A battle to dominate the world of crypto wallet drainers has been unfolding on the dark web. Throughout 2024, a handful of cyber criminal gangs that offer crypto drainers and phishing-as-a-service have proliferated. In this ongoing power struggle, $500 million worth of crypto has been stolen in 2024.
Through Telegram, Discord, and other social media platforms, phishing and wallet drainers lease out automated services or malware to operators who launch attacks. Illegal gains are then split between the developers and operators. This cybercriminal enterprise model allows the developers and distributors of the wallet drainers to escalate rapidly, with little exposure.
Cost of crypto drainer attacks increasing exponentially
The new report by ScamSniffer found that wallet drainer attacks caused about $494 million in losses in 2024, a staggering 67% increase compared to 2023. Wallet drainers are going for bigger scores, as the number of victims only increased by 3.7% while the losses escalated.
ScamSniffer identified 30 wallet drainer attacks that broke the $1 million mark. Attacks that stole over $1 million accounted for a total of $171 million, revealing a trend to target richer targets. The largest-volume single attack totaled $55.4 million.
Finding out who is behind the development of crypto wallet drainers is crucial, as most of these attacks were done using the malware of just a couple of leading drainer developers.
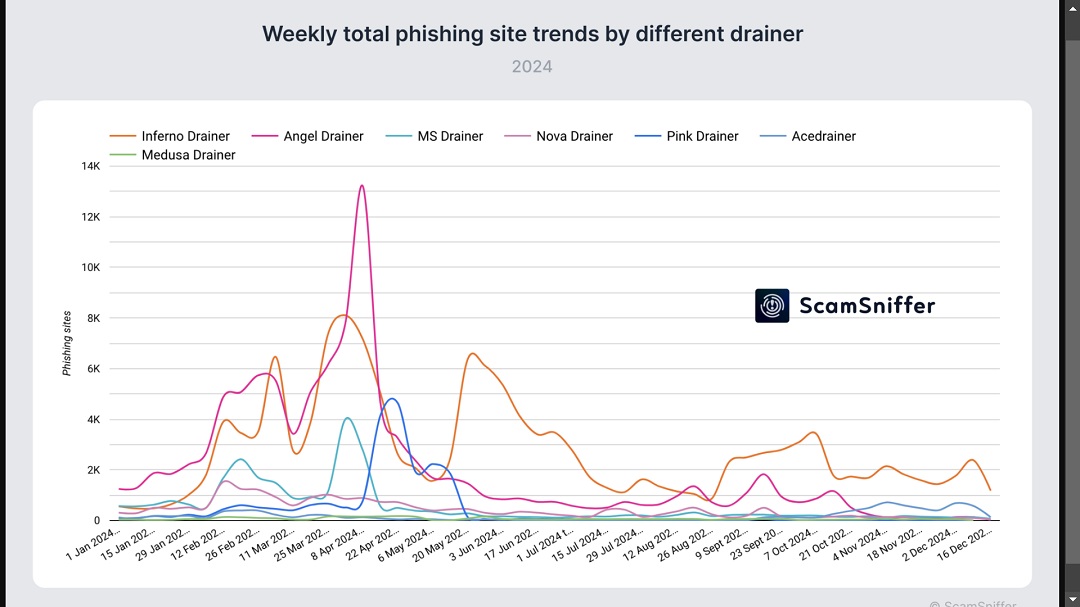
The criminal group Pink held 28% of the market in 2024 until it announced its exit in May — a common strategy in the wallet drainer world. Meanwhile, Inferno, another retired phishing and crypto wallet malware gang, made a strong comeback, dominating the year as the leading group with a market share ranging from 40 to 45% of all crypto hits in 2024.
Other gangs in the fight for global dominion over the wallet drainers’ dark market include Angel, Acedrainer, MS Drainer, and Nova Drainer.
Scary numbers: Why Ethereum is a prime target
Researchers from ScamSniffer said they identified 290,000 malicious domains that were used for phishing and deploying wallet stealers with lures such as fake free token drops by top drainer gangs.
More than 25,000 active phishing email addresses belonging to these criminal groups have also been flagged in 2024. Of the 30 large-scale crypto heists, Ethereum was the most impacted network, with losses totaling $152 million, accounting for 88.89%. Arbitrum followed with 2 cases totaling $3.55 million.
Ethereum’s dominance in the cryptocurrency landscape makes it a prime target for attackers. Its versatility, supporting a wide array of decentralized applications (dApps) beyond just currency, creates a rich ecosystem for malicious actors to exploit.
Smart contracts, while enabling innovative applications, also introduce vulnerabilities that can be leveraged by sophisticated drainers. Furthermore, Ethereum’s high transaction volume and the constant emergence of new projects and users within its ecosystem provide ample opportunities for attackers to infiltrate and execute their schemes.
How do wallet drainer attacks work?
Wallet drainers rely heavily on social engineering tactics — tricking victims into taking action — to launch successful attacks.
Criminal groups that offer wallet drainers on the dark web usually include support and automation for the entire process, making these attacks accessible to more cybercriminals without the need for highly technical know-how. Open-source versions of the wallet drainer malware also exist.
Attacks start out by redirecting victims to attacker-controlled domains (websites). Redirection of victims to these malicious domains is done via organic traffic that announces NFT or token airdrops. Attackers also hack official legitimate crypto projects on Discord and Twitter. By taking over these popular accounts, they can impersonate the project or brand and drive traffic through malicious links.
Additionally, wallet drainer attackers also abuse ad platforms like Google Search, Twitter, and Telegram advertising, where they create fake ads to direct traffic to their sites.
Once victims are on the malicious site, attackers will attempt to extract their credentials and connect their wallets to the drainer malware. This is usually done via fake CAPTCHA pages, hiding code and malware in “Claim your Airdrop!” buttons and other lures.
Once the malware gains access, the drainer will automatically target specific blockchain resources and drain accounts by transferring funds, tokens, and other valuable assets. The malware is automated, and its transactions and code are heavily obfuscated.
Another cat-and-mouse game for crypto tech security developers
As blockchain cybersecurity experts develop guardrails to mitigate these attacks, wallet drainer gangs develop new bypasses.
Recent innovations in bypass techniques include:
- Exploiting wallet normalization processes to initiate signatures that wallets can process but security detection layers might miss
- Using legitimate contracts and adding Cloudflare or fake CAPTCHA pages to prevent detection
- Attempting to bypass wallet blacklists through XSS vulnerabilities
- Deceiving wallet simulation results
ScamSnifffer said this back and forth between security patches and new bypasses “remains an ongoing cat-and-mouse game between attackers and defenders.”
The outlook for the future of crypto security is not a bright one, according to their report.
“As of 2024, known losses from phishing signature attacks have reached $790 million,” ScamSnifffer said.
As of 2024, known losses from phishing signature attacks have reached $790 million.
ScamSniffer
With attackers constantly shifting to new attack methods and Web3 and blockchain projects and assets continuing to grow, users face significant challenges in securing their wallets.
“Regardless of how attack methods evolve, continuous security awareness and building protective capabilities remain key to safeguarding assets,” ScamSnifffer said.

Simple but effective tips to secure your wallet
There is no need to reinvent the wheel to keep your crypto or NFTs safe. What follows is simple but highly effective advice. While the type of advice you will find below is given over and over again, it seems like cybersecurity specialists are preaching to the choir. Ultimately, if everyone followed these tips, these cyberattacks wouldn’t proliferate.
So, here we go again.
To keep your crypto wallets safe, use strong passwords, enable MFA, and keep your software up to date.
Be highly skeptical of any unsolicited messages (emails, DMs, etc.) offering free crypto, airdrops, or other enticing rewards. Never click on strange ads or links, and never download attachments from suspicious sources.
Additionally, stay alert for any notification you get to connect your wallet. Only connect your wallet to reputable and verified websites and applications, and consider using cold wallets.
Finally, if you currently hold over $1 million in blockchain assets, take special precautions, as you are part of a group being targeted exclusively.
Final thoughts
There are several noteworthy elements in the emerging wallet drainer malware criminal wave.
The malware itself is interesting, as well as rather low-weight and elegant. The way it can bypass chain security protocols is also creative. However, what stands out immediately is how this malware-as-a-service niche sector is beginning to closely resemble a ransomware-as-a-service sector.
Evidently, as the volume of stolen crypto assets per attack increases, operators and distributors alike are engaging in the heavy lifting of spear-phishing.
For cybercriminals motivated exclusively by financial reasons, crypto wallet drainers are a shortcut to the grand prize. There’s no need to exfiltrate data, breach accounts, or run complex malware. All it takes is automatic transfers via browser phishing-trojan techniques, and they are ready to go.