Sony, JBL, Marshall, Nothing, OnePlus, and several other popular headphone brands used by millions of users around the world are vulnerable to spying. Researchers found that Google Fast Pair and headphone brands are failing to enforce important security checks. This hack affects Mac and iPhone users, despite exploiting a Google and Android vulnerability.
Researchers discover a vulnerability that affects millions of users, including Apple devices
Researchers at the computer security COSIC group of KU Leuven recently disclosed the new vulnerability WhisperPair. While the vulnerability exploits Bluetooth accessories that do not implement Google Fast Pair correctly, Mac and iPhone users are also affected because headphone brands build Google Fast Pair into their hardware.
Threat actors exploiting this vulnerability can connect remotely to your headphones, listen and record your conversations and surroundings, and even play around with your volume controls.
More concerningly, if the headphones you are using have never connected with an Android device before, the attackers can register your headphones as their own in their Google account and use Google’s Find Hub Network to track your location, where you went, and where you are going.
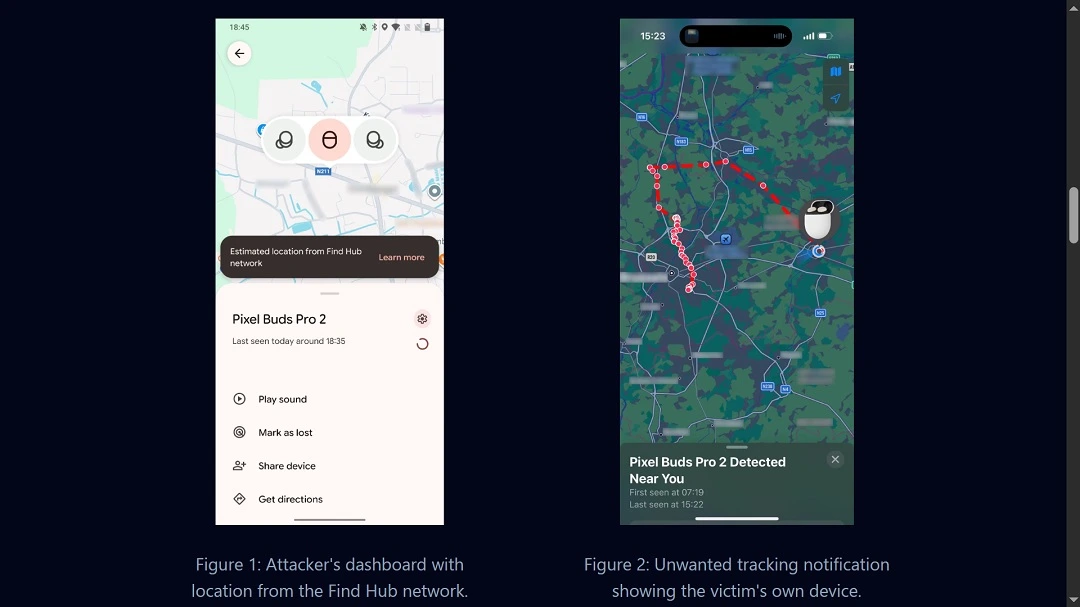
The big problem with this vulnerability is that Apple devices cannot be patched because, as mentioned, the problem is found at the hardware level of your headphones.
While we will go into steps on how to protect your privacy and security in the following sections and check to see if your Bluetooth device is affected, you can also check out the official WhisperPair vulnerable devices search page.
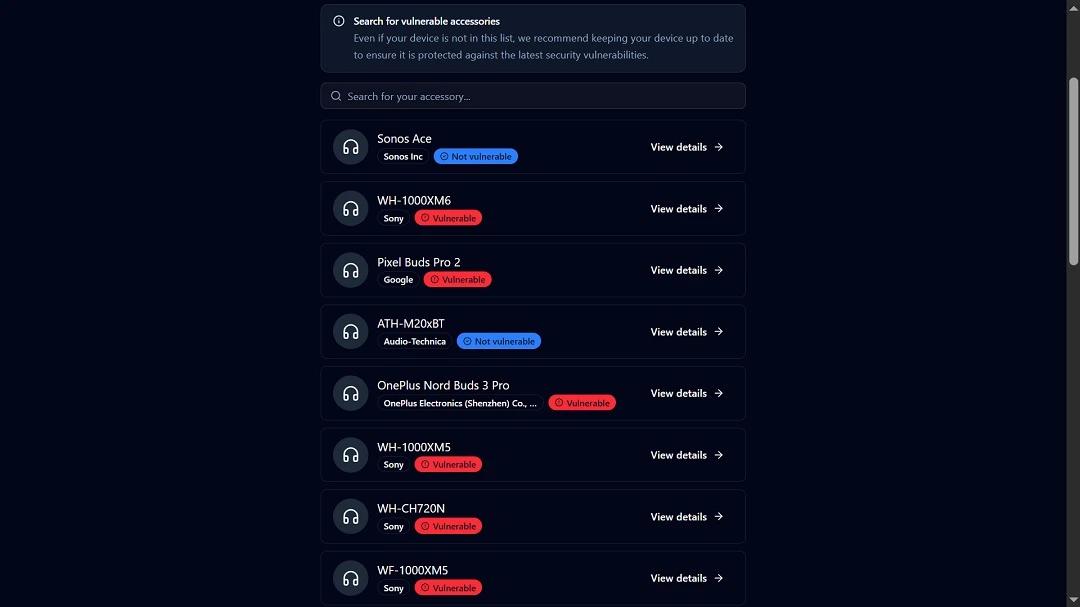
Bluetooth device manufacturers and Google fail to enforce important security checks
Technology security guardrails and certifications that ensure manufacturers are meeting certain standards are a good thing. However, if they’re just for show and no one is actually following them, they are pretty much useless.
Researchers from KU Leuven described the WhisperPair vulnerability as having a cross-ecosystem impact. “Since the Fast Pair functionality of an accessory cannot be disabled, users outside the Android ecosystem are also vulnerable to WhisperPair,” researchers explained.
The study shows that multiple devices, vendors, and chipsets are affected by this problem. While these devices passed Google’s certification process and other manufacturers’ quality assurance tests, they “demonstrate a systematic failure.”
This is not a problem with a single headphone brand but an issue that impacts a significant number of users around the world.
How does WhisperPair work? The “Ignore Pair Request” failure
Researchers did not publicly release details on how WhisperPair actually works due to ethical reasons. However, they did point out that the problem happens when the Fast Pair functionality is activated on a Bluetooth device or headphone.
Specifically, according to Fast Pair security specifications, Bluetooth devices need to ignore any pairing attempt if they are not in “Pairing Mode.”
However, this is not the case. For some reason, headphone manufacturers are ignoring this rule. This allows any bad actor who knows how WhisperPair works to pair itself to your headphones at a short distance (tested up to 14 meters).
Vulnerable devices will respond to unauthorized pairing requests, allowing attackers to basically connect to your headphones in seconds.
“The attack can be performed using commodity hardware and does not require user interaction,” researchers explained.
As mentioned, if the attacker pairs his device, a laptop, a terminal, or a smartphone to your headphones and your headphones were never linked to a Google account, the attacker can claim ownership of them. Then the attacker can use Google’s Find Hub Network to track your movements.
How to keep safe from WhisperPair and other Bluetooth vulnerabilities?
Hardware-level Bluetooth vulnerabilities are tough to work around because of the sheer volume of devices that you can connect to your computer or smartphone. That said, here are some tips that will strengthen your cybersecurity.
Keep your Bluetooth devices updated
To patch up this vulnerability, all headphone brands affected will have to roll out patches, so stay on the lookout for new updates for your headphones. You should also update your smartphone or computer, but remember that the problem is not found there. Factory-resetting your devices can remove unknown devices that are paired to your headphones, but it will not fix the underlying problem.
Get the Moonlock app. It will help stop spyware on your Mac.
A common way that malicious actors spy on unsuspecting users is via malware called spyware. An antivirus app like Moonlock will run live scans silently in the background, searching for any threat you may have encountered.
The app can also run scheduled deep Mac scans to search for spyware and other unwanted malware that may have snuck into your Mac, while providing you with special features and valuable advice on your Mac security.
You can try Moonlock with a 7-day free trial.
Use Bluetooth pairing securely
On your Mac and iPhone, there are several technologies that can help you build security around Bluetooth connections. One of them is pairing code requests.
When pairing a device, make sure the pairing code requests are matched. You should also turn off open pairing, avoid turning on Bluetooth in public spaces and public Wi-Fi environments, and use unique names for your devices. Finally, monitor your Bluetooth settings regularly to see which devices are connected. Remove any that you do not recognize.
Learn more about Apple Bluetooth Security at Apple’s official Bluetooth Security site.
Final thoughts
Bluetooth device vulnerabilities, usually used for snooping and spying on users, as well as revealing live and historic location, are nothing new. However, when new vulnerabilities like WhisperPair emerge, it’s a good opportunity to learn more about Bluetooth security and refresh security tips that help instill better digital habits that can improve our privacy and digital well-being.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and iPhone are trademarks of Apple Inc. Google and Android are trademarks of Google LLC.






