International media are warning users about a new phishing campaign carried out by hacker group Star Blizzard, which is linked to the Russian Federal Security Service (FSB). Let’s break down who Star Blizzard is, what this new attack is, and how to stay safe.
Top security agencies from the US, UK, and allies issue Star Blizzard alert
On December 7, numerous security agencies, including the US Cyber Command, CISA, and the UK. The National Cyber Security Centre (NCSC) issued a warning on the new and enhanced Star Blizzard phishing campaign.
The Russian-based hacking group is not new to the cybersecurity landscape. They have been highly active since 2019. Star Blizzard is also known as SEABORGIUM, the Callisto Group, TA446, COLDRIVER, TAG-53, and BlueCharlie.
Most of the phishing attacks that this group carries out are targeted against organizations and individuals from the UK, the US, NATO countries, and countries surrounding Russia.
Security organizations said that the new international cybersecurity alert was issued to raise public awareness. It is also to inform users of the new techniques the group is using to breach victim’s systems.
Star Blizzard targets the following sectors:
- Academia
- Defense
- Governmental organizations
- NGOs
- Think tanks
- Politicians
- Energy sector
- Defence sector
- Industrial sector
Breaking down the new Star Blizzard attack
The new Star Blizzard attack is sophisticated in its social engineering techniques as well as its new technical aspects.
This attack is a spear phishing attack. This means that the bad actors aren’t sending out mass malicious emails randomly. Rather, they are crafting each email with care, targeting specific individuals. Targets are chosen for their potential to have access to sensitive high-value information of interest to the group or its political motivations.
The tactics Star Blizzard uses
Security agencies warned that Star Blizzard is taking its time to research its targets. They are using open-source resources for reconnaissance. They scan through social media and professional networking platforms to get information on their potential victims and increase their chances of success.
Star Blizzard is known to use open-source resources to conduct reconnaissance, including social media and professional networking platforms.
US Cyber Command
The group also creates email accounts to impersonate known contacts of their targets and fake social media or networking profiles to impersonate respected experts. Plus, they use supposed conference or event invitations to bait victims.
They also create malicious domains, links, and websites that appear to be legitimate and safe to trick users into giving away their credentials. An email from Star Blizzard can come from Outlook, Gmail, Yahoo, or Proton.
According to reports, Star Blizzard prefers to send emails to personal accounts instead of emailing business accounts. This technique is used to avoid higher-level security associated with professional email accounts.
Another social engineering technique that the group has perfected is the building of rapport. They will not send out a malicious link or file in the first email. Instead, they’ll attempt to build a relationship with their target, often exchanging emails for long periods before sending out the malicious content.
Once the group has established trust, they will send a malicious link or file that directs the victim to a server they control. There, the victim is asked to enter his credentials. With the stolen credentials, the group will access the email account and steal:
- Emails
- Attachments
- Contact lists
Star Blizzard also configures breached accounts to forward emails, giving them ongoing visibility of victim correspondence.
Evasion techniques
A Microsoft Threat Intelligence report on Star Blizzard states that the group has improved its detection evasion capabilities since 2022.
New evasion techniques include:
- The use of server-side scripts to prevent automated scanning of actor-controlled infrastructure
- Use of email marketing platforms to hide true email sender addresses
- Use of a DNS provider to hide IP addresses of the group’s virtual private server (VPS) infrastructure
- The use of password-protected PDFs or links to cloud-based file-sharing platforms where PDF lures are hosted
- More randomized domain generation algorithm (DGA) for actor-registered domains
How to stay safe from the Star Blizzard attack
Star Blizzard has been linked to espionage, political cyber warfare, and international affairs. It has expanded recently to defense and energy. The group has also targeted any sector supporting Ukraine or those who do not align with Russian political agendas, including academia and information security companies. Additionally, security organizations warn that the group’s list of targets is expanding.
To protect yourself against Star Blizzard spear phishing attacks:
- If you work or are connected to any of the sectors that this group targets, be aware of Star Blizzard´s techniques and remain vigilant.
- Use strong passwords and enable MFA.
- If possible, set up screen locks and use biometrics security.
- Set your social media accounts to private or set higher restrictions for who can view your profile and data.
- Always double-check if the person contacting you via email, SMS, or other media is who they claim to be.
- Never click on suspicious links, download files, or visit untrusted websites.
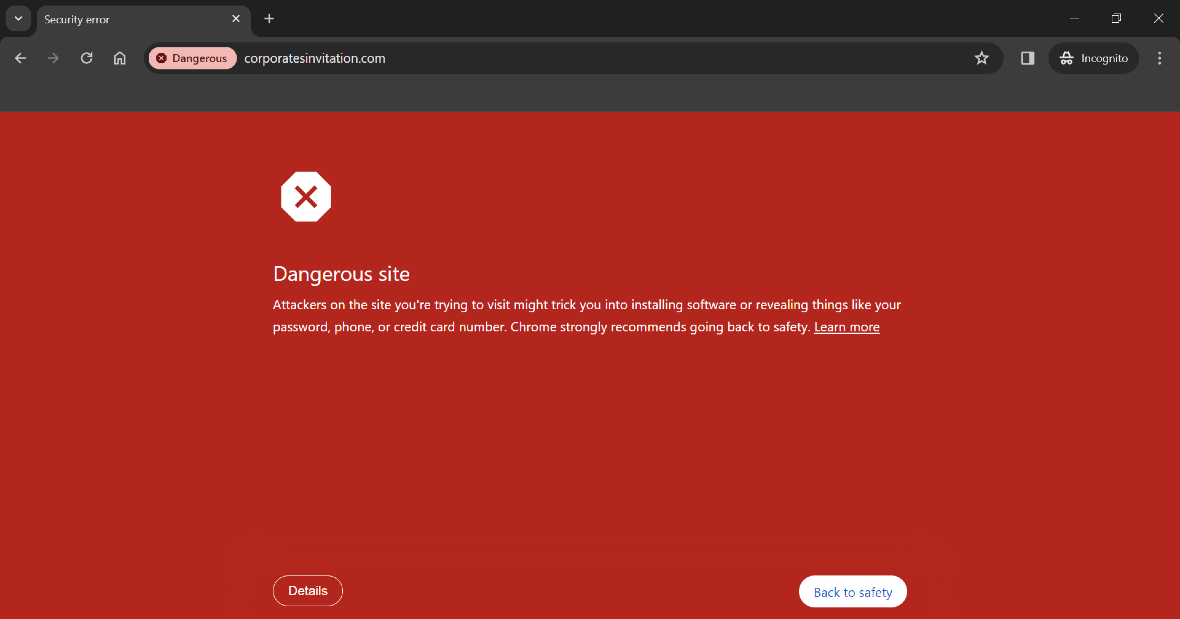
- Pay attention to web browser warnings. Safari, Chrome, Firefox, and other web browsers will flag a phishing website. If your browser says it’s dangerous, stay away.
- Never enter your credentials or passwords to access PDFs or if prompted by a website. Unreadable PDF files or websites that ask for your email and passwords are not normal and should be treated as highly suspicious.
- A phishing attack may come from any type of email, but Microsoft warns that Proton emails have been linked to this new phishing campaign more than other providers.
- Set up and run trusted, professional anti-malware on your devices.
- Stay on top of cybersecurity news.
- Keep your OS, apps, and software updated.
The final word on this attack
Star Blizzard continues to run spear phishing campaigns for two simple reasons: they have mastered this criminal technique, and they continue to be successful. They know that all it takes for them to breach systems is for one person to make a mistake.
Follow the guidelines in this report and those listed by the security agencies linked in this report to keep your data and account secure. If you have fallen victim to a Star Blizzard attack, contact the authorities in your country.