DuckTail, a group of cybercriminals from Vietnam, has been targeting TikTok, Facebook, LinkedIn, and Google for years. Now, a new investigation finally reveals how they breach accounts, infect devices, and steal sensitive data.
On August 30, Zscaler ThreatLabz released the full details of a 3-month intelligence-gathering operation with the goal of exposing DuckTail. The investigation shows that the criminals abuse a wide range of well-known sites, hack into social media and other accounts, and steal information from web browsers, including Chrome, Edge, Brave, and Firefox.
This is how DuckTail malware attacks spread
DuckTail cybercriminals use several methods to distribute their malware. These include email campaigns that target a specific group of victims — a technique known as spear phishing. They also impersonate job recruiters from real companies and contact users on LinkedIn using fake profiles or create fake posts on the platform.
The group, which has mastered both social engineering techniques and malware, is taking advantage of the recent trend of tech layoffs and the so-called Great Resignation or Great Reshuffle, as hundreds of thousands of people look for new jobs.
Focusing mostly on the digital marketing and advertising industry, DuckTail members use stolen Facebook, TikTok, and Google ad accounts to carry on their campaigns. Breached accounts are also bought and sold among the group in an underground market.
What are these cybercriminals after?
DuckTail members are sharing resources, malware, and techniques to steal social media, messaging accounts, and other accounts, with their main goal being to install infostealer malware that targets web browsers.
DuckTail members breach accounts and hack browsers to:
- Steal personal data
- Steal financial data
- Spread malware
- Sell data in underground forums
- Commit fraud and identify theft
Step by step: Tricking victims
As mentioned, DuckTail’s members set up profiles on LinkedIn, impersonating recruiters, often adding the Hiring banner to their profile picture. But let’s break down what this looks like in practice.
In 3 steps, here’s how these attacks work:
- The hacker uses a fake profile or a stolen account to impersonate a job recruiter and then contacts a victim.
- Once the victim shows interest in the fake job, they are convinced to download a file.
- If the file is downloaded, the malware is installed, breaching the device without the user’s knowledge.

This extremely simple technique is paying off for the bad actors, who have even created instructional videos to guide victims through the download process.
How to spot a DuckTail malware attack
While in the past, little was known about how this group operated, we now have enough information to help you identify this type of cyberattack. Here’s how to stay one step ahead of a DuckTail malware attack.
It’s all about language
Zscaler ThreatLabz explains that DuckTail cybercriminals have a weak spot. Their English language skills don’t match those of an HR American professional. To draft emails, ads, or contact victims, DuckTail members are using ChatGPT and GoogleTranslate to chat in real time.
The result is clear. When chatting with a DuckTail member who is trying to convince you about a fake job and to download a file, you will notice clunky language and phrases or sentences that, while accurate, are not exactly how native-English speakers speak.
Do not download that file
Another sign of a DuckTail malware attack is the insistence on downloading a file. While real job recruiters will share links and even text files with new potential employees, they will rarely ask you to download a .NET executable file, a browser extension, or an Excel file, especially one that strikes you as odd in any way.
When asked to download a file for a new job, check if the file:
- Is significantly large (70 MB or more)
- Has a strange-looking .doc or PDF icon
- Was sent along with other files, images, or videos
DuckTail hackers send these files via Telegram, LinkedIn, and email. They also send victims links to cloud-hosting sites like iCloud, Google Drive, Dropbox, Transfer.sh, Rebrandly, and OneDrive, and ask them to download the files from there.
Watch out for fake ads
DuckTail is also leveraging the popularity of new technologies like ChatGPT and Google Bard AI, creating fake ads offering these services.
In other words, if you see an ad promoting these tools, don’t click on it. You can always visit the official pages of these sites if you are interested in them.
Did you get a password notification warning? Check it
The first thing a DuckTail attacker will do after breaching an account is change the password. When that happens, you’ll get an email or SMS notification warning you of the change.
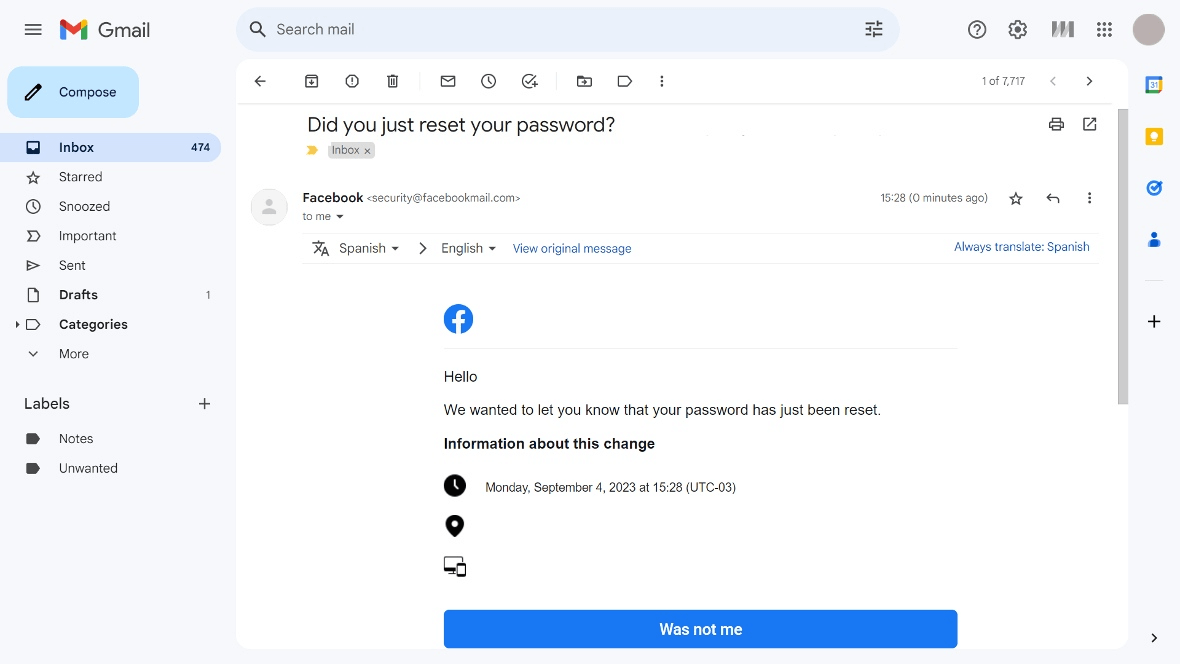
If you do get a warning that your password, recovery settings, or other authentication configurations have been modified, don’t ignore it. Log in to your account immediately, change the password, and update your recovery options. If you act fast, you can lock the attacker out before the real damage begins.
Some final words of security advice
Searching for a new job that meets your expectations is an opportunity to change your life, but it’s also a challenge. Whether you are seeking to grow in your career or your long-term professional goals, the last thing you need is a group of cybercriminals fully dedicated to luring you into a malicious scam.
Always remain vigilant when engaging with HR recruiters, especially if they seem to come out of nowhere and offer job positions that seem too good to be true. Thoroughly check the background of anyone contacting you with an offer, and if necessary, contact the company they claim to represent.
You should also pay close attention to the language of the person contacting you and any conditions they are imposing. Additionally, be extra cautious anytime someone you don’t know asks you to download a file. Plus, it’s always a good idea to have professional anti-malware software installed and running to warn you about files, links, or websites if they are suspicious or contain malware.
Follow the guidelines in this report to identify a DuckTail malware attack, and keep your passwords updated and your multi-factor authentication enabled. And finally, check your browser to see what information you are “auto-saving” on it. A little vigilance can go a long way toward keeping you safe online.