The SEKOIA.IO Threat & Detection Research Team has discovered a new stealer malware propagating across the internet called RisePro. The RisePro malware spreads via the PrivateLoader malware service, which is considered the stepping stone of many malware attack schemes.
Before discussing the new stealer, let us talk a little about the PrivateLoader malware service.
What is PrivateLoader?
PrivateLoader is a well-known malware-as-a-service (MaaS) used by different hacker groups to deploy malware packages from different families, primarily stealer malware. The PrivateLoader operator uses the Pay-per-install (PPI) business scheme to sell their service to hackers. That includes providing information about the target, delivering the malicious payload, and managing the payment process. PrivateLoader provides a dashboard for hackers containing different statistics to monitor their attacks. Such as which malware type was installed on the infected host and whether the attack — or installation — was successful.
The PrivateLoader service model allows entry-level cyber criminals to use its service to target internet users without bothering themselves with developing complex malware and finding ways to infect target devices with it.
What is RisePro?
RisePro is the latest malware type discovered that uses the PrivateLoader malware service. First detected in December 2022, RisePro targets the most popular web browsers (e.g., Firefox, Opera, and Chrome). It steals saved passwords, credit card information, and crypto-wallets. It can also steal your saved credentials for certain installed software, such as Discord and Authy Desktop.
RisePro can search infected computers for specific file patterns, such as banking and credit card receipt information. The data stolen by RisePro is saved into its working directory. It is then compressed as a .zip file (the stolen data filename carries this naming scheme “country code_victim ip address.zip”). Finally, the .zip file is delivered to the malware command and control server (C&C).
RisePro obfuscates the connection with its hackers’ command and control server. It uses the same obfuscation technique (byte substitution) used by the PrivateLoader malware service. This allows the malware to evade detection when sending the stolen data outside infected hosts.
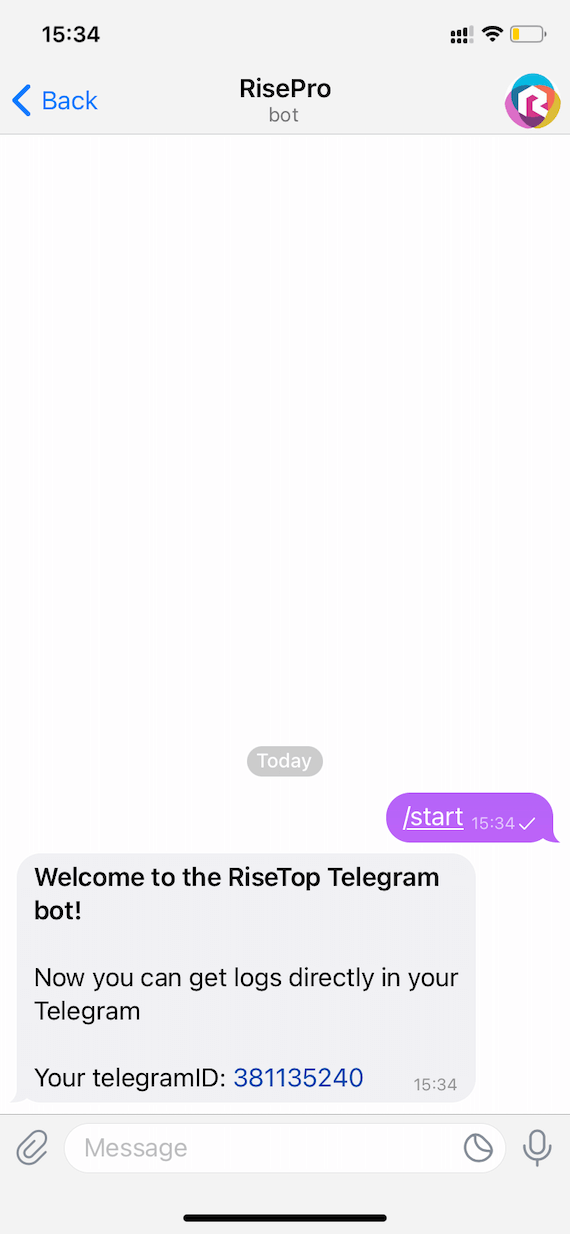
Is RisePro A new version of PrivateLoader?
According to SEKOIA.IO analysts, the similarities between the RisePro stealer and the PrivateLoader malware service suggest two possibilities:
- The RisePro malware stealer could be a modern version of PrivateLoader malware developed by the same hackers. However, it comes preconfigured to download and use its own stealer.
- The RisePro is a new stealer malware developed by a third-party hacker group. It uses the PrivateLoader malware service to infect users and steal their confidential data.
How to protect yourself from RisePro
- Keep your operating system patched with the latest security updates.
- Keep your installed applications and web browser extensions up-to-date.
- Avoid installing web browser extensions from unknown websites. It is always better to download browser extensions from the official store (e.g., Chrome Web Store for the Google Chrome browser).
- Install a robust anti malware program and keep it current.
- Do not open email attachments from unknown senders. Do not click on links within these emails.
- Avoid downloading cracked/pirated software.
The recent RisePro malware can inflict great financial damage by obtaining your banking, credit card, or crypto wallet information. Following the prevention steps above should protect you from falling victim to this new threat.