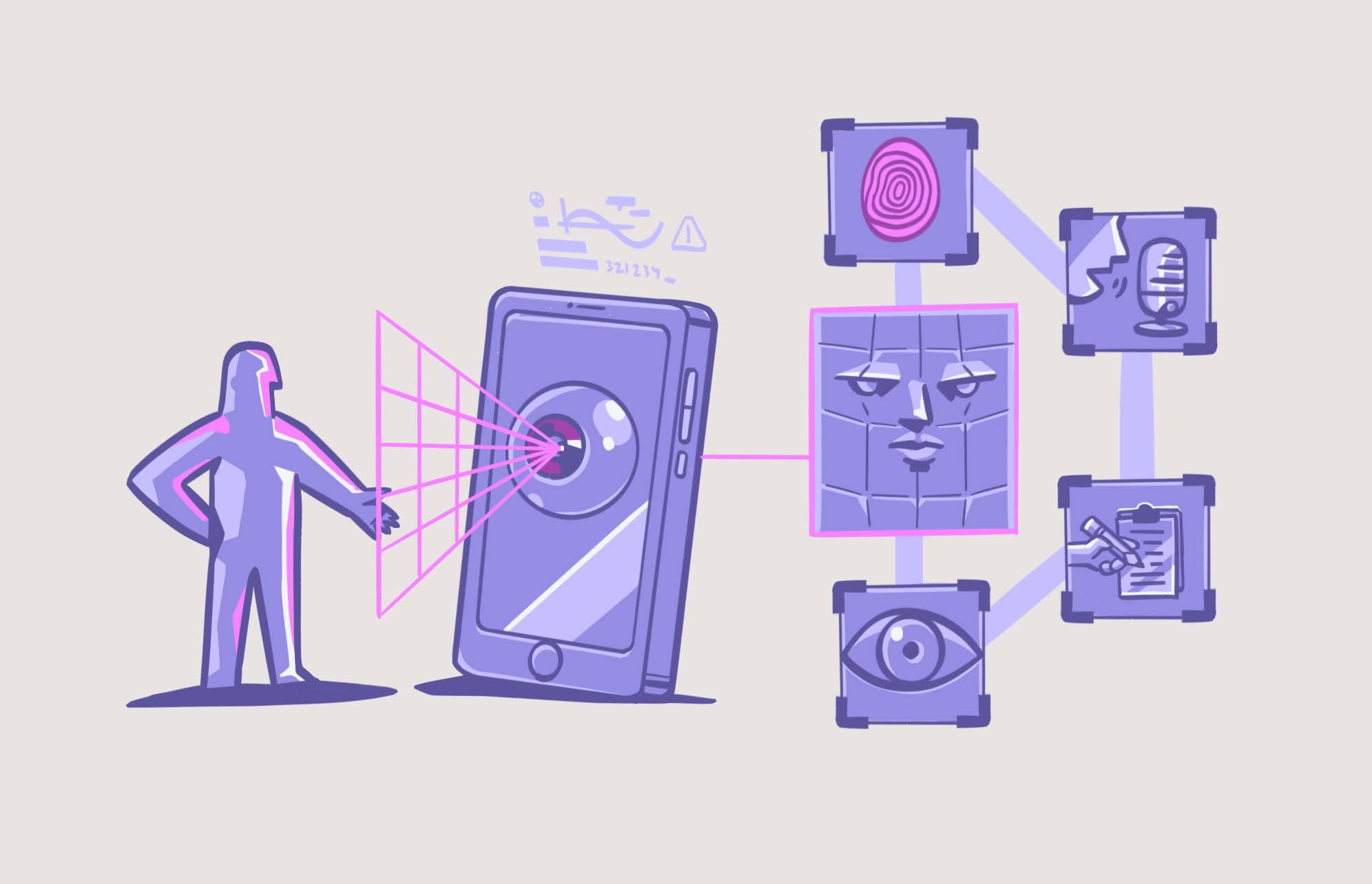
Chances are you use biometrics every day to unlock your devices without giving the process much thought. The technology is the latest advancement in security and the protection of devices against unwanted intrusion. Many of us know very little about how biometrics work and how secure our biometric data really is.
This guide will explain what biometrics are, how they work to keep you safe and secure, the different types, and any security concerns you might have.
What is biometrics?

Despite the fact that many of us use biometrics daily, we may still wonder, “What does biometrics mean?”
So, what is biometric data? Biometric data is the information gathered and stored that identifies you specifically. More specifically, biometrics refers to the biological measurements of unique physical characteristics used to identify individuals.
Is your Mac protected with Touch ID?
Fingerprints are a good example of biometrics. Another may be a retina scan or Face ID. But believe it or not, we all have dozens of other unique characteristics that could be used to identify us specifically. Other examples are how we walk, the shape and size of our ears, facial expressions, and our voice print.
How are biometrics and fingerprints used in security?
Biometrics are used frequently in security to secure buildings, mobile devices, specific offices, and other things. Biometrics allows security professionals to control access, identify users, and authenticate the use of resources.
Your iPhone may use a fingerprint scanner or the camera for Face ID when logging in to apps or unlocking your device. Biometrics are much more secure than using a username/password combination.
The only problem with this is that biometric data is very valuable, and if yours is stolen in a data breach, hackers could use it to steal your identity and access your accounts.

What is biometric authentication, and how secure is it?
Many of us use biometric identification to unlock our Macs, iPhones, and other devices. First, we set up biometric authentication when we purchase a new device, which stores biometric data about our specific characteristics. Then, anytime we try to unlock the device, it references the stored biometric data.
The use of biometrics is widespread across the globe, and many companies are using it to secure facilities. Some of the most common types of biometric security used today are:
- Facial recognition
- Fingerprint scanning
- Iris or retina scans
- Voice recognition
- Hand/vein recognition
- Heart rate sensors
Types of biometric data
Depending on the kind of hardware, software, or biometric application, security professionals may use various types of biometric data. The top three types used are biological, physical, and behavioral.
Typically, a sensor (usually hardware) reads your biometrics, and the computer processor inputs and evaluates and saves the data. The software then compares your biometrics with the saved data to see if they match.
Some advanced companies pair biometric data with a unique token, making it harder to hack and more secure.

Behavioral biometrics
Behavioral biometrics include traits about you that indicate your behavior. A biometric scan might reveal the specific way you have of walking or talking. Rather than relying on physical traits, behavioral biometrics are much more secure because they are nuanced to evaluate specific ways that people behave. Some examples include the following.
Kinesthetics
Kinesthetics refers to a person’s body posture, position, and weight distribution. It also includes features like gait, stride, and pace when walking.
Voice patterns
Voice recognition software detects distinct sound variations in a person’s voice.
Device-based gestures
Device-based biometrics evaluates how someone types on a keyboard or uses the cursor/mouse.
Some of the applications of behavioral biometrics include:
- E-commerce
- Banking
- Access control of devices, facilities, and other resources
Behavioral biometrics are incredibly secure because they are difficult to duplicate or imitate.
Physiological biometric data
Unlike behavioral biometrics, physiological biometrics are based on a person’s fingerprints, facial structure, hand or vein patterns, and eyes.
Physiological biometric data is used widely in the consumer technology industry. Apple uses users’ physiological biometric data to unlock devices. If you have an older iPhone, you probably use a fingerprint scanner, while newer iPhones use Face ID.
Physiological biometrics are easy to use, always available, and difficult to hack. Because of user convenience, many companies that produce technology are incorporating it into their devices.
Biometric security concerns: How safe is your data?
Biometrics do offer better security than usernames and passwords, but nothing in this world is 100% safe and secure. If stolen, your biometric data could be used to access your entire digital life.
Some of the common concerns about biometric safety include:
- Hacking: Although it takes a sophisticated hacker to use them, your biometrics are an attractive target. The more places you use biometrics, the more exposed you are to theft.
- Duplication: Unfortunately, some biometric data is easy to duplicate. Fingerprints, for example, can be lifted off a common drinking glass. Cybercriminals are quickly learning how to steal this data and use it for personal gain.
- Risk: Your biometric characteristics are etched in stone, and you cannot change them as easily as you can change a password, making it risky if they are stolen.
- Complacency: Users could be careless when using biometrics and expose themselves to bad actors.
- Privacy: Many devices, including smart home screens and other electronics, collect biometric data like your voice. It makes you wonder how private your details are and what companies are doing with all this data.
- Cloning: Hackers have found ways to duplicate fingerprints and even fool facial recognition scanners.
- Human error: This is another factor that makes biometrics vulnerable. People make mistakes. They rush things and don’t always remember to follow cybersecurity best practices.
Although biometrics offers users a secure, convenient, and high-tech way to access devices and resources, this doesn’t come without some risks. Be careful with whom you choose to share your biometrics.
While opting in for these features on a device like your iPhone is probably a good idea, be cautious when dealing with companies you aren’t as familiar with. You never know how they are using your data or with whom they are sharing it. For added protection, always turn on two-factor authentication so that even if one authentication method is compromised, your data will remain protected by another layer of security.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iPhone is a trademark of Apple Inc.