The most important duty of cybersecurity researchers is to keep users informed about emerging threats and vulnerabilities. So today, we delve into the world of cracked software distribution and discover how threat actors exploit the trust of unsuspecting users to deceive them into installing malware.
In response to the high demand for cracked software, sites have emerged that distribute a wide array of applications, offering pirated versions of popular pieces of software whose copy protection mechanisms have been circumvented. One such site that has come under our scrutiny is haxmac[.]cc, a famous hub for users seeking cracked applications for macOS.
Sites hosting cracked macOS apps are spreading malware
Interestingly, haxmac[.]cc is visited by half a million users per month, with 207,000 of those users being unique. This constitutes significant traffic and, in the event of malware being hosted, poses the possibility that many devices could be infected.
![An image showing the web analytics of haxmac[.]cc.](https://moonlock.com/2024/04/Web-Analytics-of-haxmac_1.webp)
A whopping 26.97% of the site’s traffic originates from organic search results. It looks like threat actors exploit trust in Google’s search rankings. By allegedly manipulating search engine optimization (SEO) tactics, they can elevate haxmac[.]cc to the top of search results for queries such as “download crack app macOS.”
![An image showing geography and traffic info for haxmac[.]cc.](https://moonlock.com/2024/04/Geography-and-traffic-of-haxmac.cc_2.webp)
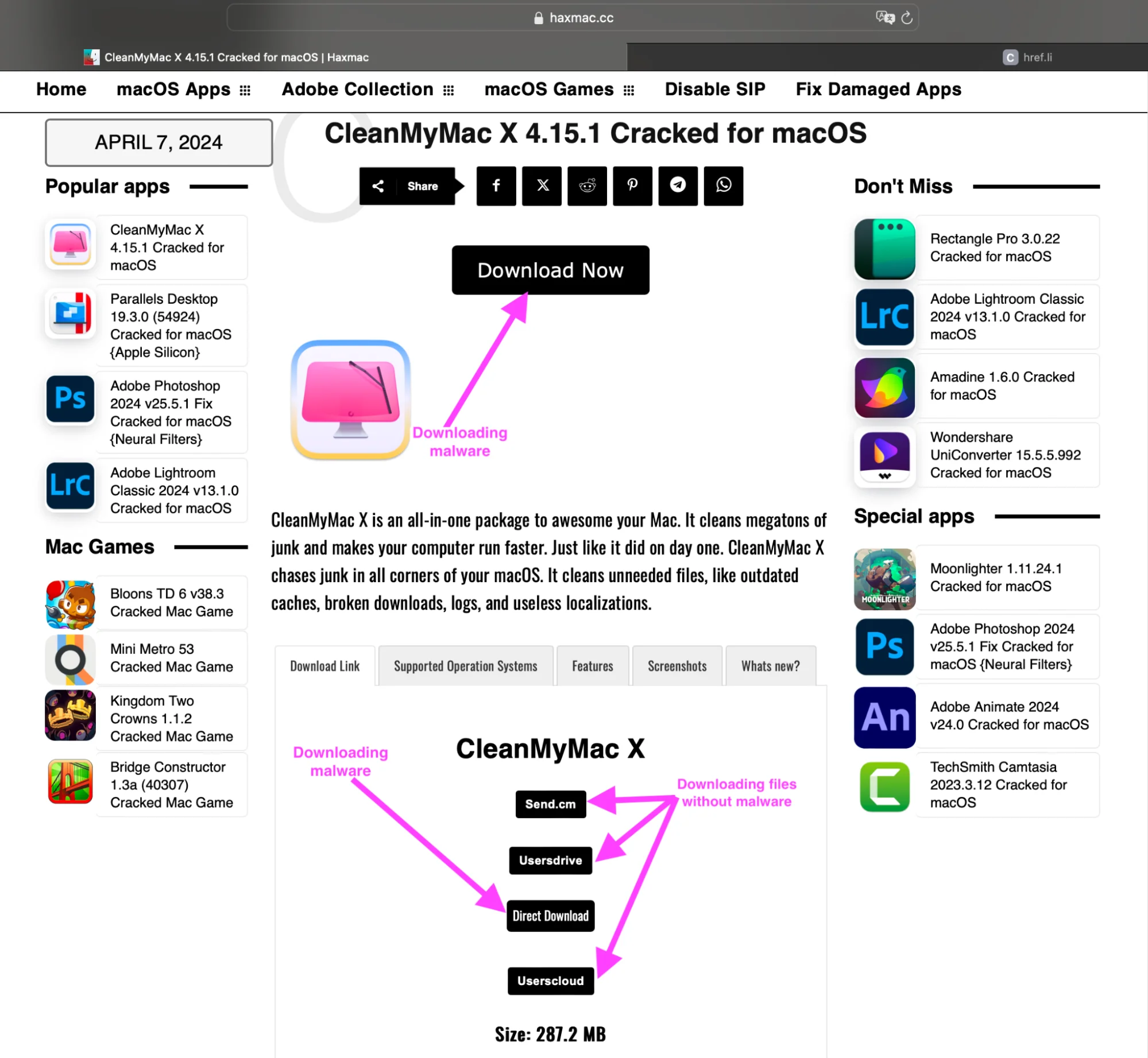
The website in question positions itself as a repository for cracked macOS software, serving as a haven for individuals seeking cracked versions of Adobe Photoshop, Adobe Illustrator, SQLPro, CleanMyMac X, and numerous other macOS applications.
![A screenshot of the main page of haxmac[.]cc.](https://moonlock.com/2024/04/Main-page-of-haxmac.cc_4.webp)
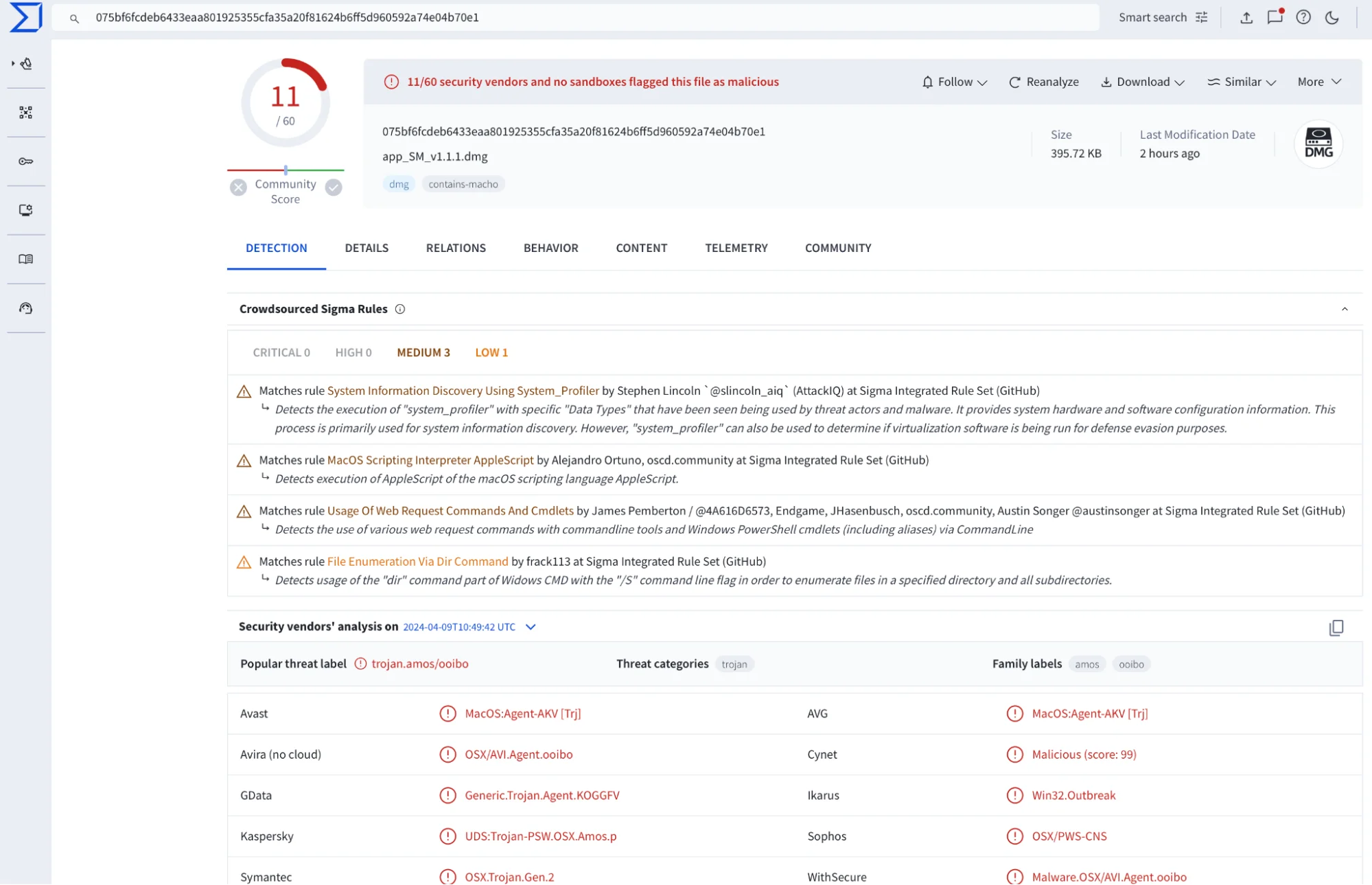
While the site appears to offer a range of legitimate software downloads, redirecting users to other services where non-malicious files are available for download, it has been discovered that clicking on the “Download Now” or the “Direct Download” button triggers the download of a malicious dmg file named “app_SM_v1.1.1.dmg,” which contains the Atomic Stealer malware.
Atomic Stealer malware found disguised as trusted software
Atomic Stealer is a sophisticated malware strain known for its stealthy capabilities and advanced functionality in stealing sensitive information. In its latest versions, it employs intricate techniques to evade detection by security software.
Once inside a system, Atomic Stealer can harvest a wide range of data, including credentials, financial information, and intellectual property, transmitting it back to its operators for exploitation.
Notably, it doesn’t matter which app from the catalog you want to download. Whether it’s CleanMyMac X, Adobe Photoshop, or something else, clicking “Download Now” or “Direct Download” will lead to the same DMG file being downloaded.
What we know about the distribution method
What sets this scheme apart is the cunning targeting that is being employed by the threat actors. Rather than casting a wide net and delivering the same malware to all users, they tailor their attacks based on the victim’s browser by leveraging the User-Agent header.
Safari users are served the macOS-specific Atomic Stealer, while those using Chromium-based browsers are redirected to a page hosting a zip archive containing the Remcos RAT, a notorious piece of Windows-targeting malware. By adapting their payload according to the victim’s browser, the threat actors increase the likelihood of successful infection.
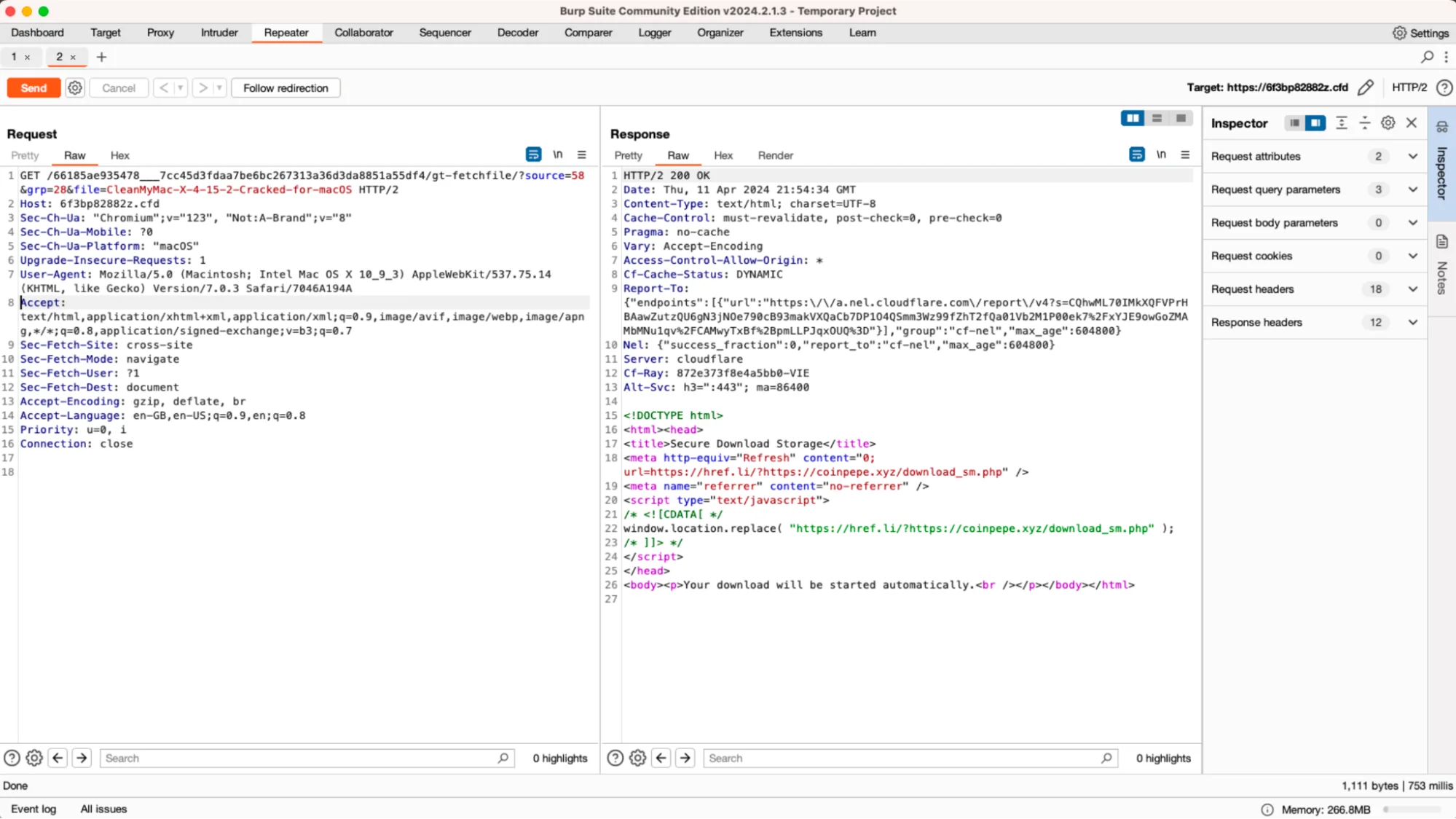
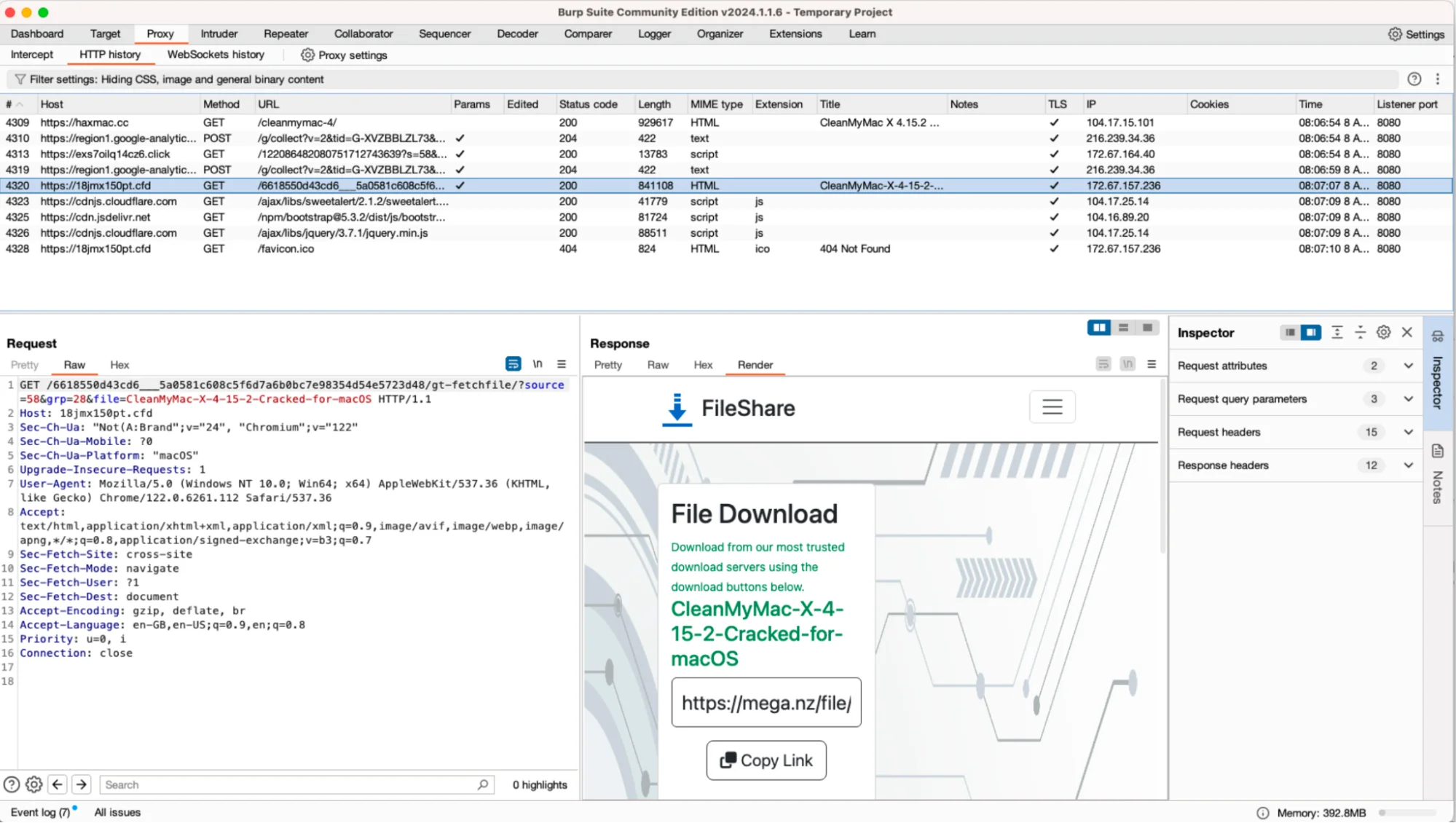
While preparing this article, we also noted that this is still an active campaign. When we posted about this case via our X account, Chrome users were redirected to https[:]//6ejj9u56155[.]cfd. After a few days, however, they began to be redirected to https[:]//18jmx150pt[.]cfd.
Now, the buttons that previously led to malicious software have been removed, most likely to avoid detection. This adaptiveness may indicate the agility of the threat actors behind the campaign.
![A screenshot of the haxmac[.]cc page after the "Download Now" and "Direct Download" buttons were removed.](https://moonlock.com/2024/04/haxmac.cc-page-after-buttons-Download-Now-and-the-Direct-Download-had-been-removed_9.webp)
It’s worth noting that haxmac[.]cc is not an isolated case. While searching for “download crack pc app,” we encountered another similar page: haxpc[.]net.
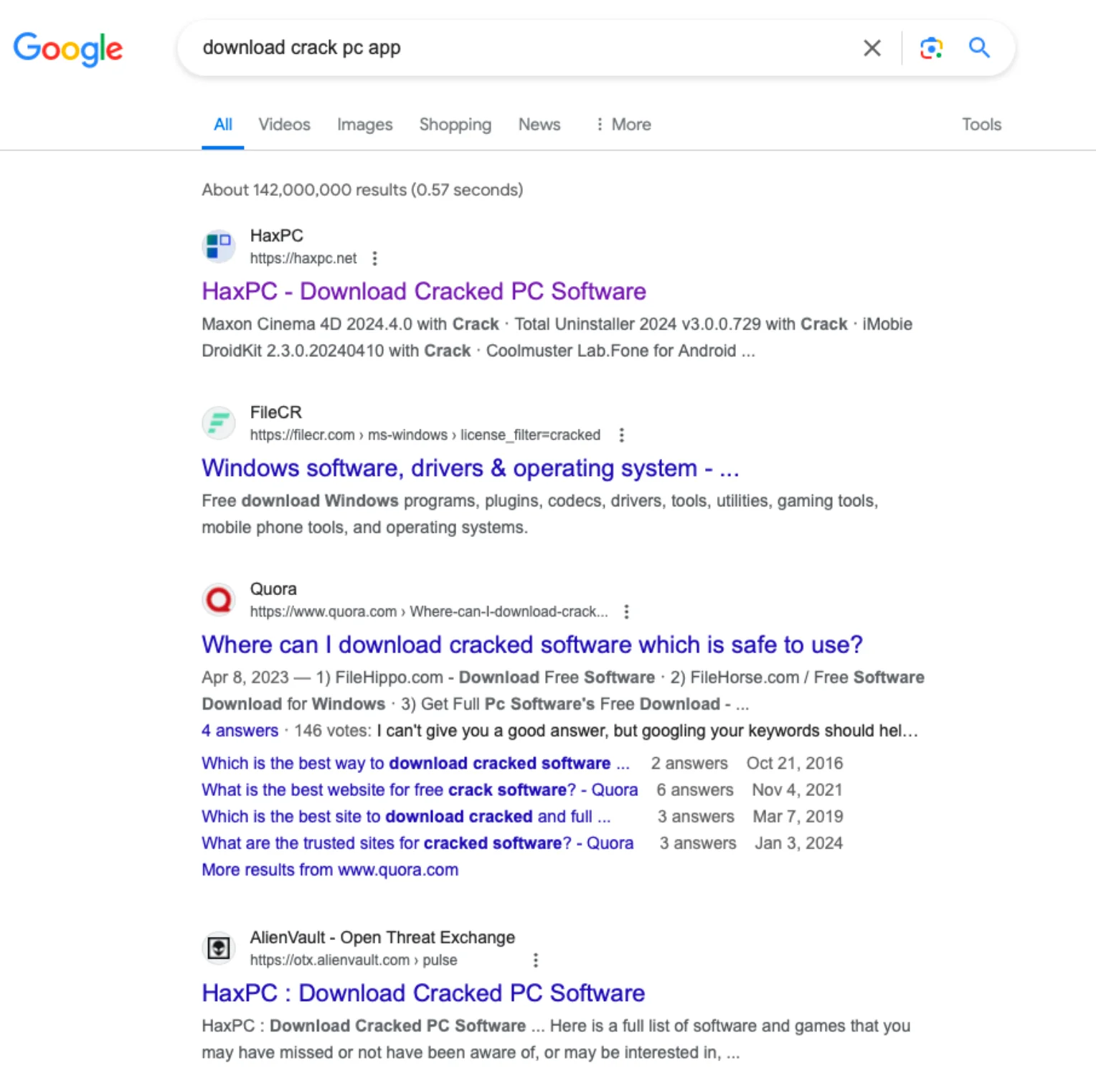
On this site, we found familiar buttons that led to downloading App_v1.0.4.dmg, a file containing a new variant of Atomic Stealer, which was detected by only 5 vendors on VirusTotal.
![A screenshot of haxpc[.]net with "Download Now" and the "Direct Download" buttons.](https://moonlock.com/2024/04/haxpc.net-with-Download-Now-and-the-Direct-Download-buttons_11.webp)
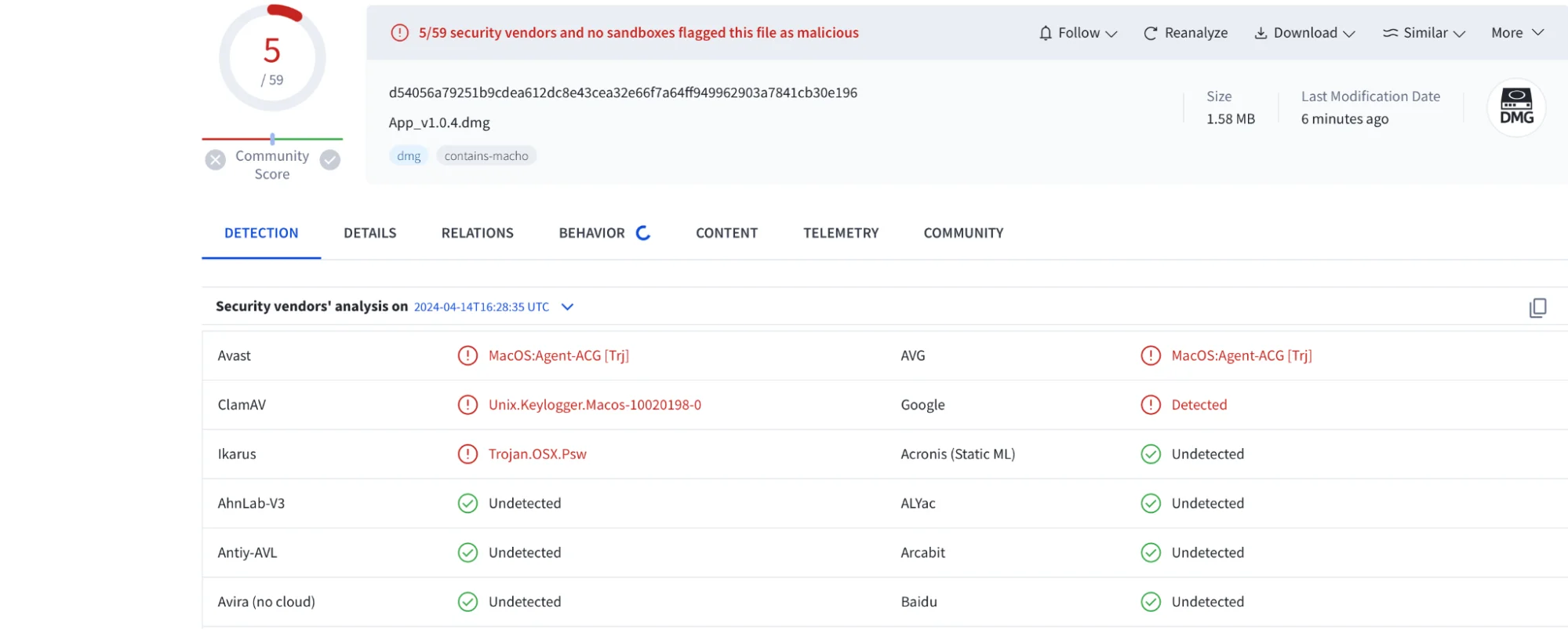
Moreover, many similar cracked software distribution sites have been found to distribute the Atomic Stealer malware. This seems to suggest a coordinated effort across multiple platforms.
Threat actors leveraging PPI through affiliate networks
It has become apparent that the distribution method is likely tied to a pay-per-install (PPI) service. This model incentivizes threat actors to distribute malware through affiliate networks, earning them a commission for each successful installation on a victim’s system.
In addition, we have observed PPI services being advertised and endorsed across multiple channels on Telegram, a popular messaging platform known for its privacy features, which often serve as hubs for cybercriminal collaboration and the exchange of malicious tools and techniques.
How to stay safe: Avoid cracked software
Our investigation into cracked software distribution revealed a complex web of deceit orchestrated by threat actors, posing significant risks to millions of users. The dynamic nature of these campaigns, as evidenced by the changing redirection URLs and the removal of incriminating buttons on haxmac[.]cc, underscores the adaptability and persistence of these adversaries.
For users, it’s crucial to avoid downloading cracked software or software from untrusted sources. Stick to official app stores and reputable websites.
Always keep your software and operating systems up to date. Additionally, using antivirus software such as CleanMyMac X, powered by Moonlock Engine, and being cautious of suspicious links or downloads can greatly reduce your risk of malware infections.
Indicators of Compromise (IOC)
| Indicators | Indicator Type | Description |
| 075bf6fcdeb6433eaa801925355cfa35a20f81624b6ff5d960592a74e04b70e1 | SHA256 | Atomic Stealer (dmg) |
| d54056a79251b9cdea612dc8e43cea32e66f7a64ff949962903a7841cb30e196 | SHA256 | Atomic Stealer (dmg) |
| 6e0e9e33c3930290b4daa8cc9dc784aae5b209d733c732e308a908e6bde020f2 | SHA256 | Atomic Stealer (dmg) |
| 3c39bf4ab58e21e3991e4a47caaa69c8a3f6e64f2eddffd3a40c2cd243a8b9ff | SHA256 | Atomic Stealer (dmg) |
| 7336719f7e294f02a282f7c8d43758288e8f5a6823b8d917cbd9e744370ee2cf | SHA256 | Atomic Stealer (macho) |
| 9f40383a6d1af5184034a21befaef19a87695aee925c5cf75db8291105a87936 | SHA256 | Atomic Stealer (macho) |
| 666d38cf4c0512b7b44323ef802638260f79999e7e7190589f7773f4cdec21d2 | SHA256 | Atomic Stealer (macho) |
| b1622c437d1684813f89a7e6bf24bbec73937eb563431d11341210babbe95ac9 | SHA256 | Atomic Stealer (macho) |
| 24783036f50017905f5402286e40b767db808116396635ed26f64eed0eea2135 | SHA256 | Remcos RAT (peexe) |
| haxmac[.]cc | Domain | Malicious Site with Cracked Apps |
| haxpc[.]net | Domain | Malicious Site with Cracked Apps |
| torrentmac[.]net | Domain | Malicious Site with Cracked Apps |
| 9to5crack[.]com | Domain | Malicious Site with Cracked Apps |
| https[:]//6ejj9u56155[.]cfd | URL | Malware Download URL |
| https[:]//18jmx150pt[.]cfd | URL | Malware Download URL |
| https[:]//imranfootwear[.]com | URL | Malware Download URL |
| coinpepe[.]xyz | Domain | Malware Download Domain |
Co-author: Artem Chumak






