The Russian hacker group APT29 is back and up to no good. This time, according to a new investigation, the group — also known as Midnight Blizzard and Cozy Bear — is luring European diplomats with fake wine-tasting invitations.
Using email and targeting European governments, diplomats, and non-European countries’ embassies located in the region, APT29 is impersonating a major European Ministry of Foreign Affairs. While this campaign only targets diplomats in Europe and poses no immediate danger to the average Apple user, it is an interesting development, so let’s dive in.
APT29 resurfaces in European diplomats’ inboxes
On April 15, Check Point Research released findings on an investigation that began in January 2025, when they began tracking a wave of spear phishing email campaigns that went after European governments and diplomats in the region.
Check Point attributed the threat campaign to the Russian group APT29 due to malware and tactics, techniques, and procedures (TTPs) that observed “strong similarities” to the March 2024 WINELOADER campaign, which was linked to the Russian hacker group.
“In that earlier attack, APT29 also initiated the campaign with a phishing email disguised as an invitation to a wine-tasting event, that time impersonating an Indian Ambassador,” Check Point said in its report.
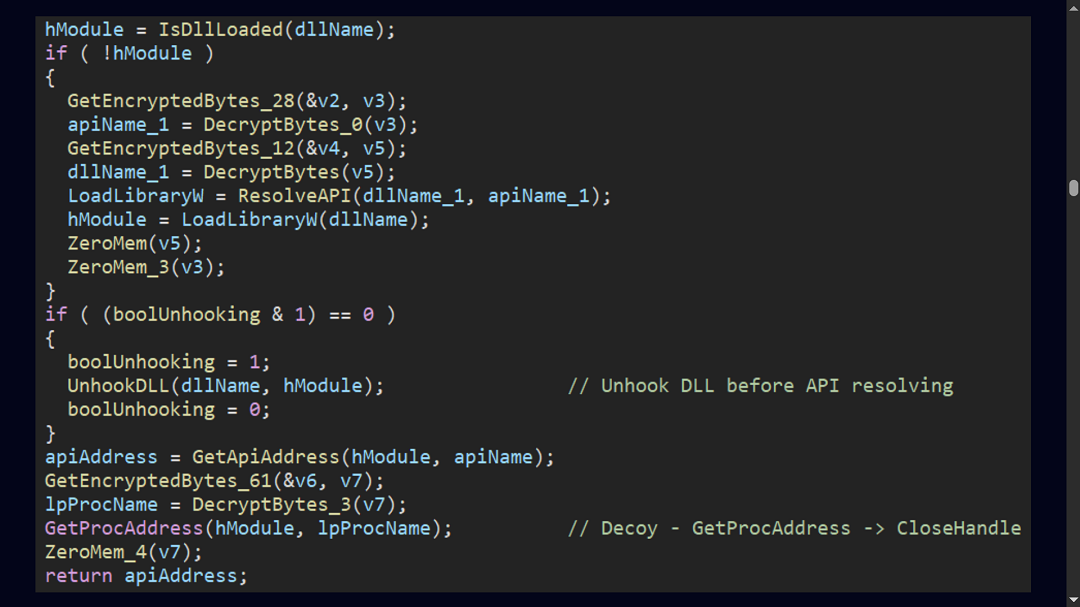
This new wine-tasting campaign, however, has some previously unseen cloak-and-dagger tricks. The initial-stage trojan is new; instead of using WINELOADER, the group developed GRAPELOADER. Other than that, the execution method, persistence technique, and side-loading remain the same as in 2024.
GRAPELOADER seems to be an enhanced version of WINELOADER, with new code that allows it to bypass security mechanisms and helps it remain hidden.
This new trojan is a modular backdoor designed to breach computers, gather basic system environment data, and set up a C2 communication channel between the victim’s device and the attacker-controlled server for further malware downloads.
Why does APT29 want to have a wine-tasting experience with European diplomats?
APT29 is a highly sophisticated nation-state threat group, most infamously known for its link to the SolarWinds cyberattack. The SolarWinds hack affected nearly 18,000 organizations and companies in the US, including high-value customers and the federal government.
While Check Point Research has not established the motive behind this new wine-tasting email and web phishing threat, it is most likely a cyberespionage campaign.
Given that this threat campaign began in January of this year, the exact time when President Trump took office, the phishing emails are most likely an attempt to gather high-value intelligence from diplomats as the world reshapes policies driven by actions taken by the new US administration.
Issues of potential national interest to the Russian government during the early months of the Trump presidency and today include the European diplomatic stance and support for Ukraine, tariffs, information on sanctions, and how supply chains might shift, especially regarding Russian oil and gas.
APT29 is not inviting Apple users to their “wine-tasting” — or are they?
According to Check Point Research, even if you happen to be a diplomat in Europe, you are still in the clear from APT29 attacks if you use an Apple environment. While you might still receive a “wine-tasting” email, the investigation shows that the malware is coded solely to breach Windows operating systems.
Nevertheless, you should not lower your guard.
APT29 is sending out two types of emails. One of them has the trojan backdoor hidden in a PowerPoint Presentation file. The other type of email includes a link to a phishing website.
The hidden backdoor in the PowerPoint Presentation file (ppcore.dll) will not run on a Mac unless very rare conditions are met. DLL files are Windows dynamic link libraries and cannot run directly on Mac devices. For this type of file to infect an Apple environment, the victim would need to have special software like one called Wine — how’s that for a coincidence?
Wine is an open-source compatibility tool that allows certain Windows applications — and the DLL files they may rely on — to run on macOS. Without such software, a DLL remains inactive on an Apple computer.
As far as we know, there is no evidence of open-source Apple environment compatibility malware included in this APT29 campaign.
While cross-OS attacks have been rising as a trend, cybercriminals run these threats by distributing two different malware variants: one for Windows and one for macOS.
Could threat actors inject open-source compatibility malware and make DLL files dangerous for macOS users? In theory, yes, but in the wild, it is rare.
Some sites European-region diplomats should avoid
Apple users could also face online data extraction risks if they click on the links to the phishing websites that APT29 created for this campaign. Known phishing websites identified so far include:
- bakenhof[.]com
- silry[.]com
Do not visit these sites. And if you receive an invitation for a wine-tasting and dinner in Europe, do not open it. Report it and delete it.
Other indicators of compromise (IoC) used to download malware include:
- hxxps://silry[.]com/inva.php
- hxxps://bakenhof[.]com/invb.php
Check Point Security Research reports that both of these sites download links to gather system information, checking things such as system data, time, and geolocation before triggering the malware download.
A look at the attack method and how the lure works
This campaign is quite simplistic and, strangely enough, lacks sophistication.
Although we have seen politicians and government representatives display a low level of cybersecurity hygiene in the past, diplomats in the European region are supposed to be briefed daily on cyber threats. They are also supposed to be given information on how phishing works and how to avoid this type of lure.
Having said that, the way the cyber attack works is this:
- You receive an email about a wine-tasting event with an attachment.
- For some reason, you download the attachment and run it.
- Modular malware is installed on your computer.
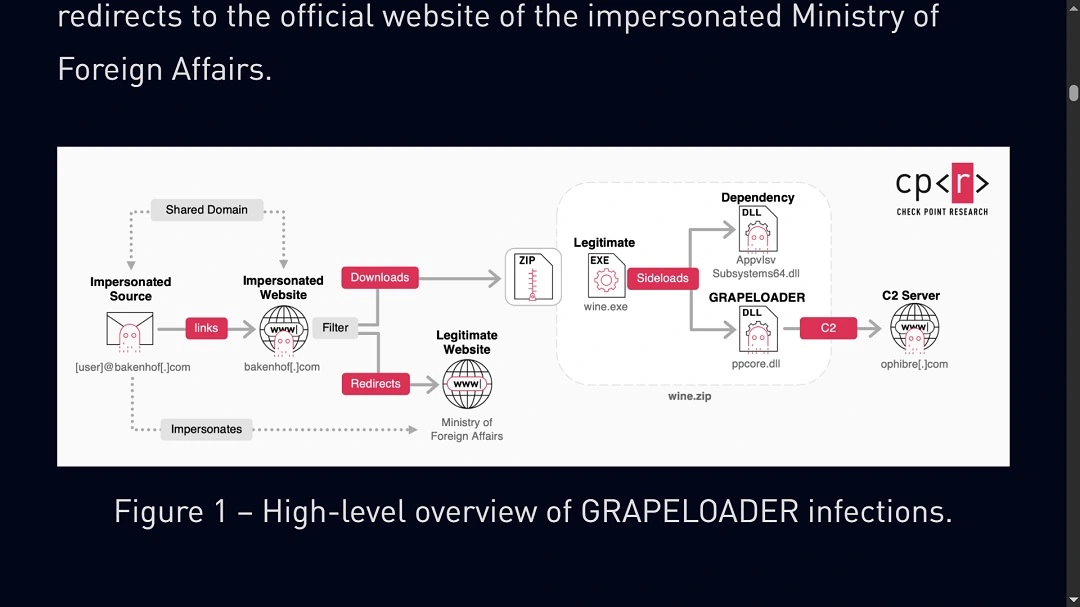
The alternate version of this attack involves a malicious link to a site designed to extract information and download the same Windows malware. But basically, that’s about it.
Compared to other attacks run by ATP29, the lack of sophistication is noteworthy. Back in 2019, ATP29 did not breach SolarWinds via phishing emails but rather through a sophisticated supply chain attack. That hack involved injecting malicious code into SolarWinds’ Orion software updates, a tactic of great complexity.
Check Point Research is confident that this new phishing email campaign is linked to APT29. They highlight that in 2024, the group executed a similar phishing campaign using this exact method and almost the exact same malware.
Final thoughts
While the volume of nation-state-supported cyber espionage campaigns breaking global news seems to have decreased significantly since the Trump administration took office, the investigation by Check Point Research shows that groups like APT29 are not dormant.
While there are some things worth taking a closer look at in this report, it does not seem to present a threat to Apple environments at this time.
What APT29 is up to with this campaign, which Moscow seems likely to either ignore or deny, is unknown. Will we see more action like this moving forward? We hope we will not have to answer that question anytime soon.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






