Malware has become the bane of every technology lover’s existence. Not only is it annoying, but it is also very damaging and can lead to severe consequences. These days, anyone who uses a computer or mobile device should learn all about malware, including how it works, what a malware infection looks like, and how to protect themselves.
Continue reading to learn about malware. You’ll also learn some professional tips on how to rid your devices of malicious threats and prevent future infections.
What is malware?
Malware is malicious software that steals data, damages networks or systems, or holds information hostage for money. It is developed by cybercriminals (also known as hackers). Some examples of malware are adware, spyware, ransomware, viruses, worms, and trojans.
Why is malware dangerous?
Malware is dangerous because it disrupts our digital lives, destroys data, compromises hardware/software, and increases our vulnerability to other threats. Anytime your device is infected, it could expose your most personal information or sensitive secrets.
It is essential to have a malware tool to protect your device(s) from threats like viruses, spyware, ransomware, and adware. This malicious software is used by hackers and other criminals to steal your data, damage files, or use your device without your knowledge. To protect against hackers using malware, you can try Moonlock.
Moonlock is a Mac protection and antivirus app that makes cybersecurity approachable and can help you secure your device, even finding threats that are hidden on your Mac. It gives you peace of mind by protecting you from existing threats and future ones, constantly scanning for malware and isolating it. You can get a free 7-day trial to see Moonlock in action and test its anti-malware protection.
What does malware do?
Some malware spies on you, copying passwords and account information. Other types display pop-up ads. Still others destroy files or hold them for ransom in exchange for payment. And while some types of malware require direct intervention, others are self-replicating and can spread across networks in seconds.
The evolution of malware
Malware is a blanket term used to describe many types of digital attacks. The first malware was a virus known as Creeper, first seen in 1971, which spread across the United States Advanced Research Projects Agency Network (ARPANET), the first public computer network.
The 80s saw many firsts, including the first Mac and PC viruses. In the late 1990s, several worms made trouble for computer owners, and by 1989, we saw the first signs of ransomware holding files hostage for money.
Since then, the world has seen thousands of different types of attacks, each more sophisticated and damaging than the last. Cybersecurity experts struggle to keep up with the evolution of it.
What is the purpose of malware today, and why is it used?
Why do criminals and hackers use malware infections? What’s in it for them? Let’s take a look at some of the motives:
- Money — the oldest motive known to man. Money is the number one reason why malware is created and sent out into the wild in the first place. This can take the form of many different malware types, such as ransomware, crypto miners, adware, and others that will steal your personal data. Malware that targets money can also be based on affiliate schemes where the hacker gets a cut every time a victim clicks on a link.
- Surveillance — in general, this will only affect a small subsection of the population. Not everybody is going to be under the watchful eye of the National Security Agency or other international government agencies. However, these types of people can use malware, such as keyloggers, to break into computers to monitor conversations and web history.
- Theft of personal data — another reason for malware is to steal someone’s personal data for the purposes of identity theft. This will include elements like names, addresses, phone numbers, dates of birth, social security numbers, and credit card numbers.
- Remote control of other computers — if a hacker uses malware to remotely access your machine, your device can theoretically be used, along with other infected devices, as part of a botnet. These botnets can then be used to carry out distributed denial of service (DDoS) attacks to take down websites and networks.
- Amusement — sometimes, a hacker doesn’t need a reason to break into something. Sometimes, hackers just get a kick out of breaking things. Attacks can be carried out for revenge or simple fun, as they see it. They may also carry out malware attacks for bragging rights.
Who becomes a target for malware?
On the face of it, everyone is a potential target for a malware attack — it doesn’t discriminate. Whether you have a Mac computer or a Windows computer, it makes no difference. And contrary to popular opinion, Macs do need antivirus software to counter malware threats.
However, there are some categories of people who are at higher risk than others:
- People who use the same password over and over for different online accounts
- People who click on links and download email attachments from unknown senders
- Computer users who do not update their operating system or their apps
- Those who use unsecured Wi-Fi networks without using a VPN
- People who click on pop-up ads
- People who download free software from unknown developers
What is a malware attack?
Digital attacks that use malware — meaning the attacker uses a type of software to carry out the attack — are extremely common. Malware attacks can vary, but the overall objective is typically financial gain. In other cases, the goal might be the destruction or theft of data to be used in identity theft.
Real-world cases of malware attacks
We have seen many real-world cases of malware affecting thousands, if not millions, of users. Some extreme cases include the following.
ILOVEYOU worm
In early 2000, the ILOVEYOU worm infected more than 45 million people, costing $15 million in damages.
WannaCry ransomware
In 2017, WannaCry malware infected 230,000 computers — in a single day. It remains one of the costliest attacks in history, totaling $4 billion in ransomware losses.
Emotet trojan
The US Department of Homeland Security calls the Emotet trojan the most damaging malware attack to date. Emotet not only stole millions of dollars of sensitive financial information from government organizations worldwide but also resulted in additional spam and phishing attacks, costing an average of $1 million per incident.
Types of malware
Each type of malware works slightly differently and is used for a specific purpose. The following are the most common types:
- Virus: Viruses infect computers or mobile devices and destroy data, copy files, or ruin operating systems.
- Worm: Worms spread across networks without any user intervention, using up system resources.
- Ransomware: Ransomware encrypts data, holding it hostage until the owner pays a ransom.
- Trojan: Trojans pose as legitimate software, only to then run in the background, stealing data or taking remote control of a network.
- Spyware: Spyware is designed to spy on your online activities and report back to a central server or collect data for identity theft.
- Adware: Adware displays ads to the user, getting them to click links.
- Keylogger: A keylogger copies keystrokes, usually with the aim of stealing login credentials for online accounts, banking info, or credit cards.
- Backdoor: A backdoor is a program that allows someone to break into a network at will. Backdoors are usually combined with other types of malware.
- Botnet: Botnets ensnare other devices into a network to perform functions usually used in conjunction with distributed denial-of-service attacks.
Common malware infection methods
Threat actors have many different infection methods at their disposal. Most infections occur, however, simply due to user error. Therefore, many of these infection methods are avoidable if you follow cybersecurity best practices.
Phishing emails
The most common method of malware infection occurs through a phishing email where the user clicks a malicious link. At that point, their device becomes infected.
Fake websites
Sometimes, websites are infected, and if you visit them, your device could be affected by a drive-by attack. Hackers are experts at making these fake websites look authentic, tricking you into thinking you are on a legitimate site.
Man-in-the-middle attacks
In a man-in-the-middle attack, bad actors steal information by positioning themselves between two sources of information. This is especially easy to do on unsecured public Wi-Fi networks. Every time you connect to an unsecured Wi-Fi network, you put yourself at risk of being infected, so never connect to an open network without using a VPN.
Downloading unsafe files
Downloading software or files from untrusted websites is never a good idea. Files from unverified third parties could be laced with malicious software, and you could infect your device that way.
Symptoms of malware and how to get rid of it quickly
The symptoms of malware rarely differ, so if you know what to look for, you can detect it and remove it quickly. Despite common misconceptions, there is a difference between malware and viruses. The most common malware symptoms include:
- Pop-up ads appear with scary messages telling you that your device has been infected.
- Your browser settings have been changed, including your default search engine.
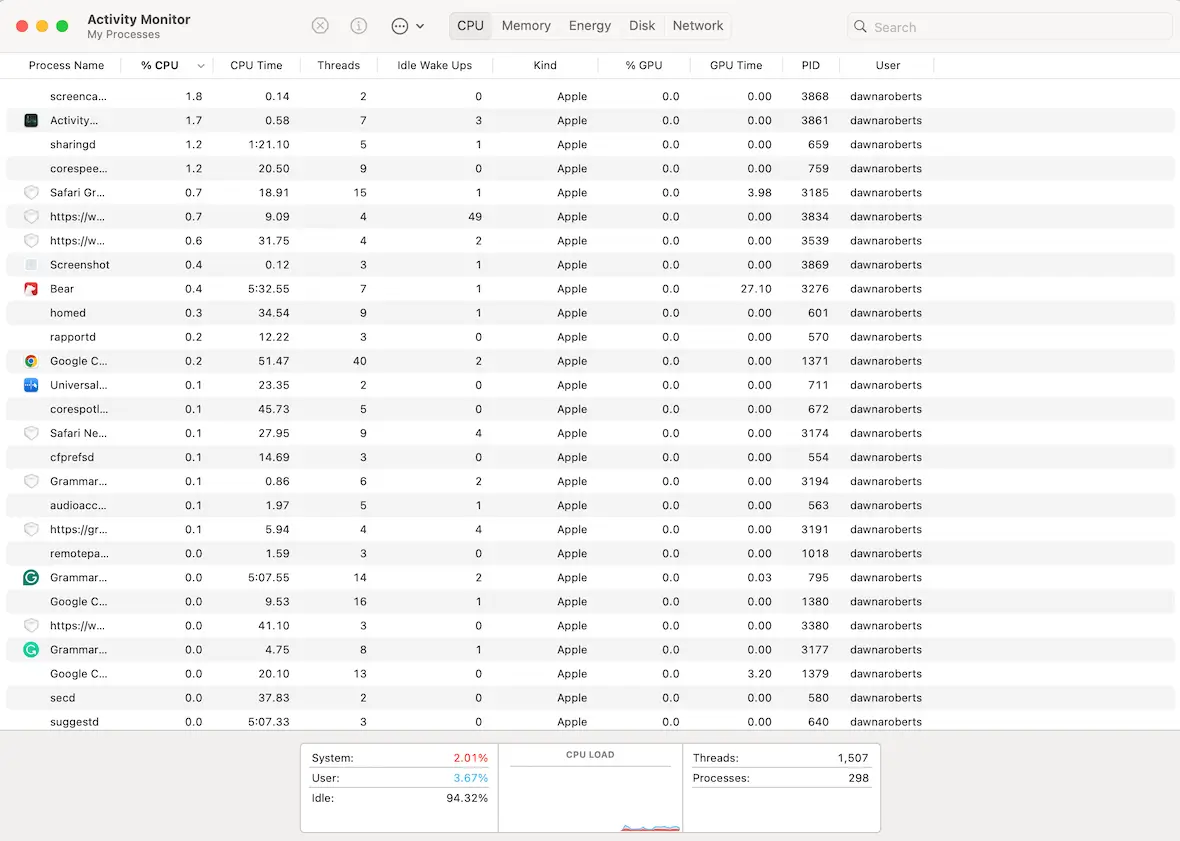
- Your device has significantly slowed down and the battery is overheating. Checking Activity Monitor will show scripts that are consuming a large amount of your CPU.
- When it comes to a MacBook, the biggest signs of malware are changes to your system, such as configuration profiles and login items.
For more on malware symptoms, we have set up tutorials on how to detect malware and how to remove malware. We highly recommend that you read these pages. We also recommend taking a look at Moonlock. As we mentioned previously, this is the best way to protect yourself against malware. Getting started with Moonlock is simple:
- Sign up for a free trial and download the Moonlock app.
- Open up the Malware Scanner.
- Make sure all of the settings are set up to your liking.
- Hit the Scan button.
- Review the findings from the scan and remove everything the scan found.

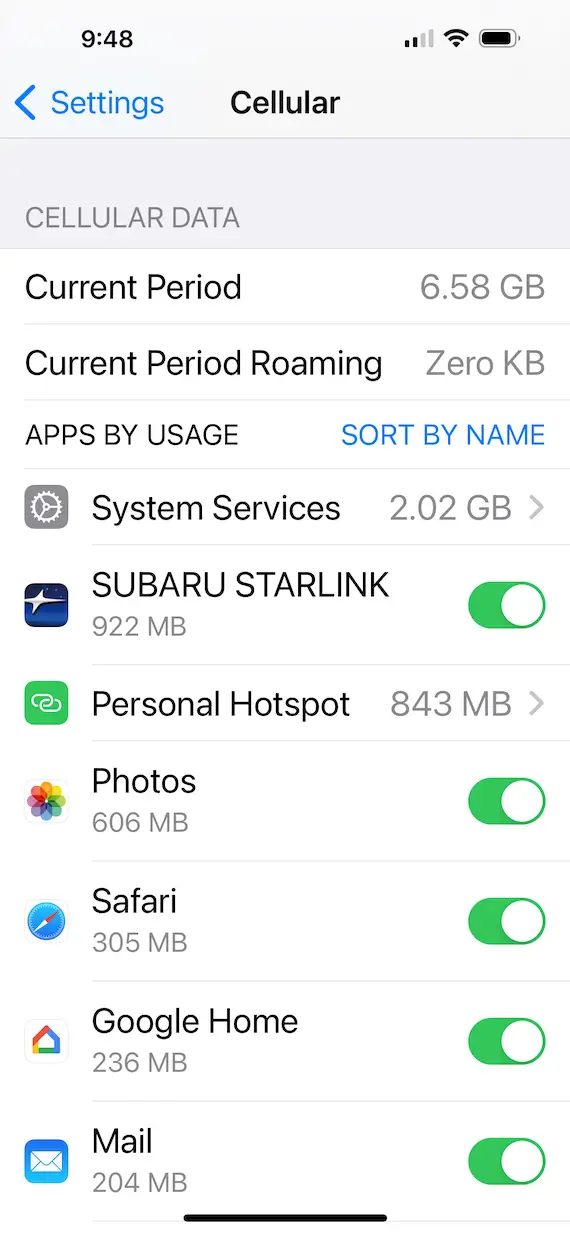
How to check for malware on iPhone
Although finding malware on an iPhone is rare, it can happen, especially if you have a jailbroken operating system. You can check for malware by looking for any apps you don’t recognize, checking your data usage and power consumption, and scanning your phone with antivirus protection software.
How to reduce your risk of malware infections
Here are the top 3 tips to prevent malware on your Mac:
- Never click any links or download any email attachments from people you don’t know.
- Always update your operating system, software, and apps as soon as a patch becomes available.
- Use Moonlock as system protection to ensure all of your system settings are locked down as tightly as possible.
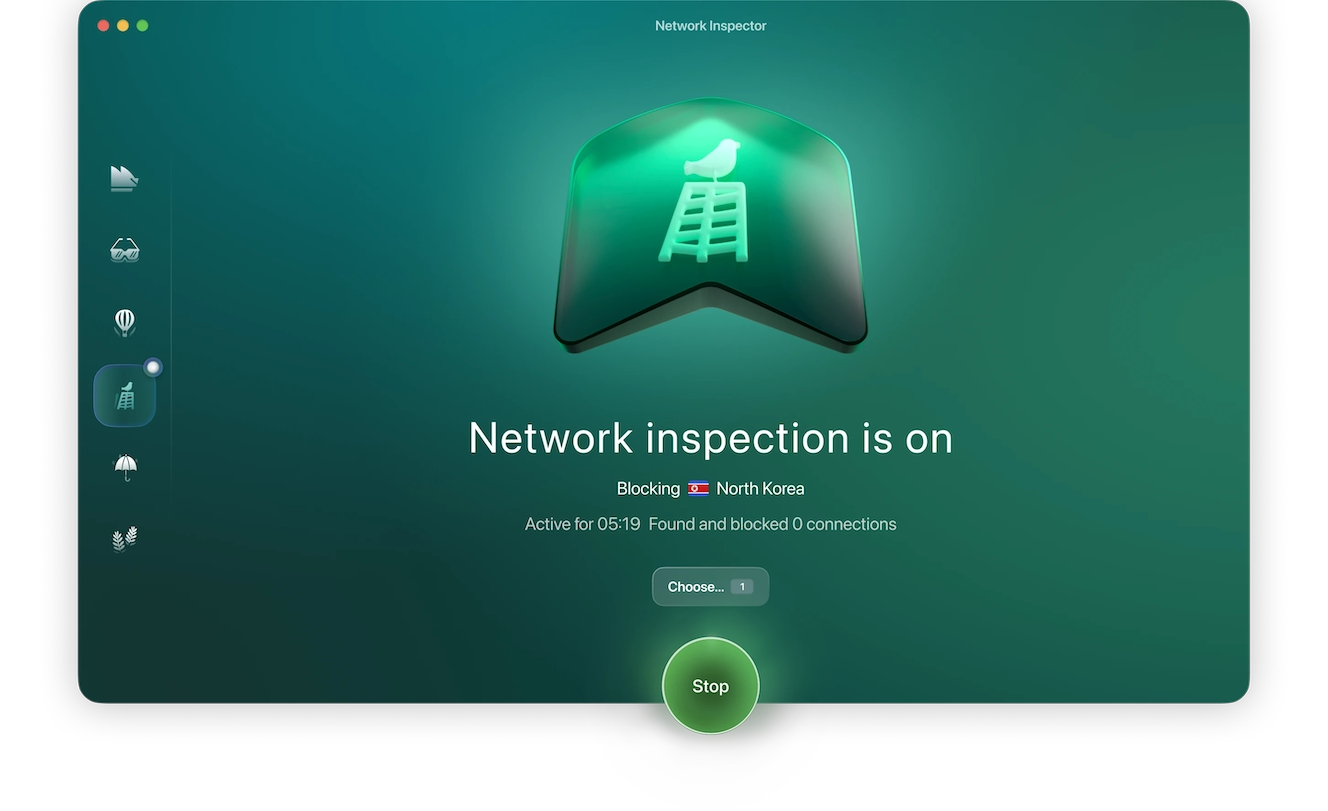
- You can also take advantage of Moonlock’s Network Inspector to block servers from accessing your data and monitor which apps send your data overseas without you knowing.
- Never use unsecured public Wi-Fi without using a VPN. Ideally, you should not use public Wi-Fi at all.
For a more comprehensive list of tips on how to avoid malware, check out our article on how to prevent malware attacks.
Malware is no minor annoyance. It is a dangerous threat to your digital security and should be treated as such. Fortunately, you can use the methods and safeguards above to keep all your devices clean and running smoothly.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iPhone, Mac, iOS, and macOS are trademarks of Apple Inc.