If you have been keeping up with recent cybersecurity news, you may have read about Apple putting less money into its security program, even as reports document the startling rise in macOS malware. Naturally, this may concern some users.
In this report, we explain what Apple is defunding, whether it has an impact on your security, and whether or not Mac malware is on the rise. Additionally, we will leave you with some tips and advice on how to take action and strengthen your security posture in just a few simple steps to respond to this breaking Mac news. Let’s dive in.
Take control of your Mac’s security
Yes, some Apple macOS bug bounty rewards are down
Recently, Csaba Fitzl, a macOS Security Researcher at Iru, an AI-powered security and IT security company, sounded the alarm on LinkedIn that Apple’s macOS bug bounty rewards were down. But what does this mean?
What is Apple’s Security Bounty program?
There are 3 ways in which Apple protects your Mac: built-in Apple cybersecurity tools, security updates, and bug bounty programs.
Apple’s bug bounty program, known officially as the Apple Security Bounty program, is the company’s way to leverage the talent of a global community of ethical hackers, security researchers, software developers, and cybersecurity companies dedicated to locating digital threats.
These digital threats, known as vulnerabilities, are how malware and threat actors sneak onto your Apple devices.
For each vulnerability submitted, researchers are paid a reward. These rewards range from $1,000 all the way up to $2 million, depending on how serious and sophisticated a vulnerability is.
Organizations like Objective-See, supported by cybersecurity companies like Palo Alto, Moonlock, Jamf, Sophos, iVerify, and Huntress, are an example of how the broader cybersecurity community, researchers, and ethical hackers contribute to Mac security.
When a company like Apple decides to lower the rewards, in this case, for macOS vulnerabilities, it naturally stirs up the cybersecurity community.
What exactly did Apple defund?
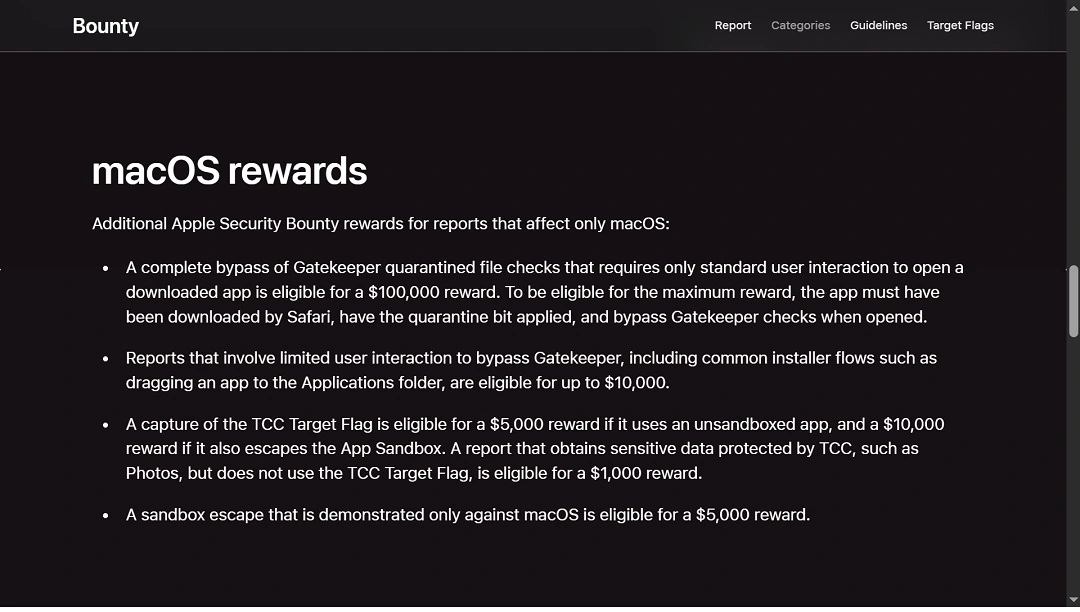
The rewards that Apple has defunded include vulnerabilities that can bypass Apple’s Transparency, Consent, and Control (TCC) privacy, a feature built into every macOS that protects your privacy by managing how data flows in your system, usually from app to app. In the past, anyone who found these vulnerabilities was rewarded with $30,500, but now, they are only worth $5,000.
Individual TCC vulnerabilities, meanwhile, which used to be worth $5,000 and $10,000, are now down to $1,000. Finally, macOS sandbox escapes—incidents when data leaves an isolated environment when it shouldn’t—are also down from $10,000 to $5,000.
Frustrated by the news, Csaba Fitzl said, “This feels really weird, especially because Apple’s mantra is privacy…”
Did Apple lower the cash prices on its entire Security Bounty program?
As Fitzl mentioned in his post, some rewards for some macOS vulnerabilities are down. However, this in no way means that the entire Apple Bounty program has been defunded, not by a long shot.
For ethical hackers and the broader cybersecurity community dedicated to finding macOS bugs and making systems more secure, there is still a lot of money on the table, as the image below shows.
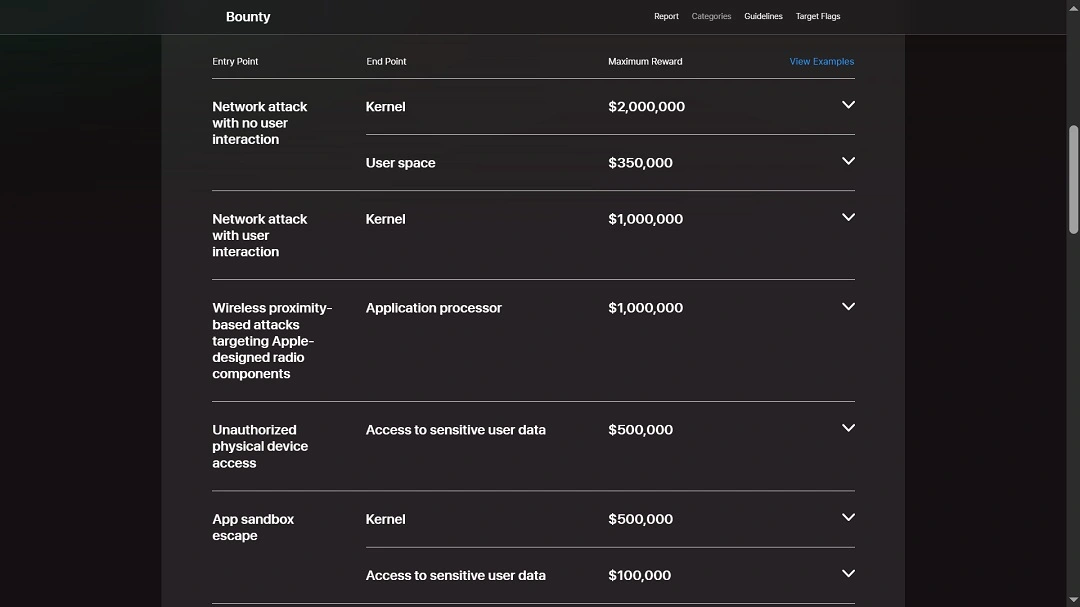
As previously mentioned, the more sophisticated and dangerous a threat, the bigger the reward. For example, vulnerabilities related to network attacks with no user interaction are worth up to $2 million, wireless proximity threats are worth up to $1 million, unauthorized physical device access to sensitive user data is worth up to $500,000, and some app sandbox escape vulnerabilities can be worth up to $500,000.
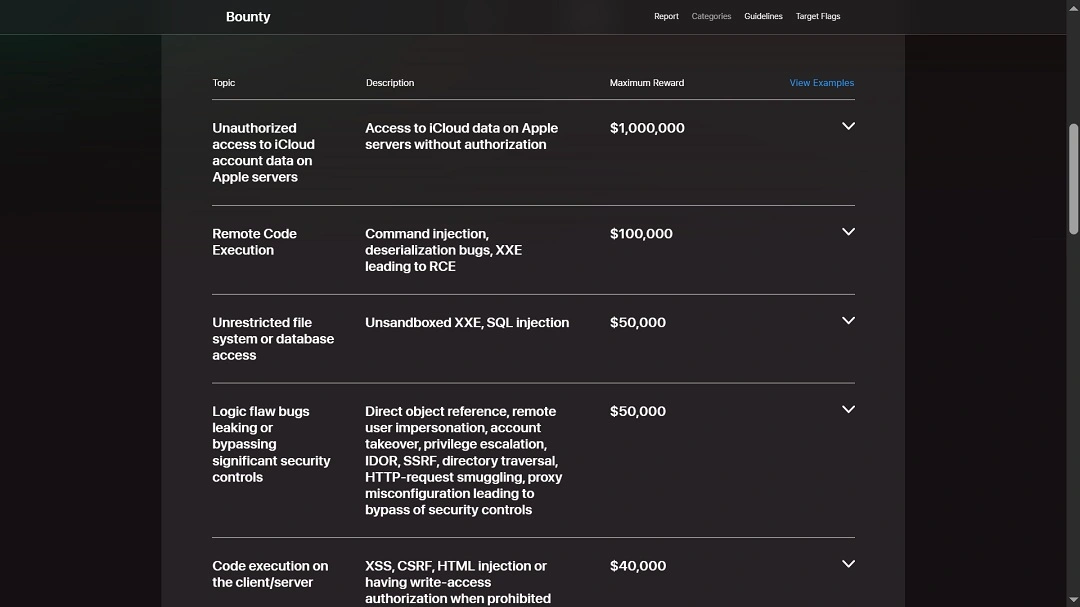
In this case, Apple is lowering the price for “low-level” vulnerabilities. This does not mean, however, that these vulnerabilities are unimportant. Let’s look at how this impacts your security.
How do lower bug bounty rewards impact Mac security?
The decision by Apple to defund low-level vulnerabilities, which malware like macOS stealers certainly exploit when stealing data from your computer, will be discouraging to some cybersecurity researchers.
The defunding may lead to several consequences, including:
- A lower number of ethical hackers and researchers interested in searching for and filing macOS bugs
- More unpatched and unsecured macOS vulnerabilities
- More room for cybercriminals and threat actors to exploit these unlocated vulnerabilities
- A loss of security innovation and privacy advancements for the Mac brand
Is Mac malware on the rise?
The recently released Moonlock 2025 macOS threat report found that Mac malware is definitely on the rise, with backdoor variants increasing by 67% in the past year and stealer variants rising by 17%.
Cybercriminals are also expanding the locations they target. The report found that users from more than 80 countries were impacted by major Mac stealer malware campaigns.
“macOS malware shows no signs of stopping,” the Moonlock report concluded.
macOS malware shows no signs of stopping.
Moonlock Lab
Mac malware is not only rising but also becoming more dangerous.
Traditionally, malware performed specific actions. But today, macOS malware is bundled in packages. This means that all it takes is for users to click the wrong link or download one malicious file to be infected by a variety of different malware.
A single piece of Mac malware today will commonly include different components, such as:
- Stealers that steal your passwords, wallet data, personal data, and files
- Backdoors that give access to hackers who can remotely control your Mac
- Spyware and keyloggers that can access the camera, mic, files, and apps, and record everything you type or say
- Bot malware that transforms your Mac into part of a network of infected devices to send out spam, launch fake traffic attacks (DDoS), distribute malware, and do other nasty things
Why is Mac malware increasing?
There are several reasons why Mac malware is on the rise. These include the capability to scale and speed up work that AI gives to threat actors, and a global, industrial black market that operates on the dark web.
In this dark web marketplace, there is heavy competition between those who develop Mac malware and tools for cybercriminals. This competition lowers the price of malware and makes malware and dark web kits more powerful.
For example, Mac stealers, which used to sell on the dark web for around $3,000, can now be bought for just $1,000. Phishing kits, stolen databases used to scam and personalize attacks and fraud, and other tools that include customer support, admin panels, and tutorials are also offered on the dark web by malware developers. This lowers the technical bar required for cybercriminals to run malware campaigns.
What can Mac users do to strengthen their security and privacy?
Despite the news of more malware and lower rewards from the Apple Security Bounty program, there are still many things users can do to protect their Macs. The following are some simple but highly effective ways to respond to these new developments and close 2025 with confidence.
Stay vigilant and informed
First things first. Your best bet is to take a proactive, hands-on approach to your own digital security. Stay informed and up to date on Mac news. The more informed you are, the better decisions you can take when it comes to your data and privacy.
Use a cybersecurity tool like Moonlock
Second, keep in mind that your Mac’s built-in security tools, like Gatekeeper and TCC, will only get you so far. Your Mac is not immune to cyberthreats, and the tools that come with your computer can (and will) be breached and bypassed by cybercriminals, scammers, and threat actors. It happens to Mac users every day.
It is highly recommended that you get your own professional and trusted anti-malware tool. Consider a reliable antivirus app like Moonlock, which monitors your Mac for threats and blocks them right away.
Take precautions online
Besides a good anti-malware app, knowing how malware gets into your Mac is fundamental for protection.
All existing macOS malware today, with the exception of rare, zero-click cyber espionage attacks, requires an action from the user to be installed on a Mac. This means that if you take special precautions online, think twice before clicking or downloading, you can increase your security posture significantly.
Moonlock’s report found that malware is breaching Macs in the following ways:
- Fake software updates
- Fake job offers and interviews
- Fake ads, impersonation malware, and phishing sites
- ClickFix attacks
- Phishing, vishing, and smishing
- Resources used by Mac developers
- Pirated software and fake downloads
This list is not exhaustive, and cybercriminals are always looking for new ways to trick users. Ultimately, only highly sophisticated zero-click malware can breach your Mac without your “permission.” These zero-click attacks are rare and are typically only linked to nation-state spyware targeting high-level organizations and individuals.
Tighten your security settings
Other cost-effective steps you can take include strengthening your passwords, enabling MFA, using biometrics, and choosing your favorite browser based on its security and privacy features and reputation. Moonlock’s System Protection will show you which macOS settings should be changed to improve your security, and its Security Advisor will walk you through secure online habits.
Final thoughts
While there are impacts to Apple lowering the price for some security rewards for Mac vulnerabilities, and while macOS malware is on the rise, you still have a say in your own security. By staying informed and taking simple actions, you can take ownership of your digital environment and protect your data.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.







