Some cyberattacks are simple to understand, with the motives behind them usually being financial or nation-state driven. However, other malicious attacks are more tricky to unravel.
Security researchers recently identified one such attack in the wild. Analysis of the campaign and of the malware it spreads has left researchers with more questions than answers.
Proofpoint discovers Voldemort attacks in the wild
On August 29, Proofpoint researchers reported an unusual campaign that used a novel attack chain to distribute malware.
The malware, named “Voldemort” by the unknown threat actor behind it, is unique and strange. Its attribution is a mystery. And while the threat actor is impersonating government tax agencies via phishing emails, they are not after money.
The malware uses tactics that cybercriminals leverage in financial attacks, but their endgame is cyber espionage.
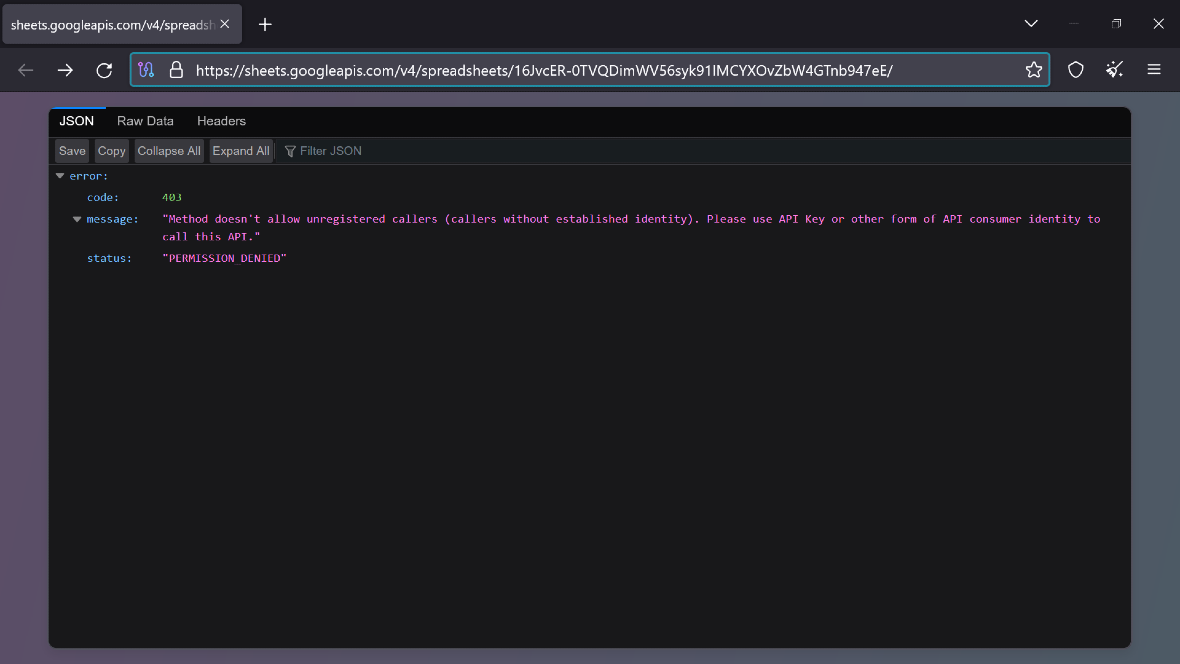
Technical details also reveal that this threat actor is using Google Sheets commands and the Google Sheets infrastructure (Google Cloud) to spy on users and communicate back and forth with the command and control (C2) server controlled by attackers.
Voldemort attackers sent 20,000 malicious emails to over 70 global organizations
This new malicious campaign, which has already sent out hundreds of thousands of emails, is operating globally and targeting victims in organizations across the United States, Europe, and Asia.
While there is practically no evidence available to safely claim who or what is behind this operation, it is evident that there is a coordinated, intentional effort to spy on specific users.
Proofpoint identified over 20,000 email messages sent by this threat actor since August 5, last month. The emails targeted more than 70 organizations worldwide.
The first stage of attack in this campaign uses email phishing. The attackers impersonate tax authorities from different governments, and the emails urge potential victims to update their tax information and download malicious PDF documents.
So far, victims of this attack have received fake emails that impersonate:
- The US Internal Revenue Service
- The UK HM Revenue & Customs
- France’s General Directorate of Public Finances
- Germany’s Federal Central Tax Office
- Italy’s Revenue Agency
- India’s Income Tax Department
- Japan’s National Tax Agency
Each email that attackers sent was written in the language of the authority it impersonated. This implies the use of AI or a team capable of communicating in different languages.
Proofpoint analysts also discovered that the attackers specifically targeted individuals based on their personal country of residence, not the location of their employer or any information gleaned from their email addresses.
For instance, some employees in a European company received emails pretending to be from the IRS because their public profiles indicated that they lived in the United States. In a few instances, the attackers mistakenly targeted individuals with common names due to confusion with more prominent figures.
50% of all Voldemort attacks target the insurance industry
Regarding industries, Voldemort targets almost every sector, from healthcare to government, media, hospitality, and aerospace. The most hit industry, however, is insurance — accounting for 50% of all attacks.
Why a cyber espionage actor would target insurance organizations around the world is also a question that has not yet been answered.
Breaking down the Voldemort chain of attack
Sending out phishing emails and impersonating government tax agencies is nothing new. But it’s clear that scammers did not design this malware. It can find information, extract it, and send it to the cybercriminals. Let’s look at how it does that.
If a victim opens the malicious attachment sent via email, they will immediately see a web browser explorer popup and be directed to a customized landing page hosted on InfinityFree. The landing page then automatically presents the victim with a “View Document” button.
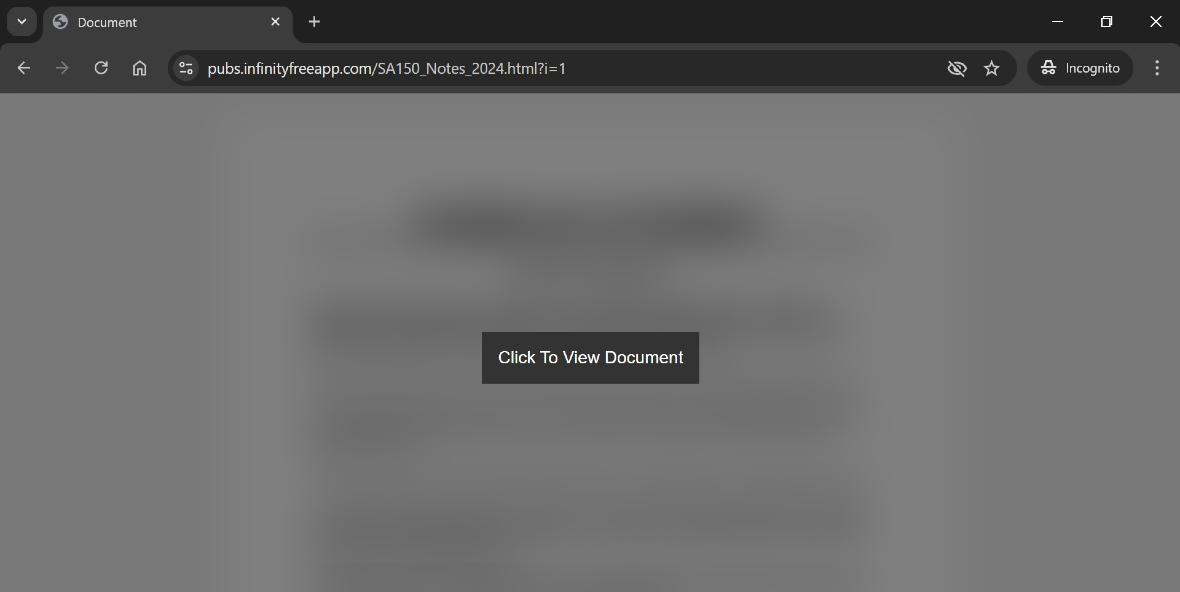
While users decide whether to click the button or not, the landing page is already working in the background, extracting the victim’s computer data, such as operating system data, browser in use, and other information.
If the code detects that the victim is running Windows OS, it will continue with the chain of attack. If it detects that it is running macOS or other operating systems, it redirects users to an empty Google Drive folder. This could mean that a macOS version of the malware is in development.
Once the user downloads the PDF, the fireworks kick in. The malware will execute several hidden commands, create and delete files, and eventually trick the user into believing the PDF has been downloaded and can be opened.
By the time the victim opens the PDF, the computer is already breached, and PowerShell Python scripts are running to get more information, including the computer’s name, Windows version information, and CPU information. The malware extracts information that it will later use to establish communication between the breached computer and the C2 server control.
“Voldemort is a backdoor with capabilities for information gathering and can load additional payloads,” Proofpoint said.
Why Voldemort abuses Google Sheets and Google’s infrastructure
The Voldemort malware’s use of Google Sheets for malicious activities is a testament to the creativity and adaptability of cybercriminals. While unconventional, this approach offers several advantages for attackers.
The ubiquity of Google Sheets, a widely used cloud-based application, means it is accessible from anywhere with an internet connection, hindering tracking and blocking efforts. Its legitimate appearance allows attackers to blend in and avoid detection, while its robust security measures can challenge defenders in intercepting or disrupting communications.
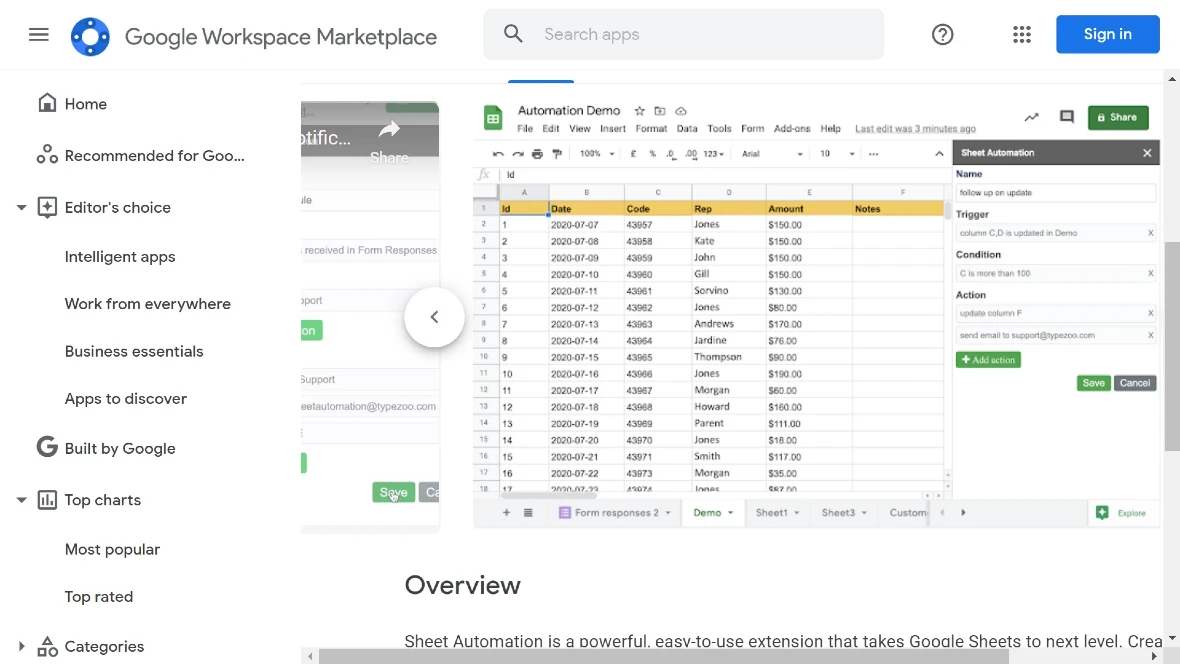
Moreover, Google Sheets’ customizable functionality enables attackers to tailor commands and responses for their specific malicious activities. This innovative use of a familiar tool showcases the ever-evolving tactics employed by cybercriminals to carry out their malicious campaigns.
While it’s very uncommon to see malware using Google Sheets in this manner, as technology evolves, so too do the methods used by attackers.
Who is behind the “Frankensteinian” Voldemort?
This attack has so many different pieces and stages stitched together in a bizarre and unique way that Proofpoint described it as a “Frankensteinian amalgamation of clever and sophisticated capabilities, paired with very basic techniques and functionalities.”
The use of email phishing, tax authorities impersonation, and backdoor/payload capabilities of this campaign are undoubtedly advanced and impressive. But the use of Google Sheets is a never-seen-before mystery.
The threat actors behind this campaign are undoubtedly resourceful and tech-savvy. Additionally, the chain of attack has separate stages, and the malware itself seems to have been pieced together to fit the chain. This suggests that several coders or threat actors worked together on this project.
Finally, it is likely that this is a nation-state campaign, as cybercriminals looking for financial gains or hacktivists seeking to send a political message do not run cyber espionage campaigns.
If we look at the countries targeted, we see that they are part of the Western alliance. This could mean that bad actors are working for Russia, China, North Korea, Iran, or other countries engaged in geopolitical tensions with the West.
How to protect yourself against these types of threats
This new malware may be unique in its method of stealing information. However, it still spreads via phishing emails, which means it depends on users clicking a link — or, in this case, a “View Document” button — as well as opening malicious attachments. Therefore, users do not have to be experts in malware or Google Sheets in order to protect themselves.
To protect themselves against this attack and similar ones, organizations should implement the following strategies:
- Robust email security: Employ advanced email security solutions with features like spam filtering, phishing detection, and sandboxing to prevent malicious emails from reaching employees.
- Employee training: Educate employees on phishing tactics and the importance of verifying the authenticity of emails before clicking on links or opening attachments.
- Endpoint protection: Deploy comprehensive endpoint protection solutions that can detect and block malicious software, including malware that leverages Google Sheets for command and control.
- Threat intelligence: Stay informed about emerging threats and trends by subscribing to threat intelligence feeds and participating in industry forums.
- Regular updates: Ensure that all software and operating systems are kept up-to-date. Download the latest security patches to address vulnerabilities that attackers could exploit.
- Network segmentation: Implement network segmentation to limit the spread of malware within the organization in case of a successful attack.
Conclusion
The Voldemort malware campaign represents a significant threat to organizations worldwide due to its innovative approach and potential for widespread damage. This sophisticated threat actor, likely a nation-state, has targeted organizations in the US, Europe, and Asia, demonstrating its broad reach and potential for severe consequences.
The malware’s capabilities for information gathering and loading additional payloads pose a significant risk of sensitive data being compromised and exfiltrated. The use of a legitimate tool like Google Sheets for command and control can help attackers evade traditional security measures and delay detection.
As scary as these innovative and creative cybercriminal techniques are, users can still protect their data and devices by practicing good cybersecurity hygiene. Follow the steps listed above to secure your devices, and always keep an eye on the news to learn how criminals are adapting.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Google Sheets is a trademark of Google, Inc.






