The recent layoff wave in the IT industry has given rise to numerous employment scams, and the Zscaler Threatlabz team has recently discovered multiple fake job portals that masquerade as legitimate websites. These fake sites steal personal information from potential job seekers to use in various social engineering attacks and to extort money from them.
Attack methodology
In these attacks, hackers disguise themselves as recruiters from specific companies primarily located in the United States and Canada. To convince candidates of the legitimacy of their job announcements, they borrow job descriptions from real websites like SmartRecruiters and LinkedIn and republish them on their own domains.
Hackers commonly use cheap domain name providers such as Namecheap to register their malicious domain names. The attackers try to impersonate authentic domain names by using the real company’s name ending with some variation such as .online, .work, or .live.
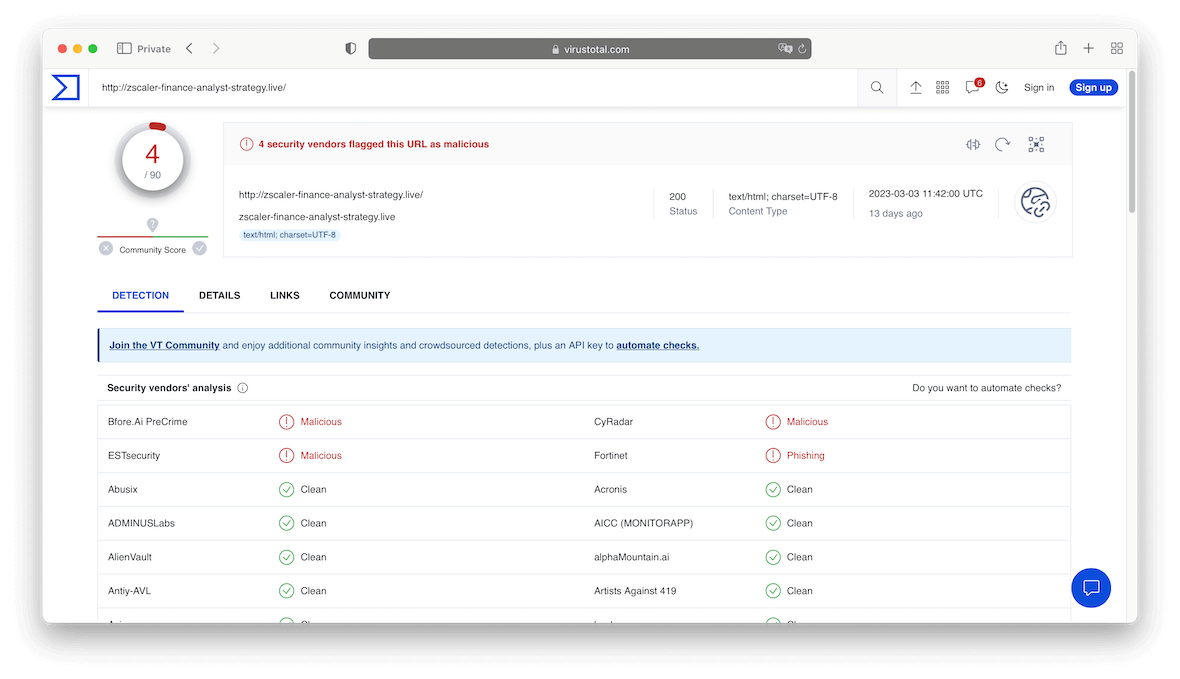
Typical recruiter attack scenario
The typical attack scenario, as discovered by Zscaler Threatlabz researchers, works as follows:
- Attackers impersonate a recruiter on LinkedIn. They use a real job announcement on an employment website and slightly modify the job requirements to attract more victims.
- To apply for this job, the candidate needs to fill out an online questionnaire, providing information about their work experience, expected compensation, and personal information.
- The questionnaire requests that the applicant provide a government ID to verify their identity, such as a driving license, passport, national ID, or residence permit.
- After the questionnaire is completed, a message will display informing the applicant that the company will contact them via email or text message within three business days.
- The scammers then email the victim to schedule a fake interview via Skype or other internet chat applications.
- To further convince the victim, the Skype account used to contact the victim uses a personal photo of one of the actual recruiters.
- After an interview with the fake recruiter, a job offer is provided.
- The final step of the fake onboarding process will require that the candidate pay for the IT hardware needed for remote work or pay fees for training. Attackers may also request candidate payment information, such as banking information and credit card details to transfer their salary.
How can you avoid such attacks?
As a job seeker, you should follow the precautions below to ensure that you don’t fall victim to this employment scam:
- Only apply to job postings on company websites or reputable job websites.
- Do not share sensitive information on job websites with strange domain names or through Google forms.
- Beware of supposed recruiters who use email addresses or phone numbers that do not belong to the company you are applying to.
- If you receive a job offer via email from a particular company, check that the email was sent from the company’s official domain name.
- Do not make any payments when negotiating a job offer. Legitimate companies do not require that candidates pay them during the onboarding process. Employment agencies typically take compensation from the hiring companies, not from job seekers.
- Do not open email attachments sent by job recruiters if they are not sent from a real company domain name.
- Make sure your operating system and installed applications are all up to date.
- Install a reputable antimalware program like CleanMyMac X, powered by Moonlock Engine, to defend your system against malicious programs.
Hackers are always pursuing new techniques to target unsuspecting users, steal their personal information, and use such information to execute social engineering attacks or extort money. So exercise caution while interacting with new contacts online, even if they pose as recruiters for legitimate companies.