Cybercriminals are using a new, surprisingly simple technique to bypass Apple’s SMS anti-phishing security feature. The new trick impersonates the way legitimate modern SMS bots used by governments and organizations around the world work. This familiarity is what drives attack success rates.
From healthcare to bank notifications, users have become accustomed to confirming appointments or transactions via automated texts. For example, it’s normal to receive legitimate automated SMS messages when confirming a doctor’s appointment, verifying a purchase, or going through other processes. To respond to these bots, we usually reply with short words, numbers, or just a few letters. We are often prompted to “respond with ‘YES’ or ‘NO.’”
However, if you reply to an unknown iMessage text, certain security features get disabled. That is exactly what this new campaign is about.
In this report, we look at how the new phishing scam works. We also examine how to protect yourself and the state of the global smishing criminal industry.
How criminals convince you to disable Apple’s “unknown sender” iMessage link security
On January 12, Bleeping Computer reported that cybercriminals are now exploiting “a trick to turn off Apple iMessage’s built-in phishing protection.” The media outlet said that these are not isolated, scarce cyberattacks. Rather, they are part of a new wave of smishing.
“Over the past couple of months, Bleeping Computer has seen a surge in smishing attacks that attempt to trick users into replying to a text so that links are enabled again,” Bleeping Computer explained.
Normally, links sent by unknown senders are disabled unless the user replies to the message or makes the person a “known sender.” Attackers are bypassing this by instructing their victims to reply, exploiting a loophole in the system. Thus, the users open themselves up to receive links.
Scams taking advantage of this security loophole
Criminals are using popular smishing templates such as the USPS shipping scam and the fake “unpaid road toll” scam. To these templates, they add malicious links designed to steal your credentials.
The message also contains detailed, step-by-step instructions that appear to be legitimate. Following these steps, however, enables the malicious link that iMessage originally disabled to protect users.
These step-by-step instructions are found at the end of the text. They say: “Please reply Y, then exit the text message, reopen the text message activation link, or copy the link to Safari browser to open it.”
We know that cybercriminals are impersonating the US Postal Service and payroll authorities. The same trick can be used to impersonate any organization and brand.
Of course, not everyone will fall for this trick. Most people are aware that suspicious texts with unsolicited links are a clear red flag. Still, it’s important to remember that if you ever receive one of these messages, you should not click on the link.
Apple says you can block, filter, and report suspicious SMS text messages at [email protected]. When you email Apple, include a screenshot of the text you are reporting. The Cupertino-based company adds that iMessage cannot directly prevent unknown senders from texting users.
A closer look at an iMessage smishing link
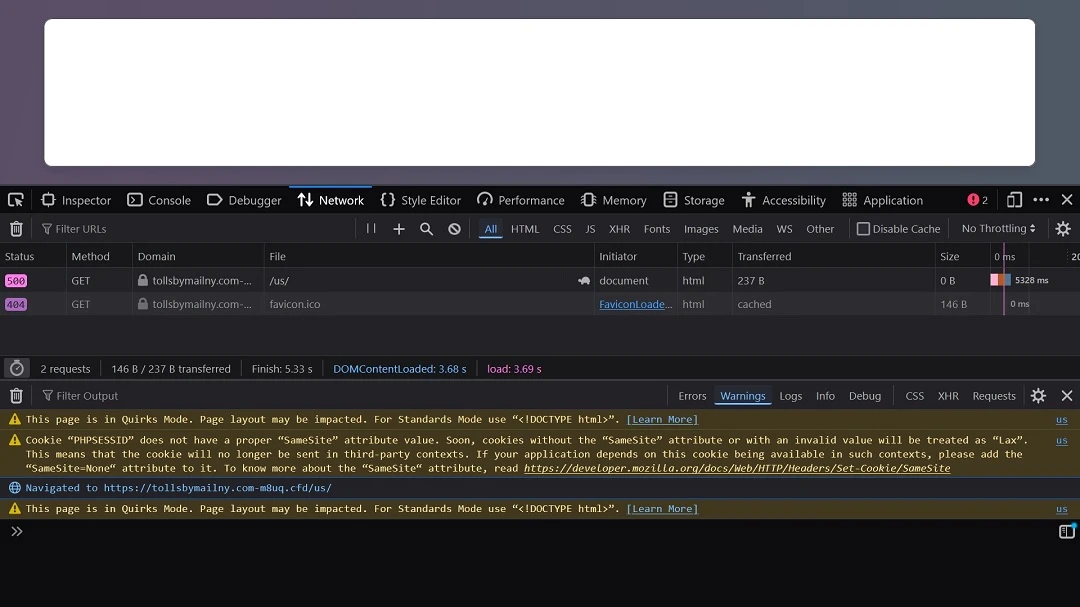
Moonlock checked one of the links included in smishing attacks discovered by Bleeping Computer. We found that the site, while apparently defunct, had “SameSite” cookie issues. This suggests the website might be vulnerable to cross-site request forgery (CSRF) attacks.
Cross-site request forgery (CSRF) is a web security vulnerability where an attacker tricks a logged-in user into unknowingly submitting a malicious request to a website. CSRF can lead to password exfiltration, financial theft, identity theft, and reputational damages.
We also found that the website appeared to make minimal requests and was likely to load basic content. This simplicity could be a tactic to avoid detection by security measures.
Area code +63: Smishing industry in Asia
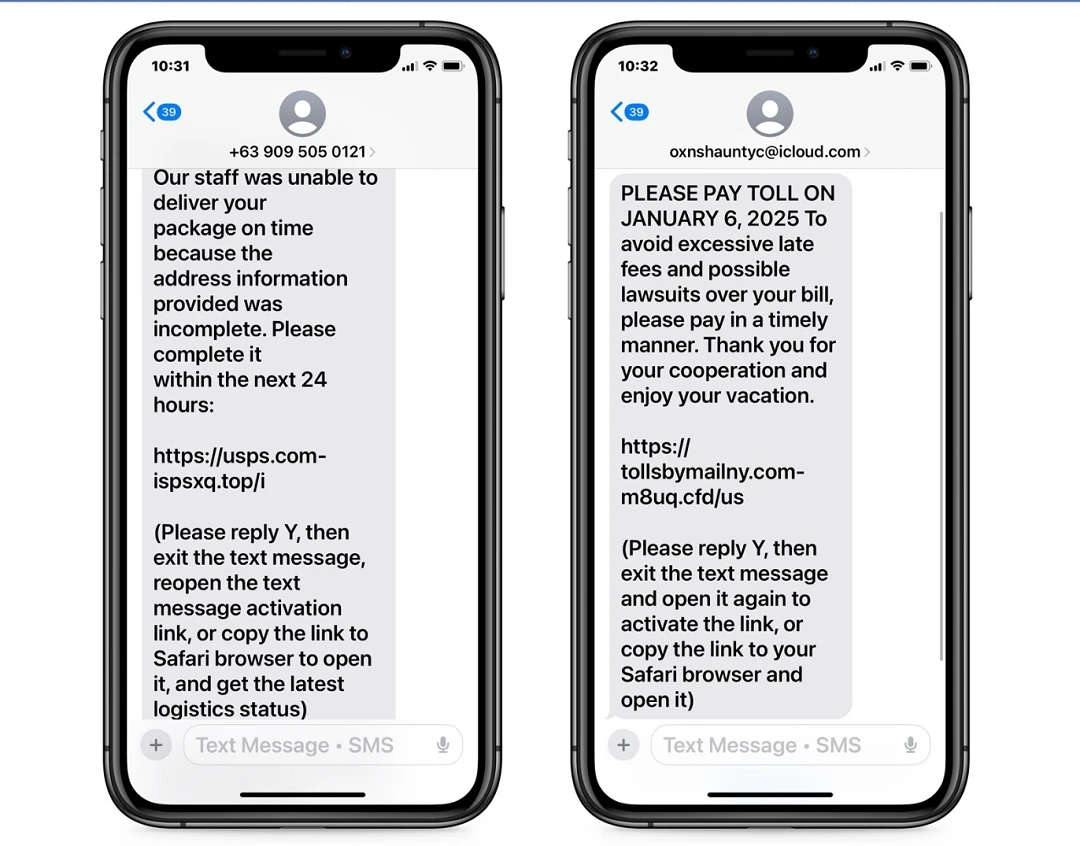
One of the phone numbers identified by Bleeping Computer in this new wave of iPhone smishing attacks includes the country code +63. This country code belongs to the Philippines. The attacker’s infrastructure could be located in this region. Or attackers could simply be making it appear as if the texts come from this region.
Coincidentally, countries like the Philippines, Thailand, Vietnam, Burma, China, and Japan have been identified as leading global areas affected by large-scale cybercriminal SMS scams. Additionally, large cybercriminal operations that run all types of scams are known to operate in Southeast Asia and have been linked to Asian triad transnational cybercriminal syndicates involved in money laundering, human trafficking, pig butchering, and other cyber crimes like SMS scams.
A rise in smishing that targets the US, the UK, and Europe is always alarming. This may imply that Asian criminal operators are expanding their activities into English-speaking regions.
It is worth noting that any user can receive an SMS message from a +63 number (Philippines) even if the sender is not physically located in the Philippines. To accomplish this, the sender or attackers would simply need to use voice over IP (VoIP) services, spoof legitimate numbers, or use automated modern SMS blasters or dark web automated smishing-as-a-service technologies.
How to protect yourself from the new iPhone text scam
When receiving an iMessage, checking the number or the email of the person sending the SMS can help you identify if the text is a scam. International numbers, iCloud email addresses, and numbers and contacts you have never seen before should raise immediate suspicion.
Follow these simple rules:
- Do not click on any links in the message.
- Do not reply to the message.
- Do not provide any personal information.
- Block, Delete, and Report the text.
Smishing-as-a-service, a growing threat for iPhone users
iMessage scams are nothing new. What is on the rise is the use of dark web services that automate the entire process of smishing. As users spend more and more time on their mobile devices and less on desktop environments, cybercriminals have turned to mobile cyberattacks and scams.
Smishing-as–a-service or phishing kits with powerful built-in features can be acquired by anyone with an internet connection on the dark web. These kits come with automated technologies that can generate a wide range of SMS messages. They use pre-built templates and develop custom-made phishing pages.
The widespread accessibility of these criminal malware solutions has dramatically lowered the technical bar. Cybercriminals no longer require the same level of skills. This has dramatically scaled cyberattacks on a global scale.
Smishing, which used to occur mostly in Android environments, has rapidly shifted to target iOS. The criminal industry developing these smishing tools is resourceful and possesses advanced technical skills.
Let’s look at just one case to understand the state of smishing today.
Last year, Moonlock reported on a new Chinese criminal platform called “Darcula.”
Darcula employed advanced technologies, had over 20,000 phishing websites, and offered cybercriminals ready-to-use social engineering resources with prices that started at $11.13 per week for the common source code for the malware. Darcula targeted Apple users via iMessage. It offered more than 200 phishing templates to impersonate different organizations and companies from more than 100 different countries.
How widespread is smishing globally? KeepNet says SMS phishing scammers are spoofing top brands including Amazon, Microsoft, Netflix, USPS, pay tolls, tax authorities, Apple, and FedEx. According to the company, over 3.5 billion phones receive unwanted SMS messages daily.
Final thoughts
Cybercriminals are extremely creative in their drive to breach robust cybersecurity features such as Apple’s iMessage anti-phishing. Simple tricks like the one used in this case are usually patched up rather rapidly, but by the time Apple develops the patch, millions of SMS might have been sent. Furthermore, when the patch is released, criminals just move along to find another vulnerability.
The only way to stop this never-ending and escalating cat-and-mouse game is to go right to the source. Attribute and identify the criminal developers and distributors, and notify law enforcement agencies in the hope that it will lead to arrests.
Still, users can make a difference. While smishing is becoming more difficult to detect because of these types of tricks that seem to blend into our normal digital life, cybersecurity awareness and caution still work like a charm. So stay alert, and if you get one of these messages, you know what to do: Block, report, and delete.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iOS, iMessage, and iPhone are trademarks of Apple Inc.






