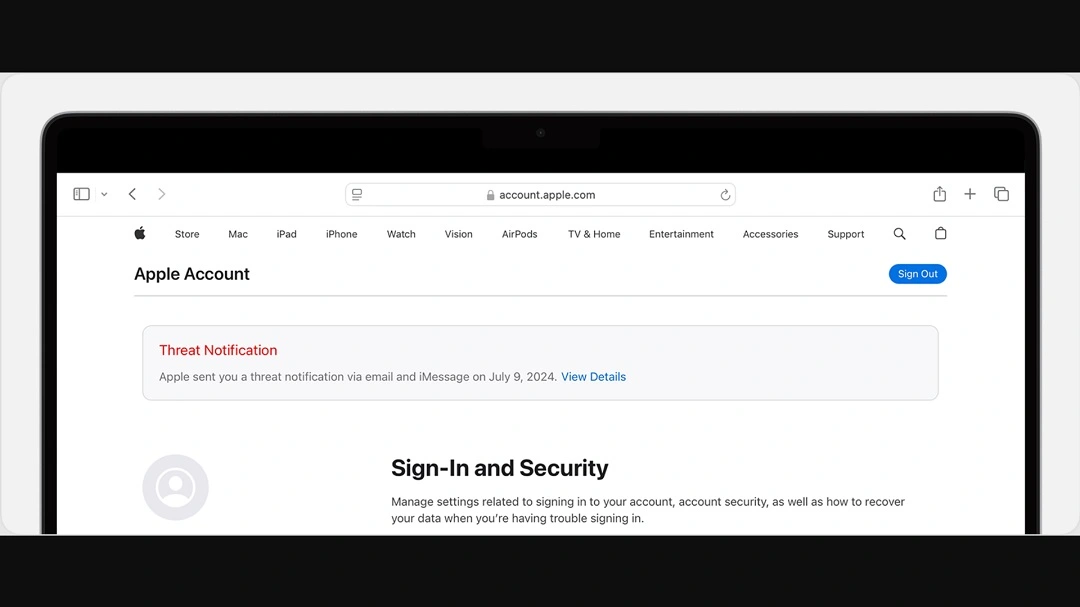
Apple and Google have released fresh new warnings in multiple countries about spyware impacting users. Several hundred accounts in over 80 countries received warning notifications informing them that they were being targeted with the new zero-click Predator spyware developed by the surveillance company Intellexa.
In this report, we look at the new Predator spyware, what it can do, how it breaches devices, who it targets, and why this news matters to all Mac users.
Users in over 80 countries targeted by spyware Predator
On December 6, Reuters reported that Apple and Google had sent a new round of threat notifications to users in over 80 countries. Warnings like these, which Apple issues several times a year, are not uncommon. They are sent when the company identifies that customers are being targeted by sophisticated surveillance malware.
Block any spyware from infecting your Mac
Apple warnings were issued on December 2. The company provided little information on the event. However, Google’s warning came with a detailed announcement.
Google Threat Group said that the spyware in this round of warnings was developed by the company Intellexa, a cyber-intelligence company that has been sanctioned by the United States government and was “evading restrictions and thriving.” Spyware developers operate in legal “gray zones” in several parts of the world, developing surveillance software products that are later leased or sold to customers, who may use them for sinister purposes.
Threat notifications are “often the first step in a string of investigations and discoveries that can lead to real accountability around spyware abuses,” said John Scott-Railton, a researcher with the Canadian digital watchdog group Citizen Lab, Reuters reported.
Why should the average end user care about sophisticated spyware?
Sophisticated malware like the new Predator spyware does not usually impact the average end user. Often, it targets high-level organizations and individuals. Nevertheless, all Mac users should be aware of these threats. Here’s why.
First of all, when companies like Google or Apple identify spyware malware, not only do they issue warnings to those impacted, but they often later roll out security patches to address these new threats. These security patches aren’t just for those impacted by spyware. They are for everyone. So, a spyware campaign may end up changing an operating system to some degree.
Additionally, while software like Predator is highly advanced, other threat actors also use spyware that can access your files, data, camera, and microphone, in addition to logging everything you type on the keyboard.
By understanding how the most advanced spyware works, you can get a solid idea of what spyware can do. You can then do something about it, like taking actions to mitigate the risk.
It goes without saying that if you have received a warning from Google or Apple, follow the instructions provided in the email. You should also check out the official Apple Support page for spyware.
Meet the new Predator, zero-click spyware
Predator now uses a new attack vector, which makes it more dangerous than ever. Dubbed “Aladdin,” this feature allows those who deploy this spyware to breach multiple mobile operating systems with a zero-click technique.
Aladdin abuses platforms inthe commercial digital advertising ecosystem to distribute a unique malicious ad. Users only have to view the ad to be breached.
Google Threat Intelligence reported that the developer of Predator has become perhaps the most prolific spyware vendor, and their spyware product, Predator, exploits zero-day vulnerabilities to breach mobile browsers. Companies like Google, Apple, and others in the cybersecurity community actively patch such vulnerabilities, but according to Google, Predator just finds new vulnerabilities to exploit and adapts to security patches. However, you should still update your device with the latest security patches.
Analysis shows that Predator targets Safari vulnerabilities as well as iOS vulnerabilities. It does the same with Google Chrome.
What can Predator do?
According to leaked internal Intellexa documentation and screenshots made public by Amnesty International’s Security Lab and Recorded Futures, Predator can do a number of things once it has breached a device.
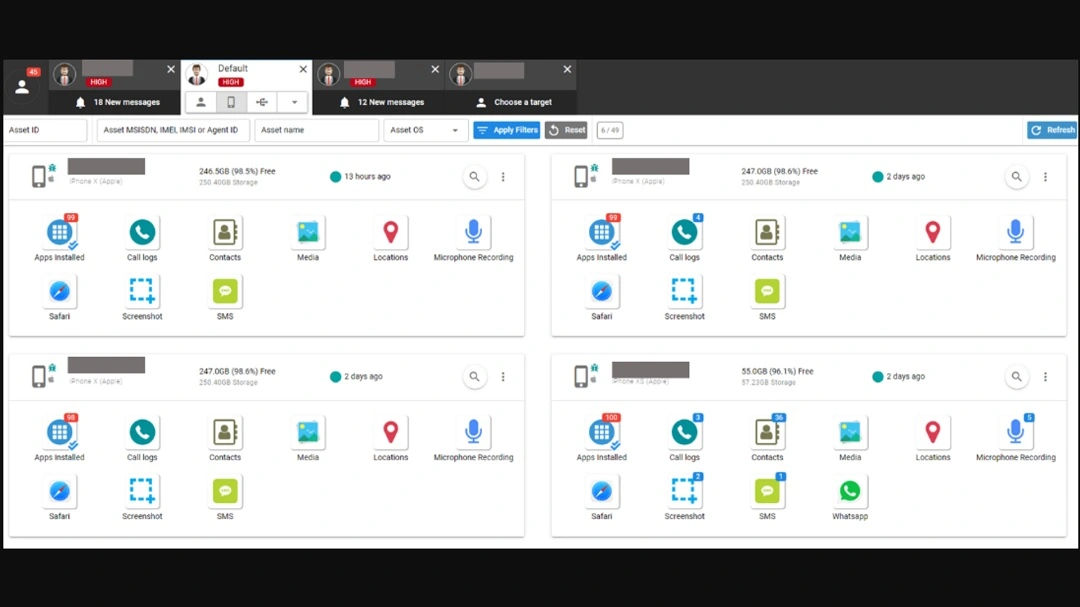
Among other things, Predator can:
- Breach Safari, Chrome, and iOS
- Breach Android devices
- Establish persistence with stealth
- Send data from breached devices to the Predator backend server via a chain of anonymization servers to prevent attribution
- See all installed apps
- Access call logs, contacts, and media on breached devices
- Access and operate SMS
- Access maps and locations
- Access the microphone and record audio
- Access Safari
- Access messaging apps like Signal and WhatsApp
- Take screenshots of breached devices
Once it is installed on a device, Predator can collect data from it for long periods of time. Those using Predator can also leverage the stolen data from breached devices to access other user accounts and use this data to breach other operating systems and device types, including Mac computers.
How does Predator breach devices?
Predator has used several methods to breach devices, including network injection and exploitation of vulnerabilities in apps and browsers. However, the new Predator, as mentioned, can breach users just by running an ad on their phone.
According to Google Threat Group, the malicious ad, which runs on third-party platforms, fingerprints users (grabs their IP) and redirects them to Intellexa’s exploit delivery servers. Once users are redirected to these servers, they are served an untrusted third-stage payload that is coded to abuse vulnerabilities in the browser, escaping its isolated environment or sandbox.
These malicious Predator ads can be found, according to Amnesty International’s Security Lab, on any website, including trusted news websites or mobile apps.
Beyond what is mentioned above, no one really knows how Aladdin pulls off the trick of infecting devices through ads in a zero-click attack.
Who does spyware like Predator target?
As previously mentioned, spyware like Predator targets high-level organizations such as government departments, human rights organizations, and others. These pieces of malware have also been documented in use against political activists, journalists, government opposition, and human rights advocates.
Google said that Predator has been identified targeting “several hundred accounts across various countries, including Pakistan, Kazakhstan, Angola, Egypt, Uzbekistan, Saudi Arabia, and Tajikistan.”
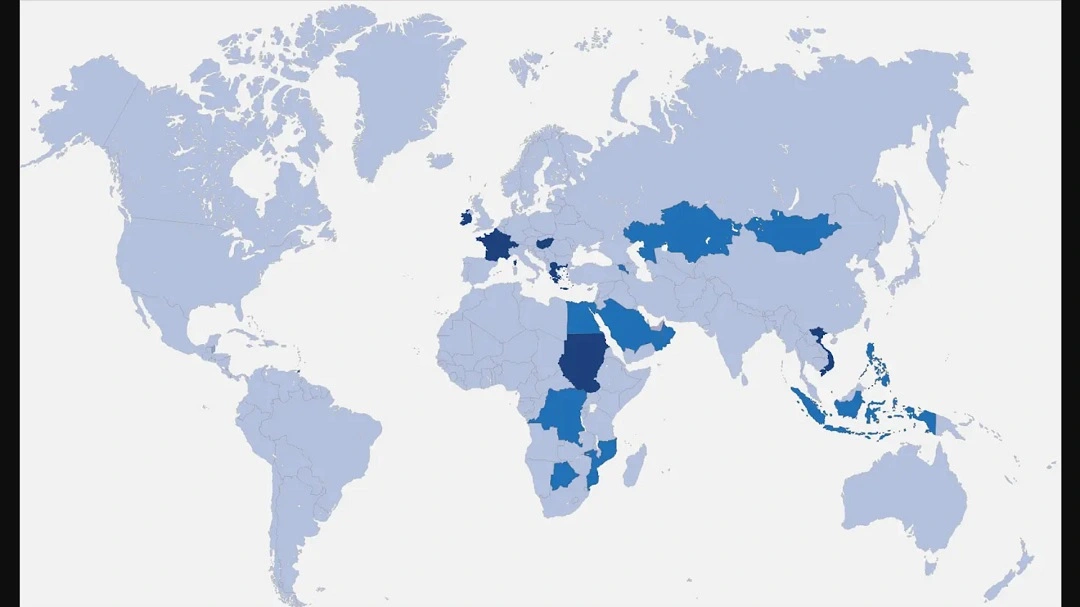
Recorded Future reported that in Greece, Predator has been used against journalists, politicians, businesspeople, and other public figures. This led to the “Predatorgate” scandal, which, in turn, led to multiple investigations and legal proceedings that are at this time ongoing.
Other investigations on Predator are also reported in the European Union. Experts say the recent leak of the internal Predator documents will most likely trigger more investigations and hopefully bring accountability to the matter.
Tips for Mac users: How to mitigate spyware and avoid zero-click malware
There are several things anyone can do to mitigate the risk of spyware, including advanced zero-click spyware. Predator seems to be exclusively leveraging browser vulnerabilities by serving malicious ads. These ad-serving, browser-breaching capabilities may be its Achilles heel.
Use an ad blocker, a VPN, and a secure browser
A good first step is to use an ad blocker. Another good idea is to use browsers designed for user privacy, such as Tor Browser or DuckDuckGo.
Because Predator needs to grab a user’s IP to redirect victims to the payload-serving server, the use of anti-malware tools is recommended. It is unclear if Predator can bypass adblockers, VPNs, and trackers.
Use an antivirus like Moonlock
If spyware tries to infect your Mac, a strong antivirus like Moonlock will quarantine it and prevent it from running.
Keep your devices updated
Additionally, while the company developing Predator responds to every security patch with a new exploit, keeping devices up to date with the latest patches is a must. If your phone pops up with a “security update available” notification, don’t wait. Install it.
Reduce your digital attack surface
Reducing your digital attack surface can help mitigate the risk of spyware too. This means having only necessary digital resources active. If you have several browsers, choose one and remove the rest. If you have many apps, delete the ones you don’t use. Apply this concept to all your devices to reduce your digital attack surface.
In the case that you think your Apple device has been targeted by spyware, turn on Lockdown Mode. Lockdown Mode is designed to dramatically reduce your digital attack surface.
Exercise caution
You should also try to avoid public or random Wi-Fi networks. Do not install random untrusted apps, and don’t scan QR codes if you aren’t sure about them.
Final thoughts
Predator is not the first, and unfortunately, will not be the last high-level mercenary spyware deployed in the wild. While the average user is generally untouched by this type of advanced spyware, understanding the issue—and what spyware technology can do today—is relevant to everyone.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. or Google LLC. Mac and Safari are trademarks of Apple Inc. Google Chrome is a trademark of Google LLC.







