Google, Brave, Edge, Firefox, Opera, 1Password, Signal, and others have released an emergency update. At the center of this cybersecurity incident is a mysterious type of attack that uses WebP — a type of image format commonly used online. The update comes just days after Apple rushed to secure iPhones and iPad devices from a zero-day threat with its iOS 16 security update, as Moonlock recently reported.
Companies like Google and Microsoft have urged users to immediately update their browsers. And while there has been no official statement from Google or other companies connecting the attacks with the recent Apple security update, Forbes reported that “coincidences run deep.”
What’s going on with the zero-day attack using WebP images?
For obvious reasons, when zero-day exploits are discovered and patched, big tech companies refrain from releasing technical details. What we do know is that the new attack, which can affect most web browsers, password managers, and messaging services, is known as CVE-2023-4863.
Zero-day attacks, as the name implies, are devastatingly abrupt. These attacks happen when cybercriminals discover a weakness in a system, app, or program and immediately exploit it.
New security updates are released in response to zero-day attacks as quickly as possible. And while users are informed of the required updates, the technical details are usually left for later. The lack of details is the reason why, at this point, no one can confirm whether the Apple security update created to patch the zero-day exploit dubbed BlastPass by CitizenLab (the first to discover it and inform Apple) is the same as CVE-2023-4863, which is affecting major web browsers and other companies.
However, if we read between the lines, a connection seems evident. Not only is the timing of the updates too close to be a coincidence, but both BlastPass and CVE-2023-4863 use images to hide malicious code.
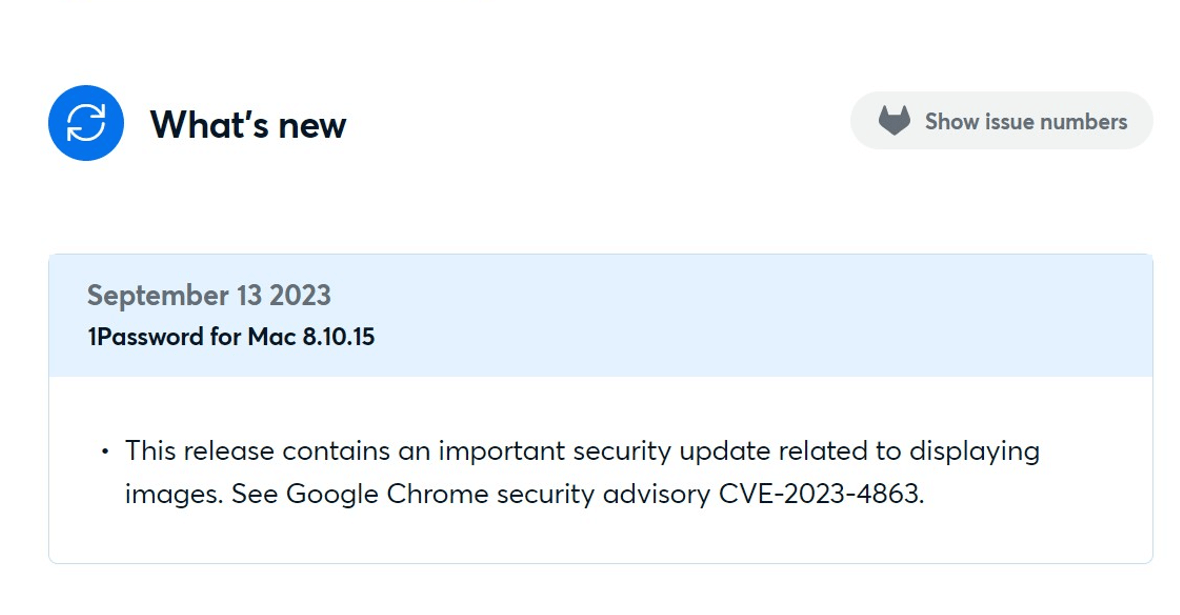
The connections between attacks on browsers and Apple’s BlastPass update
On September 11, when Google announced the vulnerability and released its new upgrade, the company said that the “critical CVE-2023-4863 is a heap buffer overflow in WebP.” The company added that it was reported by Apple and Citizen Lab. Therefore, it seems to be implied that the exploits are in some way related.
Like CitizenLab and Apple, Google also said they were “aware” that the exploit “exists in the wild.” This means that attackers are actively using this vulnerability to run real attacks.
A day after Google released the new update, Microsoft confirmed that the attack was a heap buffer overflow in WebP and issued an alert. Because Edge utilizes Chromium Open Source Software (OSS), the browser was also exposed. Microsoft assures that its new update resolves the problem.
However, things have continued to escalate. On September 13, 1Password released a new important security update that they stated was “related to displaying images” and was connected to CVE-2023-4863. The update is for 1Password Mac users. Numerous other browsers, such as Mozilla’s Firefox and Google Chrome, followed suit, releasing new security updates.
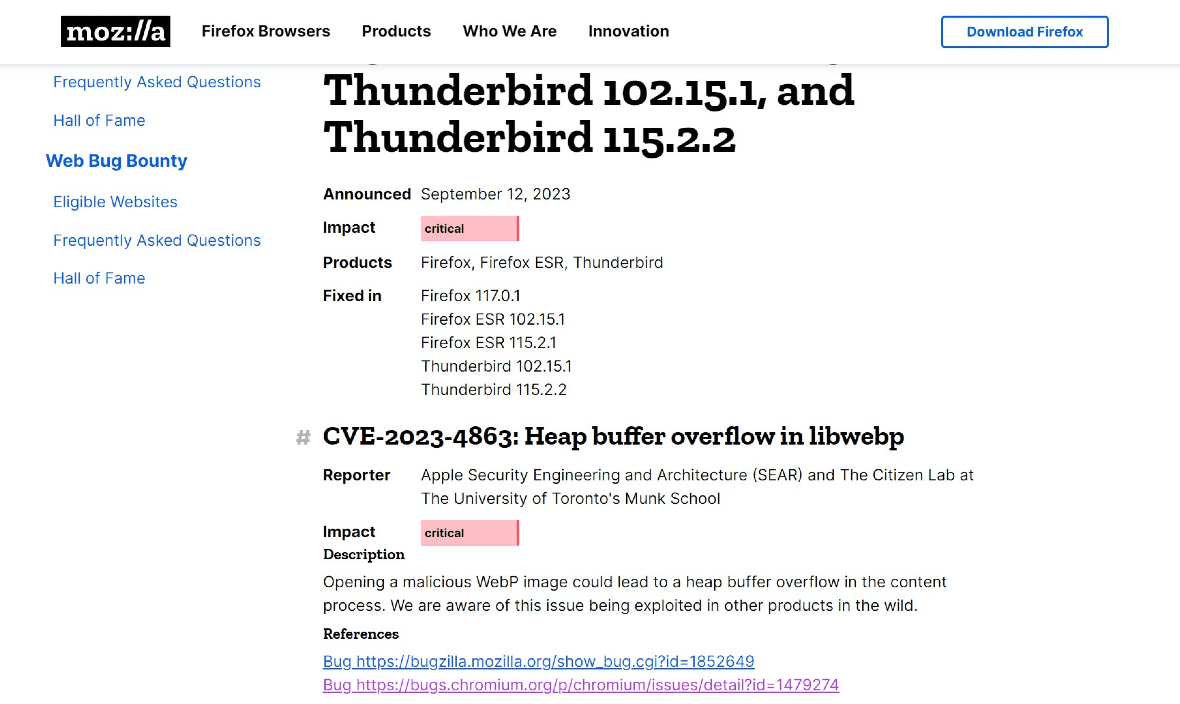
Browsers and sites affected by CVE-2023-4863
There are several browsers and services that have released CVE-2023-4863-linked updates. The list includes:
- Google Chrome
- Microsoft Edge
- Brave
- Firefox
- Opera
- Vivaldi
- Signal
- Signal Desktop
- 1Password
How criminals run a heap buffer overflow attack
In simple terms, when an app, a program, or a maliciously altered file seeks to store or write data on a computer or phone, it “asks” the operating system for a chunk of memory. This chunk of memory is known as the “heap buffer.”
If the program, app, or file writes more data than it is supposed to, the heap buffer will overflow. This overflow can cause a program to crash, but it can also give an attacker a way into your device.
By hiding malicious code in the buffer heap overflow, cybercriminals gain control of devices. They can install malware such as ransomware, keyloggers, cryptojackers, or spyware. They can also control a device and use it to launch more attacks. This technique also allows them to steal sensitive data, compromise accounts, or even damage computers and devices.
What’s next, and how do you stay safe?
At this point, what users should be focusing on is running immediate updates if they are using any of the affected browsers and services. It is also a good idea to check for new operating system updates on your computer, laptop, smartphone, or tablet. The bottom line is if you have a pending update, run it. And enable automatic updates to keep up with new releases.
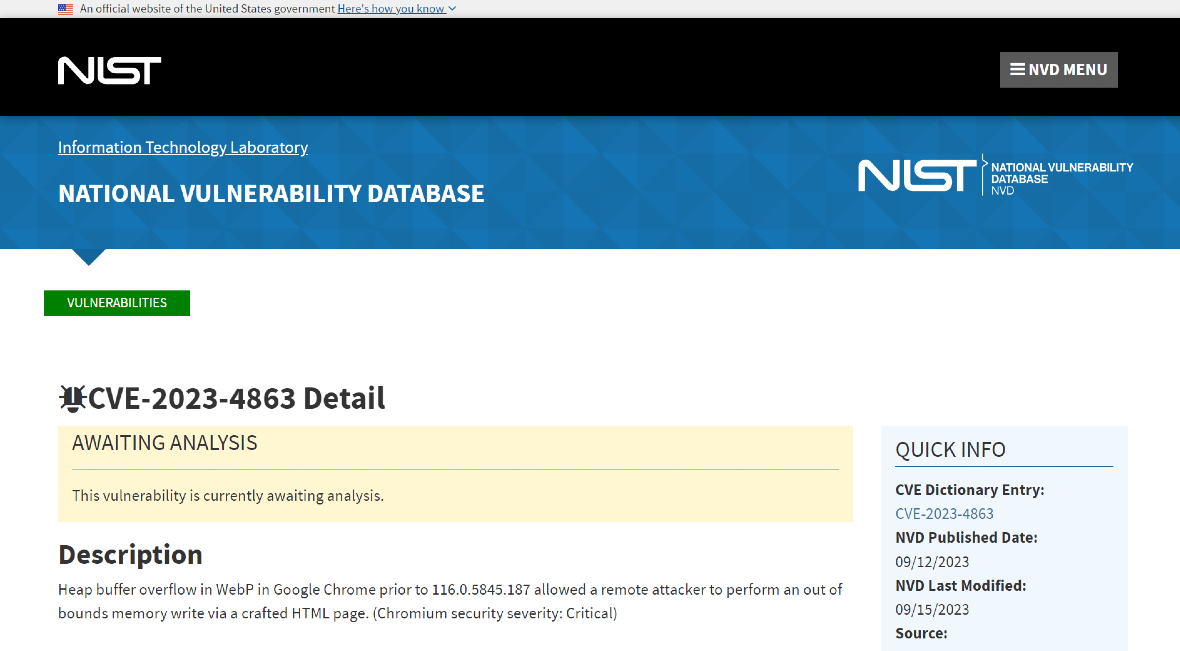
The United States Government’s National Institute of Standards and Technology (NIST) has listed CVE-2023-4863 in its national vulnerability database. Users can consult the full report for more information, including links to upgrades, advisories, solutions, and tools. A full analysis of the exploit is also expected to be made public at NIST soon.
There are several other things users can do to protect themselves. Since attackers using these exploits are reported to be maliciously altering image files, you should double-check any message or email you receive that includes an attached image. If you don’t know the sender or the message is suspicious, the best course of action is to simply delete the message. Note that the message may come through email, media, or any other messaging app.
Finally, if you received an email warning you about security or password changes in any of your accounts, take immediate action. Change your password if needed and enable multi-factor authentication.
These threats are still in their early days of discovery. Keep an eye out for news regarding updates to better understand the connections and the techniques being used, and be prepared to further upgrade your security if required. Overall, there’s no reason to panic, but when zero-day attacks affect several major players in the tech industry, it’s best to be proactive and vigilant — and to stay informed.