to create websites. Because this service provides website links that end with the words google.com, victims may think it is legitimate.
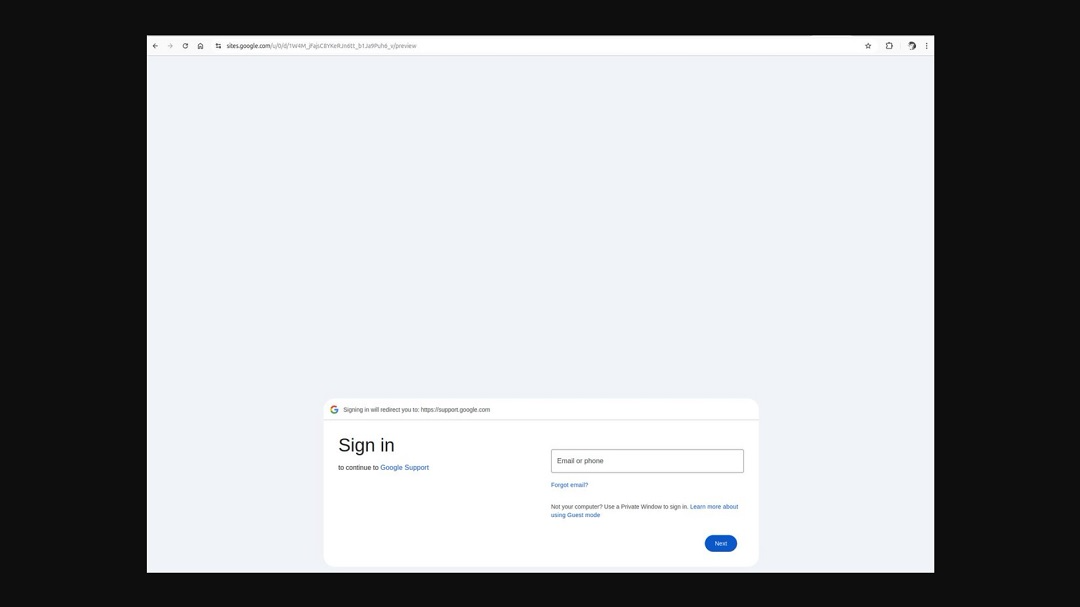
The email also contained a link, which Johnson visited and found to be a fake Google account sign-in page cleverly designed to steal Google credentials.
Breaking down how threat actors can send emails from Google’s own email addresses
So, how did the threat actors pull this off? How are they phishing victims with emails signed by Google itself?
“First, they register a domain and create a Google account for ‘me@domain,’” Johnson explained. “The domain isn’t that important, but it helps if it looks like some kind of infra(structure).”
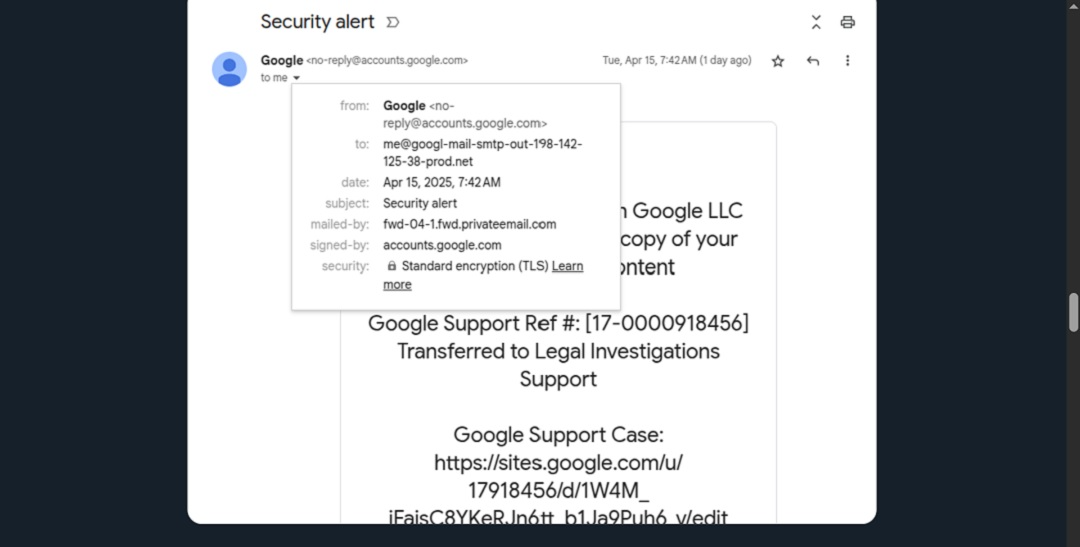
What this means is that the attackers created an email that looked like something Google would be using. In this case, the email the bad actor created was me@googl-mail-smtp-out-198-142-125-38-prod[.net].
Next, they created a Google OAuth application.
“For the name of the application, they enter the entire text of the phishing message — newlines and all — followed by a lot of whitespace and ‘Google Legal Support,’” Johnson explained.
When the hacker grants this newly created OAuth app access to their me@googl-mail-smtp-out-198-142-125-38-prod[.net] account, a “Security Alert” message from Google is generated and sent to this “me@…” email address.
“Since Google generated the email, it’s signed with a valid DKIM key and passes all the checks,” Johnson explained.
Next, all the threat actor has to do is forward the email to their victims. “Because DKIM only verifies the message and its headers and not the envelope, the message passes signature validation and shows up as a legitimate message in the user’s inbox — even in the same thread as legit security alerts,” Johnson added.
The latest update shared by Johnson on this issue celebrated that Google had reconsidered this bug and would be fixing the OAuth vulnerability, which they had previously scrapped from patching.
The same technique has been recently used to target PayPal users
BleepingComputer reported that it is not the first time they have seen this type of technique in the wild. In February 2025, threat actors targeted PayPal users by using the same method. Malicious messages originating from PayPal’s mail servers passed DKIM security checks and reached their intended targets.
In this case, the emails were being sent directly by PayPal from the address [email protected]. The email falsely informed victims that a new email had been added to their PayPal account and that their account had been hacked to buy a MacBook. The email urged readers to call a phone number where a fake customer support person would scam the victims into installing malware.
Just as in the Google OAuth phishing campaign, this PayPal scam bypassed all security and spam filters.
What can you do about these threats?
With phishing getting more convincing every day and bad actors exploiting known platforms, how can the average user stay in the clear? Here are some key tips that can help you stay safe:
- Verify the source: Always check the sender’s email address carefully. Look out for subtle misspellings or domains that don’t quite match the official ones.
- Inspect email content: Be skeptical of unexpected messages, especially those containing urgent calls to action or alarming content. Check for inconsistent design or language peculiarities.
- Use multi-factor authentication (MFA): Enable 2-factor or multi-factor authentication on your accounts wherever possible to add an extra layer of security.
- Keep software updated: Ensure that your email client and security software are up to date with the latest patches and threat intelligence.
- Educate yourself and others: Regularly update your security awareness regarding phishing techniques and social engineering tactics. Participate in cybersecurity training if available.
- Report suspicious emails: If you encounter an email that appears to be a phishing attempt, report it to the relevant organization. Companies like Google and PayPal have dedicated channels for reporting such activities.
- Examine links before clicking: Hover over any links in an email to inspect the URL. Even if the email appears to be from a trusted source, look closely for irregularities in the link address. Also, be sure the address is not a Google subdomain or similar.
By following these practices, you can significantly reduce your risk of falling victim to sophisticated phishing attacks that exploit both technological and human vulnerabilities.
Final thoughts
Cybercriminals are constantly discovering new ways to exploit platforms and services provided by companies like Google and PayPal. This is because the success of their attacks is much higher if they can trick victims into believing their scams, and abusing the trust of legitimate, popular digital platforms works like a charm.
This is not the first campaign to abuse sites.google.com or that has managed to bypass email security guardrails, and it will certainly not be the last. Stay on alert for the smallest of details when reading and engaging with new emails, because the bag of tricks used by hackers is never-ending.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Google LLC. Google and Gmail are trademarks of Google LLC.






