While ransomware and spyware constantly make international news, another major player in the cybercriminal malware world is rapidly gaining popularity and working in the shadows. Stealer attacks are booming and increasing dramatically. The average user today is more likely to fall victim to an infostealer than they are to be affected by ransomware.
Moonlock spoke to Victor Kubashok, Senior Malware Research Engineer at Moonlock Lab, Josh Amishav, Founder and CEO at Breachsense, Joseph Harisson, CEO of IT Companies Network, and Amit Malik, Head of Threat Intelligence and Research at Uptycs, to understand what is driving the infostealware trend, how the malware works, and what users need to know today.
The rise of infostealers: When data is gold
As our lives become more digital, the attack surface expands. The value of data has skyrocketed, making it an irresistible temptation for criminals. A recent Uptycs report reveals that infostealer attacks, targeting all operating systems, including macOS, have more than doubled in Q1 2023 compared to last year.
“Infostealers provide direct access to users’ private and sensitive data stored on browsers and systems, such as bank, crypto, and social media credentials, and private/portal information,” Amit Malik of Uptycs said.
“The increase in the number of stealers is driven by the possibility of getting lucrative data rather quickly, and the imperfection of data protection allows it to be quickly implemented,” Kubashok added.
Amishav agreed and added that it is “really simple economics.”
“Stealing personal information is extremely lucrative,” Amishav said, “whether it’s to make unauthorized purchases or break into a company’s network. No sense in developing a sophisticated computer exploit when malicious users can leverage infostealer logs to steal their victim’s credentials.”
“It’s really simple economics. Stealing personal information is extremely lucrative.
Josh Amishav, Breachsense
On the other hand, Harisson said that other factors, besides financial motivations, are driving the infostealer trend upwards. These factors include the ease with which infostealers can be developed and deployed. And the growth of the dark web provides a safe haven for infostealers to operate and sell stolen data.
“Infostealers are relatively easy to develop and deploy, making them accessible to a wider range of criminals,” Harisson said.
You would never guess how infostealers breach your device
Infostealers breach systems and operate in the background without the user’s knowledge. They often persist within systems for a long time, stealing personal data, financial information, and more.
Many cybersecurity experts assure that most of these attacks begin with the classical breaching techniques such as stolen credentials, phishing, MFA fatigue attacks — wearing out a victim by continuously sending him MFA push notifications — or brute force attacks.
However, the experts interviewed for this report warned that there are other techniques heavily used to breach devices. Much like trojans, infostealers can impersonate legitimate software and even operating systems.
“For example, the AMOS stealer can show a fake prompt (dialog box disguised as a system process) in which the user would enter their password,” Kubashok explained. “Thus, the malware can gain access to the system and create persistence.”
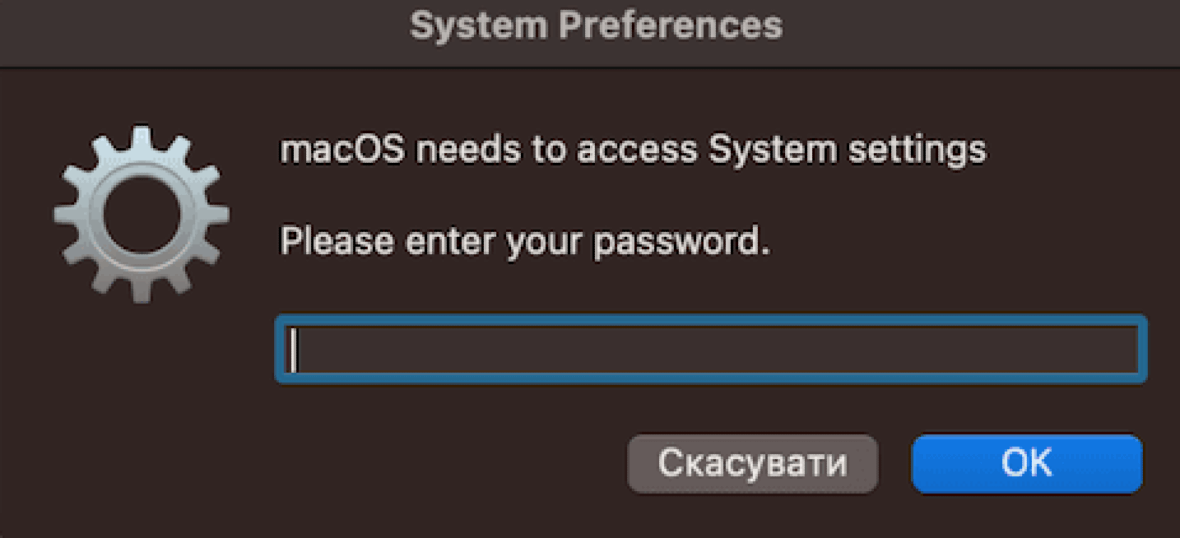
“Also, malicious software can use the OS or program vulnerabilities to obtain higher-level access to the system,” Kubashok added.
Amishav assures that stealer cyber criminals are using sniffing attacks. “The infostealer malware sniffs all of their victim’s computer traffic before it gets encrypted,” Amishav said. “This gives the attackers the plaintext credentials as well as the URL that the victim was authenticating to.”
Amishav explains that if the victim is using MFA, the malware sniffer will steal the session token as well. “Attackers can exploit the session token to bypass both the login as well as the MFA requirement.”
Malik also warns that infostealers can masquerade as well-known legitimate websites like TeamViewer and AnyDesk.
Understanding a persistent malware that evades detection
Cybersecurity software and skills have become highly advanced. So, how can infostealers, a type of malware that remains hidden in a system for long periods of time, go undetected?
We wanted to know what makes infostealers special in this way. As Kubashok explained, there is a large amount of software on the market that can detect malicious code based on patterns and various behavioral signs.
“AI-based approaches are used, too (to detect malware),” said Kubashok. “But in turn, malware developers use various techniques and tactics to avoid detection by antivirus products. Oftentimes, they are successful.”
Malware developers use various techniques and tactics to avoid detection by antivirus products. Oftentimes, they are successful.
Victor Kubashok, Moonlock Lab
Criminals use infostealers because they can change malware code signatures that antimalware security software uses to compare them to verified and known safe signatures, Kubashok added.
Criminals living off the land
Techniques like Living off The Land (LoTL) are used to make infostealers work in stealth mode.
“The trend over the last few years has been to rely on living off the land (LoTL) techniques,” Amishav added. “This is where malware relies on already installed legitimate software to carry out their malicious activities.”
Amishav also highlighted another common technique — fileless attacks.
“By using registry modifications and memory injection, malware that don’t use files are better at evading traditional antivirus detection,” Amishav said.
Chameleon polymorphic code, encryption, and zero-day exploits
Harisson jumped in and added that the use of polymorphic code, which changes its appearance each time it is executed, makes it difficult for antimalware solutions to detect infostealers. Encryption and zero-day exploits are also used by bad actors to keep their malware hidden.
“Infostealers can encrypt their code and data, and leverage zero-day vulnerabilities in software that are unknown to the vendor, breaching systems and installing infostealers without being detected,” Harisson said.
Techniques that infostealers use to breach and remain hidden include:
- Fileless malware: Fileless malware exists only in memory, making it difficult for antimalware solutions to detect.
- Cloud-based infrastructure: Infostealers can be hosted on cloud-based infrastructure, which makes them more difficult to track down and remove.
- Notarization of the application: This involves digitally signing the application with a trusted certificate, making it appear as if the application is from a legitimate source. This may help to bypass security measures.
- Built-in system tools: Infostealers can use built-in system tools to hide their presence. For example, they can hide files in obscure locations or use registry modifications to disable security features.
- Packers: Packers are tools that can be used to compress and obfuscate code. This can make it more difficult for security software to detect and analyze the infostealer.

Malik from Uptycs added that infostealer attackers are sharing stolen data via Telegram or Discord, compromising websites frequented by the target audience to infect visitors (watering hole attacks), and searching for and mapping wireless networks (wardriving). They will also commonly downgrade a secure HTTPS connection to an unencrypted HTTP connection, allowing for potential data interception.
The dark web: The stealer’s paradise
Cybercriminal operations and criminal groups have taken refuge on the dark web for decades. But in the past few years, leading cybercriminal groups have reinvented themselves and used the dark web to sell malware, ready-to-use malware kits, stolen credentials, and even support for hackers.
This malware-industrialization trend is not just fueling an illegal trillion-dollar economy. It also gives access to the tools needed to carry out cyber attacks, no matter where they are.
“Malware as a service (MaaS) simply lowers the bar for inexperienced attackers who want to deploy infostealers,” Amishav said. “The dark web serves as a marketplace for infostealers, offering a vast array of malicious tools, stolen data, as well as tutorials. When combined, this essentially enables attackers to launch sophisticated attacks with minimal technical knowledge.”
“When we talk about MaaS in the context of the Dark Web, we need to understand that there are numerous platforms that offer this service,” Kubashok said. “While most of them are related to Windows, there are also cases when malware developers offer malicious code for macOS, and those are usually stealers.”
Kubashok warned that MaaS Mac-specific malware, such as MacStealer and ShadowVault, pose a threat to Mac users. “These stealers can collect personal information from infected devices and transmit it to remote servers,” Kubashok said. “For example, MacStealer uses the Telegram messenger as a C2 (command and control) server to monitor infected devices and aggregate stolen data. Such elevation makes it difficult to detect.”
Taking it all: The data that infostealer attackers are after
The list of types of data that infostealers target is long. As Kubashok explains, this data includes:
- System information
- Login data (logins, passwords, cookies) for accessing web resources, usually stored in the web browser
- Crypto wallets
- Keychain database
- Text, graphics, PDF files, Microsoft Office documents, and others
- Browser history
- Credit card data
- Databases of messengers
Amishav adds to the list a wide range of Personal Identification Information (PII) data. That includes names, addresses, social security numbers, bank details, and session tokens.
Each attack is different and may go after different data.
“Depending on the files present on the victim’s machine, sensitive corporate files, medical records, and legal documents can be stolen as well,” Amishav said.
It all comes down to what the attacker is after. Harisson said they might even steal intellectual property, trade secrets, business plans, or customer lists.
There is no silver bullet, but the shotgun defense will work
There is no single, all-encompassing solution to the threat posed by infostealers. However, a comprehensive approach that combines multiple layers of defense can significantly reduce the risk of falling prey to these malicious actors. This “shotgun defense” strategy involves using a variety of security measures that are easy to use and known to virtually everyone.
Just as a shotgun’s multiple pellets spread out and increase the chances of hitting a target, a layered defense strategy will create multiple obstacles for infostealers to overcome. This makes it more difficult for attackers to breach your system and steal your data.
Strategies for staying safe from infostealers
To keep yourself safe from infostealers, combine the following:
- Be cautious with online activity: Avoid clicking on suspicious links or attachments in emails, messages, or online advertisements. Only visit reputable websites, and only download software from trusted sources.
- Secure your browser: Most infostealers go after your browser data. That’s where passwords, accounts, and a wide range of other data are stored. Set your browser privacy and security to the highest level and avoid password autocomplete features.
- Use strong passwords and enable multi-factor authentication (MFA): Use strong and unique passwords for all online accounts and enable MFA wherever possible. MFA adds an extra layer of security by requiring additional verification, such as a code sent to your phone or email, before allowing access. Biometric is considered the best MFA to use.
- Keep software and operating systems up to date: Regularly update software, including operating systems, web browsers, and applications. Updates often include security patches that fix vulnerabilities that cybercriminals can exploit to install infostealers.
- Install and use only reputable antimalware software: Antimalware software can help detect and remove infostealer and other malware. Choose a reputable security product and keep it updated.
- Stay off public Wi-Fi networks when possible: Avoid accessing sensitive information, conducting online banking, or shopping when using public Wi-Fi networks, as they may not be secure. If necessary, use a VPN (Virtual Private Network) to encrypt your internet traffic.
- Back up your data regularly: Regularly back up your important data to an external hard drive or cloud storage service. This ensures that you have a copy of your data in case it is lost or corrupted due to an infostealer attack.
- Educate yourself and be aware: Make sure you are updated on the latest trends, malware, and attacks. Learn how these attacks work and what you need to do to stay secure. This includes knowing how to recognize phishing scams and other types of cons and frauds.
While no approach is perfect or fail-proof, by combining multiple layers of security measures, you can significantly reduce the risk of data breaches and costly consequences.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






