
You may have never even heard of the open-source command-line tool known as curl. But, chances are, if you are an Apple user or you visit sites like YouTube, Instagram, Skype, or many other popular websites, you are already using curl regularly without even knowing it.
This small yet powerful tool and some of the libraries it depends on are used heavily by developers and programmers around the world. But why are we talking about this small tool, curl?
On November 10, Intego released the findings of a new investigation, which reveals that Apple is neglecting to patch multiple critical vulnerabilities in macOS. And, you guessed it, these vulnerabilities are linked to curl. Let’s dive into the news and find out what this means for you.
Is it me, or are Apple updates a bit strange lately?
For the past couple of months, Apple has been forced to stay quite busy updating iOS, watchOS, and macOS as it responds to zero-day exploits, new attacks, and system bugs.
It is common for software developers to find new bugs and vulnerabilities after new OS versions are released. However, it seems that things have been getting a bit out of control for Apple this year.
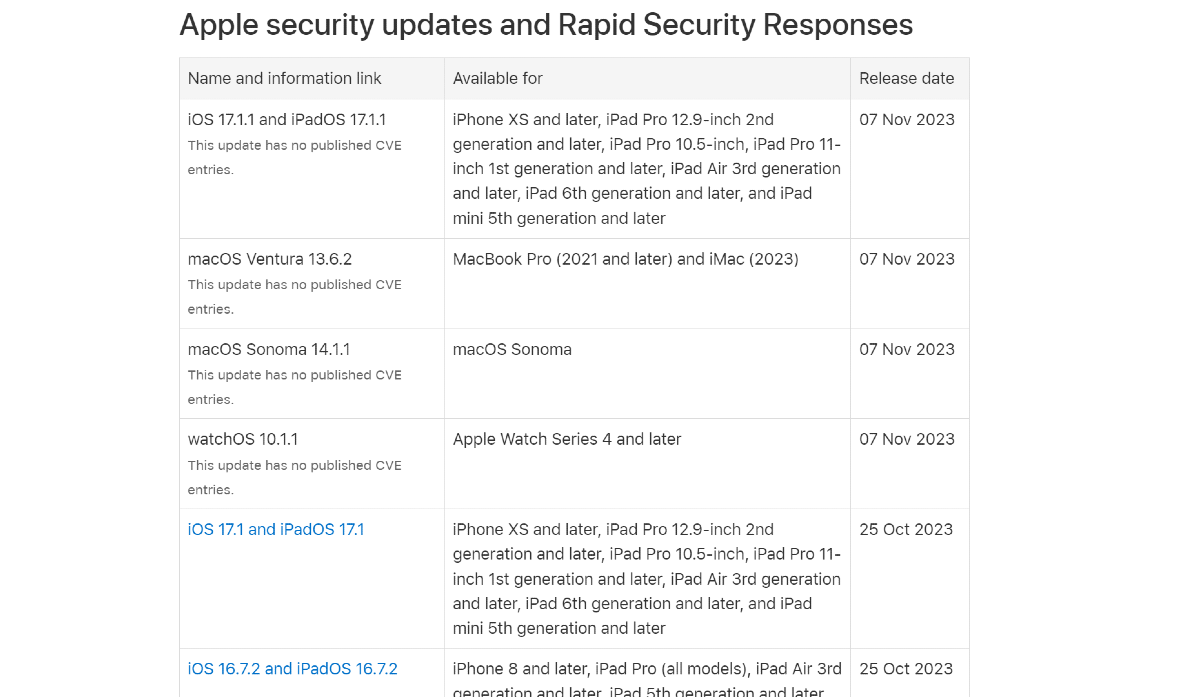
Bloomberg reported on November 7 that in a “rare” move, Apple decided to “hit the pause button” on software updates for next year for Mac, iPhone, iPad, and other devices. The reason? According to the anonymous source who spoke to Bloomberg, there are just too many bugs and issues with the existing codes.
Recent back-to-back Sonoma updates missed vulnerabilities
Mac users operating with Sonoma may be aware of the back-to-back updates released on October 25, 2023 (Sonoma 14.1) and November 7, 2023 (Sonoma 14.1.1). But, as Intego reports, both of these updates are missing vital curl security patches, which may leave Mac users exposed.

About a month ago, news media outlets reported that the popular command-line utility, curl, and its associated library, libcurl, had two newly discovered vulnerabilities. One of them, CVE-2023-38545, ranked 9.8 CRITICAL, was patched by curl on October 11.
However, when Intego checked the curl version running on macOS Sonoma 14.1.1, it was discovered to be outdated. The updated, secure version of curl is 8.4.0, but the macOS Sonoma version is 8.1.2.
“That curl version is from May 30, 2023,” Intego’s researcher wrote.
Since May, there have been two other vulnerabilities (CVE-2023-38039 and CVE-2023-38546) that curl has addressed through updates. But it appears that Apple did not implement the updates for Sonoma.
Sonoma updates leave even more things behind
Intego also reported that the new Sonoma has outdated and vulnerable versions of three of the libraries that curl depends on and uses — LLibreSSL, zlib, and nghttp2.
These libraries, used heavily by developers who use curl, are responsible for vital parts of online behaviors. They help keep users safe through encryption, are used to download files, and are used to encrypt and decrypt data transfers and compress large files, in addition to many other operations.
The nitty-gritty on the missing Sonoma curl library patches
The following are the details of the vulnerabilities related to curl libraries that exist in macOS Sonoma.
LibreSSL:
- In Sonoma: Outdated and vulnerable
- Current LibreSSL version: 3.8.2 (November 2, 2023)
- Sonoma version: 3.3.6 (March 15, 2022)
- Outdated for about 20 months
- LibreSSL National Vulnerability Database listed vulnerabilities include:
- CVE-2021-41581
- CVE-2022-48437
- CVE-2021-46880
- CVE-2023-35784
- Apple does not mention this vulnerability on its site
Zlib:
- In Sonoma: Outdated and may be vulnerable
- Current Zlib version: 1.3 (August 18, 2023)
- Sonoma version: 1.2.12 (March 27, 2022)
- Outdated for about 20 months
- Vulnerabilities that Zlib has patched since the version Sonoma uses include:
- CVE-2022-37434
- Apple assures that it has addressed this vulnerability, but it has not
Nghttp2:
- In Sonoma: Outdated and vulnerable
- Current nghttp2 version: 1.58.0 (October 27, 2023)
- Sonoma version: 1.55.1 (July 27, 2022)
- Since then, nghttp2 patched a “7.5 out of 10” high-severity vulnerability:
- CVE-2023-44487
- Apple does not mention this vulnerability on its site
Great, so how do I keep my Mac safe?
Curl and some of the libraries it uses are often unknown digital resources for average users. Nevertheless, even if you are not a developer, a programmer, or linked to that type of work, you are still affected.
As already explained, these resources are used by many applications, such as web browsers, email clients, and operating systems. These unpatched vulnerabilities do expose users and leave them more vulnerable to cyberattacks, and while Mac users have few tools at their disposal to patch these themselves, there are still some steps you can take.
First of all, keep an eye out for new updates and make sure they are set to be downloaded and installed automatically on your Mac. Second, while antimalware cannot stop zero-day attacks, nor will it patch these types of vulnerabilities, it can still detect most of the malware that cybercriminals use after exploiting the vulnerabilities.
You can think of these vulnerabilities as open gates to your computer. While there is nothing at the time that Mac users can do about the open gates, once bad actors break through that gate, they will deploy malware. This is where a trusted and professional antimalware tool comes in handy. Always keep your antimalware up and running in the background.
Finally, keep an eye on your computer and take note of any suspicious behavior as you maintain good digital security practices. Hopefully, Apple will patch these vulnerabilities quickly.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, iOS, macOS, and watchOS are trademarks of Apple Inc.





