With European elections about to begin on June 6 and rushed UK elections unexpectedly called by Prime Minister Rishi Sunak for July 4, countless warnings from cybersecurity experts are becoming reality.
For months, press and security organizations have warned that elections in Europe were expected to drive unprecedented levels of cyberattacks and misinformation campaigns. Now, a new study found that data from 918 British MPs, members of the European Parliament, and French deputies and senators was exposed and is being sold on the dark web.
During election season, the officials’ data leak is especially dangerous

On May 30, Proton revealed the findings of their investigation. The company scanned the dark web for 2,280 official government email addresses belonging to the British Parliament, European Parliament, and French Parliament. Disturbingly, the research found that about 40% of the total emails have been exposed.
The breaches and dark web data leaks of government officials include emails, passwords, birthdates, and other sensitive data.
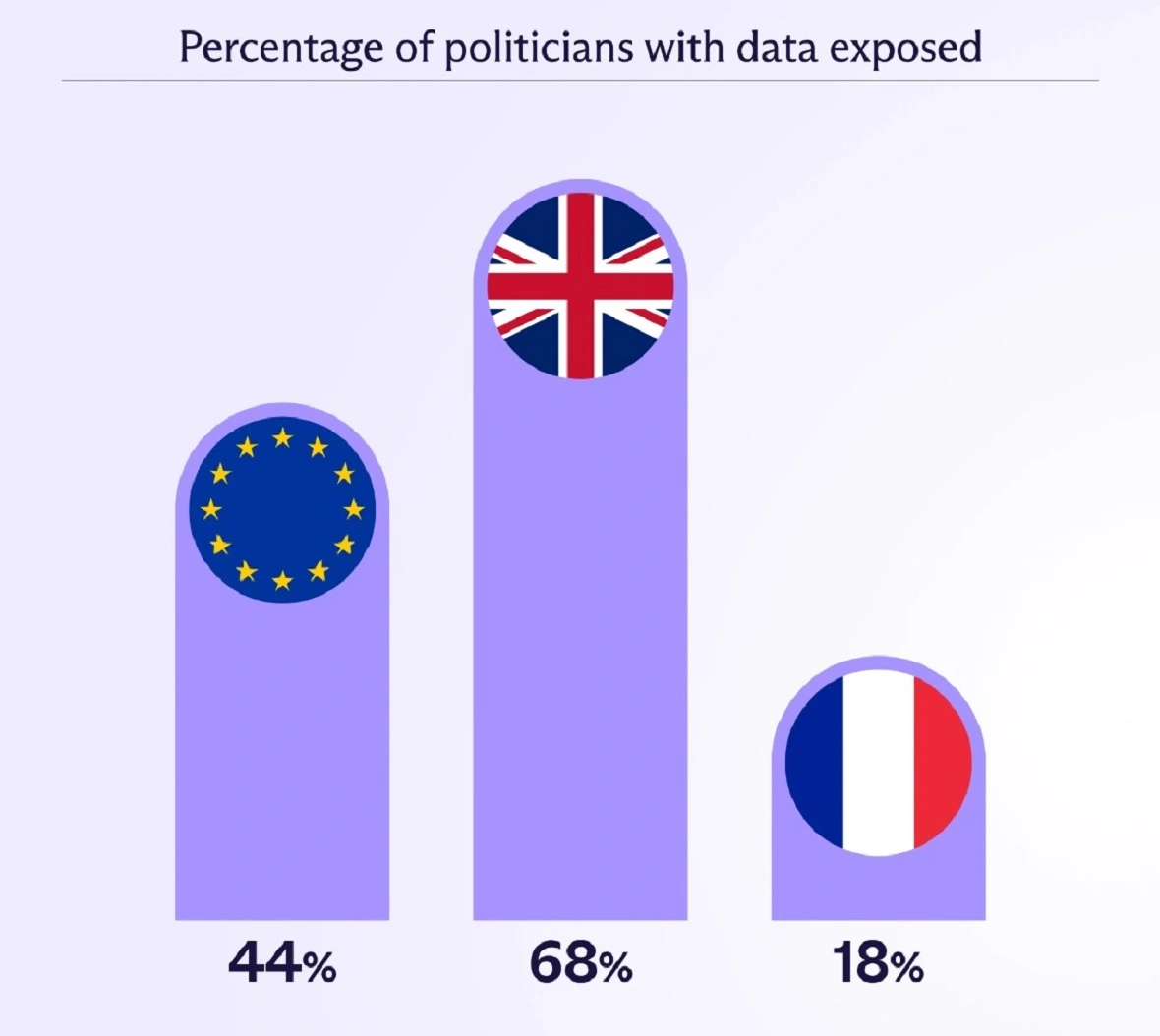
According to Proton, the British MPs had it the worst. More than two-thirds (68%) of all British MPs’ checked emails showed up on the dark web. EU MEPs followed, with 44% of checked emails found on the dark web. France fell in third with only 18% of emails but ranked high in passwords breached.
How did the Europe and United Kingdom government hack happen?
Proton explained that finding public government emails and sensitive data on the dark web does not necessarily mean that government entities have been directly breached. In fact, Proton found no evidence of cyberattacks on the British, European, or French parliaments.
So how did the data end up on the dark web if no government site was compromised by attackers? The answer is also shocking.
Apparently, government officials are using their designated government email addresses to sign up for public-facing services such as Adobe, LinkedIn, Dropbox, Dailymotion, and even dating sites. This is how their data ended up in the digital criminal underground.
What UK and EU government info is being sold on the dark web?
Along with the government emails, 697 matched passwords in plain text were identified. All politicians involved in the leak have been notified. However, if any government official used the same password for a third-party service as they did for their official account, government systems could have already been infiltrated.
The data stolen, leaked, and sold on the dark web includes:
- Emails
- Passwords
- Dates of birth
- Residential addresses
- Social media accounts
What can cybercriminals do with the leaked data?
With this data, cybercriminals can launch a multitude of attacks, including file-less attacks, identity theft, phishing, privilege escalation attacks, extortion, deep fakes, account takeovers, and misinformation campaigns.
Considering the high-profile nature of the leak, security experts should be considering all options — including worst-case scenarios.
Breached British Parliament emails totaled 443, with 216 including passwords. French Parliament elected officials saw fewer breached emails, 126 in total, but a staggering 320 passwords were leaked.
“Just over a month before the Paris Olympics begin, these results highlight concerns around politicians’ cybersecurity practices, where just one breach could be a serious national security threat,” Proton said in the report.
Just over a month before the Paris Olympics begin, these results highlight concerns around politicians’ cybersecurity practices, where just one breach could be a serious national security threat.
Proton
The implications for the EU and UK elections
It is standard practice for those who hold positions in government to be trained, skilled, and aware of cybersecurity and cyber threats. However, the Proton report shows that this is not the case whatsoever.

The report speaks badly of UK, EU, and French officials’ security practices, awareness, and capabilities. But that is not the only troubling conclusion.
As a large number of elected politicians turn a blind eye to basic security concepts like Zero Trust, government systems are put at high risk, and the psychological effects impact the wider society.
Large-scale dark web leaks and cyber scandals during key political moments such as elections not only absorb resources from other critical government tasks but erode the trust that people have in fair election processes.
Additionally, intelligence agencies dedicated to national security during election times must now look into the incident.
Proton has not attributed the dark web data leaks to any specific cybercriminal group or groups. However, the timing of the finding is undeniable. Whether the cyber attackers were financially or politically motivated is another unanswered question.
One thing is certain. The news comes just in time for one of the most critically decisive moments for the region. Elections in both the UK and the EU are expected to influence global geopolitical conflicts such as the Russia-Ukraine war, the Middle East, the Israel-Hamas conflict, and escalations in the South China Sea, as well as the next half a decade or more of policies.
Final thoughts
Proton’s findings paint a concerning picture of cybersecurity in times of election. Politicians, especially those with access to sensitive information, are prime targets for cyberattacks. Disruption attacks can have a significant impact on governments, potentially jeopardizing national security, election integrity, and even critical government systems. The consequences are undeniable.
Governments must take immediate action to bolster their cybersecurity defenses. Implementing more secure authentication technologies, deploying biometrics, and prohibiting the use of government email addresses for third-party services are all crucial steps. Additionally, governments should actively monitor the dark web and their entire digital attack surface to identify and mitigate potential threats.
The timing of this disclosure is alarming. With elections in the EU currently underway and the UK soon to follow, there is significant uncertainty surrounding the perpetrators and their motives. Whether these are coordinated attacks or isolated incidents, they cast a shadow over the democratic process, raising concerns about the security of upcoming elections.






