Bluesnarfing is an old-school method for hacking devices and downloading personal information over a Bluetooth connection without the user’s knowledge. These cyberattacks usually give the attacker limited access to data, only including things such as a phone’s contacts and calendar events. However, some more sophisticated forms of bluesnarfing can give attackers more access and control.
Bluesnarfing was primarily performed against phones during the early 2000s, when devices implemented some Bluetooth communication protocols in a way that left them vulnerable. These attacks are rare today because modern devices usually aren’t susceptible. Nevertheless, it’s better to be safe than sorry. Fortunately, there are ways to keep your device safe from bluesnarfing. Here’s all you need to know.
What is bluesnarfing in cybersecurity?
Bluesnarfing is a cyberattack that involves stealing data from your device over a Bluetooth connection. “Snarfing” is a term used in some tech communities as a synonym for “grabbing” or “taking,” usually with little regard for laws or rules. “Bluesnarfing” is the “snarfing” of someone’s data via Bluetooth.
Stay one step ahead of attackers
A bluesnarfing attack typically involves connecting to your device over Bluetooth. This is done by using a specialized bluesnarfing tool and then accessing and downloading your information without your knowledge. That information may include contacts, text messages, and calendar information.
Is bluesnarfing still possible?
Thankfully, it’s not possible to launch a bluesnarfing attack on most devices today. Bluesnarfing relies on exploiting vulnerabilities in certain phones that implement the OBEX (Object Exchange) communication protocol in a particular way. Vulnerable devices were primarily Nokia and Sony Ericsson phones from 2004 and earlier. Devices today shouldn’t be vulnerable to bluesnarfing.
Furthermore, even devices that are vulnerable to bluesnarfing attacks must be within Bluetooth range of the attacker. This typically means a distance of 30 feet. Plus, the device must have Bluetooth discoverability enabled.
Why is bluesnarfing dangerous?
Bluesnarfing can be very dangerous for devices that are vulnerable. A successful bluesnarfing hack gives the attacker access to some of your personal information. Crucially, it can also allow them to set up further cyberattacks and use your information for criminal purposes.
Here are some of the dangerous consequences of bluesnarfing:
- Stealing common Bluetooth data: Bluesnarfing attacks give access to data commonly transmitted over the Bluetooth protocol that the snarfing technique targets. This information includes contacts, call logs, calendar items, and possibly emails and text messages.
- Stealing personal data: If the bluesnarfing attack uses a more sophisticated tool, it might give the attacker access to more kinds of personal information from your device, such as photos and videos.
- Deleted files: If the bluesnarfing attack is a more sophisticated one, it might also give the attacker the ability to delete files such as your call logs, contacts, and text messages.
- Malware: A successful bluesnarfing attack could be used to prep your device for the installation of malware, which might further steal your data or gain control of your device for other purposes.
- Diverted calls and texts: A bluesnarfer might use their access to your device to set up text message and call diversion so that they receive your texts and calls instead of yourself.
- Identity theft: Data that an attacker steals when bluesnarfing could be used to steal your identity. For example, they might use what they learn about you from your calendar, contacts, text messages, and other personal files to open up credit accounts in your name. Bluesnarfing, therefore, can lead to identity theft.

Bluesnarfing vs. bluebugging
Just as with bluesnarfing and bluejacking, bluebugging is a cyberattack carried out over a Bluetooth connection.
Bluesnarfing is a Bluetooth attack that attempts to secretly steal your personal data, such as contacts and call logs. It does this by exploiting vulnerabilities in the way some older devices use the OBEX protocol.
Bluebugging is a Bluetooth attack that uses similar OBEX-based vulnerabilities to those leveraged in bluesnarfing, but once the attacker has access to your device, they install a backdoor onto it so they can gain control of it later on, even without a Bluetooth connection. This is why it’s called bluebugging. It “bugs” your phone or other Bluetooth device for repeated or continuous access.
What’s the difference between bluesnarfing and bluebugging?
Here are some of the key differences between bluesnarfing and bluebugging:
- Temporary: A bluesnarfing attack is temporary. The attacker can only download personal information from your device while they’re connected and in Bluetooth range. A bluebugging attack, however, sets up a backdoor so that the attacker can continue accessing your device in the future.
- Range: A bluebugging attack won’t necessarily require the attacker to be in Bluetooth range once they’ve set up the backdoor. They might be able to call themselves from your device at any point or use your device’s Wi-Fi connection to establish a connection to their own device. A bluesnarfing attack, on the other hand, always requires the attacker to be in Bluetooth range.
- Bluetooth enabled/disabled: Once the backdoor is set up, Bluebugging attacks might be able to connect to and control your device even when you have Bluetooth disabled. Bluesnarfing attacks, on the other hand, always require your Bluetooth to be enabled.
- Full control: While more sophisticated Bluesnarfing attacks also allow the attacker to gain a level of control over your device, such as by setting up call forwarding or deleting some of your messages or contacts, a bluebugging backdoor gives an attacker continuous access to your device. This gives them much more time to set up further exploits to control more aspects of your device.
How does bluesnarfing work?
A bluesnarfing attack usually begins when you’re in a crowded public place. Bluetooth attackers usually pick these places to target their victims because it gives them access to a larger number of potentially vulnerable Bluetooth devices.
The attacker will scan for vulnerable devices. If one happens to be vulnerable to this kind of attack, they will attempt to steal the user’s personal information via Bluetooth.
Bluesnarfing attacks accomplish this by exploiting the fact that some vendor software uses the Object Exchange (OBEX) protocol, a communication protocol originally designed for “pushing” (sending) and “pulling” (receiving) business cards from PDA (personal digital assistant) devices to other PDAs.
The attacker might use the BlueSnarf or BlueSnarf++ exploit kit that’s included as part of the Bluediving software package, or separate software such as BlueSnarfer, to scan for vulnerable Bluetooth-enabled devices. When they find one, they’ll use the software to exploit the OBEX protocol implementation on these devices and gain access.
From here, depending on the tool used and the level of access granted — BlueSnarf++, for example, allows for more access and control than BlueSnarf — the attacker might download your personal information. Alternatively, they might delete some information and access other kinds of data on your device, such as notes and photos.
An attacker might also try to discover your IMEI (international mobile equipment identity) and use this to divert your calls and texts to their own device.
What does bluesnarfing do to my device?
Most bluesnarfing attacks don’t do much to your device other than steal information from them. Here are some common effects of bluesnarfing on your device:
- Sending basic information: The primary goal of a bluesnarfing attack is to steal some of your basic personal information, such as your contact list and your calendar events.
- Deleting basic information: More sophisticated bluesnarfing tools allow the attacker to delete information rather than steal it.
- Sending more information: Bluesnarfing attacks can, in some cases, be used to set up further exploits. These exploits give the attacker access to more detailed data. Sometimes, they can be used to get your device to send data such as personal photos and text files to the attacker.
- Hijacking texting and calling: Bluesnarfing can also be used to have your device redirect texts and calls to the attacker so that they receive them and you don’t. This is commonly achieved when a Bluesnarfing attack gives the attacker access to your IMEI.
- Installing malware: In some cases, a bluesnarfing attack might be used to install malware on your device. The malware can then steal more of your information or use your device for nefarious or illegal purposes.
Signs of a bluesnarfing attack
One of the scariest things about bluesnarfing is that it’s often difficult to detect. The whole point of the hack is that the attacker accesses your device and steals some of your personal information without your knowledge. Despite this, there are some signs you can look out for.
The following are the most common signs of a bluesnarfing attack.
Deleted phone contacts
While an attacker will usually just download a victim’s list of phone contacts, they might sometimes (perhaps accidentally) delete some of those contacts. If you notice missing contacts in your phonebook, this could be a sign that you’ve been a victim of bluesnarfing.
Deleted files
Similarly, while a bluesnarfing attacker will usually just download your personal information, they might delete some of it, too. More sophisticated attacks can give the attacker access to information such as text messages, photos, and notes. If you notice that some of these things have been deleted, you might be a bluesnarfing victim.
Redirected calls or texts
Sometimes, an attacker will use this hacking method to gain access to your IMEI. They will then redirect your calls or texts to their device instead of your own. Consequently, you might notice some of the common signs of a SIM swapping or SIM spoofing attack, such as your phone only ringing for a second or two or people informing you that they can’t contact you. You can enter and call “*#21#” to see if call forwarding has been enabled.
Unusual Bluetooth activty
While it’s never a sure sign of a Bluetooth cyberattack, let alone a bluesnarfing one, unusual Bluetooth activity may be a sign of something nefarious. A hacker downloading your personal data over Bluetooth could make your other Bluetooth connections play up, for example, with intermittent connectivity.
How to prevent bluesnarfing attacks
Thankfully, most modern devices are safe from bluesnarfing. In theory, only certain older devices are vulnerable. Nevertheless, it’s better to be safe than sorry.
There are some things you can do to make bluesnarfing attacks more likely, even if your device is vulnerable. Here’s how to keep your Bluetooth devices safe from bluesnarfing.
Keep your Bluetooth devices updated
Bluetooth device manufacturers and software vendors try to keep their products secure from Bluetooth vulnerabilities. This, however, relies on users installing the security updates they release. As such, ensure you keep all your Bluetooth devices up-to-date.
Disable Bluetooth discoverability
A bluesnarfing attacker shouldn’t be able to connect to your Bluetooth device to carry out their attack if it isn’t discoverable. To hack your device when it’s not discoverable would require them to guess its MAC address, a unique identifier for which there are millions of possible combinations. It’s highly unlikely that a hacker would be able to do so.
Fortunately, most modern devices have Bluetooth discoverability disabled by default. For example, iPhones can only be discovered over Bluetooth when the Bluetooth Settings page is open. This makes bluesnarfing an iPhone very difficult.
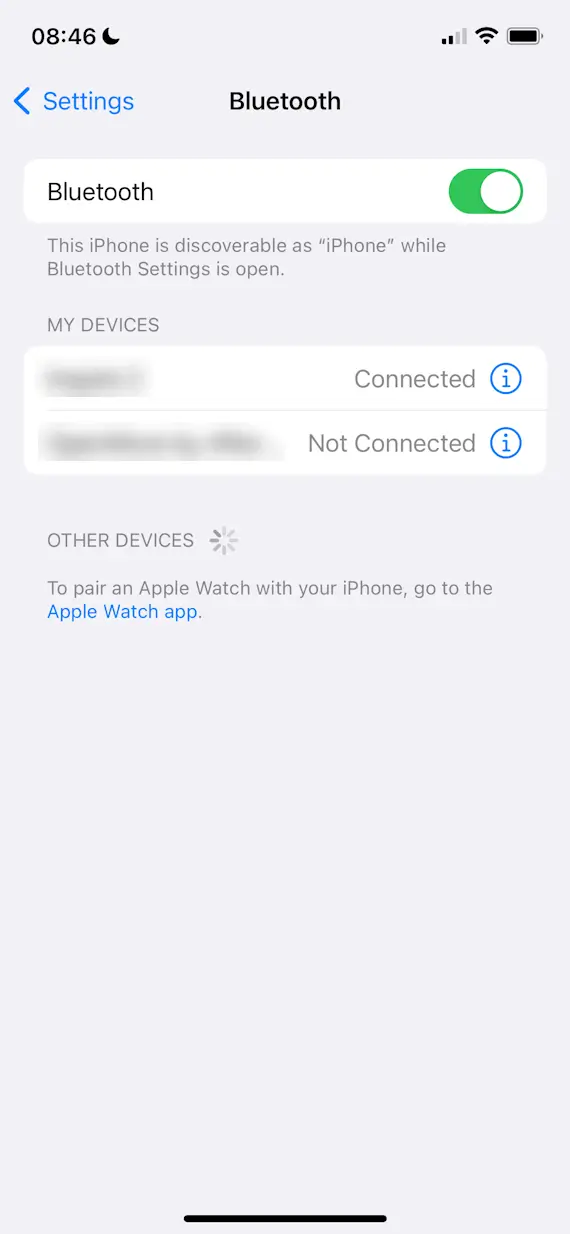
Turn off Bluetooth
The surest way to prevent your device from being attacked over Bluetooth is to disable the connection technology entirely. Most devices give you an easy way of doing this. On iPhone, for example, you can drag open the notification panel and press the Bluetooth icon to turn off Bluetooth until tomorrow. Alternatively, you can navigate to the Bluetooth section in Settings.
Don’t pair Bluetooth devices in public
Another preventative measure you can take is to not pair any Bluetooth devices in public. This is because pairing your devices often requires you to turn Bluetooth discoverability on. Because this potentially opens devices up to Bluetooth attacks such as bluesnarfing, it’s safer to only pair your devices when you’re at home. Even when Bluetooth discoverability is only enabled temporarily, it can give an in-range Bluetooth attacker the opportunity to hack your device.
Overall, bluesnarfing is a particularly dangerous Bluetooth hacking technique. It involves secretly connecting to your device over Bluetooth and stealing some of your personal information, such as your contacts, text messages, and calendar events. More sophisticated attacks can also allow an attacker to delete some of your personal information or redirect your calls and texts.
Fortunately, bluesnarfing attacks are uncommon today because most modern devices aren’t susceptible to them. But it’s still good practice to protect your device from these and other kinds of Bluetooth cyberattacks. The simplest way to do this is by keeping Bluetooth discoverability off and only enabling Bluetooth when you need to use it.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by the Bluetooth Special Interest Group. Bluetooth is a trademark of the Bluetooth Special Interest Group.







