Spear phishing is a targeted attempt to trick you into divulging your personal information. Attackers do this by pretending to be someone you know and are likely to trust. The fact that these attacks are targeted makes them particularly dangerous, and this bears out in statistics showing that spear phishing attacks are much more likely to be successful than regular phishing attacks.
Thankfully, spear phishing attacks can be dealt with in roughly the same way as phishing attacks. The only difference is that you need to be extra vigilant when assessing whether a communication is legitimate because an attack can seem pretty convincing, depending on the amount of research the attacker has done.
Trying to avoid scams?
What is spear phishing in cybersecurity?
Phishing is the attempt to trick users into divulging personal information by sending mass messages pretending to be a trustworthy source, such as a reputable company. These attacks cast a wide net, just as one might cast a literal net when seeking to land many fish.
Spear phishing takes this idea one step further. A spear phishing attack is a targeted phishing attack. Instead of casting a wide net, spear phishing targets a single particular fish.
With this in mind, we can give the following spear phishing definition: Spear phishing is the targeted attempt to trick a user into divulging personal information by sending messages pretending to be someone the user is likely to trust based on research done by the attacker.
How does spear phishing work?
First, a spear phishing attacker identifies their target. If they target you, it could be for many possible reasons. It might be for personal reasons, such as revenge. It could be because they’re targeting the company you work for, or they might be seeking access to customers of the bank you use.
The attacker then researches you to come up with a convincing pretext for their phishing message. They might scrape the internet for information about you to personalize the message they’ll send to you, using the name of a service you actually use and referring to you by your full name.
Next, the attacker composes and sends the phishing email, text, or other kind of message to you. They will try to convince you that they’re someone they’re not, hoping you take the bait and either click on a link they provide, reply with personal information, or download malware.
Finally, if you visit the link, divulge your information, or download malware, the attacker will use this for malicious purposes. This could include identity theft, theft, accessing work accounts to steal company information, and so on.
Basically, a spear phishing attack is an instance of a malicious actor (a cyber attacker) using detailed research on a target to create a convincing pretext, then sending them a message using this pretext to trick them into divulging personal information.
The history of spear phishing
Spear phishing has become a staple cyber attack today, but it wasn’t always that way. Here is how spear phishing developed:
- Pre-2009: Phishing was primarily done with nets rather than spears, metaphorically speaking. In other words, most phishing attackers didn’t research specific targets and instead relied on the law of large numbers, assuming that even without a tailored approach, someone was bound to fall for an attack if they simply distributed it to enough people. This worked well when users weren’t as familiar with best digital security practices.
- 2009–2011: Between 2009 and 2011, social media started to boom, and people began to learn more about observing good digital security practices. Users became more savvy at avoiding the most common kinds of phishing scams online. Consequently, attackers started to realize they needed to get more targeted in their approach.
- Early 2010s: While they existed prior to this time, it was after 2011 that spear phishing attacks started to become more prevalent as mass phishing attacks declined.
- Late 2010s onward: New mediums for spear phishing scams started popping up, such as text messages (smishing), voice chat (vishing), social media messaging, and others. Researching potential victims has become easier for attackers in many ways, thanks to increasing social media use since the mid-2010s. With more people using social media services, users have bigger digital footprints, which attackers can scrape for their research.

Spear phishing examples
Because spear phishing refers to a targeted attempt to scam someone, it’s no surprise that some spear phishing victims have made the news. After all, if an attacker is going to go to the effort of targeting a specific person or organization, it makes sense to pick a high-profile target.
- 2008 Red October spying campaign: In 2013, Kaspersky Lab identified a spying campaign that had targeted “diplomatic, governmental and scientific research organizations in several countries for at least 5 years” (i.e., since at least 2008). The associated “Rocra” trojan attacks were targeted phishing emails crafted for the diplomatic, government, government, and scientific officials.
- 2011 RSA hack: An employee of the American security company RSA, the creator of the widely adopted SecurID 2-factor authentication (2FA) mechanism, was the victim of a spear phishing attack. The attacker sent an email with an attachment that they claimed was a “2011 Recruitment plan.” The employee downloaded the attachment, which was actually malware. The end result was that the hackers gained access to information about how SecurID tokens were made, potentially compromising anyone using the 2FA system. This allowed them to attack other major companies, like the security company Lockheed Martin.
- 2020 Twitter Bitcoin scam: Attackers managed to take over the Twitter accounts of several famous celebrities, politicians, and businesspeople. They accomplished this thanks to spear phishing attacks that leveraged information they’d gained from scraping public-facing sites such as LinkedIn to impersonate Twitter employees. This resulted in numerous high-profile Twitter accounts being compromised and linking out to Bitcoin scams.
Why is spear phishing so dangerous?
Phishing is dangerous, and spear phishing is arguably even more so. This is, in part, because human beings can always be a weak link in any security system, and spear phishing exploits this fact.
The following are some of the primary reasons why this type of phishing is so dangerous.
Increasingly widespread
One reason spear phishing is so dangerous is just because it’s very common. In fact, according to security company Egress, phishing (including but not limited to spear phishing) is responsible for 79% of account takeover attacks.
Barracuda says that, as of 2023, “50% of organizations were victims of spear phishing in the last 12 months.” While the consequences may vary, attack attempts are clearly very common.
Harder to spot and more likely to be successful
Perhaps most obviously, spear phishing attacks are particularly dangerous because they’re often harder to identify than normal phishing attacks. This gives them a higher rate of success when it comes to tricking victims. These attacks are harder to spot because the attacker takes more time and care in crafting a compelling pretext by doing targeted research.
Compromised emails and account takeovers
In the Email Security Risk Report linked above, Egress also found, from the data pool they looked into, that 94% of organizations have had “email security incidents.”
Email accounts can be especially dangerous to have attacked because a compromised email account can lead to any number of other account takeovers. For instance, an attacker with access to your email account could reset your password and lock you out of any and all accounts you’ve used that email address to sign up with.
Identity theft
One of the scariest possible consequences of any phishing attack, including a spear phishing attack, is identity theft. An attack, if you fall for it, could give the attacker all they need to carry out identity fraud and ruin your credit or worse.
Business compromises
Spear phishing attackers often target people who are likely to give access to “bigger fish,” such as their organization’s accounts and personnel. If the personal information that you use to access business accounts or services is compromised, the attacker might use this information to gain further information about your company or others who work for it.
This kind of targeted attack is on the rise, too. Trend Micro states that “business email compromise (BEC) detections rose to 446,234 in 2023, a growth of 16%.”

Phishing vs. spear phishing: How do they differ?
Spear phishing is a kind of phishing, but it targets a specific person or people to create a more convincing pretext and make it more likely that they’ll fall for the scam than a regular phishing scam.
Here are the main differences:
- Personal connection: A spear phishing message is more likely to claim to be someone you know, because a spear phishing attacker might research who you know and use this to try to trick you.
- Less urgency: While they might sometimes rely on a sense of urgency, attacks are less likely to rely on this than regular phishing attacks. This is because a more sophisticated and believable pretext doesn’t need you to rush your decision-making as much to get you to perform the action the attacker wants.
- Important data: Spear phishing attacks are more likely to target people with lots of money or access to important information, because attackers won’t want to spend time crafting a tailored pretext for little reward.
What is the difference between spear phishing and whaling?
Whaling is a kind of spear phishing that targets high-ranking or high-earning individuals in an organization. Here are the most common differences between spear phishing and whaling:
- High-ranking target: Whaling always targets a high-ranking target in an organization. A general spear phishing attack, on the other hand, might not always target such individuals.
- High-ranking source: Because whaling attackers target high-ranking officials, they’re also more likely to pretend to be high-ranking officials themselves. High-ranking people are more likely to deal with other high-ranking people, especially concerning financial decisions, for example.
- Financial requests: Many whaling attacks will request that the high-ranking target take action of an explicitly financial nature, such as setting up a wire transfer for a new company product or service.
What is the difference between spear phishing and CEO phishing?
CEO phishing, or CEO fraud, is a kind of spear phishing where an attacker pretends to be the CEO of an organization to target employees or other high-ranking officials. Here are the main differences:
- High-ranking source: It should go without saying, but CEO fraud involves pretending to be the CEO of a company, which is a high-ranking official.
- Pressure from authority: Sometimes, the goal of CEO fraud is to get an employee to divulge information or give access to company accounts out of fear of authority. Putting pressure on employees can be effective because they might be afraid of being fired if they refuse.
- Financial requests: A CEO phishing attack might involve asking a finance department employee or a high-ranking official at a partner company to wire money to them directly. CEOs are more likely to be able to ask for such things under the premise that it’s for the company, and people are less likely to refuse if they think it’s the CEO asking.
How to identify spear phishing
While spear phishing is harder to spot than regular phishing, it’s not impossible to do so. Here are some telltale signs that the email or message you’re reading is a phishing attempt.
Asking for personal information
A spear phishing attack, as with any kind of phishing attack, will likely ask for your personal information. This might happen in the initial phishing message, or the message might direct you to a site that asks you for this information. Whatever the case, if you’re being asked to divulge any information, be wary.
Email attachments
One common strategy that spear phishing attackers employ is to include malware in their email attachments. This is because users are more likely to open email attachments than to follow links.
An attacker might, for example, pretend to be an employee in the accounting department at your workplace who is requesting that you look at an Excel spreadsheet they send you. If you download this attachment, it might infect your device and send your personal information back to the attacker.
Using a personal account
Another common strategy commonly employed by spear phishing scammers is to claim that they’re a boss or coworker emailing from a personal account. They say this to try to counter any suspicions you might have about why they’re not using their work email to contact you.
Requests from friends or family
Spear phishing attackers might be able to find out the name of one of your friends or relatives and use this to create their pretext. They might, for example, claim to be a friend or family member who is short on cash and ask for a bank transfer.
Pressure from authority
Spear phishing scams are some of the scams that most commonly employ the social engineering tactic of applying pressure from apparent authority. Some spear phishing attackers will pretend to be your boss or someone else in a position of authority and use this authority to try to get you to hand over personal information, visit a sketchy link, or download malware.
How to prevent spear phishing attacks
Spear phishing attacks can be prevented in the same way as regular phishing attacks. The main difference is that you need to be extra vigilant against spear phishing attacks because the pretext will be tailored specifically to you or people like you.
Check the sender’s details
It’s a good practice to get in the habit of checking the sender’s details on any communication you receive, whether that’s by email, text message, social media DMs, or any other means. Scammers will often use email addresses that look legitimate at a glance but, on closer inspection, aren’t quite right.
Don’t click links or download attachments
While it would be difficult to never click links or download attachments again, it’s a good rule of thumb not to do so when you can avoid it. At the very least, only visit links and download attachments from verified senders that you’re sure you trust and whose contact details you’ve checked.
Use AI email filtering
While traditional email filtering might not have been able to catch spear phishing attempts as easily as regular phishing attempts, AI might be able to do so. Some paid services can add a layer of AI-enhanced filtering to your email inbox, which could help filter out spear phishing attempts.
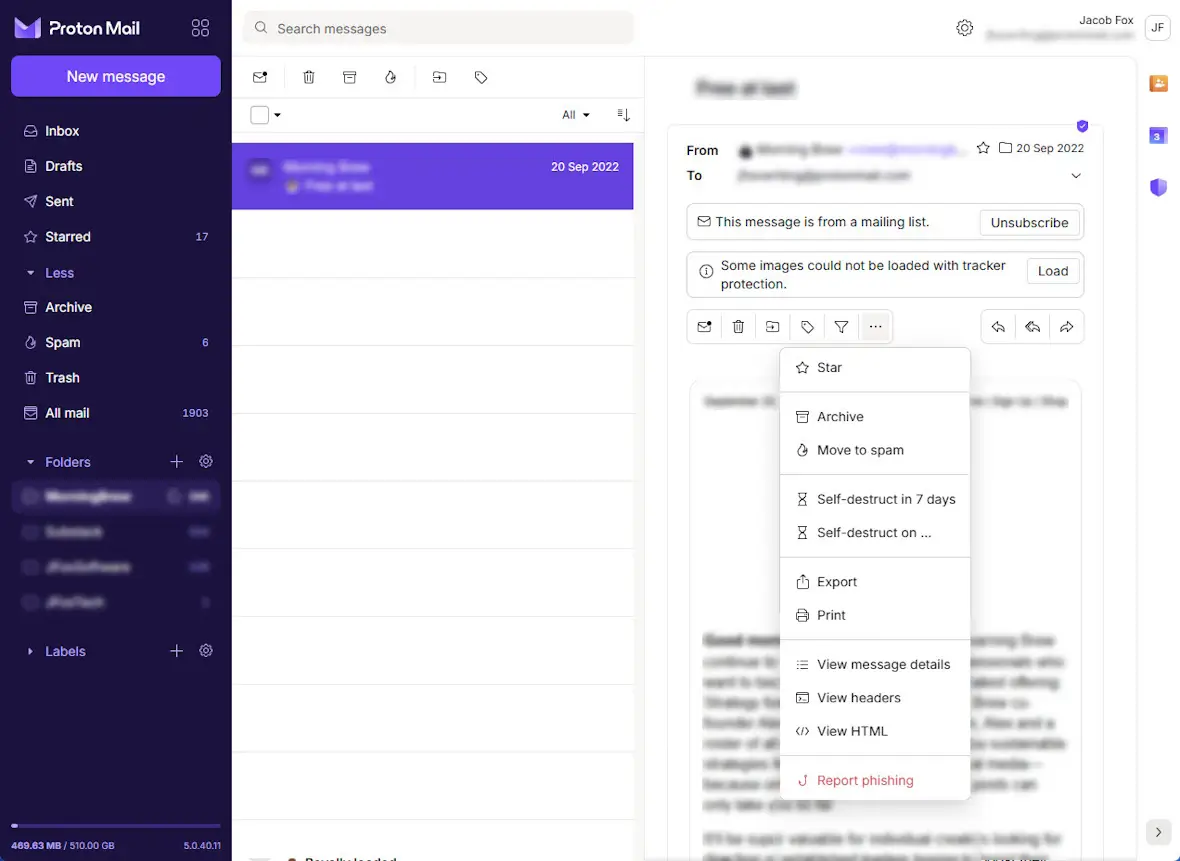
Report phishing emails
One of the best things you can do to prevent spear phishing is to report it when you see it. If you get an email that you think is a spear phishing attempt, report it. You can usually do this by clicking the 3 dots at the top of an email and selecting Report. Doing this helps teach your email filter what to block automatically in the future.
Use official contact details
If you’ve received a communication from someone and you’re not sure whether it’s legitimate or a spear phishing attempt, open up a new communication channel using official contact details. For example, if it’s someone saying they’re a bank employee, contact the bank via their official support email address.
Spear phishing attacks can be particularly tricky scams to spot. This is because they attempt to trick you into divulging your personal information by researching you and coming up with a sophisticated, believable pretext.
Fortunately, there are actions you can take to avoid being scammed by spear phishing attempts. Avoid clicking links or downloading attachments from anyone you’re not sure is legitimate, be wary of any message from someone claiming to be in a position of authority over you, and always check the sender information on emails and messages you receive.







